Remote video surveillance
The Internet of things has been unknowingly integrated into our life and brought convenience to us. For example, smart door locks, ETC electronic automatic charging system, ETC. at first, it felt very novel, and now it is used to it.
It can even be said that the Internet of things is the inevitable trend of Internet development, especially now 5G provides necessary support. Moreover, many large domestic companies have begun to layout the Internet of things. For example, the well-known Xiaomi smart home; There are also cloud computing enterprises and Internet giants: Alibaba cloud and Tencent cloud, which have invested a lot of manpower and capital to layout the Internet of things industry.
When business opportunities come, naturally there is more demand for talents. Especially in recent years, many large factories have been recruiting Iot talents. Technicians interested in this field should seize the opportunity.
Industry demand
Campus video surveillance
Enterprise production environment video monitoring
Community video surveillance

Road video surveillance
1. Effect demonstration
Demonstrate the whole process of remote monitoring
2. Principle analysis
Communication + video transmission
Important: if it is determined that the data transmission of one frame is completed
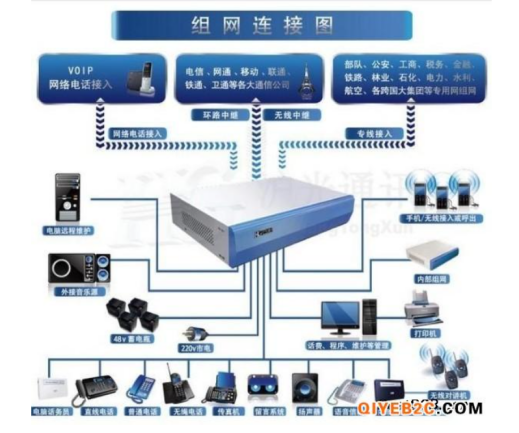
System framework
3. Background knowledge
Network Communications
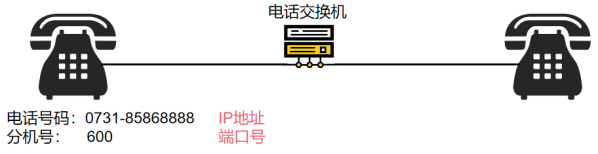
Does the beacon tower count?

Does earth phone count?

Network Communications
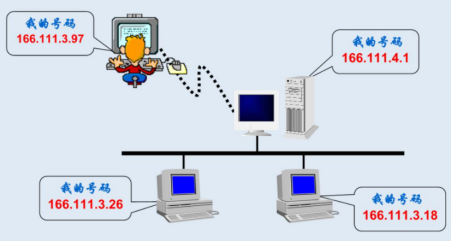
IP address
The most commonly used IP address: "192.168.1.1"
What is "the same segment"? (is it on the same LAN)
Are these four addresses the same "network segment"?
If the subnet mask is 255.255.0.0, the above four addresses are in the same network segment
If the subnet mask is 255.255.255.0
IP addresses are divided into:
Network address + host address in the network
166.111.3.26
255.255.255.0
11111111.11111111.11111111.00000000
Why are many network addresses 192.168 xxx. xxx
Subnet mask:
It is used to distinguish the length of network address and host address
The most commonly used subnet mask: 255.255.255.0
Port number
The port number is "ask what service you need in the same place"

Most commonly used port number:
Port 80 - WEB Service
www.baidu.com That's it www.baidu.com:80
TCP/UDP
Who is TCP and who is UDP?

TCP: exclusive channel, high-end customization, exclusive access in the whole process
UDP: the route of each data is temporarily determined. The sending order and arrival order may be inconsistent and packet loss may occur
socket
socket
[IP + port number] is combined into a "socket", which is a socket
Use socket to send / receive data
4. Code implementation
Implementation of monitoring terminal
1. Project preparation
Any version of VS/VC + +
2. Create project
Create an empty project.
3. Project framework
#include <stdio.h>
#include <graphics. h> / / easy graphics library qt
#define FILE_NAME "jian_kong.jpg"
void receiveImg(const char* fileName) {
}
bool cmdJianKong() {
return false;
}
bool init() {
return false;
}
void connect() {
}
int main(void) {
if (!init()) {
printf("Network initialization failed!\n");
return -1;
}
connect(); // Connect the monitored end
while (1) {
if (!cmdJianKong()) { // Send monitoring command
break;
}
receiveImg(FILE_NAME);
loadimage(0, FILE_NAME);
Sleep(10);
}
return 0;
}4. Network protocol initialization
#include <stdio.h>
#include <winsock2.h>
#pragma comment (lib, "WS2_32.lib")
#include <graphics. h> / / easy graphics library qt
bool init() {
WSADATA wsaData;
int err = WSAStartup(MAKEWORD(1, 1), &wsaData);
if (err != 0) {
return false;
}
return true;
}Special attention:
#include <winsock2. h> Must be placed in #include < graphics h> Before!
5. Initialization of network socket and network address
sockaddr_in sockAddr; //network address
SOCKET serverSocket; // network sockets
#define JIAN_KONG_IP "127.0.0.1"
#define JIAN_KONG_PORT 2021
bool init() {
WSADATA wsaData;
int err = WSAStartup(MAKEWORD(1, 1), &wsaData);
if (err != 0) {
return false;
}
serverSocket = socket(PF_INET, SOCK_STREAM, IPPROTO_TCP);
sockAddr.sin_family = PF_INET;
sockAddr.sin_addr.S_un.S_addr = inet_addr(JIAN_KONG_IP);
sockAddr.sin_port = htons(JIAN_KONG_PORT);
return true;
}
6. Create monitoring window
bool init() {
......
//Create monitoring window
initgraph(640, 480);
return true;
}7. Connect the monitoring terminal
void connect() {
// Connect the monitored end (initiate network connection)
connect(serverSocket, (SOCKADDR*)&sockAddr, sizeof(sockAddr));
}8. Send monitoring instructions
#define CMD_JIAN_KONG "jian_kong"
bool cmdJianKong() {
// Send monitoring instructions
char buff[] = CMD_JIAN_KONG;
int ret = send(serverSocket, buff, strlen(buff) + 1, 0);
return ret > 0;
}9. Receive one frame of data
void receiveImg(const char* fileName) {
int len;
// Accept the length of the photo first
recv(serverSocket, (char*)&len, 4, NULL);
char buff[4096];
FILE* file = fopen(fileName, "wb");
int count = 0;
while (1) {
int ret = recv(serverSocket, buff, sizeof(buff), NULL);
if (ret < 0) {
printf("Acceptance failure!\n");
break;
}
else if (ret == 0) {
printf("Opposite end closing\n");
break;
}
else {
printf("Received %d byte\n", ret);
// Save the received data in the file!!!
fwrite(buff, ret, 1, file);
}
count = count + ret;
if (count == len) {
break;
}
}
fclose(file);
}So far! The monitoring end has been set up. Next, let's implement the "monitored end"
Source code data acquisition method:
After following + forwarding, the private key word [data] can be obtained!
Note: you can only send private messages after paying attention to me
After following + forwarding, the private key word [data] can obtain courseware, code, source code, video, etc
Say important things three times, forward, forward, and then send a private message before you can get it!