Bored casually did a few questions
catalogue
It's no use being single for a hundred years
Hand speed of being single for 20 years
contradiction
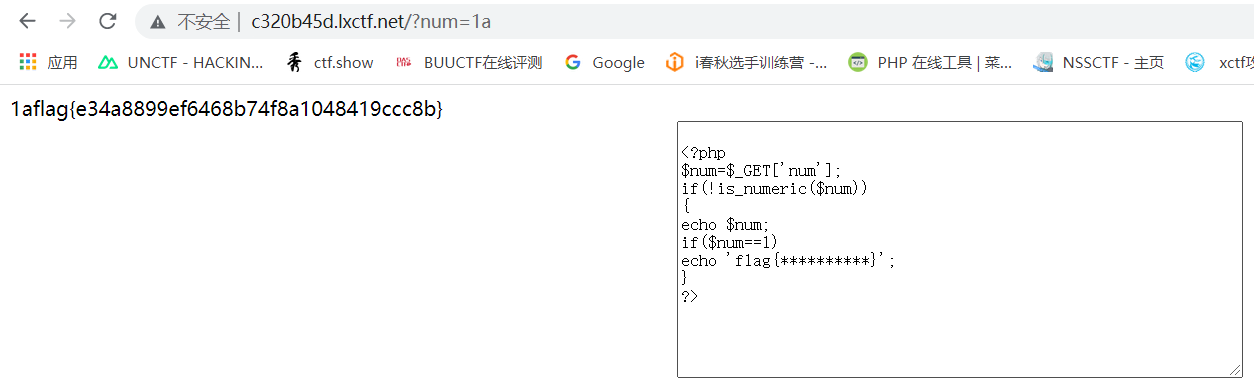
<?php
$num=$_GET['num'];
if(!is_numeric($num))
{
echo $num;
if($num==1)
echo 'flag{**********}';
}
?>If you normally give a string of code, you will feel a contradiction under normal thinking. The contradiction lies in the function is_numeric() needs num not to be an integer number. But num==1, this is a contradiction, and how to bypass it needs to be discussed.
Firstly, this is a weak comparison between num and 1, and the difference between weak comparison and strong comparison is:
When php compares numbers with strings or performs operations, php will first convert strings into numbers and then compare them.
The conversion rule of php is: if the string starts with a number, take the first number as the conversion result. If there is no number, take 0
When PHP compares a number with a string or performs an operation, PHP will convert the string into a number for comparison. The rule of PHP conversion is: if the string starts with a number, take the first number as the conversion result, and if not, output 0. In PHP, = = will perform type conversion first and then compare, while = = = will compare types first. If the types are different, it will directly return false.
According to the above conversion method of weak comparison, the payload is constructed as? num=1 + other characters can be bypassed.
It's no use being single for a hundred years
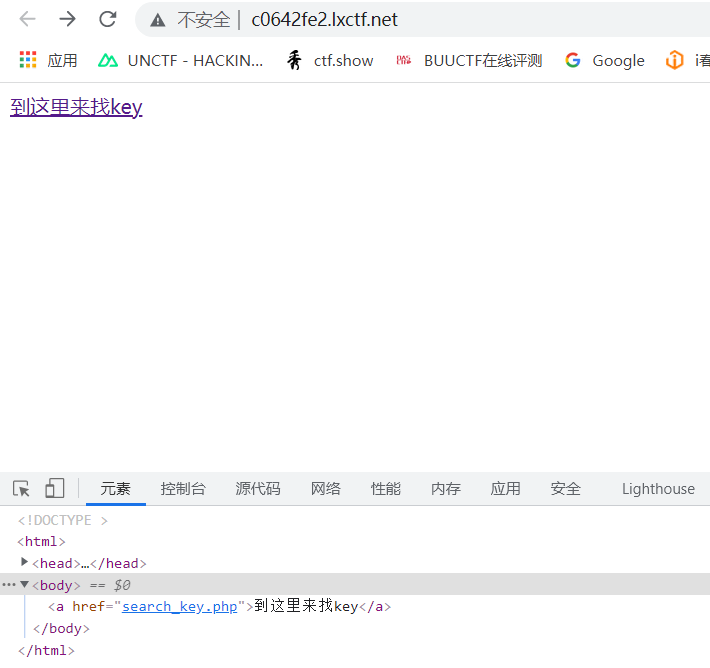
You can see that clicking the link will jump to search_key.php, but click to find
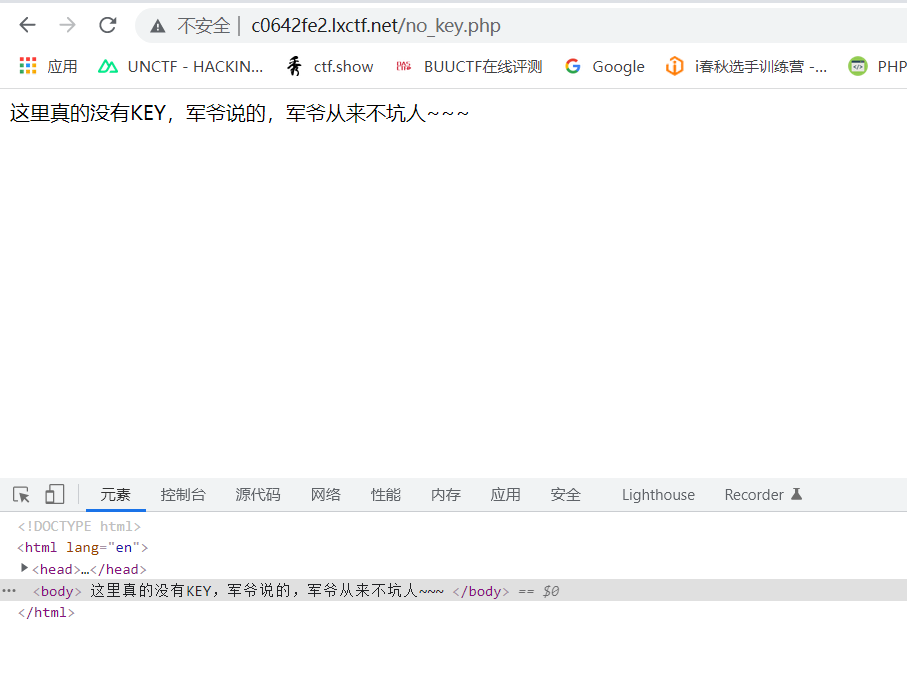
Jump to no_key.php indicates that there is a jump in the content of the target link, so bp packet capture is used to prevent the jump
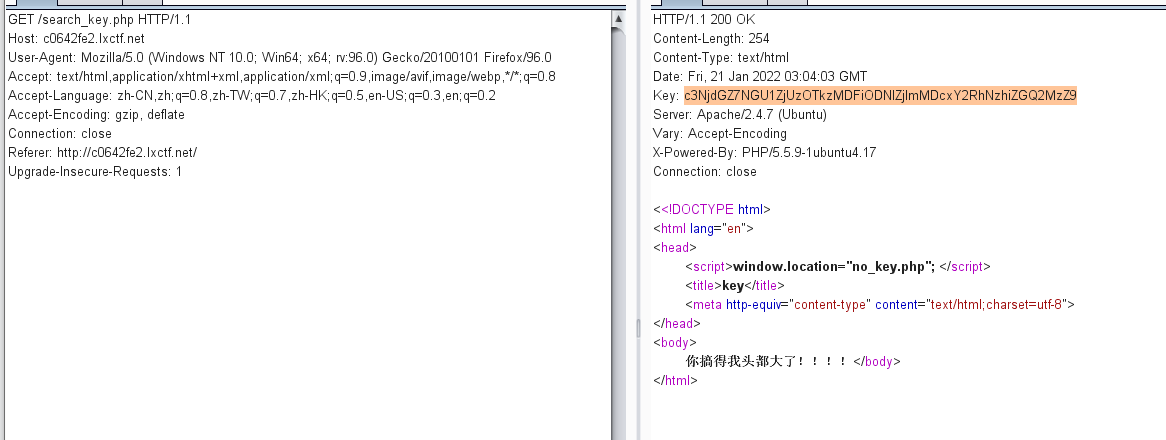
Finally, the key is found, that is, the target flag
Hand speed of being single for 20 years
It's no different from the previous question, and its flag is completely hidden
ereg
Pre knowledge
-
The ereg() function searches for the specified string in a string with the specified pattern. If the matching is successful, it returns true. Otherwise, it returns false. Characters that search for letters are case sensitive.
-
The ereg function has a NULL truncation vulnerability, which causes the regular filtering to be bypassed, so you can use% 00 to truncate the regular matching
It's a white start. All questions depend on sweeping
Find the source code on robots Txt
if (isset ($_GET['password'])) {
if (ereg ("^[a-zA-Z0-9]+$", $_GET['password']) === FALSE)//If the password is not a number or letter
{
echo '<p>You password must be alphanumeric</p>';
}
else if (strlen($_GET['password']) < 8 && $_GET['password'] > 9999999)//The password length is less than 8, and the key value is greater than 999999
{
if (strpos ($_GET['password'], '*-*') !== FALSE)// Judge whether the password parameter value appears*-*
{
die('Flag: ' . $flag);
}
else
{
echo('<p>*-* have not been found</p>');
}
}
else
{
echo '<p>Invalid password</p>';
}
}Through the analysis, the payload is finally constructed as? password=1e9%00*-*
reference resources : clover cloud show-CTF03# ereg_weixin_43973521 blog - CSDN blog
intval
Pre knowledge -- int overflow
The maximum integer number supported by the current PHP version. It is usually int(2147483647) in 32-bit system and int(9223372036854775807) in 64 bit system. Available as of PHP 5.0.5.
<?php
if(!isset($_GET['source'])){
highlight_file('index.php');
die();
}
include('flag.php');
$key1 = $_GET['f'];
$key2 = $_GET['l'];
$key3 = $_GET['a'];
$key4 = $_GET['g'];
if(isset($key1)&&isset($key2)&&isset($key3)&&isset($key4))
{
if(intval($key1) > 1 || intval($key1) < 0)
die("key1 is error.");
elseif(intval(intval($key1)) < 1)
{
if($key1 == 1){
if($key2 < 1){
die("key2 is error.");
}else{
if(intval($key2 + $key1) > 1){
die("key is error.");
}else{
$check = is_numeric($key3) and is_numeric($key4);
if(!$check){
die("key3 or key4 is error.");
}elseif(!(is_numeric($key3) and is_numeric($key4))){
$key3 = $flag;
$key4 = $redpacket;
}
die("flag:".$key3."<br>"."Alipay red envelope password".$key4);
}
}
}
else
die("key1 is error.");
}
else
die("key1 is error.");
}
?>After analysis:
*For key1, it is necessary to construct a method to make intval (key1) < 1 and key1 = = 1 -- > this is mainly for intval
Method: hexadecimal 0x can be used to bypass intval. 0x1 is translated by intval to be equal to 0, but it is actually 1
*For key2, when it is greater than or equal to 1, plus key1, it should be less than or equal to 1 -- > int maximum len gt h overflow will be used here
After overflow, the number of bits of the original management sign of the two-level system will change, resulting in the original being exactly a negative sign
Methods: the maximum int(9223372036854775807) was negative after adding 1
*While key3 and key4 need to detect whether the variables are numbers or numeric strings, one or both of them are null -- > here is a problem with the code priority
Method: use the priority of = and and to empty g
Finally, the payload is constructed as:? f=0x1&l=9223372036854775807&a=1&g=&source=1