System files related to user accounts
/etc/passwd
Every user on a Linux system has a corresponding record line in the / etc/passwd file that records some of the user's basic properties. This file is readable to all users.
root:x:0:0:root:/root:/bin/bash bin:x:1:1:bin:/bin:/sbin/nologin daemon:x:2:2:daemon:/sbin:/sbin/nologin adm:x:3:4:adm:/var/adm:/sbin/nologin lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail:/sbin/nologin operator:x:11:0:operator:/root:/sbin/nologin games:x:12:100:games:/usr/games:/sbin/nologin ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin nobody:x:99:99:Nobody:/:/sbin/nologin systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin dbus:x:81:81:System message bus:/:/sbin/nologin polkitd:x:999:997:User for polkitd:/:/sbin/nologin postfix:x:89:89::/var/spool/postfix:/sbin/nologin sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin test:x:1000:1000::/home/test:/bin/bash User name:Passwords:User ID:Group ID:Annotative Description:home directory:Sign in Shell
/etc/shadow
Since the /etc/passwd file is readable by all users and can be easily cracked by an ordinary computer if the user's password is too simple or the rules are obvious, Linux systems with higher security requirements isolate the encrypted password and store it in a single file, which is the /etc/shadow file. Super users have read access to the file, which ensures the security of the user's password.
The record line in /etc/shadow corresponds to one in /etc/passwd, which is automatically generated by the pwconv command based on the data in /etc/passwd
root:$6$ZjgVVFhxfrdv5d/t$Pq7yLBEC/7f6gfTRW12BOHq4Dbv8JM25prkM8Ss6aqs5onbgkwZB.WKNk1G9J/MHLnzbh9QLefwFYu1xIV2BY/::0:99999:7::: bin:*:17110:0:99999:7::: daemon:*:17110:0:99999:7::: adm:*:17110:0:99999:7::: lp:*:17110:0:99999:7::: sync:*:17110:0:99999:7::: shutdown:*:17110:0:99999:7::: halt:*:17110:0:99999:7::: mail:*:17110:0:99999:7::: operator:*:17110:0:99999:7::: games:*:17110:0:99999:7::: ftp:*:17110:0:99999:7::: nobody:*:17110:0:99999:7::: systemd-network:!!:18860:::::: dbus:!!:18860:::::: polkitd:!!:18860:::::: postfix:!!:18860:::::: sshd:!!:18860:::::: test:$6$XLA0qyL4$Yqcn80DTvJSgM0q67x9Gcjm/0x..Dwom1MfwmTR1q5Sw92ZCsue9Jz5wrYeCM4wttmCu/1xAkl4ZiLxFGu2i8.:18861:0:99999:7::: Login name:encrypted password:Last Modified Time:Minimum time interval:Maximum time interval:Warning Time:Inactive Time:Failure Time:sign
/etc/group
Grouping users is a means of managing and controlling access rights for users in Linux systems.
Each user belongs to a user group; There can be multiple users in a group, and one user can belong to a different group.
When a user is a member of more than one group at the same time, the primary group to which the user belongs is recorded in the /etc/passwd file, which is the default group to which the user belongs at logon time, while the other groups are called additional groups.
To access files belonging to additional groups, users must first use the newgrp command to make themselves members of the group they want to access.
root:x:0: bin:x:1: daemon:x:2: sys:x:3: adm:x:4: tty:x:5: disk:x:6: lp:x:7: mem:x:8: kmem:x:9: wheel:x:10: cdrom:x:11: mail:x:12:postfix man:x:15: dialout:x:18: floppy:x:19: Group name:Passwords:Group ID:List of intra-group users
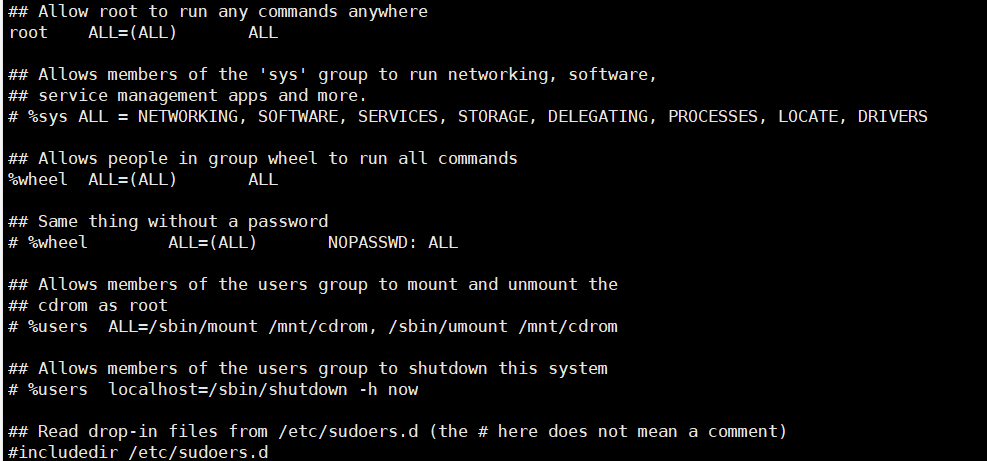
sudo claim
Sudo is a Linux system administration command and a tool that allows system administrators to let ordinary users execute some or all of the root commands. On Linux, for security, we generally operate under the normal user, but sometimes the normal user needs to use root privileges, such as when installing software. At this point if we need to cut back to the root user. After installation, you may need to cut back to the normal user, which makes the operation less efficient, so sudo commands are convenient.
When sudo is executed, it is equivalent to having root privileges to execute commands and automatically cut back to the normal user after execution
How to give normal users sudo privileges
Edit/etc/sudoers file
Each line represents what it means to be able to Baidu by itself, so that an ordinary user can have sudo privileges in a variety of ways, such as adding users to the wheel group or adding users (user groups) to files