1. narration
There are many encryption algorithm classes under the java security package, and we can simply call them. Although they have complete functions, they are a little cumbersome to use. I encapsulate some common encryption algorithms and their common methods here to simplify the code.
The structure of tool class is as follows:
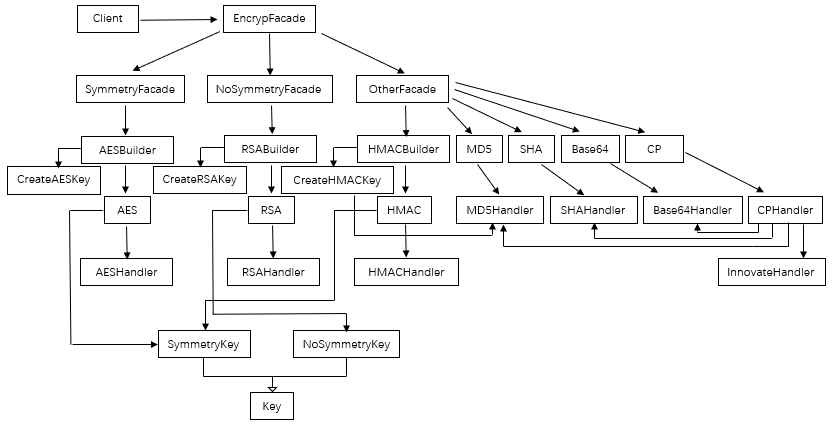
Call step:
1. The client is the calling class, calling the encrypfacade uniformly. Through the corresponding method of encrypting the facade object, you can choose to build symmetric, asymmetric and other encrypted facade objects.
2. Symmetric encryption and asymmetric encryption need a key. During construction, the key is generated, and then the object is constructed (HMAC is special, which is a hash algorithm that needs public key encryption). These objects are constructed using the builder ending method in the facade object. Other encryption algorithms directly use the corresponding method of OtherFacade object to realize encryption and decryption. OtherFacade will call the method of specific encryption object according to the specific method, and these encryption objects will then call their respective handles.
3. use the builder method to get the encrypted object and then invoke specific methods to implement encryption and decryption. These methods are in the Handler that they call each other.
Advantage:
Although we generally don't use many encryption algorithms in development, members of each class do delay loading, and instance objects will be generated when calling, so we don't need to worry about class expansion. On the contrary, it is easier for us to expand it.
2. example
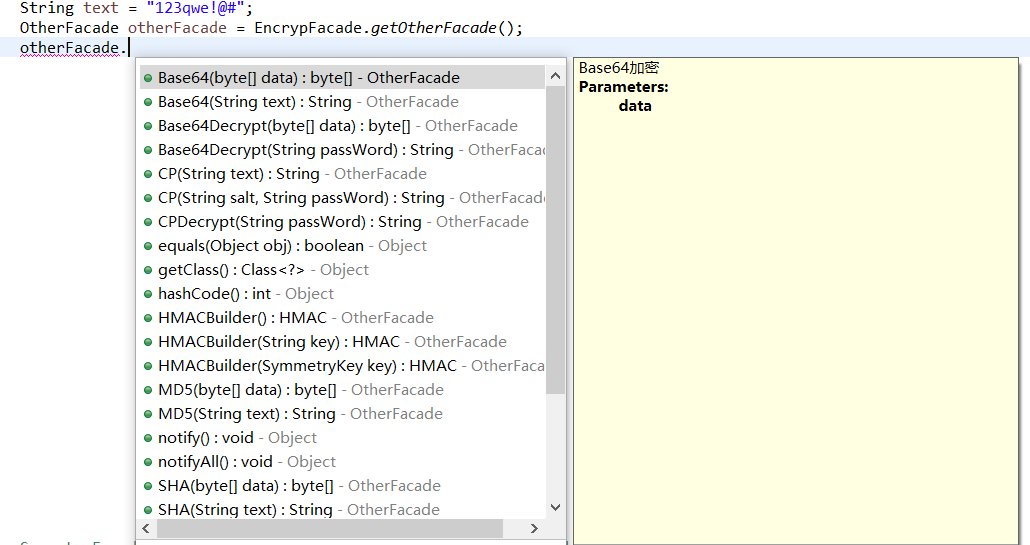
2.1 use of Base64
String text = "123qwe!@#"; OtherFacade otherFacade = EncrypFacade.getOtherFacade(); String base64 = otherFacade.Base64(text); System.out.println("base64 The encrypted ciphertext is:"+base64); String base64Decrypt = otherFacade.Base64Decrypt(base64); System.out.println("base64 The decrypted plaintext is:"+base64Decrypt);
byte[] data = "123qwe!@#".getBytes();
System.out.println("data: "+Arrays.toString(data));
OtherFacade otherFacade = EncrypFacade.getOtherFacade();
byte[] base64 = otherFacade.Base64(data);
System.out.println("Base64 The result of encrypted byte array is:"+Arrays.toString(base64));
byte[] base64Decrypt = otherFacade.Base64Decrypt(base64);
System.out.println("Base64 The result of decrypting byte array is:"+Arrays.toString(base64Decrypt));
Code 1:
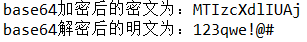
Code 2:
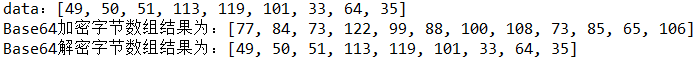
2.2 use of MD5
String text = "123qwe!@#"; OtherFacade otherFacade = EncrypFacade.getOtherFacade(); String md5 = otherFacade.MD5(text); System.out.println("md5 The encrypted ciphertext is:"+md5);
byte[] data = "123qwe!@#".getBytes();
System.out.println("data: "+Arrays.toString(data));
OtherFacade otherFacade = EncrypFacade.getOtherFacade();
byte[] md5 = otherFacade.MD5(data);
System.out.println("md5 The result of encrypted byte array is:"+Arrays.toString(md5));
Code 1:
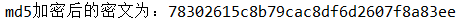
Code 2:
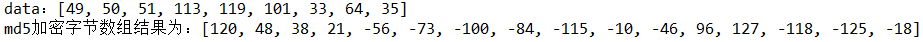
2.3 use of Sha
String text = "123qwe!@#"; OtherFacade otherFacade = EncrypFacade.getOtherFacade(); String sha = otherFacade.SHA(text); System.out.println("SHA The encrypted ciphertext is:"+sha);
byte[] data = "123qwe!@#".getBytes();
System.out.println("data: "+Arrays.toString(data));
OtherFacade otherFacade = EncrypFacade.getOtherFacade();
byte[] sha = otherFacade.SHA(data);
System.out.println("SHA The result of encrypted byte array is:"+Arrays.toString(sha));
Code 1:
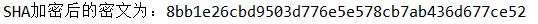
Code 2:
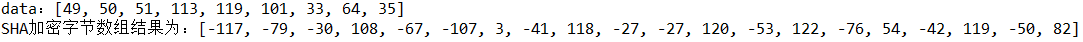
2.4 use of CP
This encryption algorithm is a self-made algorithm. It is actually a hybrid version of other encryption.
The following example is the CP encryption that can be decrypted. When encrypting, base64 is used first, and then innovate is used. When decrypting, innovate is the name that I start at will. As for this algorithm, I need it from Du Niang. And I did not disclose the innovative encryption algorithm in the facade object.
String text = "123qwe!@#"; OtherFacade otherFacade = EncrypFacade.getOtherFacade(); String cp = otherFacade.CP(text); System.out.println("CP The encrypted ciphertext is:"+cp); String cpDecrypt = otherFacade.CPDecrypt(cp); System.out.println("CP The decrypted plaintext is:"+cpDecrypt);
Result:

The following example is irreversible encryption. It uses four kinds of multiple encryption algorithms, MD5, Base64, SHA and innovate. The encryption order of these algorithms is determined by the salt value of the internal algorithm defined by the user. That is to say, the encrypted plaintext is the same, and the different salt value will lead to different ciphertext.
String text = "123qwe!@#"; String salt = "userName"; OtherFacade otherFacade = EncrypFacade.getOtherFacade(); String cp = otherFacade.CP(salt, text); System.out.println("CP The encrypted ciphertext is:"+cp);
Result:

2.5 use of HMAC
String text = "123qwe!@#"; OtherFacade otherFacade = EncrypFacade.getOtherFacade(); HMAC hmac1 = otherFacade.HMACBuilder(); SymmetryKey key = hmac1.getKey(); System.out.println("HMAC Generated key For:"+key.getPublicKey()); String encrypt1 = hmac1.Encrypt(text); System.out.println("A Use HMAC The encryption result is:"+encrypt1); //simulation A take key Pass to B HMAC hmac2 = otherFacade.HMACBuilder(key); //HMAC hmac2 = otherFacade.HMACBuilder(key.getPublicKey());//Ditto String encrypt2 = hmac2.Encrypt(text); System.out.println("B Use HMAC The encryption result is:"+encrypt2);
byte[] data = "123qwe!@#".getBytes(); System.out.println("data: "+Arrays.toString(data)); OtherFacade otherFacade = EncrypFacade.getOtherFacade(); HMAC hmac1 = otherFacade.HMACBuilder(); SymmetryKey key = hmac1.getKey(); System.out.println("HMAC Generated key For:"+key.getPublicKey()); byte[] encrypt1 = hmac1.Encrypt(data); System.out.println("A Use HMAC The result of encrypted byte array is:"+Arrays.toString(encrypt1)); //simulation A take key Pass to B HMAC hmac2 = otherFacade.HMACBuilder(key); //HMAC hmac2 = otherFacade.HMACBuilder(key.getPublicKey());//Ditto byte[] encrypt2 = hmac2.Encrypt(data); System.out.println("B Use HMAC The result of encrypted byte array is:"+Arrays.toString(encrypt2));
Code 1:

Code 2:
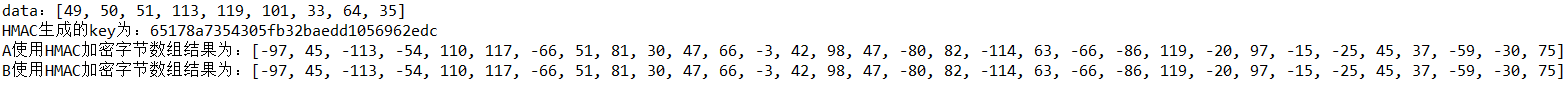
2.6 use of AES
String text = "123qwe!@#"; SymmetryFacade symmetryFacade = EncrypFacade.getSymmetryFacade(); AES aes1 = symmetryFacade.AESBuilder();
SymmetryKey key = aes1.getKey(); System.out.println("AES Generated key For:"+key.getPublicKey()); String encrypt = aes1.Encrypt(text); System.out.println("A Use AES The encryption result is:"+encrypt); //simulation A take key Pass to B AES aes2 = symmetryFacade.AESBuilder(key); //AES aes2 = symmetryFacade.AESBuilder(key.getPublicKey());//Ditto String decrypt = aes2.Decrypt(encrypt); System.out.println("B Use AES The decryption result is:"+decrypt);
byte[] data = "123qwe!@#".getBytes(); System.out.println("data: "+Arrays.toString(data)); SymmetryFacade symmetryFacade = EncrypFacade.getSymmetryFacade(); AES aes1 = symmetryFacade.AESBuilder(); SymmetryKey key = aes1.getKey(); System.out.println("AES Generated key For:"+key.getPublicKey()); byte[] encrypt = aes1.Encrypt(data); System.out.println("A Use AES The encryption result is:"+Arrays.toString(encrypt)); //simulation A take key Pass to B AES aes2 = symmetryFacade.AESBuilder(key); //AES aes2 = symmetryFacade.AESBuilder(key.getPublicKey());//Ditto byte[] decrypt = aes2.Decrypt(encrypt); System.out.println("B Use AES The decryption result is:"+Arrays.toString(decrypt));
Code 1:
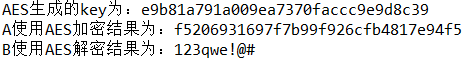
Code 2:

2.7 use of res
Let's first understand the process of digital signature and asymmetric encryption
1. Digital signature:
Digital signature is the simulation of handwriting signature, which is used to ensure the integrity of information transmission, identity authentication of sender, and prevent repudiation in transaction.
The basic idea of public key signature system is as follows:
① sender A encrypts the information with his private key to sign the file
② send the signed document to receiver B
③ B uses A's public key (which can be obtained from CA organization and other channels) to decrypt the file, so as to verify the signature.
2. Asymmetric encryption process
Encrypted communication is required between A and B. the asymmetric encryption process is as follows:
① both A and B need to generate A pair of encryption and decryption keys for encryption and decryption
(2) A generates A pair of keys and exposes the public key to other parties. Pass the public key to B and keep the private key. B transfers the public key to A and keeps the private key.
③ when A sends A message to B, it encrypts the message with B's public key, and then sends the ciphertext to B
④ when B receives the message from A, it decrypts it with its own private key
Note: A and B can only use their private key to encrypt any information encrypted by their public key.
String text = "123qwe!@#"; NoSymmetryFacade noSymmetryFacade = EncrypFacade.getNoSymmetryFacade(); //512 Is the length of the public key. Theoretically, the longer the length is, the harder it is to be cracked. If the parameter is not filled, the default value is 1024. If it is less than 512, the default value is used RSA res1 = noSymmetryFacade.RESBuilder(512); NoSymmetryKey key1 = res1.getKey(); RSA res2 = noSymmetryFacade.RESBuilder(512); NoSymmetryKey key2 = res2.getKey(); //exchange publicKey res1.setKey(key2); res2.setKey(key1); //res1.setKey(key2.getPublicKey());//Ditto //res2.setKey(key1.getPublicKey());//Ditto //A First use B And then use your own private key to encrypt String privateEncrypt = res1.privateEncrypt(res1.publicEncrypt(text)); //Generate signature String sign1 = res1.sign(privateEncrypt); System.out.println("A Of RSA The public key is:"+key1.getPublicKey()); System.out.println("B Of RSA The public key is:"+key2.getPublicKey()); System.out.println("A Of RSA The signature is:"+sign1); System.out.println("A Use RSA The encrypted data is:"+privateEncrypt); //B Get signature and encrypted data //First verify the signature to determine whether the data has been changed if(res2.verify(privateEncrypt, sign1)){ //Then decrypt //First use A Decrypt the public key of B Decrypt the private key of in the reverse order of encryption String publicDecrypt = res2.privateDecrypt(res2.publicDecrypt(privateEncrypt)); System.out.println("B Use RSA The decrypted data is:"+publicDecrypt); }
byte[] data = "123qwe!@#".getBytes(); System.out.println("data: "+Arrays.toString(data)); NoSymmetryFacade noSymmetryFacade = EncrypFacade.getNoSymmetryFacade(); //512 Is the length of the public key. Theoretically, the longer the length is, the harder it is to be cracked. If the parameter is not filled, the default value is 1024. If it is less than 512, the default value is used RSA res1 = noSymmetryFacade.RESBuilder(512); NoSymmetryKey key1 = res1.getKey(); RSA res2 = noSymmetryFacade.RESBuilder(512); NoSymmetryKey key2 = res2.getKey(); //exchange publicKey res1.setKey(key2); res2.setKey(key1); //res1.setKey(key2.getPublicKey());//Ditto //res2.setKey(key1.getPublicKey());//Ditto //A First use B And then use your own private key to encrypt byte[] privateEncrypt = res1.privateEncrypt(res1.publicEncrypt(data)); //Generate signature byte[] sign1 = res1.sign(privateEncrypt); System.out.println("A Of RSA The public key is:"+key1.getPublicKey()); System.out.println("B Of RSA The public key is:"+key2.getPublicKey()); System.out.println("A Of RSA The signature is:"+Arrays.toString(sign1)); System.out.println("A Use RSA The encrypted data is:"+Arrays.toString(privateEncrypt)); //B Get signature and encrypted data //First verify the signature to determine whether the data has been changed if(res2.verify(privateEncrypt, sign1)){ //Then decrypt //First use A Decrypt the public key of B Decrypt the private key of in the reverse order of encryption byte[] publicDecrypt = res2.privateDecrypt(res2.publicDecrypt(privateEncrypt)); System.out.println("B Use RSA The decrypted data is:"+Arrays.toString(publicDecrypt)); }
Code 1:

Code 2:

Download address: