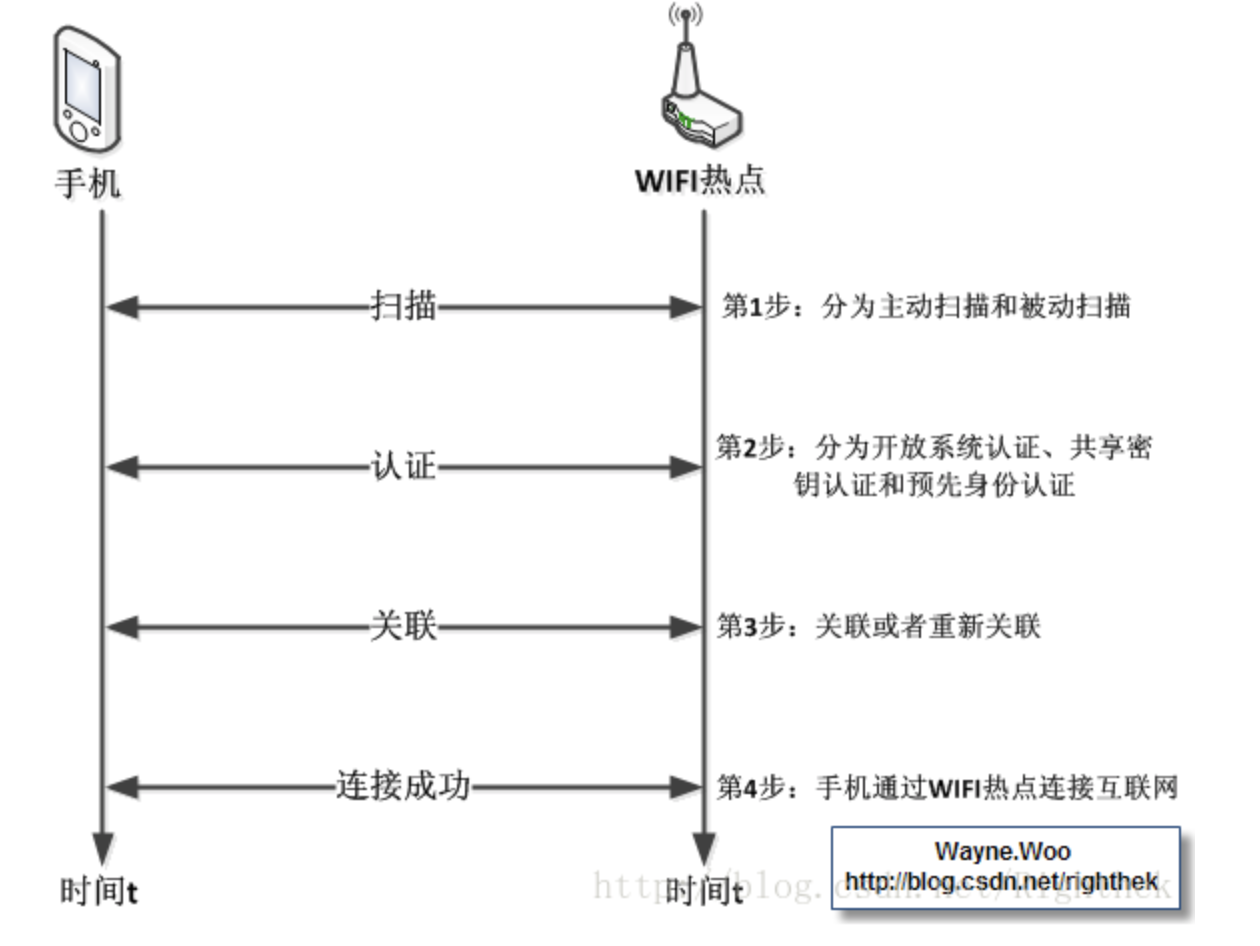
1. When using the WIFI function, our regular operation is to open the WIFI device on the mobile phone, search for the hotspot you want to connect, enter the password, and connect successfully. In fact, this process has corresponding professional terms, namely: Scanning, Authentication and Association. Here is a diagram to show this process.
2. Scanning purpose
Scanning is mainly to find a wireless network and then join the network.
3. Scanning classification
| pattern | describe |
| Active scanning | Scan by sending probe request. This mode is the default scanning mode. |
| Passive scanning | Do not send probe request. Jump to a specific channel and wait for beacon. Applications are available via WiFi_ scan_ config_ Scan in t_ The type field enables passive scanning. |
| Fast scan | In this mode, the scan is completed immediately after a matching AP is detected, even if the channel is not fully scanned. You can set the threshold of signal strength and select the required authentication mode provided by the AP. The Wi Fi driver will ignore APS that do not meet the standards. |
| Full channel scanning | The scanning will not end until all channels are scanned; The Wi Fi driver will store 4 perfectly matched APS. The sorting methods for APS include rssi and authmode. After scanning, the Wi Fi driver will select the most suitable AP according to the order. |
| Specific channel scanning | Scan only specific channels. wifi_ scan_ config_ When the channel field in t is 1-14, the current mode is specific channel scanning. |
| Front end scanning | When Wi Fi is not connected in station mode, front-end scanning can be performed. The Wi Fi driver determines whether to perform front-end scanning or back-end scanning, and the application cannot configure these two modes. |
| Back end scan | When Wi Fi is connected in station mode or station/AP coexistence mode, back-end scanning can be performed. The Wi Fi driver determines whether to perform front-end scanning or back-end scanning, and the application cannot configure these two modes. |
4. How to use
1) Initialize wifi environment
First, we need to initialize the WiFi subsystem by ourselves. When we write our own program, we need to call {esp_wifi_init (& config) method.
ESP_ERROR_CHECK(esp_netif_init()); ESP_ERROR_CHECK(esp_event_loop_create_default()); esp_netif_t *sta_netif = esp_netif_create_default_wifi_sta(); assert(sta_netif); wifi_init_config_t cfg = WIFI_INIT_CONFIG_DEFAULT(); ESP_ERROR_CHECK(esp_wifi_init(&cfg));
2) Set operation mode
You can call the function esp_wifi_set_mode(). The scanning needs to be completed in the "station" or "station/softap" coexistence mode. At the same time, we can also call "ESP"_ wifi_ get_ Mode () to retrieve our current mode.
ESP_ERROR_CHECK(esp_wifi_set_mode(WIFI_MODE_STA));
3) Start scanning
ESP_ERROR_CHECK(esp_wifi_start()); esp_wifi_scan_start(NULL, true);
Call esp_wifi_scan_start(const wifi_scan_config_t *config, bool block) function to complete Wi Fi scanning function. At the same time, you can call this interface to set scanning type and other scanning attributes. The following table describes the structure WiFi in detail_ scan_ config_ Tfield information.
| field | field |
| ssid | If the value of this field is not NULL, only AP S with the same SSID value can be scanned |
| bssid | If the value of this field is not NULL, only AP S with the same BSSID value can be scanned |
| channel | If the field value is 0, full channel scanning will be performed; Conversely, scanning will be performed for a specific channel. |
| show_hidden | If the field value is 0, the AP with hidden SSID will be ignored in this scan; Conversely, these APS will also be regarded as normal APS at the time of scanning |
| scan_type | If the field value is WIFI_SCAN_TYPE_ACTIVE, then this scan is active; Conversely, it will be regarded as passive scanning. |
| scan_time | This field is used to control the scanning time of each channel. During passive scanning, scan_ time. The passive field is responsible for specifying the scan time for each channel. During active scanning, the scanning time of each channel is shown in the following list. Where min stands for scan_time_active_min, Max stands for scan_time_active_max.
If you want to improve Wi Fi scanning performance, you can modify the above two parameters. |
4) Scan complete
After the request to start scanning is issued, we will be notified of scanning when {system_ EVENT_ SCAN_ When the done} event is released, we think the scan is complete.
After Wi Fi scanning, the scanning results will be stored in the dynamic memory allocated by ESP32. When we call esp_wifi_scan_get_ap_records(uint16_t *number, wifi_ap_record_t *ap_records), the stored AP information will be returned, and the internally allocated storage will also be released.
Scan records are included in Wi Fi_ ap_ record_ An example of t structure is as follows:
/** @brief Description of a WiFi AP */
typedef struct {
uint8_t bssid[6]; /**< MAC address of AP */
uint8_t ssid[33]; /**< SSID of AP */
uint8_t primary; /**< channel of AP */
wifi_second_chan_t second; /**< secondary channel of AP */
int8_t rssi; /**< signal strength of AP */
wifi_auth_mode_t authmode; /**< authmode of AP */
wifi_cipher_type_t pairwise_cipher; /**< pairwise cipher of AP */
wifi_cipher_type_t group_cipher; /**< group cipher of AP */
wifi_ant_t ant; /**< antenna used to receive beacon from AP */
uint32_t phy_11b:1; /**< bit: 0 flag to identify if 11b mode is enabled or not */
uint32_t phy_11g:1; /**< bit: 1 flag to identify if 11g mode is enabled or not */
uint32_t phy_11n:1; /**< bit: 2 flag to identify if 11n mode is enabled or not */
uint32_t phy_lr:1; /**< bit: 3 flag to identify if low rate is enabled or not */
uint32_t wps:1; /**< bit: 4 flag to identify if WPS is supported or not */
uint32_t ftm_responder:1; /**< bit: 5 flag to identify if FTM is supported in responder mode */
uint32_t ftm_initiator:1; /**< bit: 6 flag to identify if FTM is supported in initiator mode */
uint32_t reserved:25; /**< bit: 7..31 reserved */
wifi_country_t country; /**< country information of AP */
} wifi_ap_record_t;If we want to cancel the scan by ourselves before completing the scan, we can call esp_wifi_scan_stop() .
The number of AP scans can be through esp_ ERROR_ Check (esp_wifi_scan_get_ap_num (& ap_count)) interface.
5. Example operation
1) scan example
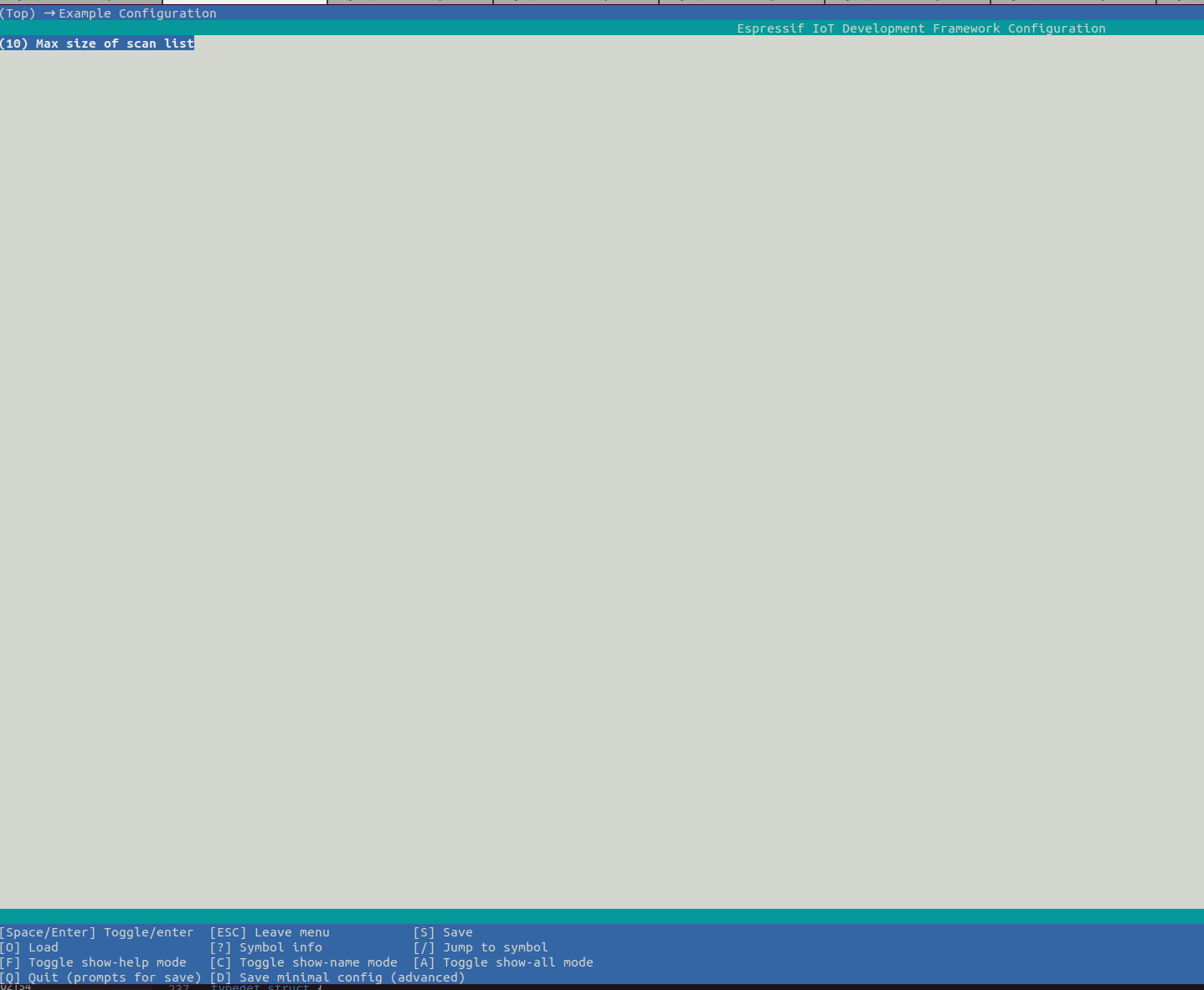
You can set and save ap data in menuconfig. The default setting is 10, and the maximum support is 20.
idf.py menuconfig---->Example Configuration---->(10)Max size of scan list
The operation results are as follows:
I (636) wifi_init: rx ba win: 6 I (636) wifi_init: tcpip mbox: 32 I (646) wifi_init: udp mbox: 6 I (646) wifi_init: tcp mbox: 6 I (646) wifi_init: tcp tx win: 5744 I (656) wifi_init: tcp rx win: 5744 I (656) wifi_init: tcp mss: 1440 I (666) wifi_init: WiFi IRAM OP enabled I (666) wifi_init: WiFi RX IRAM OP enabled I (676) phy_init: phy_version 4670,719f9f6,Feb 18 2021,17:07:07 I (786) wifi:mode : sta (30:ae:a4:10:85:60) I (786) wifi:enable tsf I (2886) scan: Total APs scanned = 72 I (2886) scan: SSID iot I (2886) scan: RSSI -25 I (2886) scan: Authmode WIFI_AUTH_WPA2_PSK I (2886) scan: Pairwise Cipher WIFI_CIPHER_TYPE_CCMP I (2896) scan: Group Cipher WIFI_CIPHER_TYPE_CCMP I (2896) scan: Channel 1 I (2906) scan: SSID cc2.4 I (2906) scan: RSSI -26 I (2906) scan: Authmode WIFI_AUTH_WPA_WPA2_PSK I (2916) scan: Pairwise Cipher WIFI_CIPHER_TYPE_CCMP I (2916) scan: Group Cipher WIFI_CIPHER_TYPE_CCMP I (2926) scan: Channel 1 I (2926) scan: SSID MERCURY_C6D4 I (2936) scan: RSSI -37 I (2936) scan: Authmode WIFI_AUTH_WPA_WPA2_PSK I (2946) scan: Pairwise Cipher WIFI_CIPHER_TYPE_CCMP I (2946) scan: Group Cipher WIFI_CIPHER_TYPE_CCMP I (2956) scan: Channel 1 I (2956) scan: SSID Huawei-jyf I (2956) scan: RSSI -38 I (2966) scan: Authmode WIFI_AUTH_WPA_WPA2_PSK I (2966) scan: Pairwise Cipher WIFI_CIPHER_TYPE_CCMP I (2976) scan: Group Cipher WIFI_CIPHER_TYPE_CCMP I (2976) scan: Channel 5 I (2986) scan: SSID cgh I (2986) scan: RSSI -41 I (2986) scan: Authmode WIFI_AUTH_WPA_WPA2_PSK I (2996) scan: Pairwise Cipher WIFI_CIPHER_TYPE_CCMP I (2996) scan: Group Cipher WIFI_CIPHER_TYPE_CCMP I (3006) scan: Channel 11 I (3006) scan: SSID myssid I (3016) scan: RSSI -45 I (3016) scan: Authmode WIFI_AUTH_WPA2_PSK I (3026) scan: Pairwise Cipher WIFI_CIPHER_TYPE_CCMP I (3026) scan: Group Cipher WIFI_CIPHER_TYPE_CCMP I (3036) scan: Channel 7 I (3036) scan: SSID xiaomi_2.4g I (3036) scan: RSSI -46 I (3046) scan: Authmode WIFI_AUTH_OPEN I (3046) scan: Pairwise Cipher WIFI_CIPHER_TYPE_NONE I (3056) scan: Group Cipher WIFI_CIPHER_TYPE_NONE I (3056) scan: Channel 2 I (3066) scan: SSID myap I (3066) scan: RSSI -49 I (3066) scan: Authmode WIFI_AUTH_WPA_WPA2_PSK I (3076) scan: Pairwise Cipher WIFI_CIPHER_TYPE_CCMP I (3076) scan: Group Cipher WIFI_CIPHER_TYPE_TKIP I (3086) scan: Channel 11 I (3086) scan: SSID 394 I (3096) scan: RSSI -51 I (3096) scan: Authmode WIFI_AUTH_OPEN I (3096) scan: Pairwise Cipher WIFI_CIPHER_TYPE_NONE I (3106) scan: Group Cipher WIFI_CIPHER_TYPE_NONE I (3116) scan: Channel 5 I (3116) scan: SSID TL-XDR1860_1 I (3116) scan: RSSI -52 I (3126) scan: Authmode WIFI_AUTH_WPA_WPA2_PSK I (3126) scan: Pairwise Cipher WIFI_CIPHER_TYPE_CCMP I (3136) scan: Group Cipher WIFI_CIPHER_TYPE_CCMP I (3136) scan: Channel 5
2) fast scan example
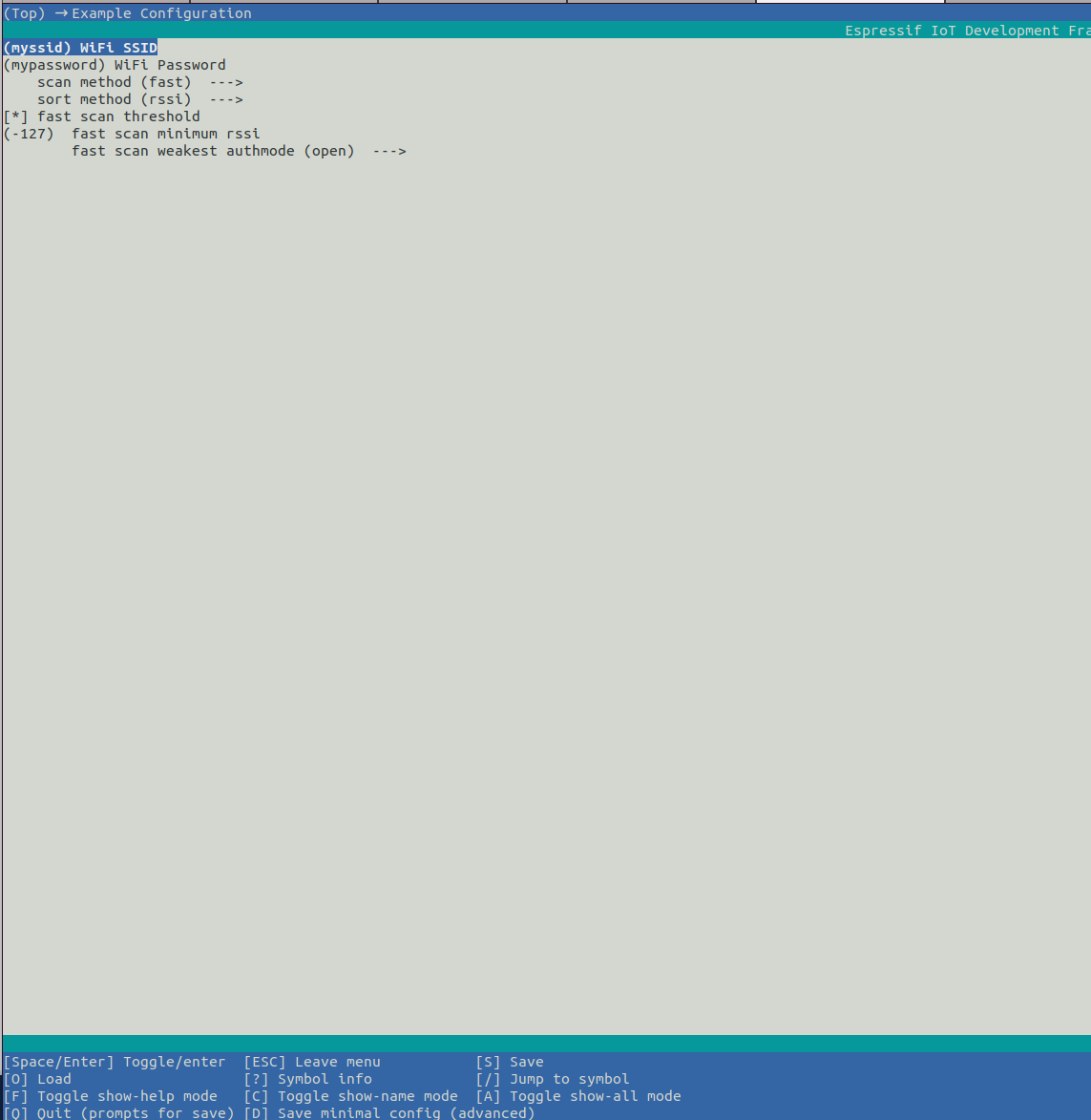
Fast scanning or full channel scanning can be configured in menuconfig.
idf.py menuconfig---->Example Configuration---->[*]fast scan threshold
The results of the quick scan run are as follows:
I (635) wifi_init: rx ba win: 6 I (635) wifi_init: tcpip mbox: 32 I (645) wifi_init: udp mbox: 6 I (645) wifi_init: tcp mbox: 6 I (645) wifi_init: tcp tx win: 5744 I (655) wifi_init: tcp rx win: 5744 I (655) wifi_init: tcp mss: 1440 I (665) wifi_init: WiFi IRAM OP enabled I (665) wifi_init: WiFi RX IRAM OP enabled I (765) phy_init: phy_version 4670,719f9f6,Feb 18 2021,17:07:07 I (865) wifi:mode : sta (30:ae:a4:10:85:60) I (865) wifi:enable tsf I (875) wifi:new:<1,0>, old:<1,0>, ap:<255,255>, sta:<1,0>, prof:8 I (1645) wifi:state: init -> auth (b0) I (1695) wifi:state: auth -> assoc (0) I (1725) wifi:state: assoc -> run (10) I (3795) wifi:connected with iot, aid = 58, channel 1, BW20, bssid = 30:a2:c2:70:27:88 I (3795) wifi:security: WPA2-PSK, phy: bgn, rssi: -25 I (3815) wifi:pm start, type: 1 I (3815) wifi:AP's beacon interval = 102400 us, DTIM period = 1 I (4565) scan: got ip:192.168.3.17 I (4565) esp_netif_handlers: sta ip: 192.168.3.17, mask: 255.255.255.0, gw: 192.168.3.1
Full channel scanning
I (786) wifi:mode : sta (30:ae:a4:10:85:60) I (796) wifi:enable tsf I (806) wifi:new:<1,0>, old:<1,0>, ap:<255,255>, sta:<1,0>, prof:8 I (806) wifi:state: init -> auth (b0) I (826) wifi:state: auth -> assoc (0) I (826) wifi:state: assoc -> init (3a0) I (826) wifi:new:<1,0>, old:<1,0>, ap:<255,255>, sta:<1,0>, prof:8 I (2886) wifi:new:<1,0>, old:<1,0>, ap:<255,255>, sta:<1,0>, prof:8 I (2886) wifi:state: init -> auth (b0) I (2896) wifi:state: auth -> assoc (0) I (2906) wifi:state: assoc -> run (10) I (3006) wifi:connected with iot, aid = 60, channel 1, BW20, bssid = 30:a2:c2:70:27:88 I (3006) wifi:security: WPA2-PSK, phy: bgn, rssi: -25 I (3006) wifi:pm start, type: 1 I (3076) wifi:AP's beacon interval = 102400 us, DTIM period = 1 I (4066) scan: got ip:192.168.3.17 I (4066) esp_netif_handlers: sta ip: 192.168.3.17, mask: 255.255.255.0, gw: 192.168.3.1