Unity Science
Old rules, let's first introduce Unity's popular science knowledge:
- Unity is a real-time 3D interactive content creation and operation platform.
- All creators, including game development, art, architecture, automobile design and film and television, turn creativity into reality with Unity.
- Unity platform provides a complete set of software solutions that can be used to create, operate and realize any real-time interactive 2D and 3D content. The supporting platforms include mobile phones, tablets, PC s, game consoles, augmented reality and virtual reality devices.
- Unity can also be simply understood as a game engine, which can be used to professionally make games!
Unity steps on the pit to learn small knowledge points
Unity calls the API to dynamically obtain Android permissions
When developing Android applications, the problem of obtaining Android permissions is often used.
There are two solutions to this problem
- One is that the method of dynamically obtaining permissions has been written on the Android side, and Unity can call this method.
- The other is to call API directly in Unity and apply for permission access (after 2019, Unity has already provided Android oriented permissions).
For Unity developers, it's convenient to directly call API on Unity side to apply for permission. Here's how to call it.
If you want to know the first method, you can see this article: How Unity interacts with Android Studio ✨ Obtain mobile phone permission (storage, recording, camera, etc.)
Unity official API link: https://docs.unity3d.com/ScriptReference/Android.Permission.html
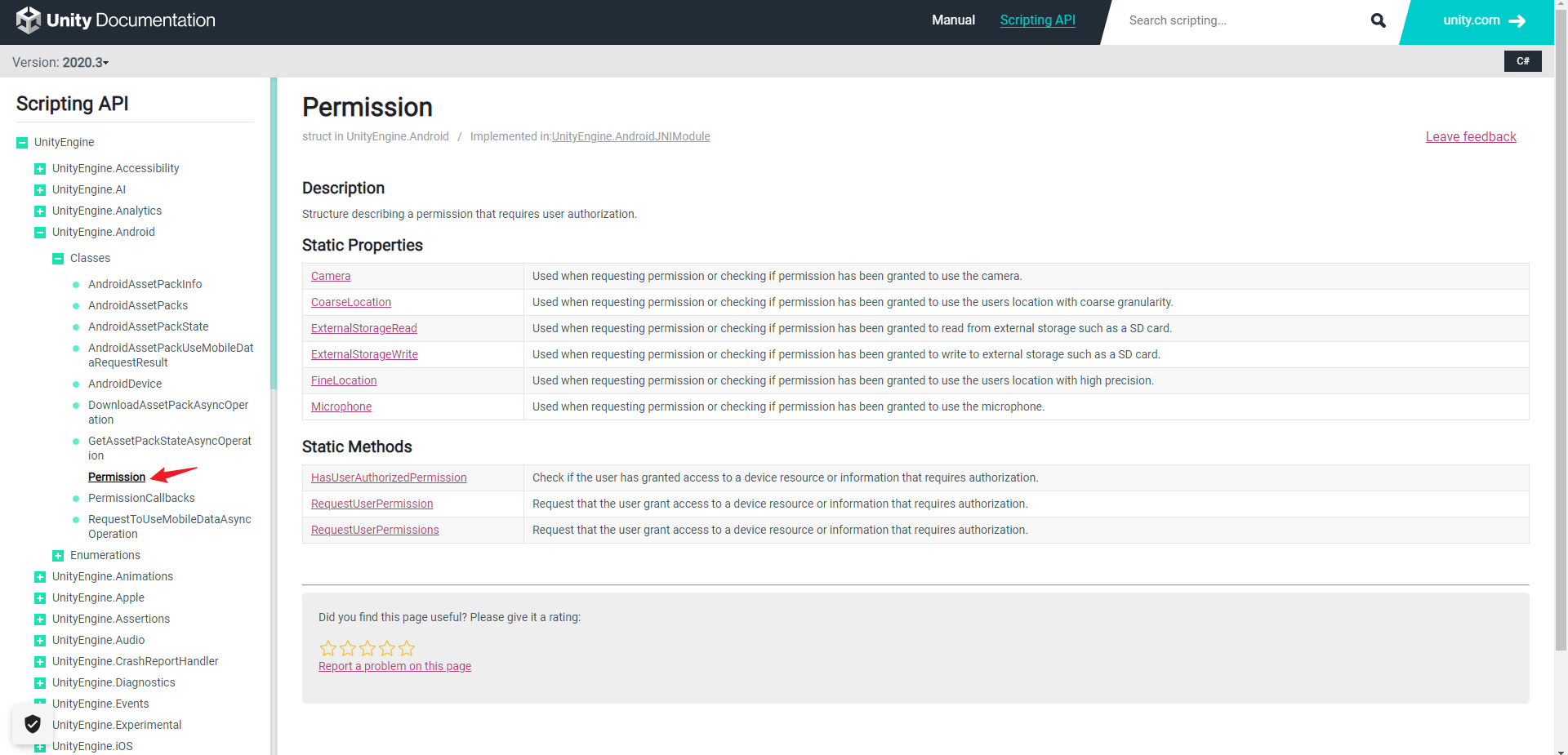
Click the source code to see that Unity also has permission names, which means that we can also customize some permissions to pop-up windows, and we don't have to use them.
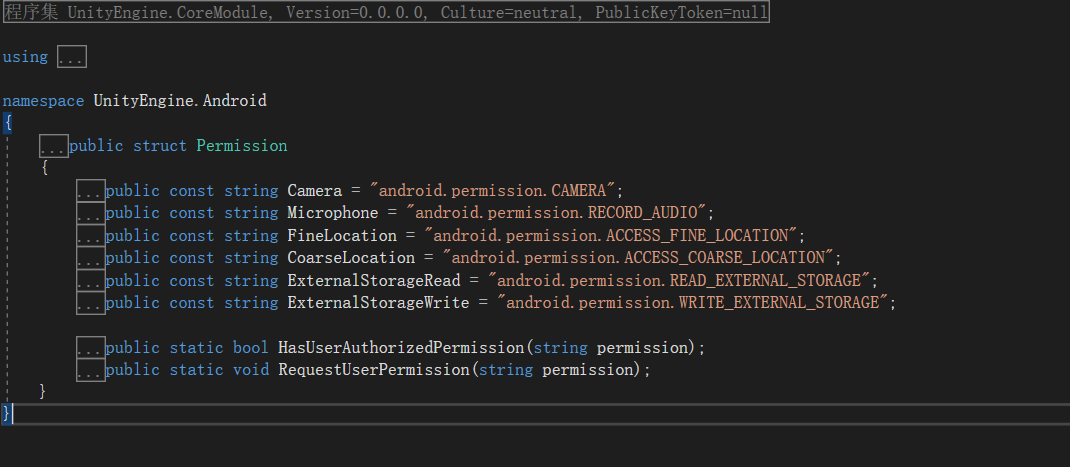
The API provided by Unity can be called directly in the script. Examples of API usage are as follows:
private void Start()
{
Permission.RequestUserPermission(Permission.Camera);
Permission.RequestUserPermission(Permission.Microphone);
Permission.RequestUserPermission(Permission.FineLocation);
Permission.RequestUserPermission(Permission.CoarseLocation);
Permission.RequestUserPermission(Permission.ExternalStorageRead);
Permission.RequestUserPermission(Permission.ExternalStorageWrite);
}
The following is a complete example code of using Unity to dynamically apply for permission:
The first scheme:
using System.Collections;
using System.Collections.Generic;
using System.Linq;
using UnityEngine;
using UnityEngine.Android;
public class PerTest : MonoBehaviour
{
string[] strs = new string[] {
"android.permission.INTERNET",
"android.permission.READ_PHONE_STATE",
"android.permission.READ_EXTERNAL_STORAGE",
"android.permission.WRITE_EXTERNAL_STORAGE",
"android.permission.ACCESS_WIFI_STATE",
"android.permission.ACCESS_NETWORK_STATE",
"android.permission.GET_TASKS",
"android.permission.REQUEST_INSTALL_PACKAGES",
"android.permission.WAKE_LOCK",
"android.permission.SYSTEM_ALERT_WINDOW",
"android.permission.CHANGE_WIFI_STATE",
"android.permission.CHANGE_NETWORK_STATE",
"android.permission.ACCESS_COARSE_LOCATION",
"android.permission.ACCESS_FINE_LOCATION",
"android.permission.SYSTEM_OVERLAY_WINDOW",
"android.permission.ACCESS_COARSE_UPDATES",
"android.permission.WRITE_SETTINGS",
"android.permission.BATTERY_STATS",
"android.permission.MOUNT_UNMOUNT_FILESYSTEMS"
};
void Start()
{
for (int i = 0; i <= strs.Length - 1; i++)
{
Permission.RequestUserPermission(strs[i]);
Debug.Log("add permission: " + strs[i]);
}
}
}
The second scheme:
using System.Linq;
using UnityEngine;
using UnityEngine.Android;
public class PerTest : MonoBehaviour
{
//An array of strings for which you want permission
string[] strs = new string[] {
"android.permission.INTERNET",
"android.permission.READ_PHONE_STATE",
"android.permission.READ_EXTERNAL_STORAGE",
"android.permission.WRITE_EXTERNAL_STORAGE",
"android.permission.ACCESS_WIFI_STATE",
"android.permission.ACCESS_NETWORK_STATE",
"android.permission.GET_TASKS",
"android.permission.REQUEST_INSTALL_PACKAGES",
"android.permission.WAKE_LOCK",
"android.permission.SYSTEM_ALERT_WINDOW",
"android.permission.CHANGE_WIFI_STATE",
"android.permission.CHANGE_NETWORK_STATE",
"android.permission.ACCESS_COARSE_LOCATION",
"android.permission.ACCESS_FINE_LOCATION",
"android.permission.SYSTEM_OVERLAY_WINDOW",
"android.permission.ACCESS_COARSE_UPDATES",
"android.permission.WRITE_SETTINGS",
"android.permission.BATTERY_STATS",
"android.permission.MOUNT_UNMOUNT_FILESYSTEMS"
};
void Start()
{
//Start dynamic request permission
strs.ToList().ForEach(s => {
Debug.Log("RequestUserPermission: "+s);
if (!Permission.HasUserAuthorizedPermission(s))
{
Permission.RequestUserPermission(s);
Debug.Log("add RequestUserPermission: " + s);
}
else
{
Debug.Log("it has RequestUserPermission: " + s);
}
});
}
}
The third scheme:
using System.Collections;
using System.Collections.Generic;
using UnityEngine;
using UnityEngine.Android;
public class PerTest : MonoBehaviour
{
public static PerTest instance;
private void Awake()
{
instance = this;
}
//Initialization, permission application should be made as early as possible
[RuntimeInitializeOnLoadMethod(RuntimeInitializeLoadType.BeforeSceneLoad)]
public static void Init()
{
//First add the permission to the list, and then apply
AndroidPermissionMgr.permissionList.Add("android.permission.READ_PHONE_STATE");
AndroidPermissionMgr.permissionList.Add(Permission.ExternalStorageRead);
AndroidPermissionMgr.permissionList.Add(Permission.ExternalStorageWrite);
AndroidPermissionMgr.permissionList.Add(Permission.FineLocation);
AndroidPermissionMgr.permissionList.Add(Permission.CoarseLocation);
AndroidPermissionMgr.StartCheckPermission(0.02f); //Start application
Debug.Log("Permission application completed");
}
}
public static class AndroidPermissionMgr
{
static int index;
public static List<string> permissionList = new List<string>();
public static void StartCheckPermission(float time)
{
Debug.Log("Start permission application");
if (permissionList.Count > 0)
{
Get(permissionList[index], time);
}
}
/// <summary>
///External access method
/// </summary>
///< param name = "type" > permission name < / param >
///< param name = "time" > if you refuse, how long is the delay to apply again < / param >
static void Get(string type, float time)
{
if (!Permission.HasUserAuthorizedPermission(type))
{
Permission.RequestUserPermission(type);
Debug.Log("Obtaining permissions for:" + type);
PerTest.instance.StartCoroutine(Check(type, time));
}
else
{
Debug.Log("Permission obtained:" + type);
if (index < permissionList.Count - 1)
{
index += 1;
Get(permissionList[index], time);
}
}
}
static IEnumerator Check(string type, float time)
{
yield return new WaitForSeconds(time);
Get(type, time);
}
}
The pop-up window of the three schemes has the same effect, and different permissions can be added according to different permission requirements.
The following is all the Android permission tables you can refer to.
Android common permissions sorting
<!--Connection network permission, used to perform cloud voice capability -->
<uses-permission android:name="android.permission.INTERNET"/>
<!--Obtain the permission to use the mobile phone recorder. This permission is required for dictation, recognition and semantic understanding -->
<uses-permission android:name="android.permission.RECORD_AUDIO"/>
<!--Read network information status -->
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<!--Get current wifi state -->
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE"/>
<!--Allow programs to change network connection status -->
<uses-permission android:name="android.permission.CHANGE_NETWORK_STATE"/>
<!--Permission to read mobile phone information -->
<uses-permission android:name="android.permission.READ_PHONE_STATE"/>
<!--Read contact permission, which is required for uploading contacts -->
<uses-permission android:name="android.permission.READ_CONTACTS"/>
<!--Write permission for external storage, which is required for building syntax -->
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE"/>
<!--External storage read permission, which is required for building syntax -->
<uses-permission android:name="android.permission.READ_EXTERNAL_STORAGE"/>
<!--Configuration permission is used to record application configuration information -->
<uses-permission android:name="android.permission.WRITE_SETTINGS"
tools:ignore="ProtectedPermissions" />
<!--Mobile positioning information is used to provide positioning for semantic and other functions and provide more accurate services-->
<!--Location information is sensitive information, which can be accessed through Setting.setLocationEnable(false)Close location request -->
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"/>
<!--If you need to use camera head, you also need to use photo recognition -->
<uses-permission android:name="android.permission.CAMERA" />
Android dangerous permissions
| number | Permission group | jurisdiction |
|---|---|---|
| 0 | CALENDAR | READ_CALENDAR WRITE_CALENDAR |
| 1 | CAMERA | CAMERA |
| 2 | CONTACTS | READ_CONTACTS WRITE_CONTACTS GET_ACCOUNTS |
| 3 | LOCATION | ACCESS_FINE_LOCATION ACCESS_COARSE_LOCATION |
| 4 | MICROPHONE | RECORD_AUDIO |
| 5 | PHONE | READ_PHONE_STATE CALL_PHONE READ_CALL_LOG WRITE_CALL_LOG ADD_VOICEMAIL USE_SIP PROCESS_OUTGOING_CALLS |
| 6 | SENSORS | BODY_SENSORS |
| 7 | SMS | SEND_SMS RECEIVE_SMS READ_SMS RECEIVE_WAP_PUSH RECEIVE_MMS |
| 8 | STORAGE | READ_EXTERNAL_STORAGE WRITE_EXTERNAL_STORAGE |
Android all permissions
| Serial number | jurisdiction | explain |
|---|---|---|
| 001 | ACCESS_CHECKIN_PROPERTIES | Allow read-write access to the "properties" table in the checkin database, The value can be modified and uploaded |
| 002 | ACCESS_COARSE_LOCATION | Allow a program to access CellID or WiFi hotspots to get a rough location |
| 003 | ACCESS_FINE_LOCATION | Allow a program to access CellID or WiFi hotspots to get a rough location |
| 004 | ACCESS_LOCATION_EXTRA_COMMANDS | Allow applications to access additional locations to provide commands |
| 005 | ACCESS_NETWORK_STATE | Allows the program to obtain network information status, such as whether the current network connection is valid |
| 006 | ACCESS_NOTIFICATION_POLICY | Tag permissions for applications that want to access notification policies |
| 007 | ACCESS_WIFI_STATE | Allow the program to obtain the current WiFi access status and WLAN hotspot information |
| 008 | ACCOUNT_MANAGER | Allow the program to access account management through account authentication ACCOUNT_MANAGER related information |
| 009 | ADD_VOICEMAIL | Allow an application to add a voice mail system |
| 010 | BATTERY_STATS | Allow programs to update phone battery statistics |
| 011 | BIND_ACCESSIBILITY_SERVICE | Request the accessibilityservice service to ensure that only the system can bind to it |
| 012 | BIND_APPWIDGET | Allow the program to tell the appWidget service that it needs to access the database of the widget. Only very few applications use this permission |
| 013 | BIND_CARRIER_MESSAGING_SERVICE | Use when API level is higher than 23, otherwise use BIND_CARRIER_SERVICES |
| 014 | BIND_CARRIER_SERVICES | System processes that allow binding to services in operator applications will have this permission |
| 015 | BIND_CHOOSER_TARGET_SERVICE | It must be required by ChooserTargetService to ensure that only the system can bind to it |
| 016 | BIND_DEVICE_ADMIN | Request the system administrator receiver. Only the system can use it |
| 017 | BIND_DREAM_SERVICE | It must be required by a DreamService to ensure that only the system can bind to it |
| 018 | BIND_INCALL_SERVICE | It must be required by a MidiDeviceService to ensure that only the system can bind to it |
| 019 | BIND_INPUT_METHOD | Request InputMethodService service, which can only be used by the system |
| 020 | BIND_MIDI_DEVICE_SERVICE | It must be required by a MidiDeviceService to ensure that only the system can bind to it |
| 021 | BIND_NFC_SERVICE | By HostApduService or OffHostApduService, you must ensure that only the system can bind to it |
| 022 | BIND_NOTIFICATION_LISTENER_SERVICE | Notification listener service must be required to ensure that only the system can bind to it |
| 023 | BIND_PRINT_SERVICE | printservice must be required to ensure that only the system can bind to it |
| 024 | BIND_REMOTEVIEWS | The request must be made through the RemoteViewsService service, which can only be used by the system |
| 025 | BIND_TELECOM_CONNECTION_SERVICE | Must be required by ConnectionService to ensure that only the system can bind to it |
| 026 | BIND_TEXT_SERVICE | Textservice (for example, spell checker service) must be required to ensure that only the system can bind to it |
| 027 | BIND_TV_INPUT | The TvInputService must ensure that only the system can bind to it |
| 028 | BIND_VOICE_INTERACTION | Must be required by VoiceInteractionService to ensure that only the system can bind to it |
| 029 | BIND_VPN_SERVICE | Binding VPN service must be requested through VpnService service, which can only be used by the system |
| 030 | BIND_WALLPAPER | The request must be made through the WallpaperService service, which can only be used by the system |
| 031 | BLUETOOTH | Allow programs to connect to paired bluetooth devices |
| 032 | BLUETOOTH_ADMIN | Allow programs to discover and pair new Bluetooth devices |
| 033 | BLUETOOTH_PRIVILEGED | Allows applications to pair bluetooth devices without user interaction. This is not a third-party application available |
| 034 | BODY_SENSORS | Allows the application to access the sensors used by the user to measure what is happening in his / her body, such as a heart rate meter |
| 035 | BROADCAST_PACKAGE_REMOVED | Allows the program to broadcast a prompt message after an application package has been removed |
| 036 | BROADCAST_SMS | Allows the program to trigger a broadcast when it receives a text message |
| 037 | BROADCAST_STICKY | Allows the program to quickly receive the next broadcast after receiving the broadcast |
| 038 | BROADCAST_WAP_PUSH | The WAP PUSH service triggers a broadcast after receiving it |
| 039 | CALL_PHONE | Allow programs to make calls from non system dialers |
| 040 | CALL_PRIVILEGED | Allow the program to make calls and replace the Dialer Interface of the system |
| 041 | CAMERA | Allow the program to access the camera to take photos |
| 042 | CAPTURE_AUDIO_OUTPUT | Allows an application to capture audio output. Not used by third-party applications |
| 043 | CAPTURE_SECURE_VIDEO_OUTPUT | Allows an application to capture video output. Not used by third-party applications |
| 044 | CAPTURE_VIDEO_OUTPUT | Allow an application to capture video output and not be used by third-party applications |
| 045 | CHANGE_COMPONENT_ENABLED_STATE | Change whether the component is enabled |
| 046 | CHANGE_CONFIGURATION | Allows the current application to change configuration, such as positioning |
| 047 | CHANGE_NETWORK_STATE | Allows the program to change the network state, such as whether it is connected to the network |
| 048 | CHANGE_WIFI_MULTICAST_STATE | Allow programs to change WiFi multicast status |
| 049 | CHANGE_WIFI_STATE | Allow programs to change WiFi status |
| 050 | CLEAR_APP_CACHE | Allows the application to clear the application cache |
| 051 | CONTROL_LOCATION_UPDATES | Allow programs to obtain mobile network location information changes |
| 052 | DELETE_CACHE_FILES | Allow programs to delete cache files |
| 053 | DELETE_PACKAGES | Allow programs to delete apps |
| 054 | DIAGNOSTIC | Allow programs to RW to diagnostic resources |
| 055 | DISABLE_KEYGUARD | Allows the program to disable the keyboard lock |
| 056 | DUMP | Allows programs to obtain system dump information from system services |
| 057 | EXPAND_STATUS_BAR | Allow programs to expand or shrink the status bar |
| 058 | FACTORY_TEST | Allows the program to run in factory test mode |
| 059 | FLASHLIGHT | Allow access to flash |
| 060 | GET_ACCOUNTS | Allow programs to access account Gmail lists |
| 061 | GET_ACCOUNTS_PRIVILEGED | Allow access to the list of accounts in the account service |
| 062 | GET_PACKAGE_SIZE | Allow a program to obtain the space occupied by any package |
| 063 | GET_TASKS | Allows a program to obtain information about a currently or recently running task, an abbreviated task status, whether it is active, and so on |
| 064 | GLOBAL_SEARCH | Allow programs to allow global search |
| 065 | INSTALL_LOCATION_PROVIDER | Allow program installation location provider |
| 066 | INSTALL_PACKAGES | Allow applications to install |
| 067 | INSTALL_SHORTCUT | create shortcut |
| 068 | INTERNET | Allowing programs to access network connections may generate GPRS traffic |
| 069 | KILL_BACKGROUND_PROCESSES | Allows programs to call killBackgroundProcesses(String) Method to end the background process |
| 070 | LOCATION_HARDWARE | Hardware that allows location functionality to be used in an application without third-party applications |
| 071 | MANAGE_DOCUMENTS | Allows an application to manage access to documents, usually a document selector section |
| 072 | MASTER_CLEAR | Allows programs to perform soft formatting and delete system configuration information |
| 073 | MEDIA_CONTENT_CONTROL | Allow an application to know what is playing and control its content. Not used by third-party applications |
| 074 | MODIFY_AUDIO_SETTINGS | Allows the program to modify sound setting information |
| 075 | MODIFY_PHONE_STATE | Allows the program to modify the phone status, such as flight mode, but does not include the replacement system Dialer Interface |
| 076 | MOUNT_FORMAT_FILESYSTEMS | Allows programs to format removable file systems, such as formatting and emptying SD cards |
| 077 | MOUNT_UNMOUNT_FILESYSTEMS | Allow programs to mount and unmount external file systems |
| 078 | NFC | Allows the program to perform NFC short-range communication operations for mobile support |
| 079 | PACKAGE_USAGE_STATS | Allows a program to set its activities display |
| 080 | PERSISTENT_ACTIVITY | Allows the program to create a permanent Activity that is marked to be removed in the future |
| 081 | PROCESS_OUTGOING_CALLS | Allow programs to monitor, modify, or abandon broadcast calls |
| 082 | READ_CALENDAR | Allows the program to read the user's schedule information |
| 083 | READ_CALL_LOG | Read call records |
| 084 | READ_CONTACTS | Allow programs to access contact address book information |
| 085 | READ_EXTERNAL_STORAGE | The program can read the files in the external storage space of the device (built-in SDcard and external SDCard), if your App has added "write"_ EXTERNAL_ "Storage" permission, there is no need to add read permission. Write permission already includes read permission |
| 086 | READ_FRAME_BUFFER | Allows the program to read the frame cache for screenshots |
| 087 | READ_INPUT_STATE | Allows the program to read the input status of the current key, which is only used for the system |
| 088 | READ_LOGS | Allow programs to read the underlying system logs |
| 089 | READ_PHONE_STATE | Allow programs to access phone status |
| 090 | READ_SMS | Allow programs to read SMS content |
| 091 | READ_SYNC_SETTINGS | Allow programs to read synchronization settings and Google online synchronization settings |
| 092 | READ_SYNC_STATS | Allow the program to read the synchronization status and get Google online synchronization status |
| 093 | READ_VOICEMAIL | Allow applications to read voice mail on the system |
| 094 | REBOOT | Allow programs to restart devices |
| 095 | RECEIVE_BOOT_COMPLETED | Allow programs to run automatically after startup |
| 096 | RECEIVE_MMS | Allow programs to receive multimedia messages |
| 097 | RECEIVE_SMS | Allow programs to receive text messages |
| 098 | RECEIVE_WAP_PUSH | Allow programs to receive WAP PUSH information |
| 099 | RECORD_AUDIO | A microphone that allows programs to record sound through a phone or headset |
| 100 | REORDER_TASKS | The Z-axis in the system allows tasks to be reordered |
| 101 | REQUEST_IGNORE_BATTERY_OPTIMIZATIONS | Applications with permissions must use ACTION_REQUEST_IGNORE_BATTERY_OPTIMIZATIONS this is a normal permission: an application requests that it will always be granted permission without user approval or seeing it. |
| 102 | REQUEST_INSTALL_PACKAGES | Allow applications to request installation packages. For API greater than 22, you must hold the license to use ACTION_INSTALL_PACKAGE application. |
| 103 | RESTART_PACKAGES | Allow the program to end the task through the restartPackage(String) method, which will be abandoned externally |
| 104 | SEND_RESPOND_VIA_MESSAGE | Allow users to use your app to reply to instant SMS when they call |
| 105 | SEND_SMS | Allow programs to send text messages |
| 106 | SET_ALARM | Allow the program to set alarm reminder |
| 107 | SET_ALWAYS_FINISH | Allows the program to set whether the program always exits in the background |
| 108 | SET_ANIMATION_SCALE | Allows the program to set global animation scaling |
| 109 | SET_DEBUG_APP | Allows programs to set up debugging programs, which are generally used for development |
| 110 | SET_PREFERRED_APPLICATIONS | It allows the program to set the parameters of the application. It no longer works. For details, see the introduction of addPackageToPreferred(String) |
| 111 | SET_PROCESS_LIMIT | Allows programs to set a limit on the maximum number of processes |
| 112 | SET_TIME | Allow programs to set system time |
| 113 | SET_TIME_ZONE | Allows the program to set the system time zone |
| 114 | SET_WALLPAPER | Allow programs to set desktop wallpaper |
| 115 | SET_WALLPAPER_HINTS | Allow programs to set wallpaper suggestions |
| 116 | SIGNAL_PERSISTENT_PROCESSES | Allows the program to send a permanent process signal |
| 117 | STATUS_BAR | Allow programs to open, close, and disable the status bar |
| 118 | SYSTEM_ALERT_WINDOW | Allow programs to display system Windows |
| 119 | TRANSMIT_IR | Allow the use of the device's infrared transmitter, if available |
| 120 | UNINSTALL_SHORTCUT | remove shortcuts |
| 121 | UPDATE_DEVICE_STATS | Allow programs to update device status |
| 122 | USE_FINGERPRINT | Allow applications to use fingerprint hardware |
| 123 | USE_SIP | Allow programs to use SIP Video Services |
| 124 | VIBRATE | Allow program vibration |
| 125 | WAKE_LOCK | Allow the application to run the background process after the phone screen is closed |
| 126 | WRITE_APN_SETTINGS | Allow programs to write network GPRS access point settings |
| 127 | WRITE_CALENDAR | Allows the program to write to the schedule, but not read |
| 128 | WRITE_CALL_LOG | Allows the program to write (but not read) the user's contact data |
| 129 | WRITE_CONTACTS | Write contact, but not read |
| 130 | WRITE_EXTERNAL_STORAGE | Allow programs to write to external storage, such as writing files on SD cards |
| 131 | WRITE_GSERVICES | Allow programs to modify Google service maps |
| 132 | WRITE_SECURE_SETTINGS | Allow applications to read or write security system settings |
| 133 | WRITE_SETTINGS | Allows programs to read or write system settings |
| 134 | WRITE_SYNC_SETTINGS | Allow programs to write synchronization settings |
| 135 | WRITE_VOICEMAIL | Allow the application to modify and delete the existing voice mail in the system, which can only be used by the system |