VMP2.X version features
The VMP of version 2.X has the following changes compared with version 1.0
- Self inflation increases a lot of confusing instructions
- VM_ The storage mode of context is changed from memory to stack, and there is no vmp1 section
- There are special analysis plug-ins to help analyze and understand
- The overall structure has changed
VMP2.13 shelling
This time, the plug-in is used to analyze VMP2.13.8. First, the target program is shelled, the minimum protection is selected, and only the virtual machine part of VM is analyzed
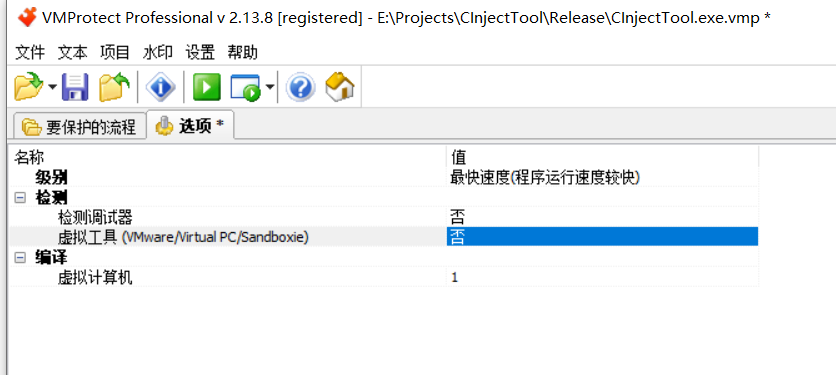
VMP2.13 code analysis
Enter VM virtual machine
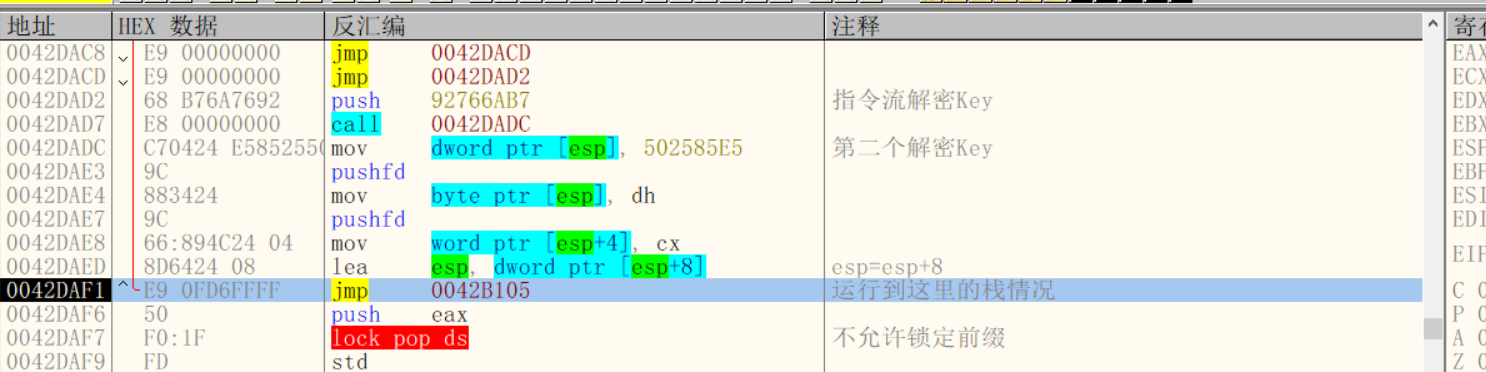
As before, an instruction stream decryption Key and Key are pressed into the virtual machine. Different from the previous version 1.0, the instruction stream decryption Key is encrypted.
0042DAE3 9C pushfd 0042DAE4 883424 mov byte ptr [esp], dh 0042DAE7 9C pushfd 0042DAE8 66:894C24 04 mov word ptr [esp+4], cx 0042DAED 8D6424 08 lea esp, dword ptr [esp+8] ; esp=esp+8
This string of instructions in the middle is confusing code. The stack has not changed before and after execution, so it is of no practical use.
save stack
Here, according to previous experience, you should start saving the register environment. Here, record the stack after entering the VM.
Compared with version 1.0, the save stack in version 2.X is relatively complex, and it is a little dizzy at the beginning of analysis.
$-8 > 502585E5--->Second decryption Key $-4 > 92766AB7--->Instruction stream decryption Key $ ==> > 0019FF30--->get into VM Timely ESP
Save eflags and edx
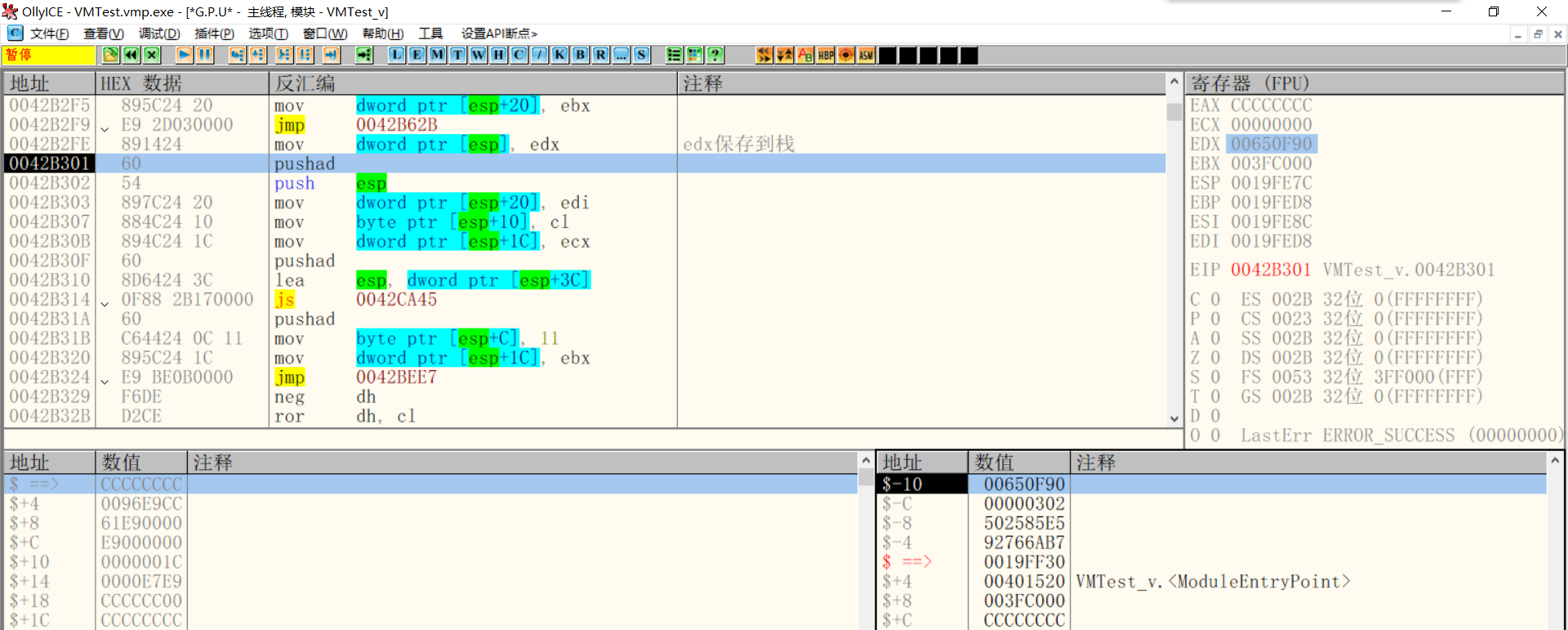
Continue the analysis. The VM starts to save edx to the stack. At this time, the stack environment is as follows:
$-10 > 00650F90--->edx $-C > 00000302--->eflags $-8 > 502585E5--->Second decryption Key $-4 > 92766AB7--->Instruction stream decryption Key $ ==> > 0019FF30--->get into VM Timely ESP
Save ecx and edi
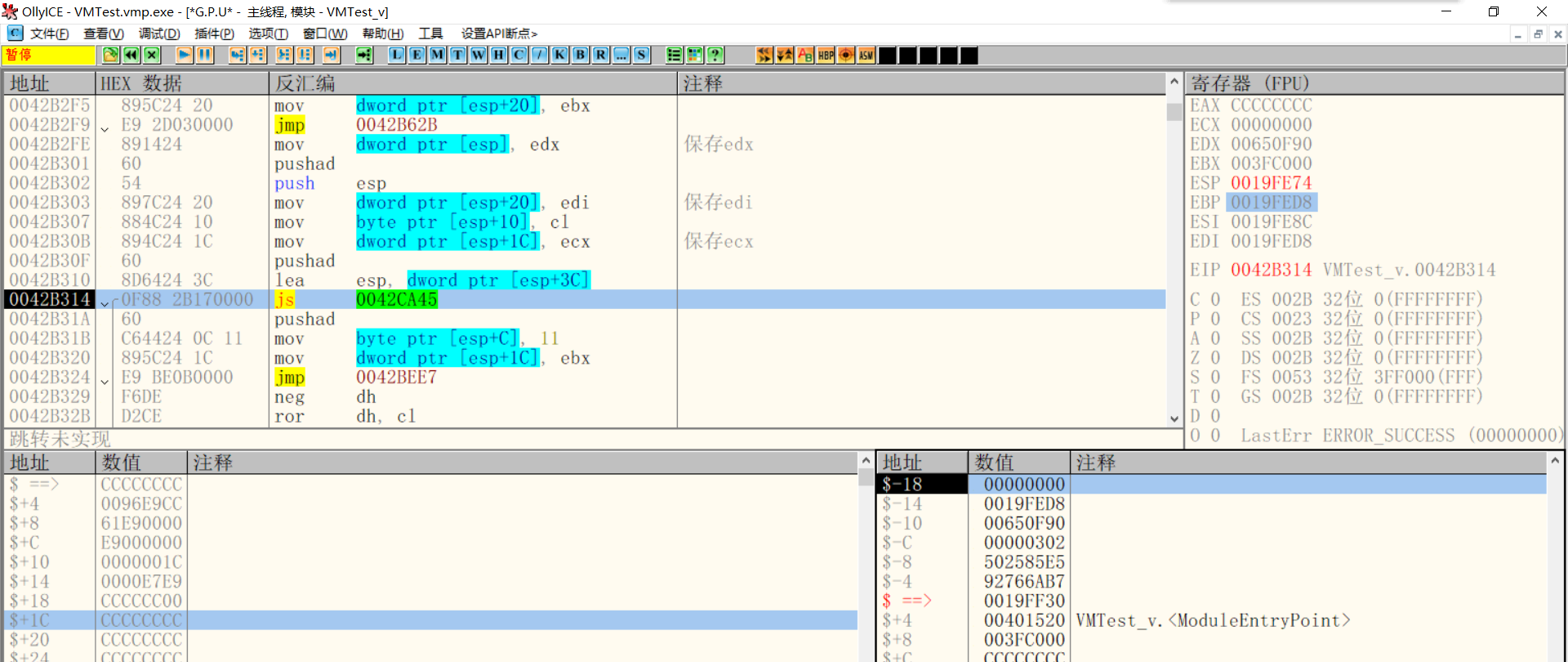
Moving on, the VM saves edi and ecx. The flower instruction in the middle is used to interfere with our analysis. We don't need to delve into it. Just pay attention to the stack changes in real time. The stack is as follows:
$-18 > 00000000--->ecx $-14 > 0019FED8--->edi $-10 > 00650F90--->edx $-C > 00000302--->eflags $-8 > 502585E5--->Second decryption Key $-4 > 92766AB7--->Instruction stream decryption Key $ ==> > 0019FF30--->get into VM Timely ESP
Save ebx
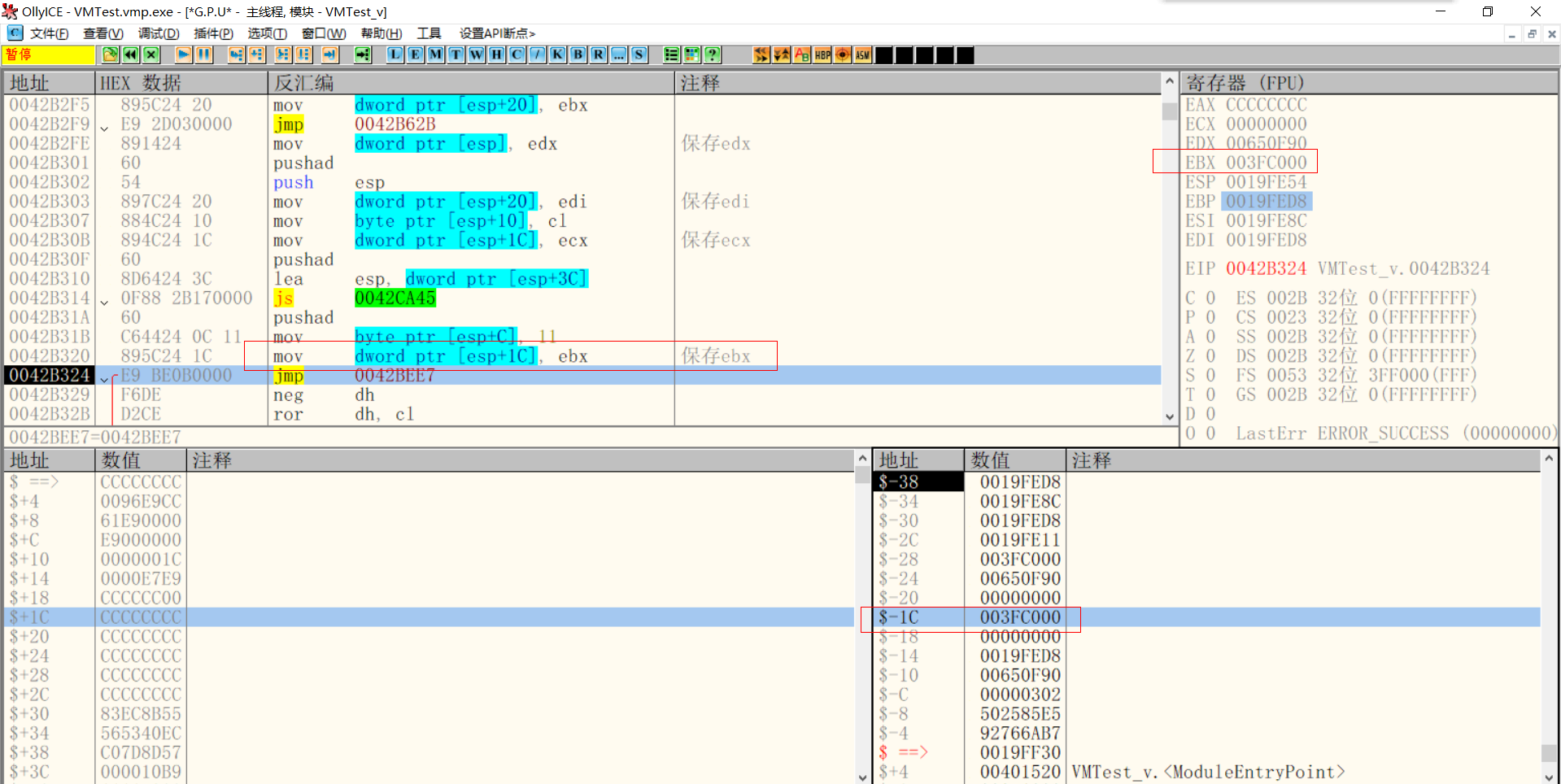
Then save ebx
$-1C > 003FC000--->ebx $-18 > 00000000--->ecx $-14 > 0019FED8--->edi $-10 > 00650F90--->edx $-C > 00000302--->eflags $-8 > 502585E5--->Second decryption Key $-4 > 92766AB7--->Instruction stream decryption Key $ ==> > 0019FF30--->get into VM Timely ESP
Save eax
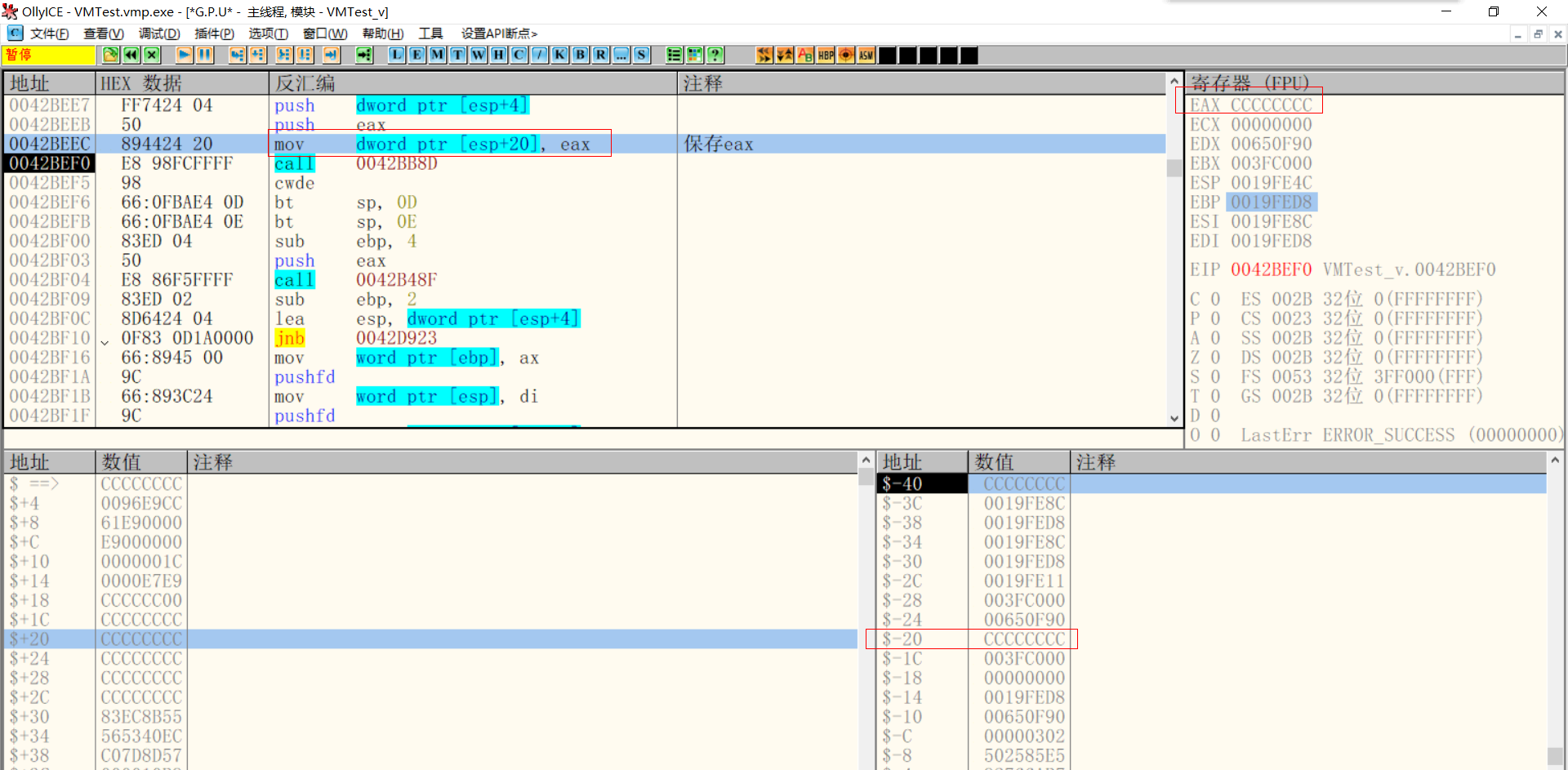
Then continue to save eax
$-20 > CCCCCCCC--->eax $-1C > 003FC000--->ebx $-18 > 00000000--->ecx $-14 > 0019FED8--->edi $-10 > 00650F90--->edx $-C > 00000302--->eflags $-8 > 502585E5--->Second decryption Key $-4 > 92766AB7--->Instruction stream decryption Key $ ==> > 0019FF30--->get into VM Timely ESP
Save ebx, EBP, and esi
Then save ebx, EBP and esi
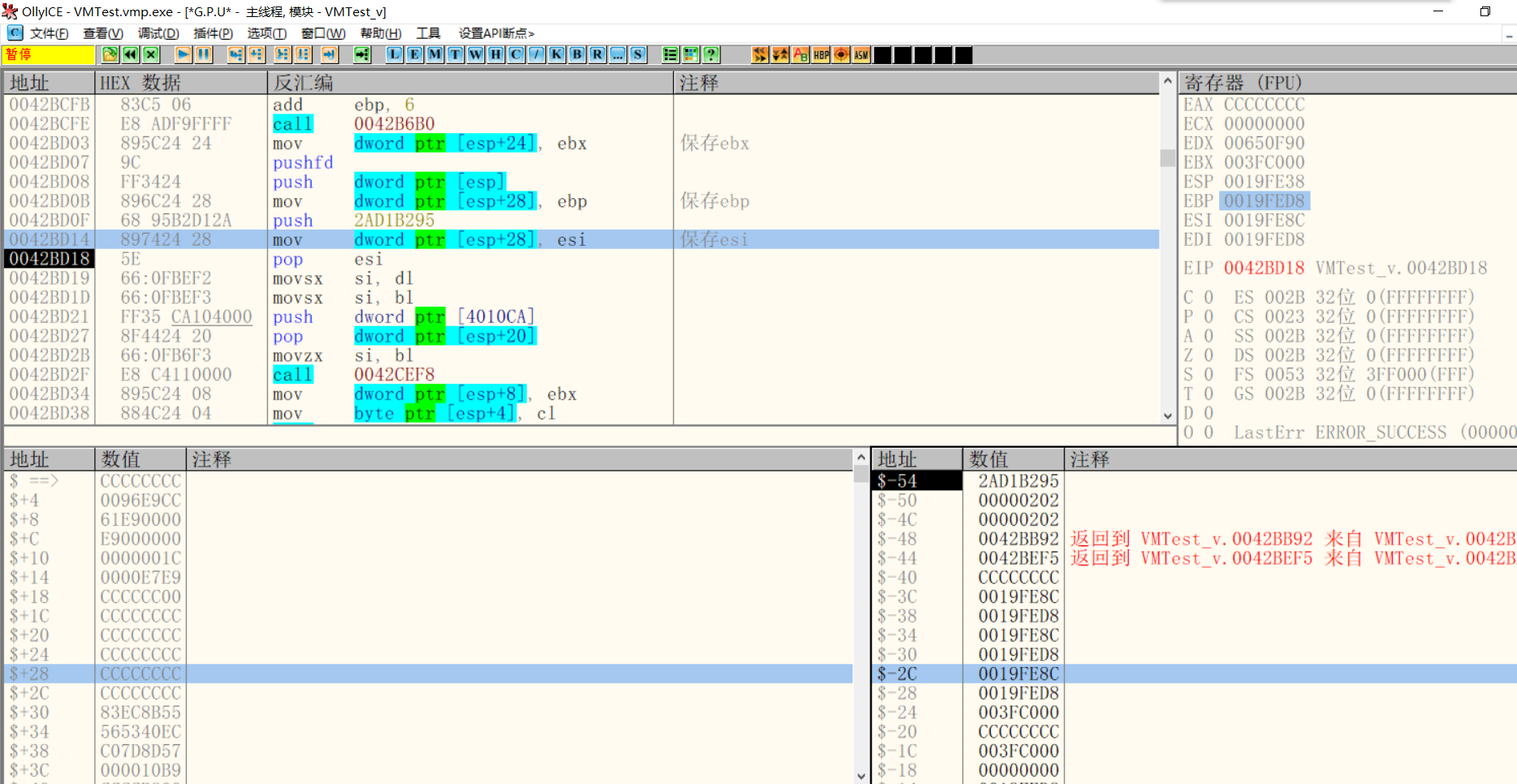
$-2C > 0019FE8C--->esi $-28 > 0019FED8--->ebp $-24 > 003FC000--->ebx $-20 > CCCCCCCC--->eax $-1C > 003FC000--->ebx $-18 > 00000000--->ecx $-14 > 0019FED8--->edi $-10 > 00650F90--->edx $-C > 00000302--->eflags $-8 > 502585E5--->Second decryption Key $-4 > 92766AB7--->Instruction stream decryption Key $ ==> > 0019FF30--->get into VM Timely ESP
At this point, the stack is saved and the VM decoding cycle begins
VM decoding cycle
Different from version 1.0, the VM decoding cycle of version 2.X needs to decrypt the instruction stream Key for decryption.
Decrypt instruction stream key
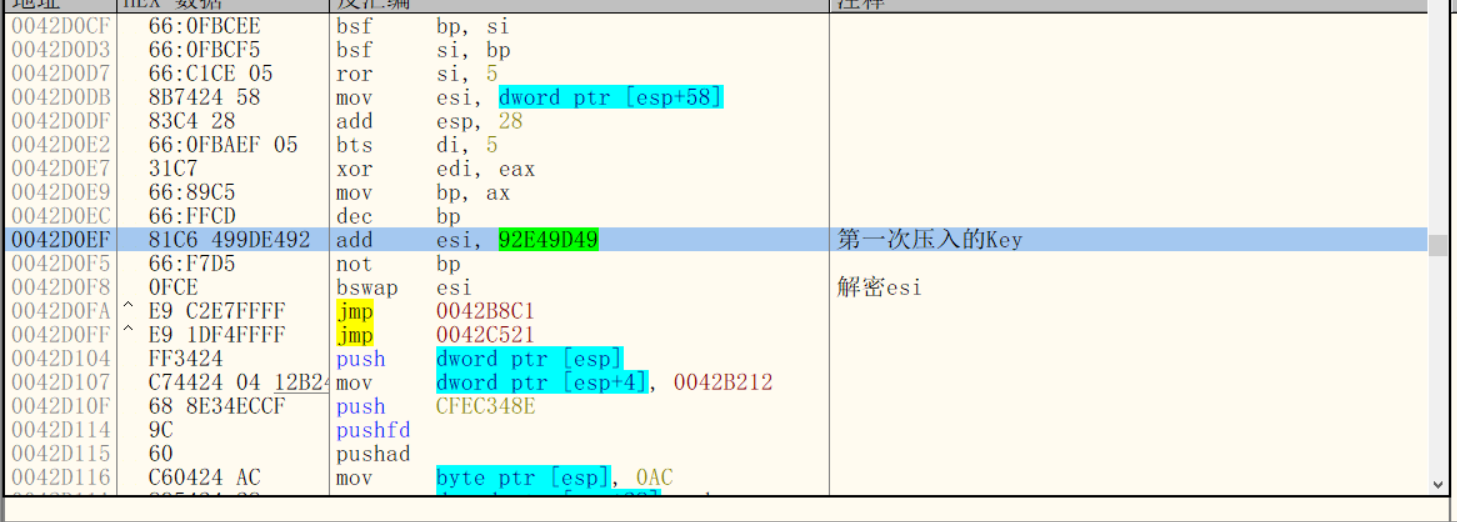
Then add the esi and the first pressed Key to decrypt the esi
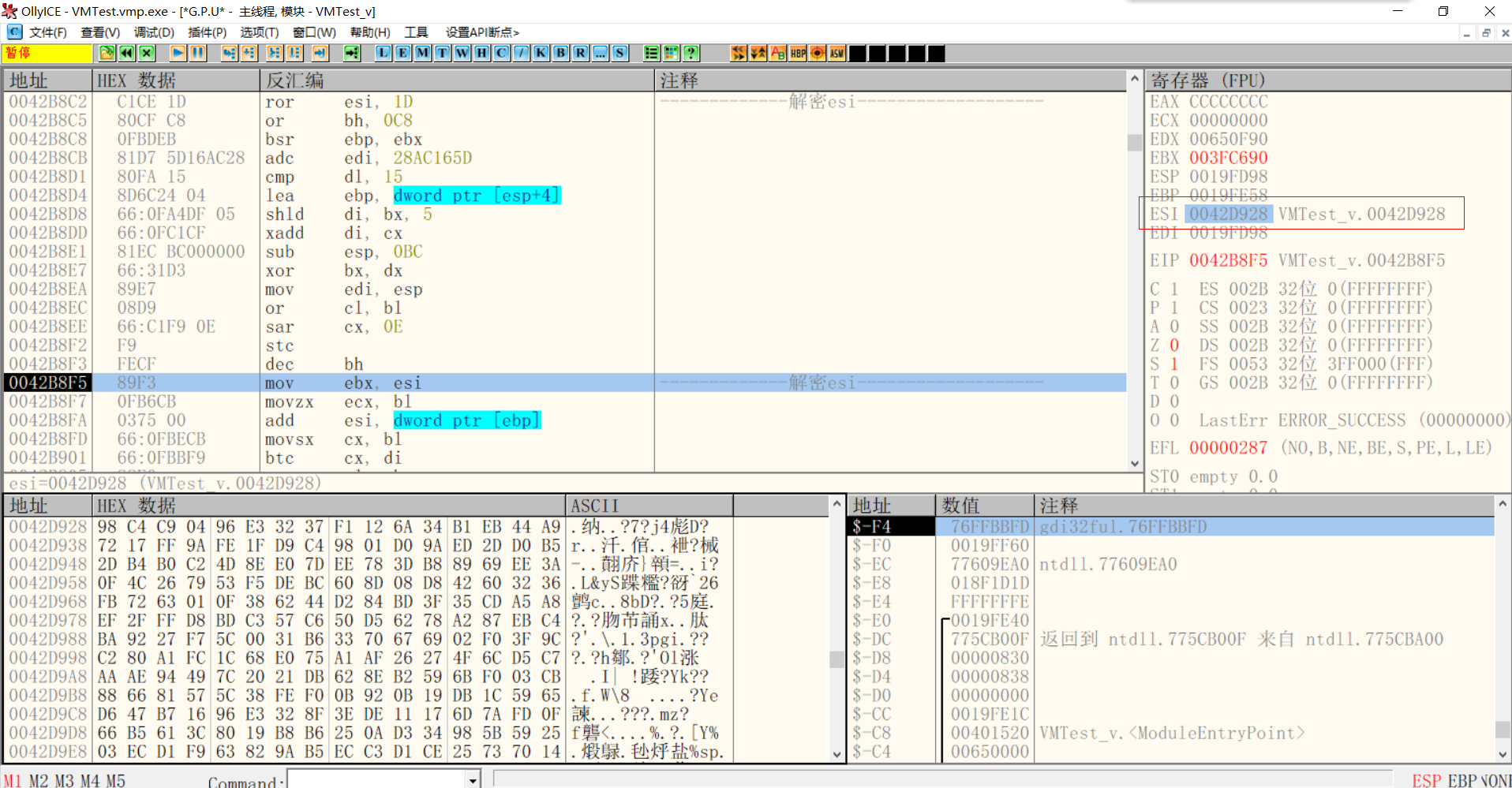
The content pointed to by the address after esi decryption is the instruction stream of the VM.
Decryption opcode
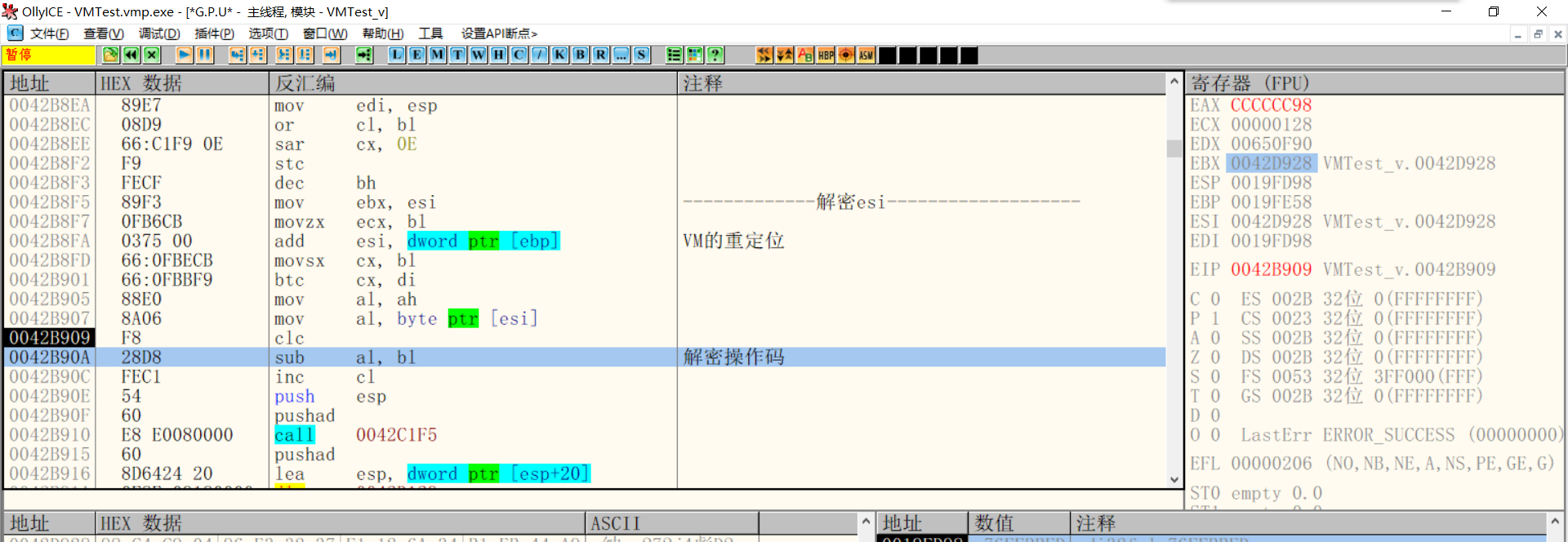
Then start fetching opcodes from the instruction stream
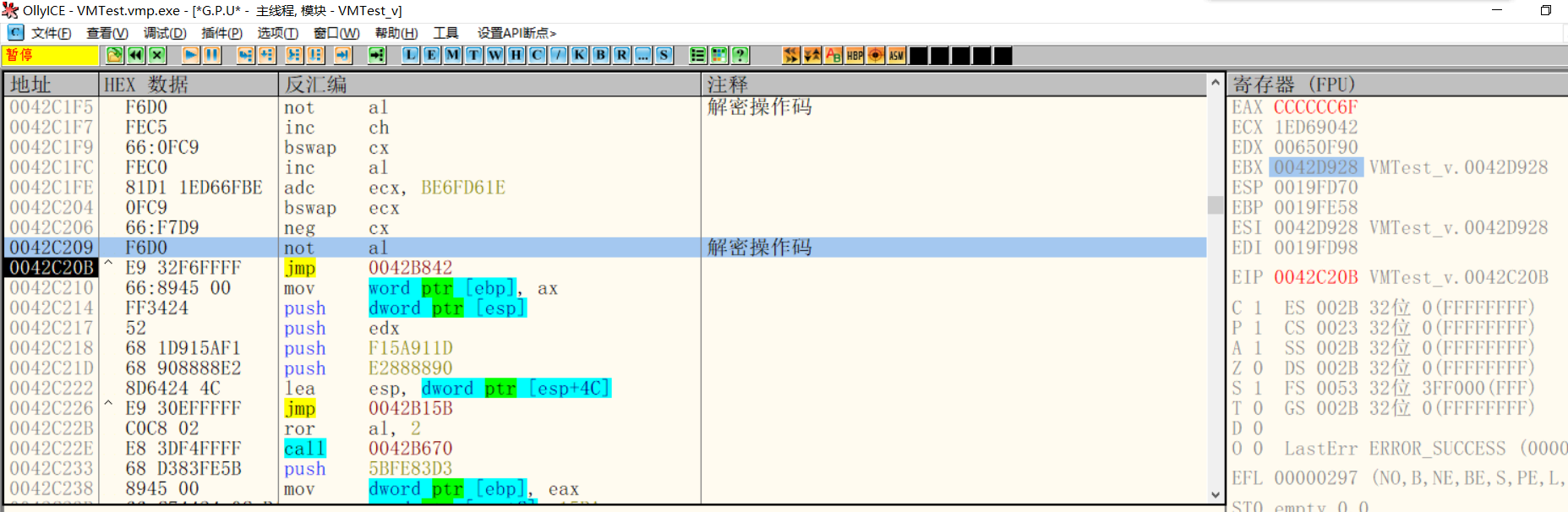
Then decrypt the opcode
Get encrypted handler
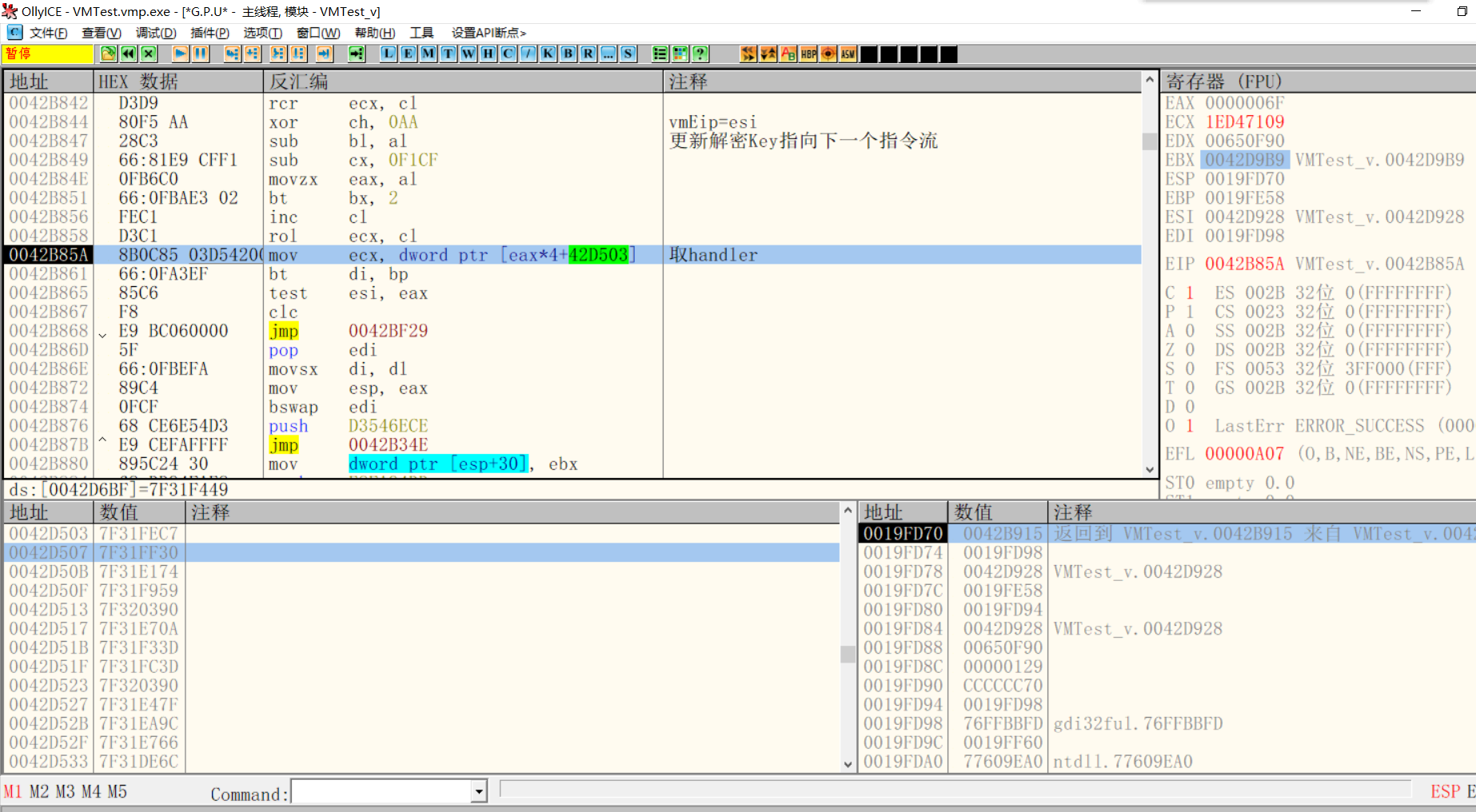
After vmEip points to the next instruction stream, start to get the handler. This handler is encrypted and needs to be decrypted before jumping to the correct address to execute the code
Decrypt handler
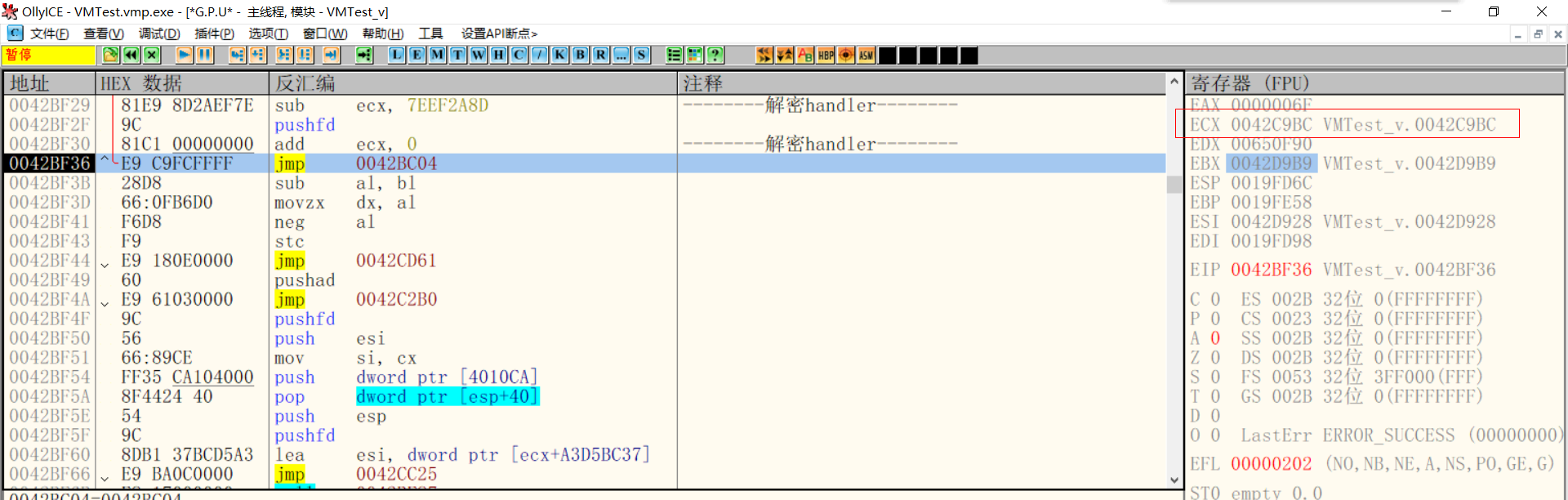
After decryption, the handler points to the correct jump address
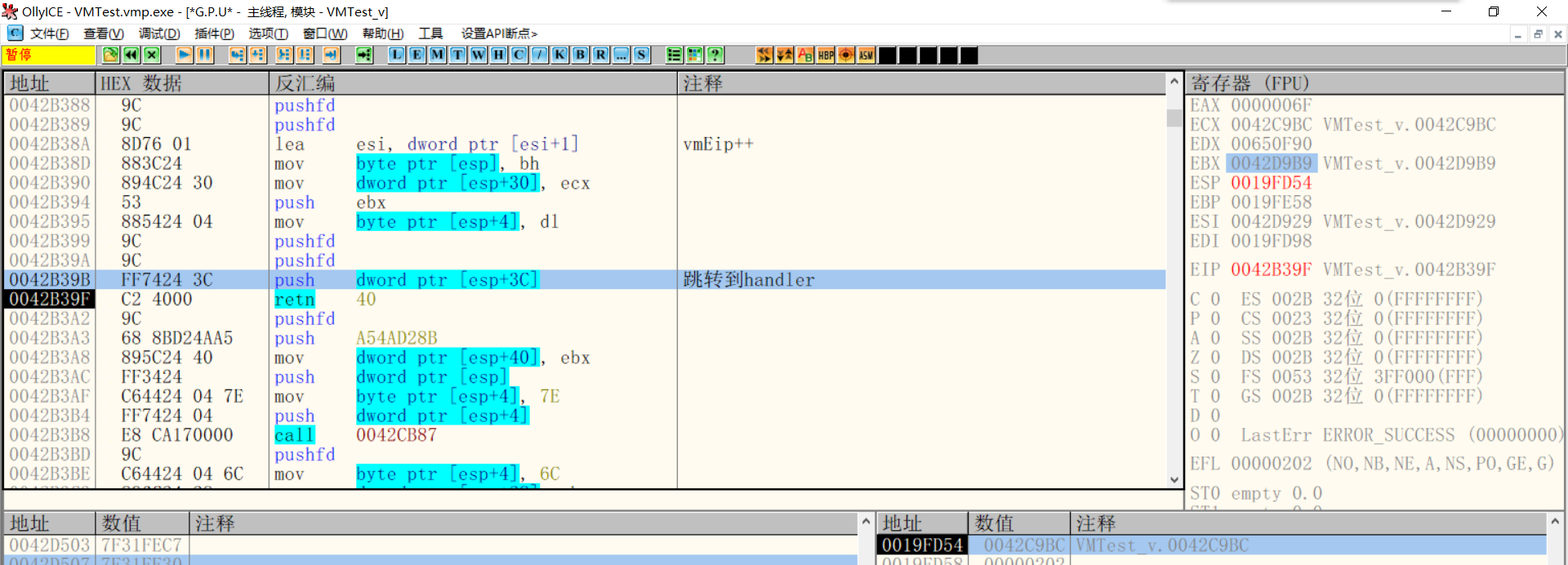
Then use push+ret to jump to handler
Decryption operand
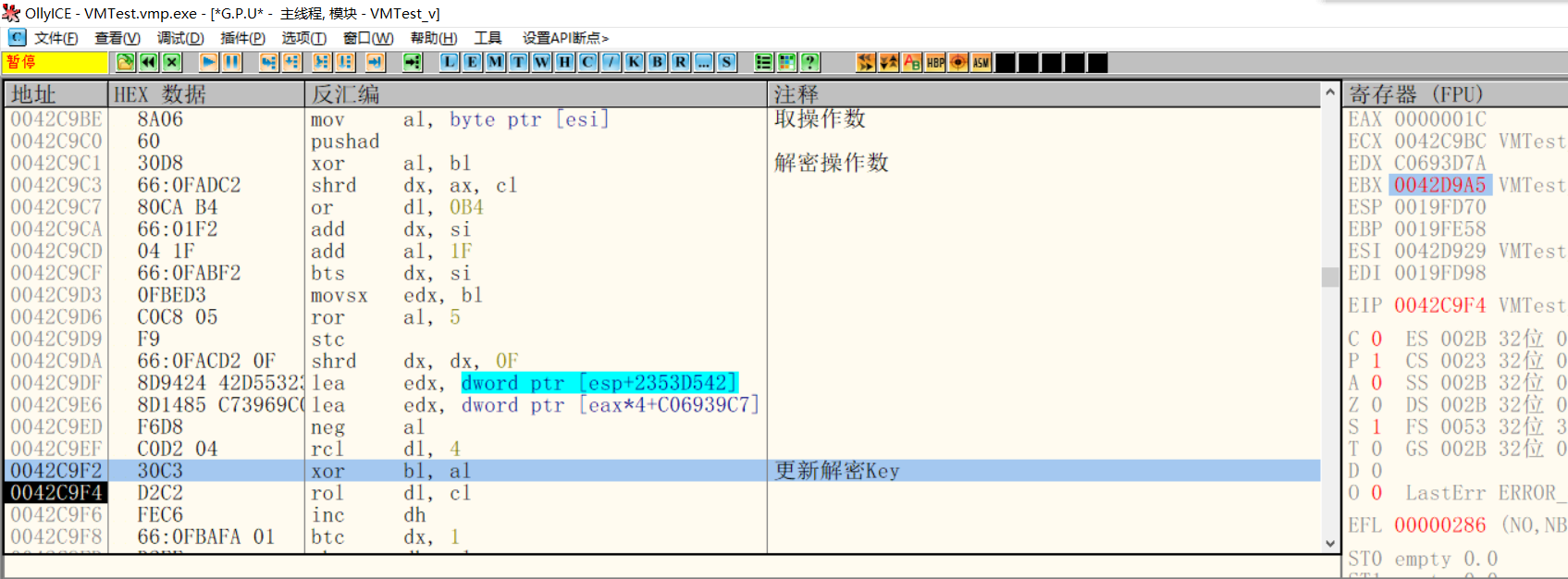
Before jumping to the handler, continue to fetch operands from the instruction stream and decrypt them. After decryption, update the decryption Key
Execute handler function
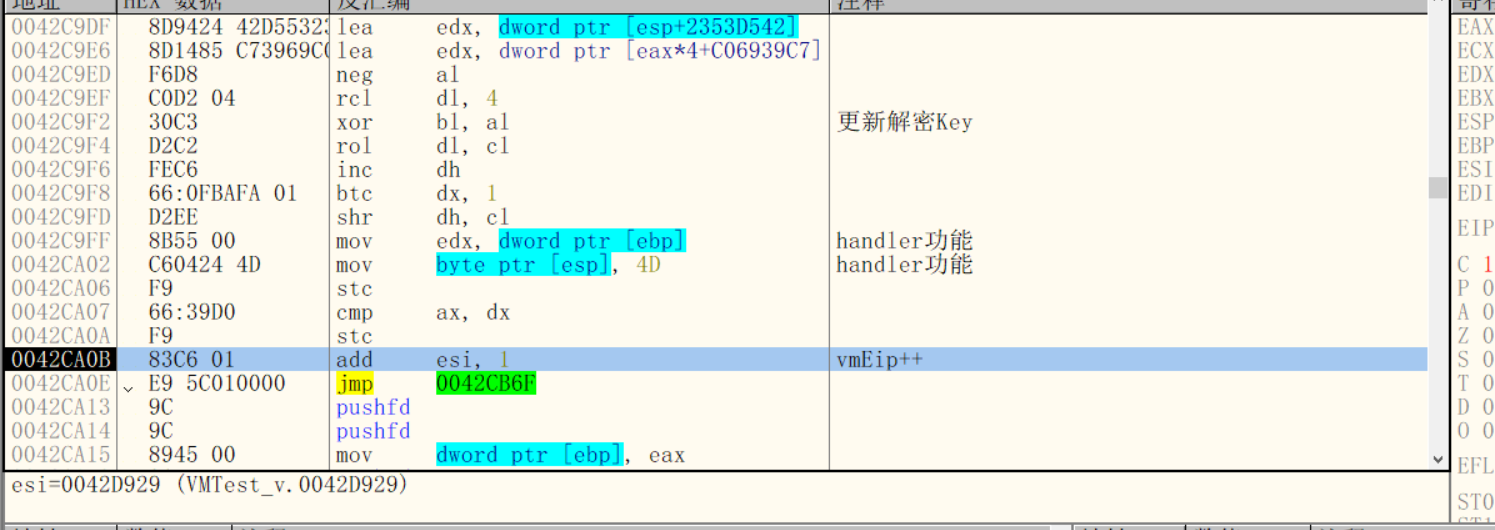
After the decryption Key is updated, start to execute the handler function and let vpEip++
After execution, jump to the position where the decoding cycle starts and start a new decoding cycle.
VMP2.13 process summary
The code flow of VMP2.13 is summarized as follows:
- Enter VM virtual machine
- Save stack environment
- Decrypt the Key pointing to the instruction stream
- Decryption opcode
- Get encrypted handler
- Decrypt handler
- Decryption operand
- Execute handler function code
- Start a new VM decoding cycle
- Restore stack, exit VM virtual machine