Today, I want to make a tool for micro-blog to climb personal pages to satisfy some secrets. So first of all, do what you have to do! Simulated landing...
The code is for reference: https://www.douban.com/note/201767245/
I optimized the code, refactored it into Python version 3.6, and added a lot of comments for you to learn.
When PC logs on to Sina Weibo, the user name and password are encrypted in advance with js on the client side, and a set of GET parameters will be generated before POST, which will also be part of POST_DATA. In this way, it is not possible to simulate POST logins (such as Renren) in the usual simple way.
1.
Before submitting a POST request, GET is required to obtain two parameters.
The address is:
http://login.sina.com.cn/sso/login.php?client=ssologin.js(v1.3.18)
There are servertime and non CE values in the data, which are random, and other values seem to be useless.
What I don't know in the process of learning can be added to me?
python Learning Exchange Button qun,784758214
//There are good learning video tutorials, development tools and e-books in the group.
//Share with you the current talent needs of python enterprises and how to learn python from zero foundation, and what to learn
def get_servertime():
url = 'http://login.sina.com.cn/sso/prelogin.php?entry=weibo&callback=sinaSSOController.preloginCallBack&su=dW5kZWZpbmVk&client=ssologin.js(v1.3.18)&_=1329806375939'
# It returns a Response object that cannot be retrieved directly. After text, it can be matched by regular matching.
# About this: sinaSSOController.preloginCallBack({"retcode":0,"servertime":1545606770,...})
data = requests.request('GET', url).text
p = re.compile('\((.*)\)')
try:
json_data = p.search(data).group(1)
data = json.loads(json_data)
servertime = str(data['servertime'])
nonce = data['nonce']
return servertime, nonce
except:
print('Obtain severtime fail!')
return None
2.
Observing POST data through httpfox, the parameters are more complex, among which "su" is the encrypted username and SP is the encrypted password. Serrtime and non CE were obtained from the previous step. The other parameters are constant.
username is computed by BASE64:
username = base64.encodestring( urllib.quote(username) )[:-1]
password is encrypted three times by SHA1, and servertime and non CE are added to it to interfere.
That is, after two SHA1 encryptions, the results are added to the values of servertime and non ce, and then calculated by SHA1 again.
def get_pwd(pwd, servertime, nonce): # For the first calculation, notice that Python 3 encryption requires encode, using bytes pwd1 = hashlib.sha1(pwd.encode()).hexdigest() # Using the results of pwd1 to calculate the second time pwd2 = hashlib.sha1(pwd1.encode()).hexdigest() # Using the second result plus the previously calculated servertime and non CE values, hash once pwd3_ = pwd2 + servertime + nonce pwd3 = hashlib.sha1(pwd3_.encode()).hexdigest() return pwd3 def get_user(username): # Converting @ symbols into recognizable characters in URLs _username = urllib.request.quote(username) # base64 calculation in Python 3 also needs bytes # After base64 came out, there was a line break at the end, so the last character was sliced away. username = base64.encodebytes(_username.encode())[:-1] return username
3.
Organize the parameters, POST request. No login has been successful since then.
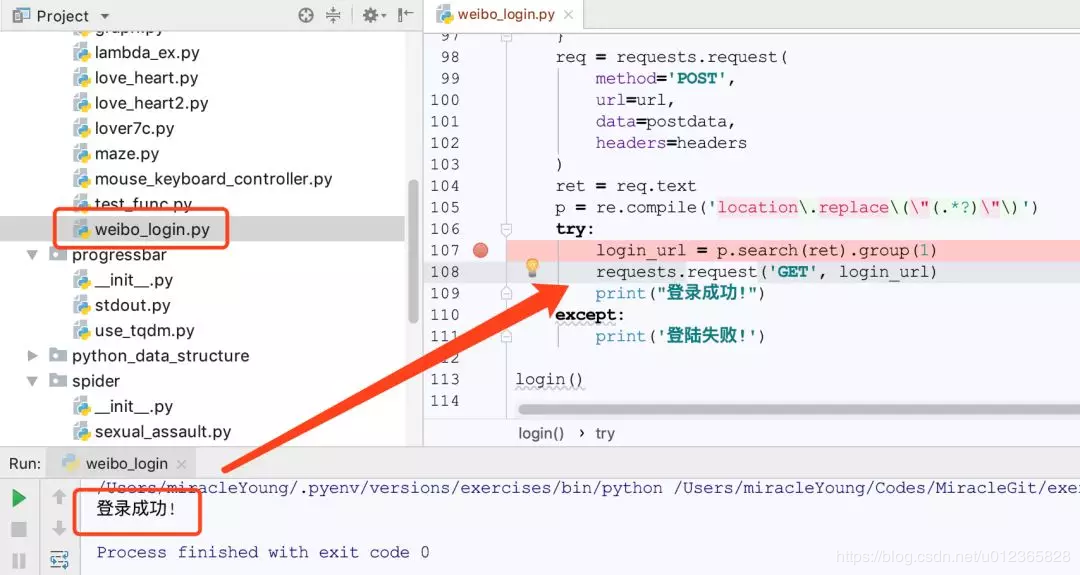
The POST contains a sentence:
location.replace("http://weibo.com/ajaxlogin.php?framelogin=1&callback=parent.sinaSSOController.feedBackUrlCallBack&retcode=101&reason=%B5%C7%C2%BC%C3%FB%BB%F2%C3%DC%C2%EB%B4%ED%CE%F3")
This is the result of login failure. The result is similar to that of successful login, but the retcode value is 0.
Next, ask for this URL, so that you can log in to Weibo successfully.
If you are still confused in the world of programming, you can join our Python learning button qun: 784758214 to see how our predecessors learned! Exchange experience! I am a senior Python development engineer, from basic Python script to web development, crawler, django, data mining and so on, zero-based to the actual project data have been collated. To every Python buddy! Share some learning methods and small details that need attention. Click to join us. python learner gathering place
Remember to build the cache ahead of time.