With the development of the Internet environment, a series of security problems caused by network security problems will lead to the disclosure of trade secrets, economic losses of enterprises / individuals, and even cyber crime, or endanger national security.
In the current development scenario, some key information needs to be encrypted and transmitted. In addition to some server operation and maintenance levels, such as firewall, monitoring software, etc., and https encryption, we adopt RSA and AES encryption and decryption algorithms to realize the encryption and decryption transmission of information. The specific steps are as follows:
Step 1: first, use tools or commands to generate a public-private key of RSA
Here we use the online website tool to generate http://www.metools.info/code/c80.html
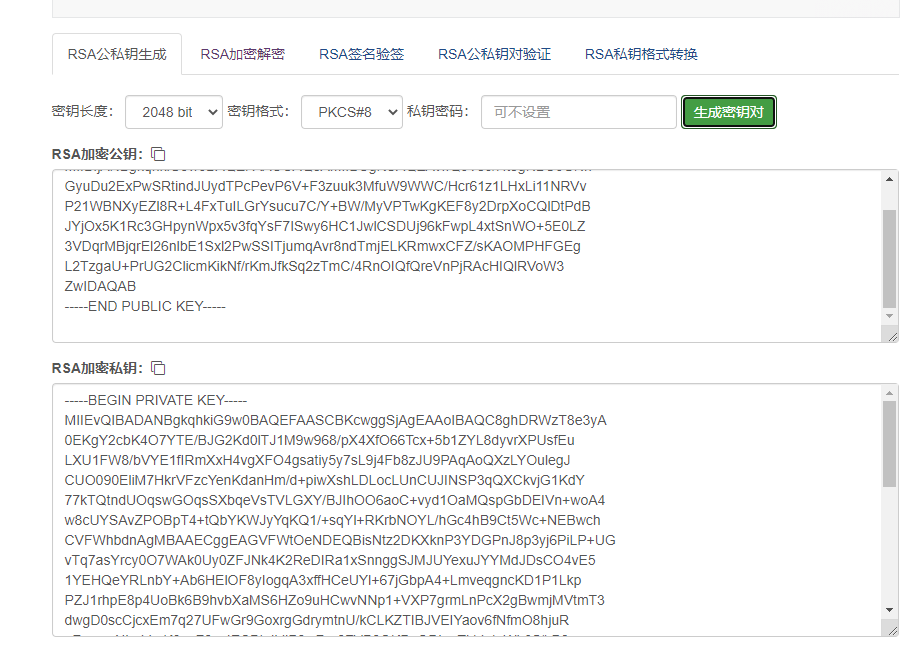
Get the public key:
-----BEGIN PUBLIC KEY----- MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAvIIQ0Vs0/Ht8gNBCoGNn GyuDu2ExPwSRtindJUydTPcPevP6V+F3zuuk3MfuW9WWC/Hcr61z1LHxLi11NRVv P21WBNXyEZl8R+L4FxTuILGrYsucu7C/Y+BW/MyVPTwKgKEF8y2DrpXoCQlDtPdB JYjOx5K1Rc3GHpynWpx5v3fqYsF7ISwy6HC1JwlCSDUj96kFwpL4xtSnWO+5E0LZ 3VDqrMBjqrEl26nlbE1Sxl2PwSSITjumqAvr8ndTmjELKRmwxCFZ/sKAOMPHFGEg L2TzgaU+PrUG2ClicmKikNf/rKmJfkSq2zTmC/4RnOIQfQreVnPjRAcHIQlRVoW3 ZwIDAQAB -----END PUBLIC KEY-----
Get private key:
-----BEGIN PRIVATE KEY----- MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQC8ghDRWzT8e3yA 0EKgY2cbK4O7YTE/BJG2Kd0lTJ1M9w968/pX4XfO66Tcx+5b1ZYL8dyvrXPUsfEu LXU1FW8/bVYE1fIRmXxH4vgXFO4gsatiy5y7sL9j4Fb8zJU9PAqAoQXzLYOulegJ CUO090EliM7HkrVFzcYenKdanHm/d+piwXshLDLocLUnCUJINSP3qQXCkvjG1KdY 77kTQtndUOqswGOqsSXbqeVsTVLGXY/BJIhOO6aoC+vyd1OaMQspGbDEIVn+woA4 w8cUYSAvZPOBpT4+tQbYKWJyYqKQ1/+sqYl+RKrbNOYL/hGc4hB9Ct5Wc+NEBwch CVFWhbdnAgMBAAECggEAGVFWtOeNDEQBisNtz2DKXknP3YDGPnJ8p3yj6PiLP+UG vTq7asYrcy0O7WAk0Uy0ZFJNk4K2ReDIRa1xSnnggSJMJUYexuJYYMdJDsCO4vE5 1YEHQeYRLnbY+Ab6HElOF8yIogqA3xffHCeUYl+67jGbpA4+LmveqgncKD1P1Lkp PZJ1rhpE8p4UoBk6B9hvbXaMS6HZo9uHCwvNNp1+VXP7grmLnPcX2gBwmjMVtmT3 dwgD0scCjcxEm7q27UFwGr9GoxrgGdrymtnU/kCLKZTIBJVEIYaov6fNfmO8hjuR oFxamgNlorbkgK9s+F8xqIECBtnildlP8wRm8FVB8QKBgQDl+uTkLhJuWh35/LB8 jdAgKg6x4dkFttSXuUpf3LVXPmEHHI+sWLyjAwwNctm2uZaqCupLGq+/2R9dMkJS GWqeAtRVdX/mFEJSCSouNT68BJPGz406wclfnd9W2nxD6Mw1W3My5u6dP60rlmml krNF6tS3XVAvdC5U4/rsQyL/kwKBgQDR1fvKLgbj/9afEJUW5nkLxnLld/XiYGnX 8Iip8GGB1k3rZTstNomD62WE1Ti+2ZGedJH9mZuvSr24V2gs1umFSLmJikSFwKWg quebFF9ArkeeFbMDHazwgs83y8AgW9es4s8PnWK+frirwUJbLUDwY7cnnf3owMil x+T65YsFXQKBgAzvTYxf4v196A21Xp/Cwh/s/aKXl0MxA0f9TeeSXEip438o5hPF ceahNz5SZVhXm9e4gXDz8UqTBaaSOxSvBUYZ1qNv1l+0Z/6BMXQj3oFoqH8YEVNq rs7H7FXQOAkBwOqHWDVWs7j4ad73uL1tQNP/3zLo9qeUmz5/DA/ZvtAtAoGBAIiB Vh1+t8jXBD3SQcr1/8TjQpd45KJx6ikqNx2mXShjy6jY4BhXpDoHhrFVLGcrjomw d9CsfxUX4Dft1L1myd+FIf4RzuXcH2NYCvdd12FyfvCeWSgrw/dqgXdguwnR9Ypo uh8EWdpnAafqP0qlM9uuYtYI98bUszL1yUZW0YuZAoGAdQNhMmeLWDyb+kAhzhde aVFJv3HQXM1zmuV69Kf3VYIvW6i0QVVicMQH68/0ARD4iXjGSun+T9pLxDrpCnr6 qBGJL2+q3c3d+mfVy1HuWTrXyDwModuIxtRqbdW2lT5OQ52E/XPaeMxlsHq8magz WBedmvwOT8m4lKn5a2GjYOY= -----END PRIVATE KEY-----
Step 2: generate a random number, decrypt the random number information using the public key generated by RSA, and obtain the encrypted key
Here we use the online URL tool for transformation http://www.metools.info/code/c81.html
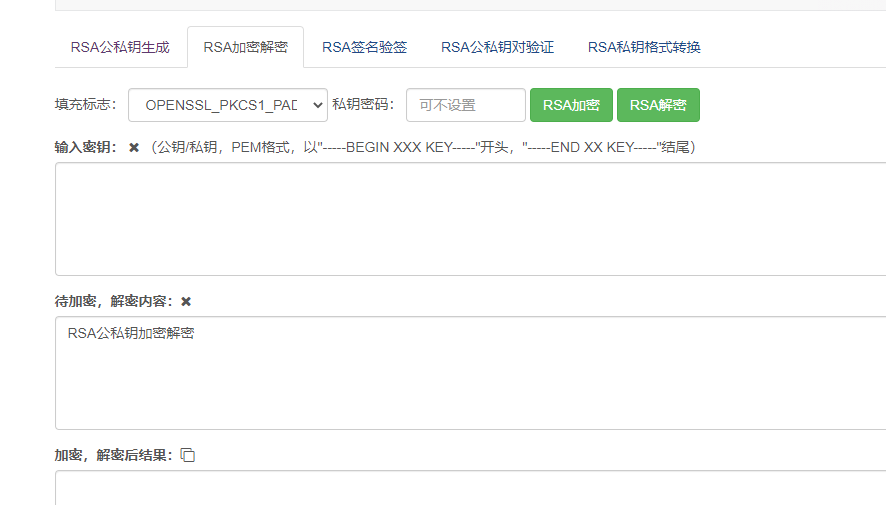
If the random number is J83683fGgS
Get the encryption key:
XHew7bE1XOW9e7ex4eIX3iAtlpWgZD0N2JLPpWjKjWFOPFJFMW24iOlfO4IwHFuatxszpgPuf2+tI6Ip9OZsFTMV5KwYp6yRRCcuQbg03xUCfSU/XJ7dqNA/NR9whZNZ8JhFQiJOy3epGdPCoqGWv2HoeDaecPqVDHcy29RO5pXUo4CPRlHKrOy9KOOQ9LuBLnV7DT7stHusGeObb94e+cjV9xvShqqnvncWahKs80Grbv9luRUBJ++gXHroz7Pjb3q2mmDMcFDWfXHHzm0Lv4WeiA73SUPuzg5FPGpD2vhi81DmC2FQaWN4ww4SHf1qaNq+nywGbSKdWAaCZ7Mkyg==
Step 3: use AES encryption algorithm to encrypt the information to be encrypted, and the password is the plaintext key defined in step 2
Here we use the online website tool to convert AES http://www.metools.info/code/c24.html
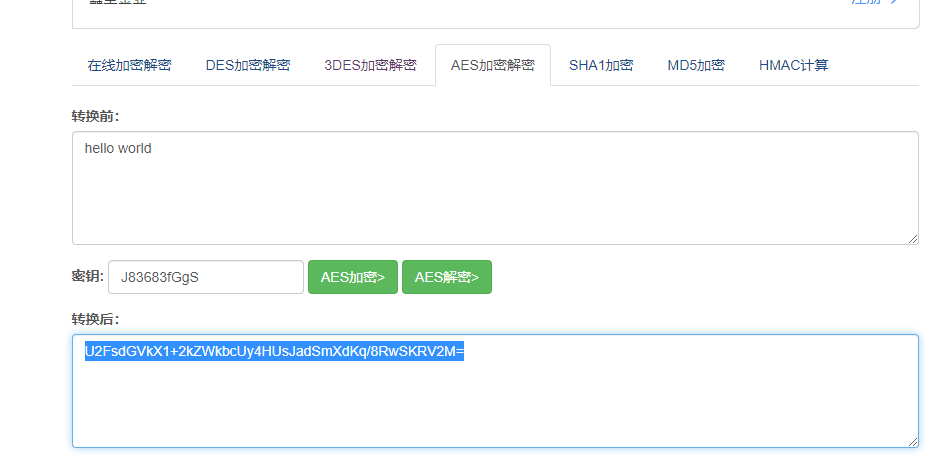
For example, the encrypted information is hello world string , Obtain the encrypted data of AES
U2FsdGVkX1+2kZWkbcUy4HUsJadSmXdKq/8RwSKRV2M=
nowadays Two encrypted messages key and ciphertext data are transmitted At this point, the information encryption process has ended. The decryption process is described below.
Step 4: distribute the private key generated in step 1 Give it to the decryptor. The decryptor obtains the encrypted data and key for decryption.
Step 5: decrypt the ciphertext key with the private key to obtain the plaintext key
Here we use online website tools to decrypt http://www.metools.info/code/c81.html
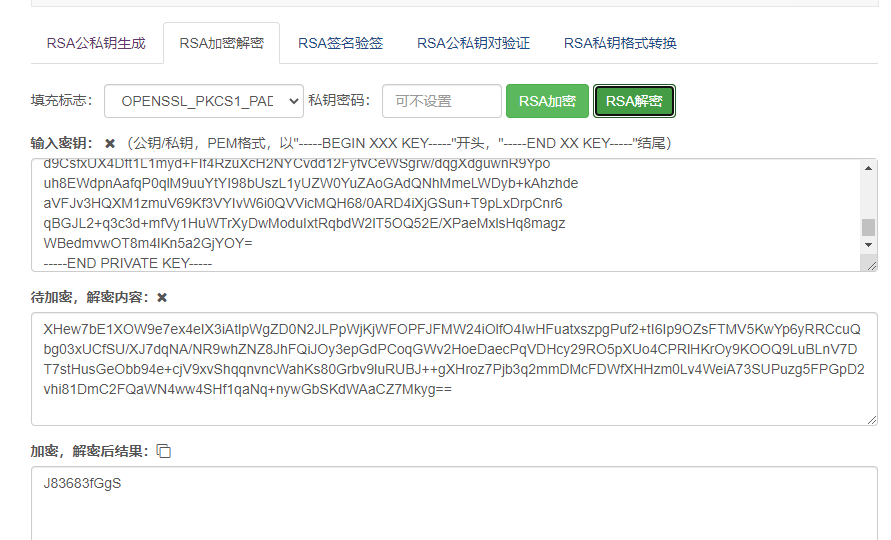
Get plaintext key:
J83683fGgS
Step 6: use the plaintext key as the decryption password of its AES to decrypt its ciphertext data
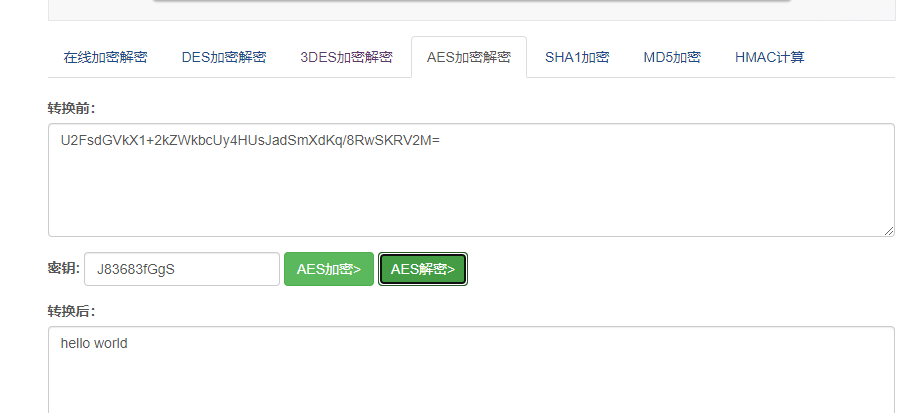
Get the final plaintext data The hello world string.
thus The whole encryption and decryption process is over.
This scheme is applicable to various languages and is cross language boundary. Appeal is just an idea of encryption and decryption. It is for reference only. Welcome to communicate. thank you.