introduction:
After entering the intranet, it is a point-to-line and then face-to-face test. First, find out the current machine situation, such as the role in the domain and the services provided; Then use this as a springboard to collect information from other machines. When enough information is collected, the higher the possibility of winning domain control.
Native information collection
In order to perform subsequent operations such as raising rights, you must first obtain the permissions of the current machine as much as possible, so it is also necessary to collect information about the current machine.
View system configuration information
systeminfo can view the system information, but there are too many contents. At some time, the returned results cannot be seen through tools such as kitchen knife. You can output the contents to a file or query the specified contents in combination with findstr, such as querying the information of the operating system, i.e. software. systeminfo | findstr /B /C:"OS"
There are many input contents in this instruction. In addition to using finder to select output, some information can be displayed separately with other instructions, such as echo% processor_ Architecture% view the system architecture, and net statistics workstation view the system startup time
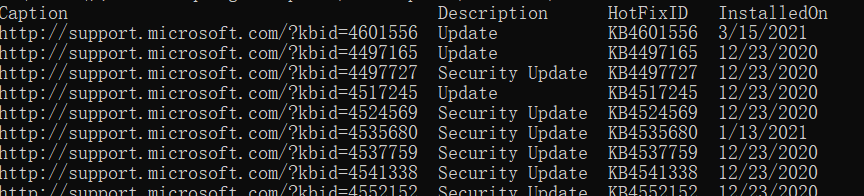
The patch information can be obtained using wmic QFE get caption, description, hotfix ID and installedon
Wmic extends WMI (Windows Management Instrumentation) and provides support for system management from command line interface and batch command script. Sometimes the data found in cmd is incomplete, such as the pid of some processes. At this time, wmic can be used for operation. Wmic provides a large number of global switches, aliases, verbs, commands and rich command lines to help enhance the user interface.
wmic product get name,version, and view the software version installed in the system.
Wmic / node: localhost / namespace: \ \ root \ securitycenter2 path antivirus product get displayName / format: List
In addition to the first time, you can also use netsh firewall show config and netsh advfirewall firewall show config to view the firewall configuration information
View system service information
wmic startup get command,caption to view the startup program information
wmic service list brief to query local service information
You can also use tasklist to query process information
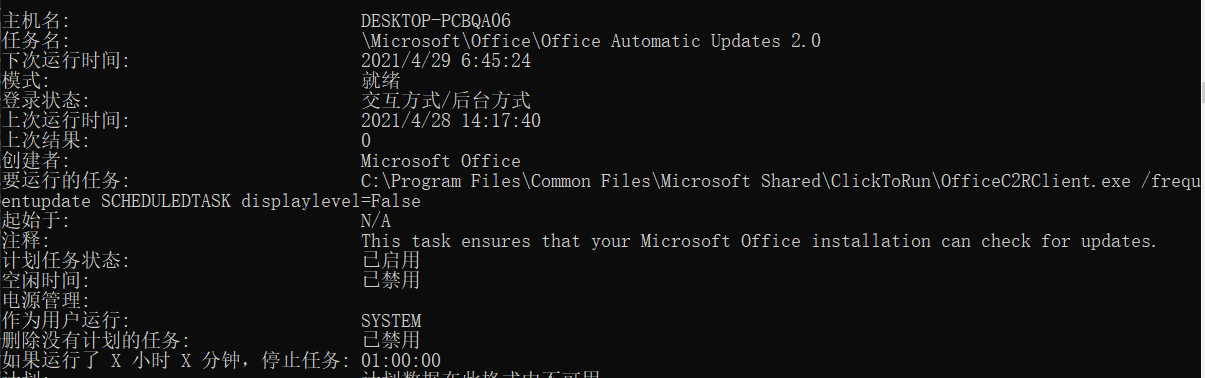
schtasks /query /fo LIST /V to view scheduled tasks
netstat -ano view port list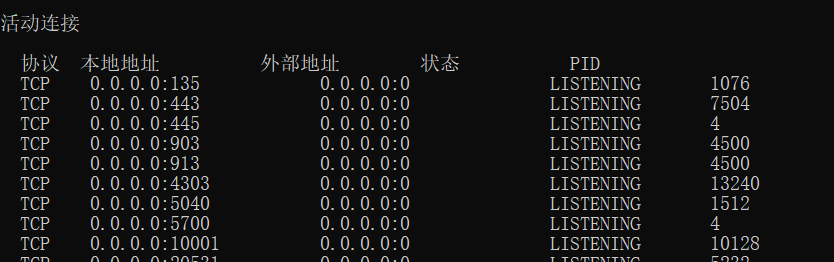
Note: generally, check the process port, first check the process pid, and then check the port according to the pid
Process of common anti-virus software
Process ----------- software name
360 antivirus: 360sd EXE
360 real time protection: 360tray EXE
360 active defense: zhudongfangyu EXE
Jinshan guard: ksafetray EXE
Server dongle: safedogupdatecenter EXE
McAfee antivirus software: McAfee mcshield EXE
NOD32: EGUI.EXE
Kaspersky: AVP EXE
Little red umbrella: avguard EXE
BITDEFENDER: BDAGENT.EXE
View system login information
query user, the user information logged in to the system
net session, which lists the connection session information, but generally requires high permissions to execute
Automatic information collection
Many post penetration modules can collect information. I won't talk about it here. I'll share a whoring script
for /f "delims=" %%A in ('dir /s /b %WINDIR%\system32\*htable.xsl') do set "var=%%A"
wmic process get CSName,Description,ExecutablePath,ProcessId /format:"%var%" >> out.html
wmic service get Caption,Name,PathName,ServiceType,Started,StartMode,StartName /format:"%var%" >> out.html
wmic USERACCOUNT list full /format:"%var%" >> out.html
wmic group list full /format:"%var%" >> out.html
wmic nicconfig where IPEnabled='true' get Caption,DefaultIPGateway,Description,DHCPEnabled,DHCPServer,IPAddress,IPSubnet,MACAddress /format:"%var%" >> out.html
wmic volume get Label,DeviceID,DriveLetter,FileSystem,Capacity,FreeSpace /format:"%var%" >> out.html
wmic netuse list full /format:"%var%" >> out.html
wmic qfe get Caption,Description,HotFixID,InstalledOn /format:"%var%" >> out.html
wmic startup get Caption,Command,Location,User /format:"%var%" >> out.html
wmic PRODUCT get Description,InstallDate,InstallLocation,PackageCache,Vendor,Version /format:"%var%" >> out.html
wmic os get name,version,InstallDate,LastBootUpTime,LocalDateTime,Manufacturer,RegisteredUser,ServicePackMajorVersion,SystemDirectory /format:"%var%" >> out.html
wmic Timezone get DaylightName,Description,StandardName /format:"%var%" >> out.html
Copy as bat file and the result is out Html is saved in the root directory of Disk c, and the name and path can be modified by yourself.
Intra domain information collection
Determine whether a domain exists
whoami, if the current account is a domain user, the returned result is usually domain name \ user name
ipconfig. If it is a dual network card, there is usually an intranet
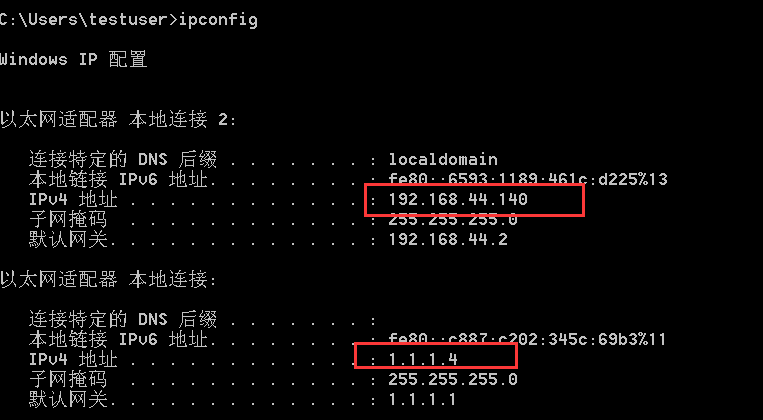
systeminfo, if in the domain, as shown in the figure; otherwise, it is workgroup
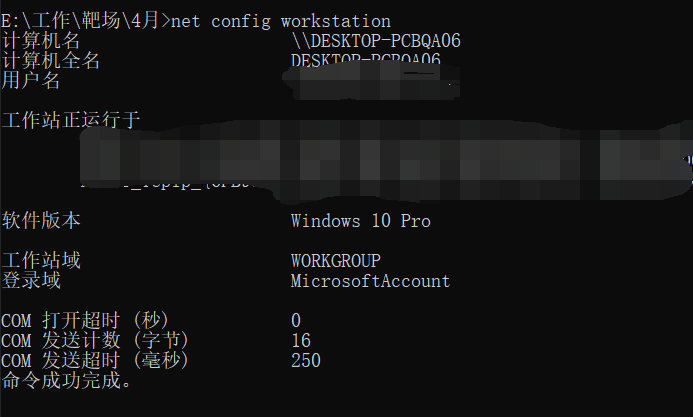
net config workstation. In the domain, the full computer name is usually the computer name domain name
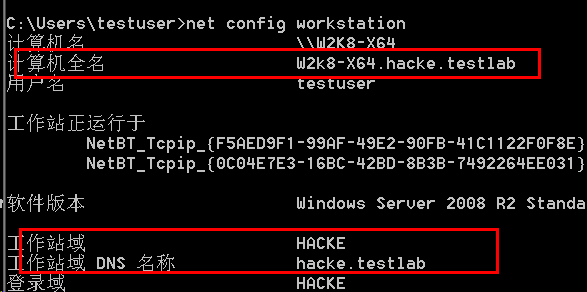
Not in the domain, as shown in the figure below
net time /domain to view the time server. The dns server and time server of the machine in the domain are usually domain controllers. The following figure shows that there is a domain and the current login user is a domain user
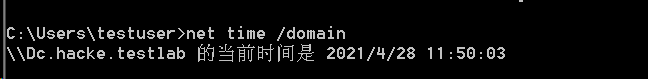
The following figure shows that it is not in the domain
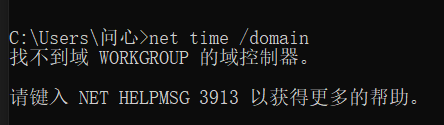
The following figure shows that the user is in the domain, but the current user is not a domain user
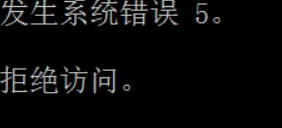
In addition, you can see other contents when collecting, such as system information, user information, etc
Probe domain memory host & Port
The easiest tool to think of for detecting surviving hosts and ports is nmap. However, this tool is too large and there are risks in direct installation. Port forwarding is limited by the network environment. Other methods are selected here
powershell
powershell can provide powerful assistance in penetration. Remember to modify the ip address when using the following scripts
Scan survival ip, top 1 255 is segment d of the ip address, and the final range is 192.168.0.1-255. The judgment and modification methods are the same below
1..255 | % {echo "192.168.0.$_"; ping -n 1 -w 100 192.168.0.$_} | Select-String ttl
Judge the host type according to the ttl value. The range is 192.168.0.1-255
1..255 | % {echo "192.168.0.$_"; ping -n 1 -w 100 192.168.0.$_} | Select-String ttl |% { if ($_ -match "ms") { $ttl = $_.line.split('=')[2] -as [int]; if ($ttl -lt 65) { $os = "linux"} elseif ($ttl -gt 64 -And $ttl -lt 129) { $os = "windows"} else {$os = "cisco"}; write-host "192.168.0.$_ OS:$os" ; echo "192.168.0.$_" >> scan_results.txt }}
Scan port
24..25 | % {echo ((new-object Net.Sockets.TcpClient).Connect("192.168.1.119",$_)) "Port $_ is open!"} 2>$null
24..25 |% {echo "$_ is "; Test-NetConnection -Port $_ -InformationLevel "Quiet" 192.168.1.119}2>null
Scan the ip address of the specified port
foreach ($ip in 1..20) {Test-NetConnection -Port 80 -InformationLevel "Detailed" 192.168.0.$ip}
arp scan
In Intranet, mac address is usually used for machine search, which can be realized by arp protocol
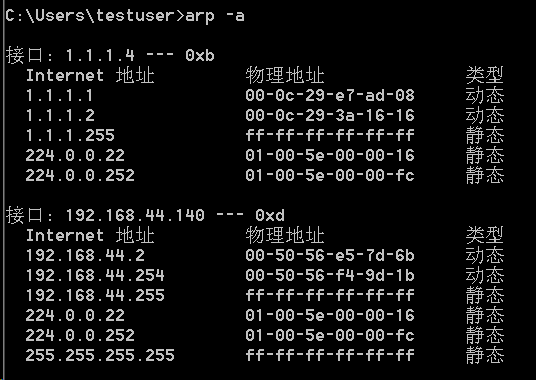
Gadgets
Many installation free gadgets can also be scanned, such as nbtscan, which can be directly sent to the target server for operation. The tool download address is: http://www.unixwiz.net/tools/nbtscan.html , usage: nbtscan Exe network segment. For more usage, refer to: nbgtscam exe /?
The meaning is as follows:
|Token | meaning|
|-|-|
SHARING | the file and print SHARING service running on the machine, but this does not necessarily have content SHARING
DC | the machine may be a Windows NT domain controller, whether it is a primary domain or a secondary domain.
U=user | the machine may have a login user with the specified name
IIS | the machine may have Microsoft's Internet information server (IIS) installed
EXCHANGE | the machine may have Microsoft Exchange installed
NOTES | Lotus Notes e-mail client may be installed on a single machine
? | NETBIOS resource not recognized
telnet
telnet is commonly used to establish a connection with the server and also to detect whether the port is open
Usage: telnet host port, such as telnet dc 3389. Note: not all machines have this service installed.
View user & Machine & session related information
View machine related information
net view /domain to query the domain information and determine the domain joined by the current machine
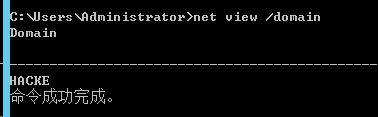
net view /domain: domain name to query all hosts in the domain
In the domain, there is a vital machine called domain controller, which is called domain controller for short. The machine name is usually DC. In the actual environment, the domain controller is one active and one standby.
netdom query pdc to view the domain controller name 
View user related information
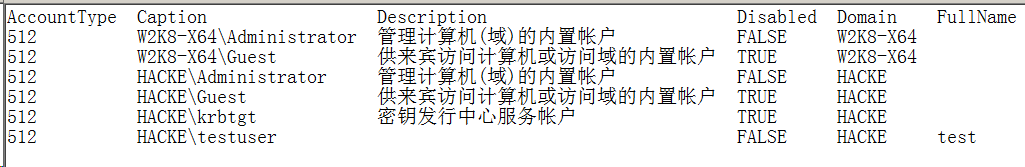
Net user queries all users of the current machine, and net user /domain views domain users
net user name to view the user information in the current machine
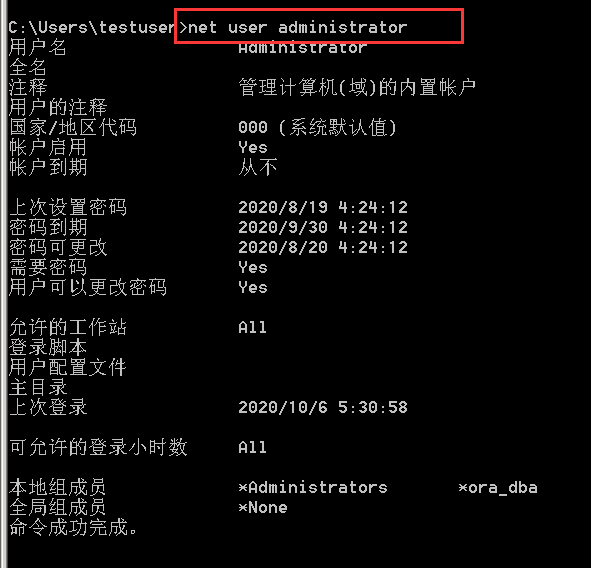
net user user name / domain view the domain user information in the current machine
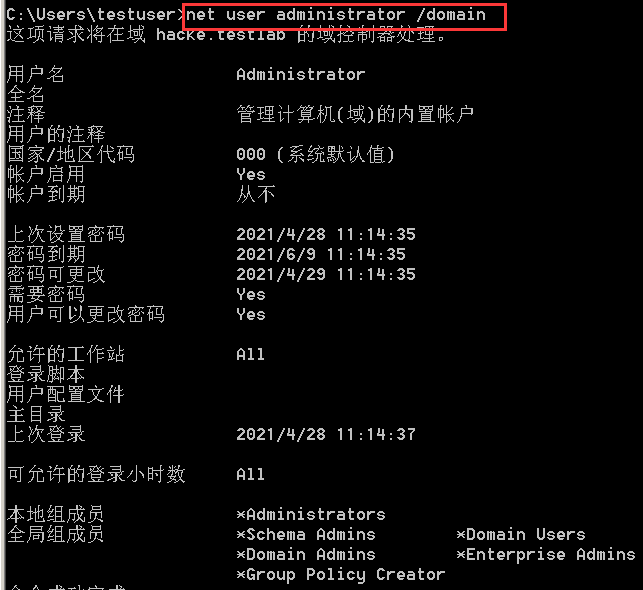
Note the differences between the above results. In addition, net user localgroup,net user localgroup /domain and net group /domain are also different
wmic useraccount get /all to get the details of users in the domain