1. Preface
Steps: analyze Android global Java obfuscator, analyze TCP private protocol, and write socket script to realize data capture
The analyzed app is here
https://wwo.lanzouy.com/ifKPbytn9mh password:fhj0
This analysis process is limited to learning and use. Do not use it for illegal purposes. If the reader uses it for illegal purposes, all the consequences have nothing to do with him
Note: if you have overseas App data needs, you can contact me. After WeChat official account, you can add WeChat to me directly in the menu bar.

2.app analysis
Use iptables to mask the relevant IP to make it impossible to force HTTP requests. Each room has its own IP, and if all IP fails, there will be no data display directly
2-1 various tests
The app encountered the same problem as the previous one Reverse analysis Frida, Xposed, Root detection and protobuf data analysis of an App
After a careful look, yes appsflyer The products of this security company are making trouble
The company still kindly told us all the hook technologies we need to learn
2-2 global Java obfuscator
The global code variable names are confused. If you look at them too much, the code will be confused into the following example, the library Java obfuscator This effect can be achieved
3. Packet capture
3-1 Wireshark packet capture analysis
Today we are analyzing this interface,
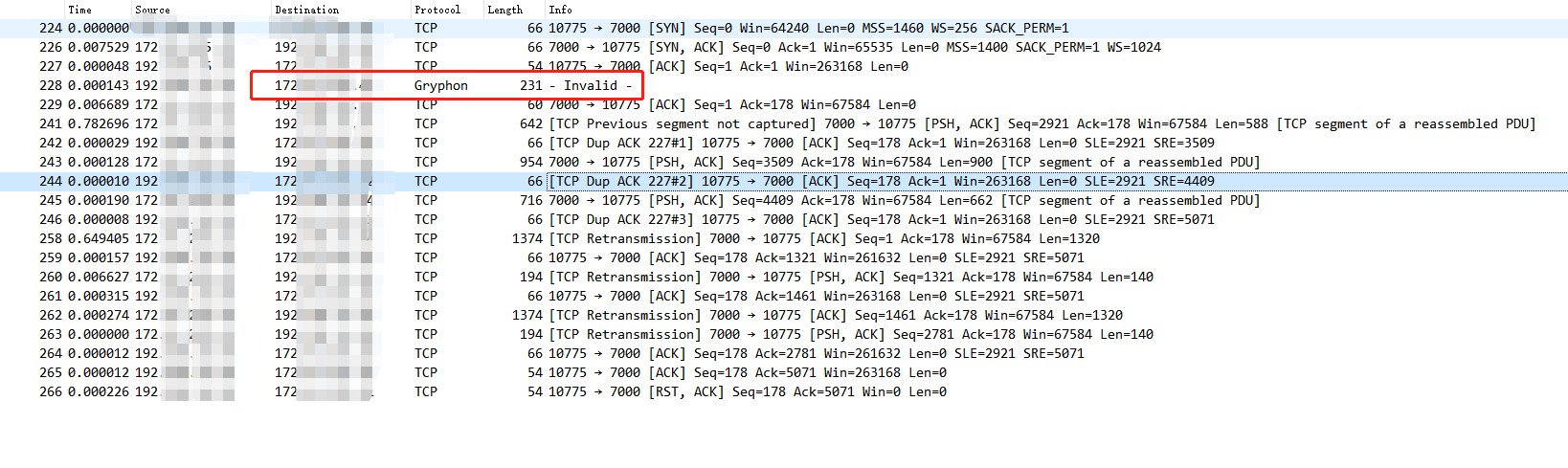
This Gryphon seems to have never seen such a protocol. Don't panic. Let's track the tcp flow. Oh, isn't this a simple tcp request? Is this the end of the article? It's not as simple as we think. Let's analyze it slowly
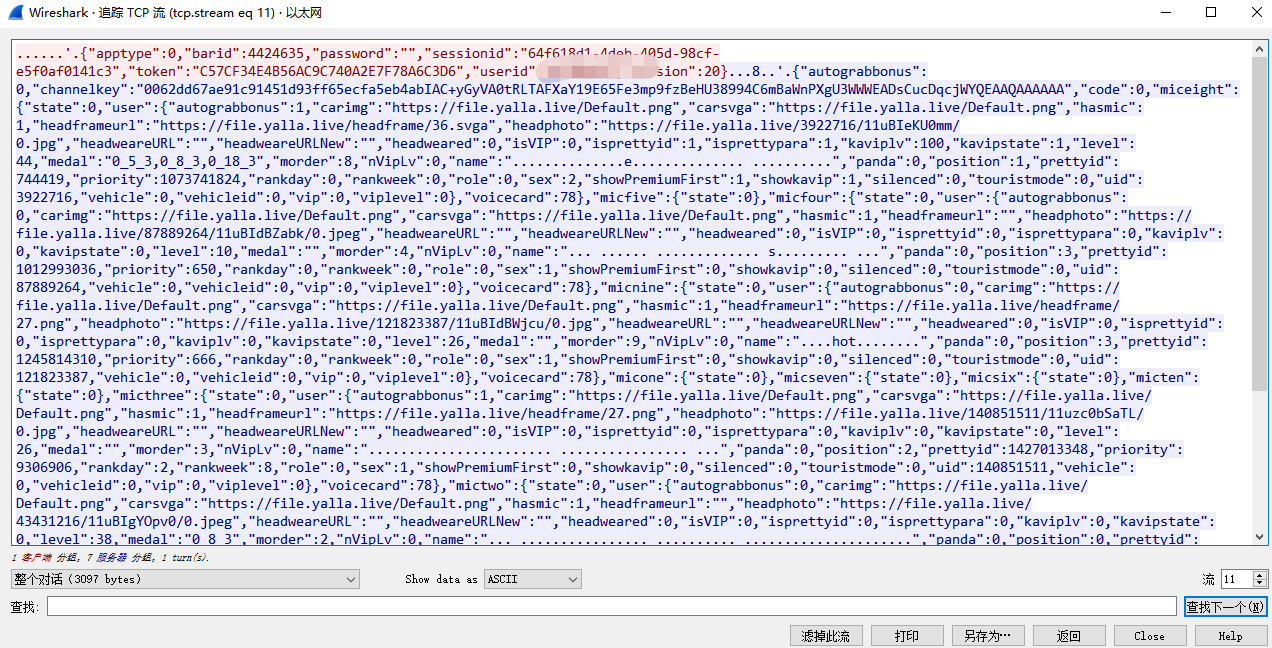
So we try to create a simple socket to send TCP messages
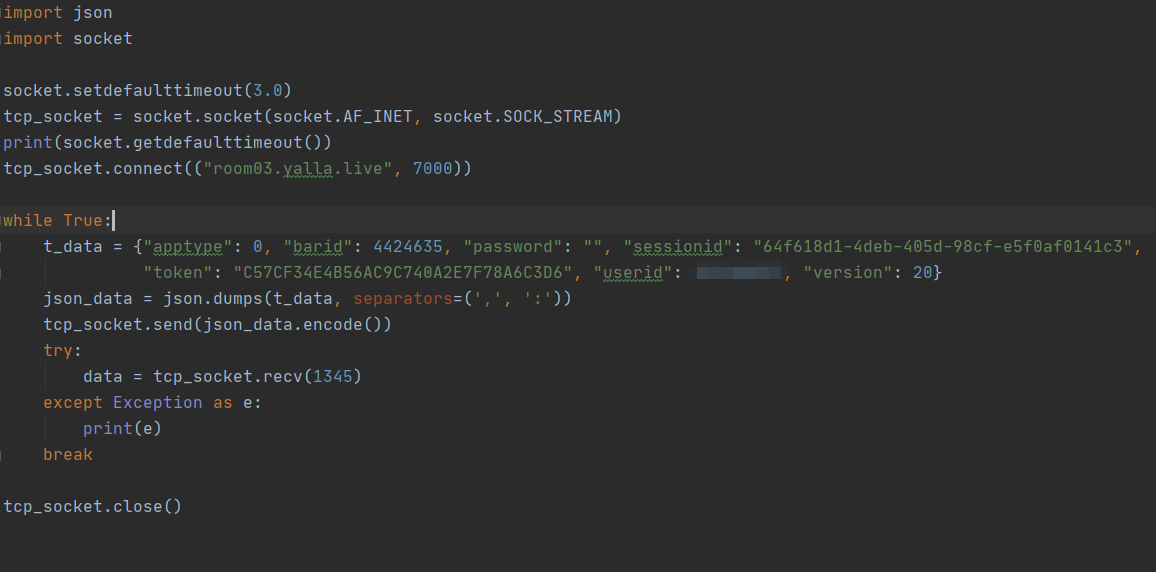
3-2 positioning key codes
After object dynamic analysis, locate key activities
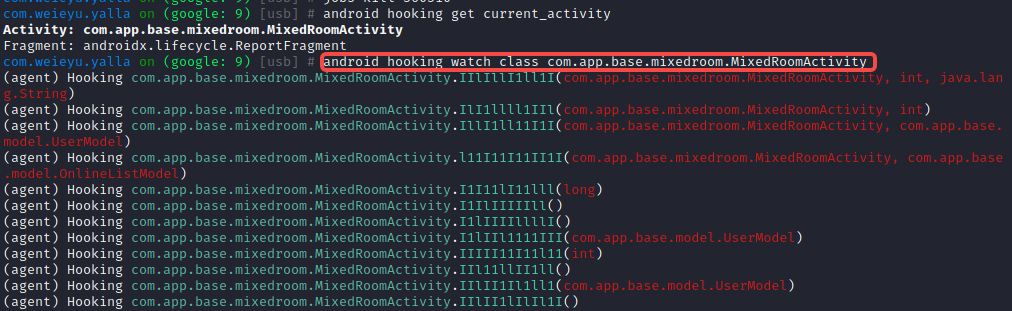
After the object analysis, go to the Hook corresponding key code in combination with Frida
Eventually you'll be here
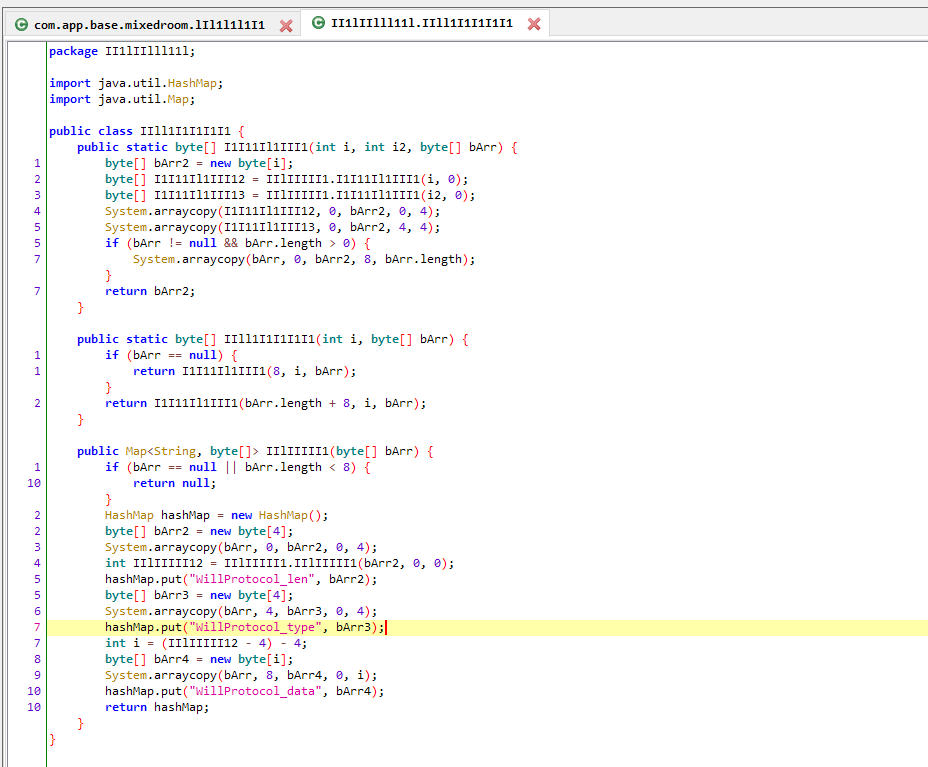
Then after another round of analysis, it is found that
public static byte[] I1I11Il1III1(int i, int i2, byte[] bArr)
This method is an encryption function
public Map<String, byte[]> IIlIIIII1(byte[] bArr)
This is the decryption function
4. Implementation code and results
4.1 tcp private protocol restore
def system_array_copy(array1, start_index, array2, target_index, copy_num):
# Java System.arraycopy rewrite
for index, i in enumerate(range(target_index, target_index + copy_num)):
array2[i] = array1[start_index + index]
# print(array1[start_index:start_index + index].decode('unicode_escape'))
return array2
def encode_the_string(i, i2, raw_barr):
# encode_the_string
bArr2 = bytearray()
for i in range(i):
bArr2.append(ord('0'))
byte_array2 = ack(i, 0, ff=1)
byte_array3 = ack(i2, 0)
system_array_copy(byte_array2, 0, bArr2, 0, 4)
system_array_copy(byte_array3, 0, bArr2, 4, 4)
if raw_barr is not None and len(raw_barr) > 0:
system_array_copy(raw_barr, 0, bArr2, 8, len(raw_barr))
return bArr2
def decode_will_protocol_data(bArr):
# decode_will_protocol_data
data = bArr.split('\x11'.encode())[1].split('\x17'.encode())
return json.loads(data[0][:data[0].find(b'}}') + 2].decode()), json.loads(
data[1][:data[1].find(b'}}') + 2].decode())
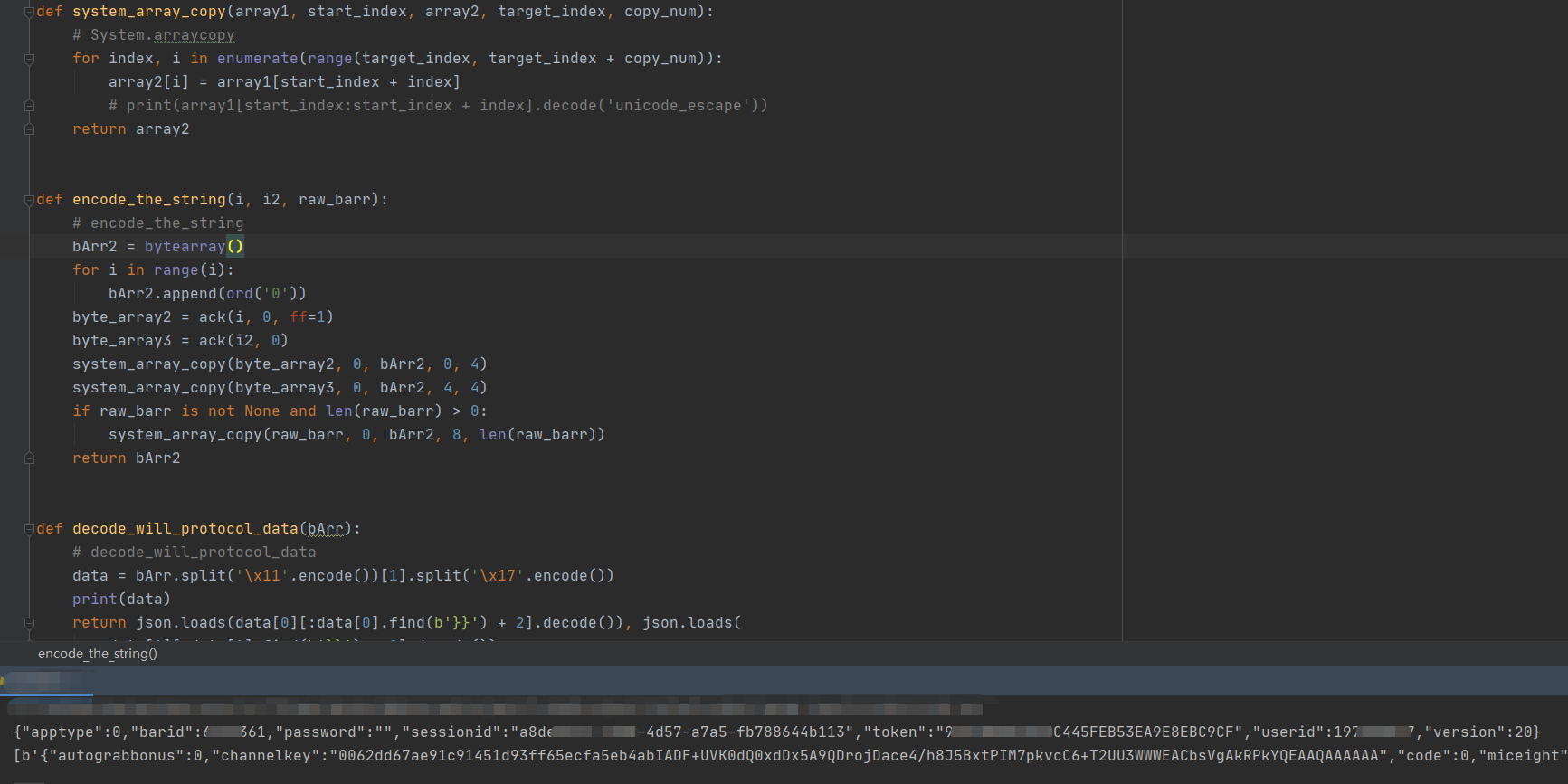
4.2 results
The result is very nice
4. Summary
Writing socket programming is often less involved by web crawlers, and it will only be more and more difficult behind the TCP private protocol
This is the last article to analyze the Java layer. Subsequent articles will focus more on the analysis of SO layer files. After all, with object and GDA, there is no Java layer hook code that can't be written at all
GDA automatically generates Frida hook code
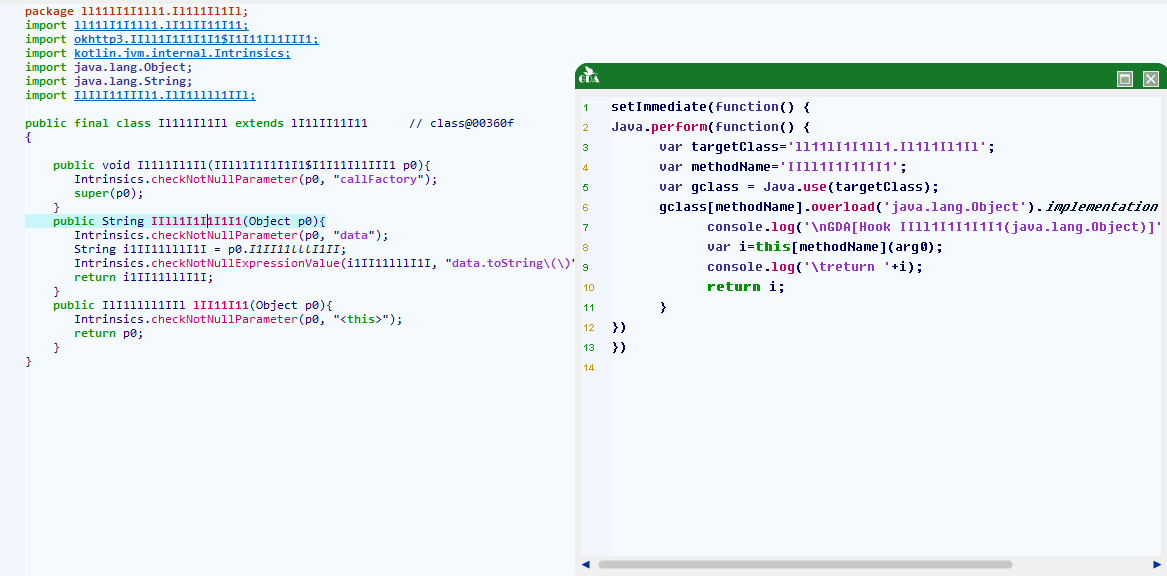
Object can generate templates that require hook functions (except constructors)
android hooking generate simple theFuckingClassName