preface
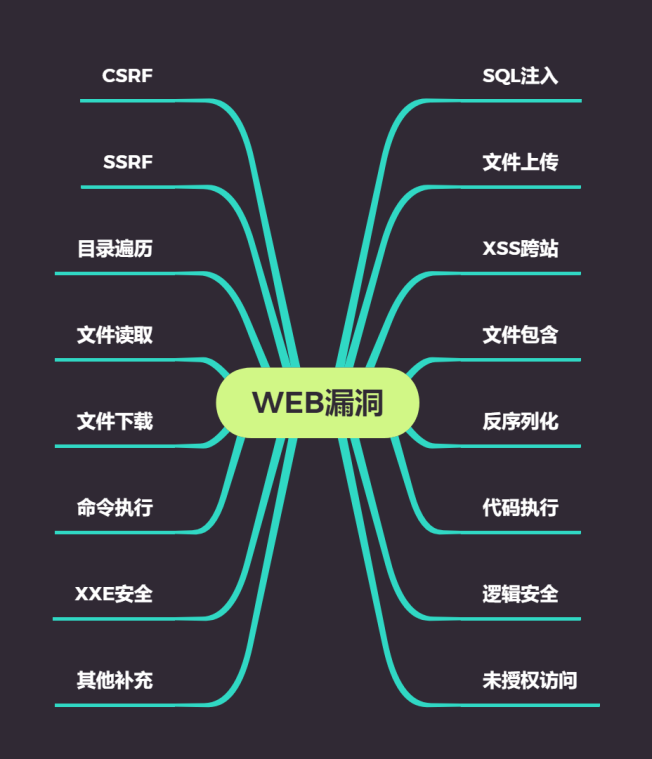
Explain the types of vulnerabilities on various WEB levels, the hazard level of specific vulnerabilities, and a brief impact range test for example analysis. The vulnerabilities in the mind map are also various knowledge points we will learn. In fact, according to the formation principle of vulnerabilities, how to find and use them.
CTF, SRC, red blue confrontation, actual combat, etc
Brief description of vulnerability hazards
The harm of each vulnerability is different
Brief description of vulnerability classification
Vulnerability hazard determines vulnerability level
High risk vulnerabilities: SQL injection, file upload, file inclusion, code execution, unauthorized access, command execution
Impact: it directly affects the website permission and database permission, and can obtain data or sensitive files of the website. Data security and permission loss are high-risk vulnerabilities
Medium risk vulnerability: deserialization, logical security
Low risk vulnerabilities: XSS cross site, directory traversal, file reading
Impact: the source code of the website, some account passwords of the website
Briefly describe the key contents of the vulnerability
CTF: SQL injection, file upload, deserialization, code execution
SRC: vulnerabilities can appear in the picture, and there are more logical security
Red blue confrontation: high risk vulnerabilities involved, including file upload, file inclusion, code execution and command execution
Briefly describe the vulnerability situation
The reason why I can't find the vulnerability is that I didn't collect the information well and I didn't understand the vulnerability enough
case
SQL injection vulnerability - database operation hazard
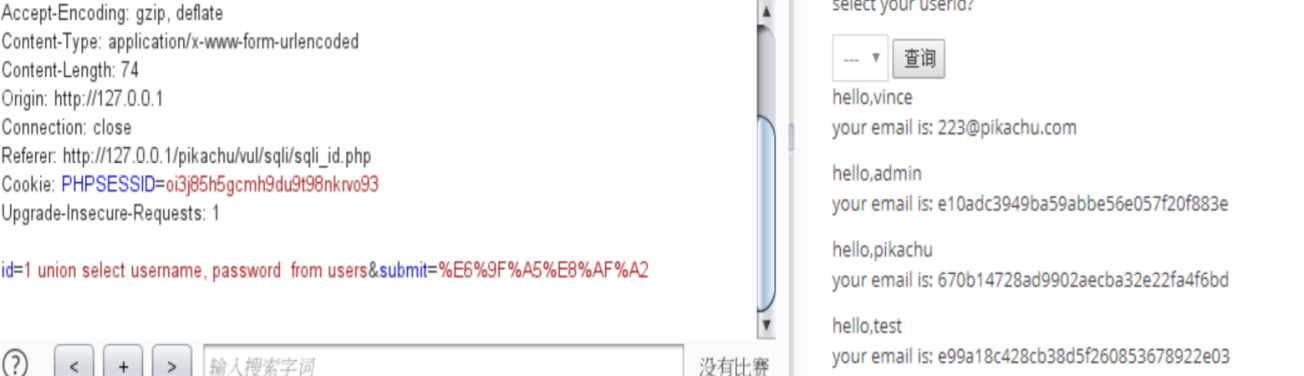
union query
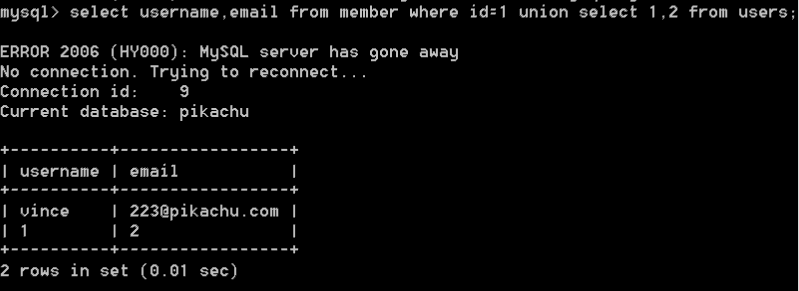
select username,email from member where id =1 union select username,password from users;
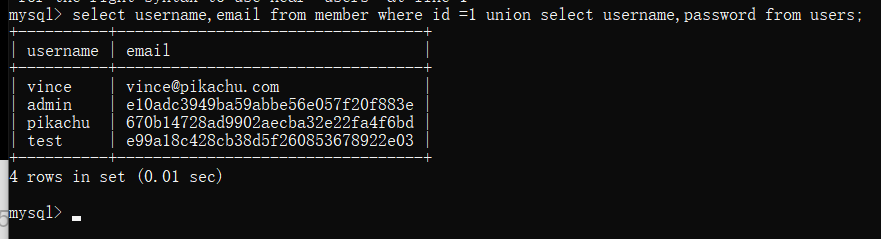
Click query, grab the data packet through bp, change the parameter id, and inject sql
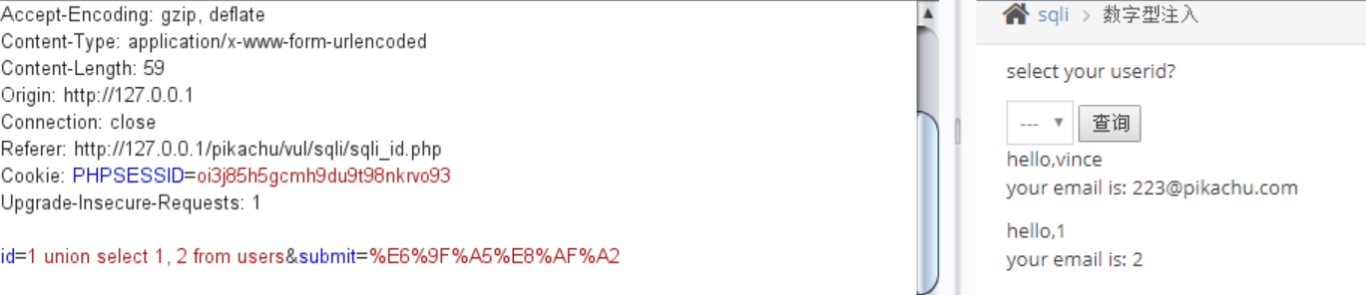
By guessing the field name and table name, we can find the user name and password in the database
Directory traversal vulnerability - source structure disclosure hazard (read folders and files but cannot read contents)
stay web In functional design,Many times, we will define the files to be accessed as variables, so as to make the front-end functions more flexible. When a user initiates a front-end request, the value of the requested file will be(Such as file name)Transfer to the background, and then execute its corresponding file in the background. In this process, if the background does not strictly consider the security of the value passed in from the front end, the attacker may pass“../"This method allows the background to open or execute some other files. As a result, the file results of other directories on the background server are traversed, forming a directory traversal vulnerability. See here,You may think that directory traversal vulnerabilities and unsafe file downloads and even File Inclusion vulnerabilities have the same meaning. Yes, the main reasons for the formation of directory traversal vulnerabilities are the same as these two. They are caused by passing the use of variables of files to be operated to the background in the functional design without strict security considerations, It's just that the phenomenon displayed by the location is different. Therefore, it's better to define it separately here. What needs to be distinguished is,If you pass without parameters url(For example: http://xxxx/doc) lists all the files in the doc folder. In this case, we become sensitive information disclosure. It is not classified as a directory traversal vulnerability. (you can learn more about sensitive information disclosure in "i can see you ABC")
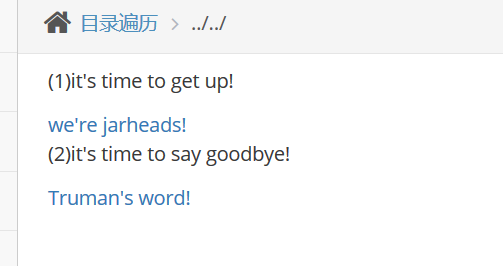
By viewing the source code of the web page, it is found that the source code of this line of elements is

After analyzing the source code of the two elements, it is found that it jumps to the php page through parameters
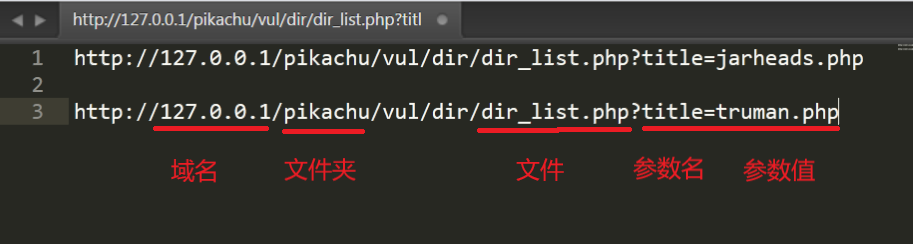
…/…/…/…/xxx.php can read across paths
Database information files can be obtained through directory traversal
Scan the directory through the scanning tool through... /... / index PHP look at the source code to find the file
File reading vulnerability - source code content acquisition harm (reading of a single file)
Construct a code to traverse folders and files and put it in the directory
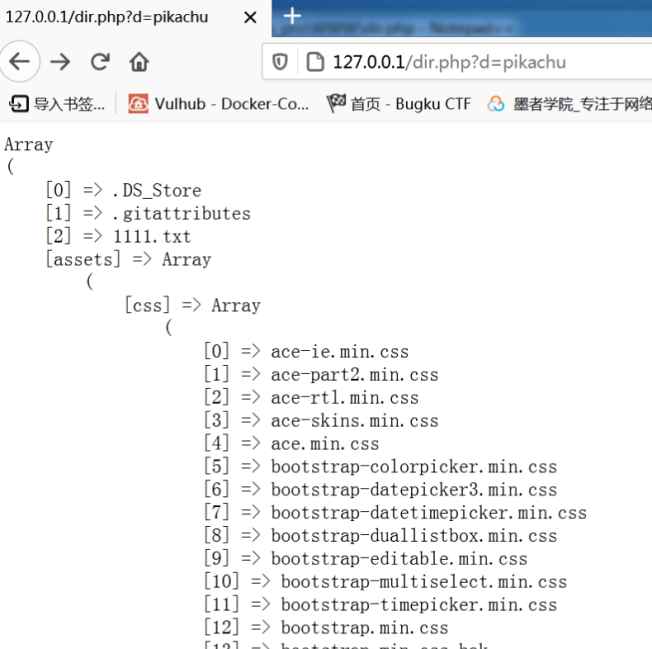
It will cause the disclosure of sensitive files
File upload vulnerability - WEB permission loss hazard
File upload function in web Application systems are very common. For example, many websites need to upload avatars and attachments when registering. When the user clicks the upload button, the background will judge whether the uploaded file is the specified type, suffix, size, etc., and then rename it according to the designed format and store it in the specified directory. If the background does not make any security judgment on the uploaded files or the judgment conditions are not rigorous enough, the attack may upload some malicious files, such as a one sentence Trojan horse, resulting in the destruction of the background server webshell. Therefore, when designing the file upload function, we must strictly consider the security of the transmitted files. For example: --Verify file type, suffix, size; --Verify how files are uploaded; --Some complex renaming of files; --Do not expose the path after file upload; --wait... You can pass“ Unsafe file upload"The corresponding test column to further understand the vulnerability
1. Upload files to the other party's website
2. If the other party has a file upload vulnerability, you can upload the back door file to the other party's folder
High risk vulnerability
example:
From the picture, you can only upload pictures
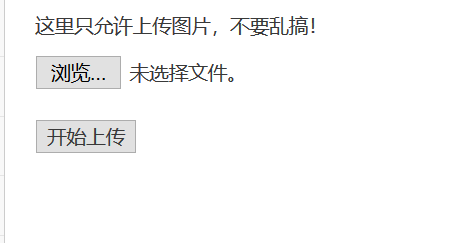
Let's try uploading a file first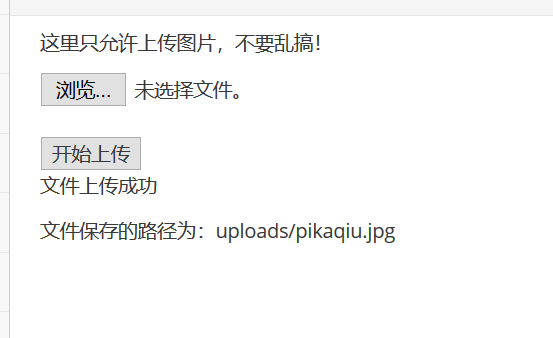
However, we can successfully upload the file by modifying the file suffix through bp packet capture.
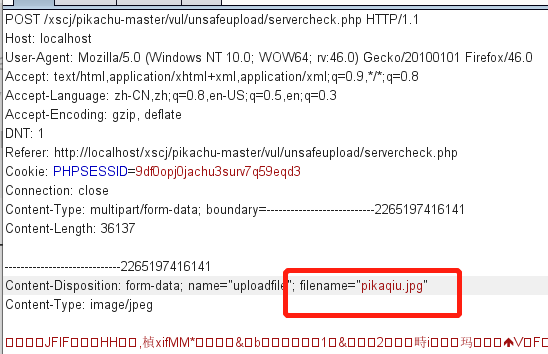
Modify jpg to php to upload Trojan files

File download vulnerability
The file download function is available in many ways web It will appear on the system. Generally, when we click the download link, we will send a download request to the background. Generally, this request will contain a file name to be downloaded. After receiving the request, the background will start to execute the download code to download the file corresponding to the file name response To the browser to complete the download. If the background receives the requested file name,If it is directly spelled into the path of the downloaded file without security judgment, it may lead to unsafe file download vulnerabilities. At this time, if the attacker submits not the file name expected by a program, but a carefully constructed path(such as../../../etc/passwd),It is likely that the specified file will be downloaded directly. This leads to sensitive information in the background(Password file, source code, etc)Downloaded. Therefore, when designing the file download function, if the downloaded target file is transmitted from the front end, the security of the transmitted file must be considered. Remember: all data interacting with the front end is unsafe and cannot be taken lightly!