Reference articles: Log analysis tool LogParser learning notes_ Memetali_ss blog - CSDN blog I didn't see it until I finished. Vomited
0x01 basic settings
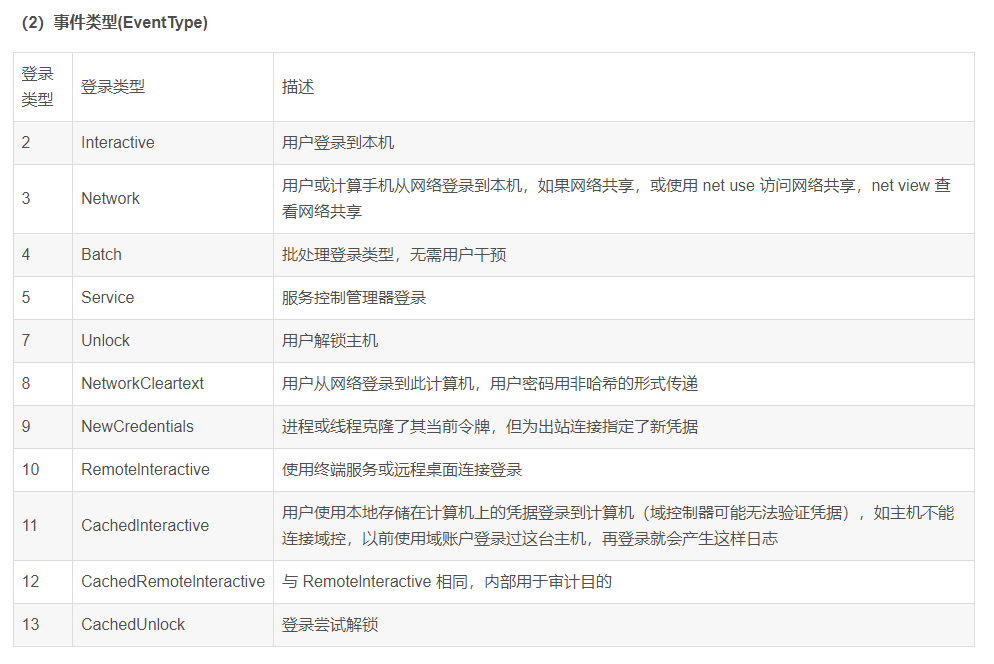
Event ID and common scenarios
For Windows event log analysis, different event IDS represent different meanings. Extract the description of some common security events.
4624 --Login succeeded 4625 --Login failed 4634 -- Logout succeeded 4647 -- User initiated logoff 4672 -- Log in using a superuser (such as an administrator) System: 1074,Through this event ID Check the startup, shutdown and restart time of the computer, as well as the reasons and comments. 6005,Indicates that the computer log service has started, if an event occurs ID If it is 6005, it indicates that the system is started normally on this day. 104,This time ID Record all audit log clearing events. This event occurs when a log is cleared ID. Safety: 4624,This event ID It refers to the user who has successfully logged in, which is used to filter the user login success of the system. 4625,This event ID Indicates the user whose login failed. 4720,4722,4723,4724,4725,4726,4738,4740,event ID Indicates the event record when the user account is created, deleted or changed. 4727,4737,4739,4762,event ID This event is generated when a user group is added, deleted, or a member is added to the group.
For example:
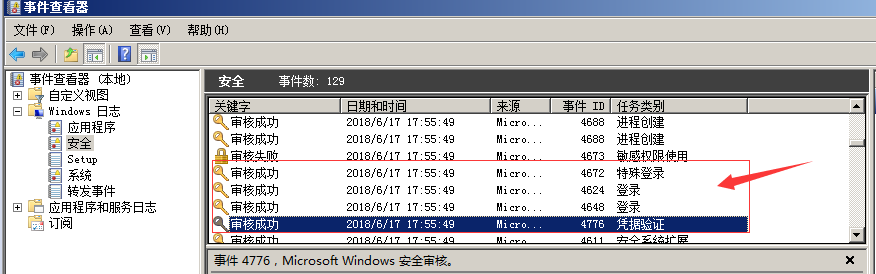
1. Administrator login
When using mstsc to remotely log in to a host, if the account used is an administrator account, an event with ID S 4776, 4648, 4624 and 4672 will be generated if successful.
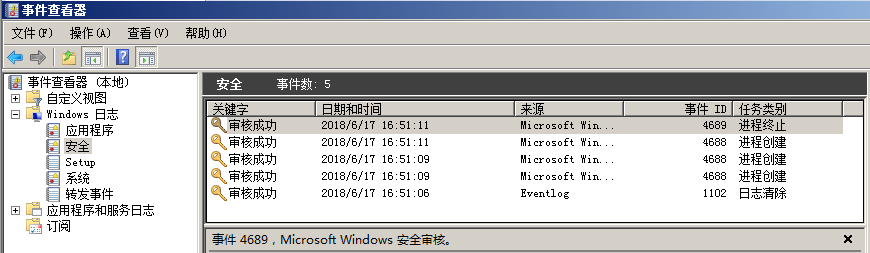
2. Execute system commands
Open Win+R, enter "CMD", enter "ipconfig", and the log process is as follows:
Process creation C: \ windows \ system32 \ CMD exe
Process creation C: \ windows \ system32 \ ipconfig exe
Process termination C: \ windows \ system32 \ ipconfig exe
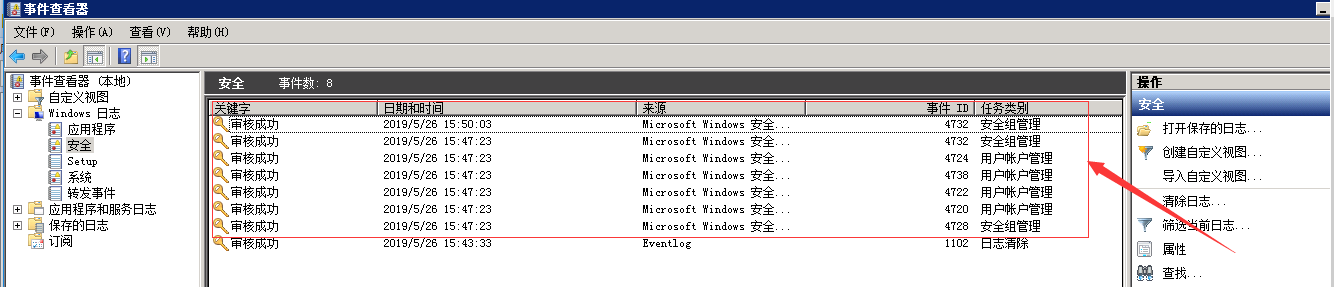
3. In the process of intrusion authorization, the following two statements are often used. What kind of log will be formed?
net user USER PASSWORD /add net localgroup administrators USER /add
0x02 log analysis tool
2.1. Log Parser 2.2 download address
https://www.microsoft.com/en-us/download/details.aspx?id=24659
The log of Log Parser can be queried through SQL.
2.1.1 sql fields
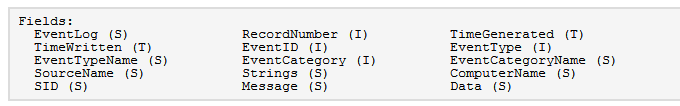
S: String array
Call format:
EXTRACT_TOKEN(EventTypeName, 0, ' ') ) EventTypeName:Field name 0: Sequence, starting from 0 "|": Separator
T: Time. Time class
I: intger. Integer class
Both T and I are called directly:
SELECT TO_DATE(TimeGenerated), TO_UPPERCASE( EXTRACT_TOKEN(EventTypeName, 0, ' ') ), SourceName FROM System TimeGenerated
2.1.2 field interpretation
RecordNumber: the log record number starts from 0
TimeGenerated: event generation time
TimeWritten: event logging time
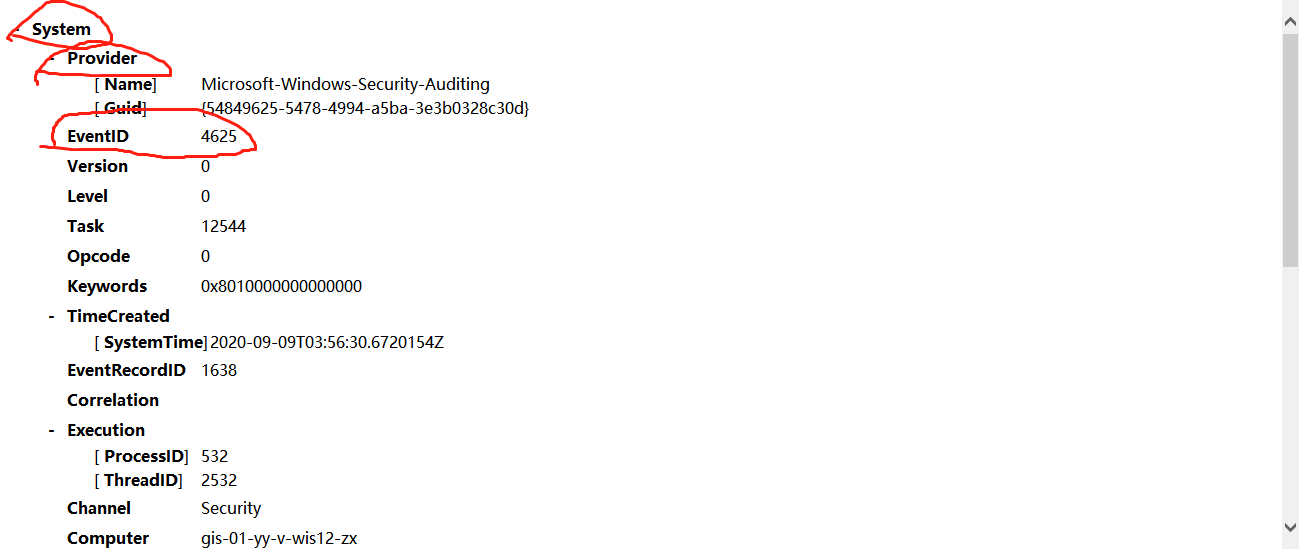
EventID: event ID

EventType: event type
EventCategory: I don't understand. reference resources Windows API ReportEvent write system log - jqdy - blog Garden
String:
Meaning of each location:
0 security IP(SID) 1 Account name 2 Account domain 3 Sign in ID 4 security ID 5 Account name 6 Account domain 7 Sign in ID 8 Login type 9 Login process 10 Authentication packet 11 Network account name 12 account number GUID 13 Network account domain 14 Packet name 15 Key length 16 process ID 17 Process path 18 Source network address 19 Source port 20 Simulation level 21 22 23 24 Virtual account 25 26 Promoted token
EventLog:
Meaning of each location:
0 File absolute path
EventTypeName
Meaning of each location:
0 Audit succeeded/Audit failed
SourceName: source
Meaning of each location:
0: Source location eg: Microsoft-Windows-Security-Auditing
SID: the view result is empty
Message: message
Meaning of each location:
0 The description for Event ID 4625 in Source "Microsoft-Windows-Security-Auditing" cannot be found. The local computer may not have the necessary registry information or message DLL files to display messages from a remote compute
Data: all empty
ComputerName: computer name
0 WIN-L5ST0VQ25FA Computer name
EventCategoryName
0 The name for category 12544 in Source "Microsoft-Windows-Security-Auditing" cannot be found. The local computer may not have the necessary registry information or message DLL files to display messages from a remote computer
The main fields are: TimeGenerated: event generation time; EventID: event ID; EventType: event type; String: EventLog; ComputerName: computer name
2.1.3 command composition
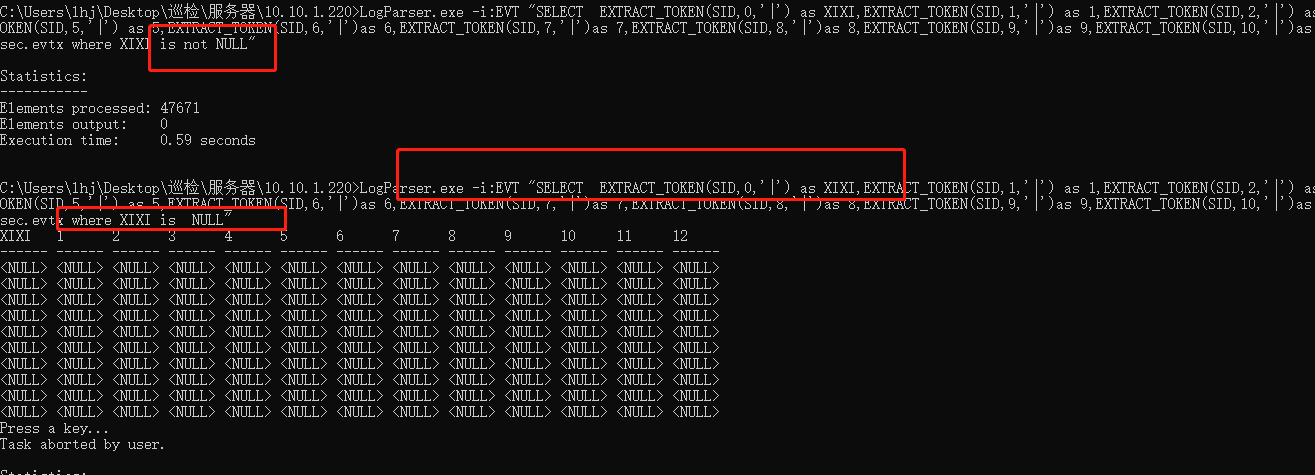
Basic format: logparser -i: input file format [- input file parameters] - o: output file format [- output format parameters] "SQL query statement"
LogParser.exe -i:EVT "SELECT EventID as EventID,TimeGenerated as LoginTime,EXTRACT_TOKEN(Strings,5,'|') as username,EXTRACT_TOKEN(Strings,19,'|') as ip FROM C:\Users\172.16.5.30\sec.evtx where EventID=4625"
EventID: the value is the EventID under the System node;
TimeGenerated: this value is similar to EventID, time
EXTRACT_TOKEN(Strings,5, '|'): the value is the value of the sixth part of the EventData part and the value of TargetUserName.
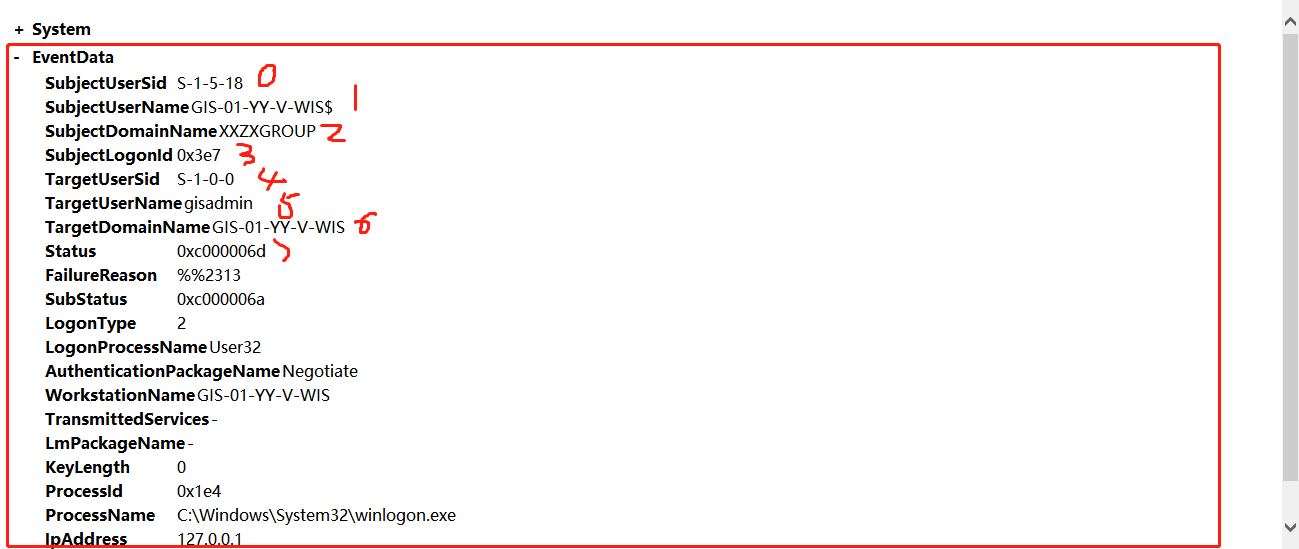
2.1.1. Common commands
1. Administrator login time and login user name (login successful)
LogParser.exe -i:EVT "SELECT TimeGenerated as LoginTime,EXTRACT_TOKEN(Strings,5,'|') as username FROM c:\11.evtx where EventID=4624"

2. View the record of (login failure)
LogParser.exe -i:EVT "SELECT TimeGenerated as LoginTime,EXTRACT_TOKEN(Strings,5,'|') as username FROM c:\11.evtx where EventID=4625"
3. User name and blasting times used by RDP blasting
To be continued..