Self use ~ do not spray
4.1.1 overview of network layer functions
*Overview of network layer functions
The packet is transmitted from the source end to the destination end to provide communication services for different hosts in the packet switching network
*Network layer functions
1.Routing and forwarding 2.Heterogeneous network interconnection // Through routers, mobile phones, computers, 4g,wifi and other heterogeneous networks are connected together for communication 3.congestion control 4.
*Congestion control
> Congestion control concept
> When all nodes have no time to accept packets and need to discard a large number of packets, the network is in a congested state;
> At this time, certain control measures need to be adopted;
> Congestion solution
1. Open loop control
// It is static, that is, it controls the aspects that may cause congestion in advance
2.closed-loop control
// It is dynamic and automatically adjusts after the network runs
*Flow control
> Compared with the sender, the flow control is caused by the sender sending too fast; > Congestion control is global, which is caused by excessive load;
4.1.2 circuit switching, message switching and packet switching
*Overview
// Layer 2 switching equipment, bridge? // Layer 3 switching device, router? > The switching equipment is interconnected to form a switching network > It not only realizes long-distance communication, but also reduces the number of ports of switching equipment
*Exchange mode classification
> Circuit switching > Message exchange >packet switching //Datagram mode and virtual circuit mode
*Circuit switching
e.g.telephone network > Circuit switching phase // Establish connection (call) -- Communication -- release connection (remove circuit) > Once the connection is established, there will be a fixed path for transmission > The bandwidth of the circuit is very large, which will cause waste, so multiplexing (time, frequency, code) is adopted // Similar to multi Lane
*Circuit switching advantages
1. Small communication delay // No connection establishment process, no error detection process, direct forwarding 2. Orderly transmission // Exclusive resources, send in order, accept in order 3.No conflict // Exclusive resources 4.Strong real-time performance // Monopolize resources and say what you want // Even if there is no call, the resource will not be used by others
*Circuit switching disadvantages
1.Long connection time 2.The line is exclusive and the use efficiency is low 3.Poor flexibility (one switching device fails and the whole connection is disconnected) 4.Error free control capability
*Message exchange
> The data sent is the whole of the information--message > The path can be selected randomly and not fixed > Different from the direct forwarding of circuit switching, message switching needs to store and forward and wait for the path to be idle > Similar to a serial process
*Advantages of message exchange
1.No connection required 2.Store and forward, dynamically allocate lines // First store, and then select a link according to the network status 3.High line reliability // There is a problem with one switching device. You can choose another path 4.High line utilization // It does not occupy a whole line, but only a part, and the rest can be used by other resources 5.Multi-objective service // A message can be sent to multiple destination addresses
*Disadvantages of message exchange
1.store-and-forward delays 2.The message size is uncertain, so the network node needs to have a large cache space
*Packet switching
> What is grouping? Divide a large data block (message) into small data blocks > characteristic Similar to parallel processes
*Packet switching advantages
1.No connection required 2.Store and forward, dynamically allocate lines 3.High line reliability // The grouping is short and the probability of error is reduced 4.High line utilization // It's not an exclusive path, it's just a small segment 5.Compared with message exchange, storage management is easier
*Packet switching disadvantages
1.store-and-forward delays 2.Additional information needs to be transmitted // Source address, destination address, packet number, etc 3.When the destination host is reached out of order, it needs to be sorted and reorganized
4.2 routing algorithm
The routing algorithm will select a better path under the current conditions, usually the shortest path or the least hops, and fill it in the forwarding table
The forwarding table contains four columns: destination network IP address, subnet mask, next hop IP address and interface
*Routing algorithm classification
> Static routing algorithm (non adaptive routing algorithm) // The administrator manually configures the routing information > Advantages: it is simple and reliable, and works well in networks with little topology change > Disadvantages: route update is slow and not suitable for large networks > Dynamic routing algorithm (adaptive routing algorithm) // Routers exchange information with each other and optimize the routing table entries according to the routing algorithm > Advantages: fast route update, suitable for large networks, and timely respond to link costs (path costs, such as hops) or network topology changes > Disadvantages: the algorithm is complex and increases the network burden
*Classification of dynamic routing algorithms
> Global: link state routing algorithm e.g.OSPF agreement // All routers have complete network topology and link cost information > Dispersion: distance vector routing algorithm e.g.RIP agreement // The router only knows the order and link cost of physical connection
*Hierarchical routing protocol
> Reasons for adopting hierarchical routing protocol (1) Large scale Internet (2) Many units do not want the outside world to know their routing protocol, but also want to connect to the Internet, so they adopt autonomous system AS // Routers in autonomous system AS not only use an internal routing protocol and common metrics to confirm the routing in AS; // A routing protocol between AS is also used to confirm the routing between autonomous system AS // Multiple routers in an autonomous system AS are connected in the autonomous system
*Hierarchical routing diagram
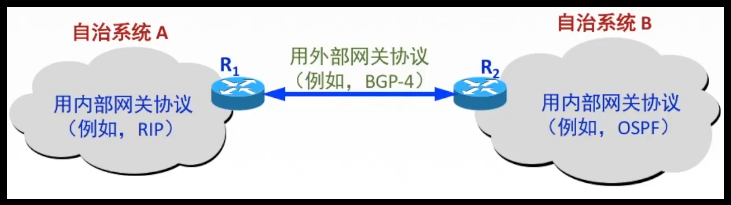
*Routing protocol in autonomous system AS
> Internal gateway protocol IGP // Used in autonomous system AS // e.g.RIP protocol, OSPF Protocol > External gateway protocol EGP // Use between autonomous systems AS // e.g.BGP
4.3.1 IP datagram format
*Main agreements of each layer
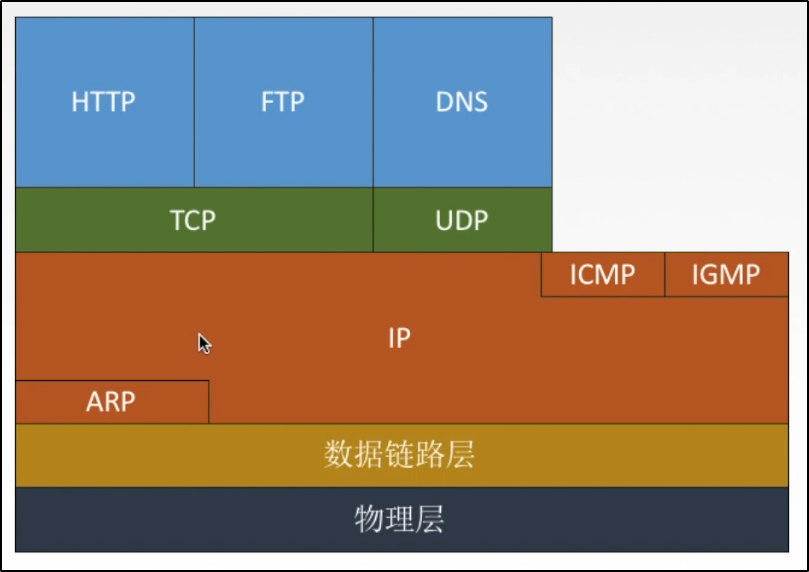
> ARP by IP Provide certain services; > IP by ICMP,IGMP Provide certain services;
*Overview of ip datagram structure
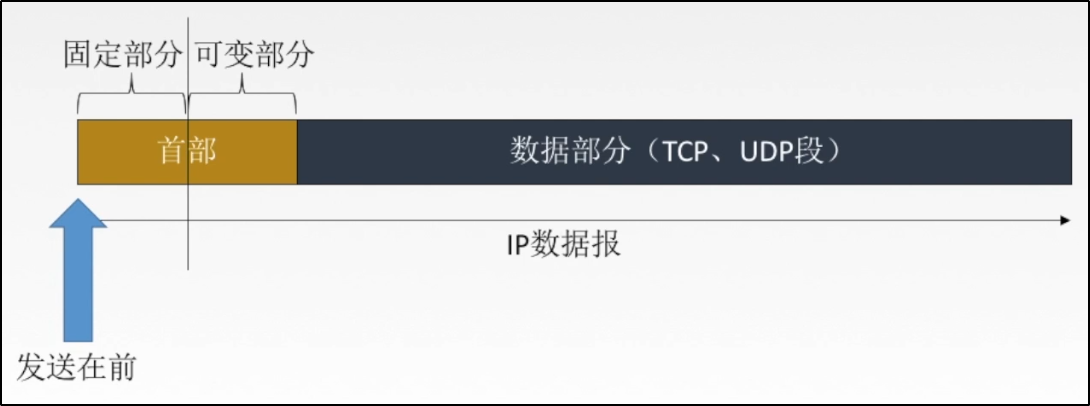
> IP The datagram is divided into header and data part > The first part is divided into fixed part and variable part
*IPv4 format
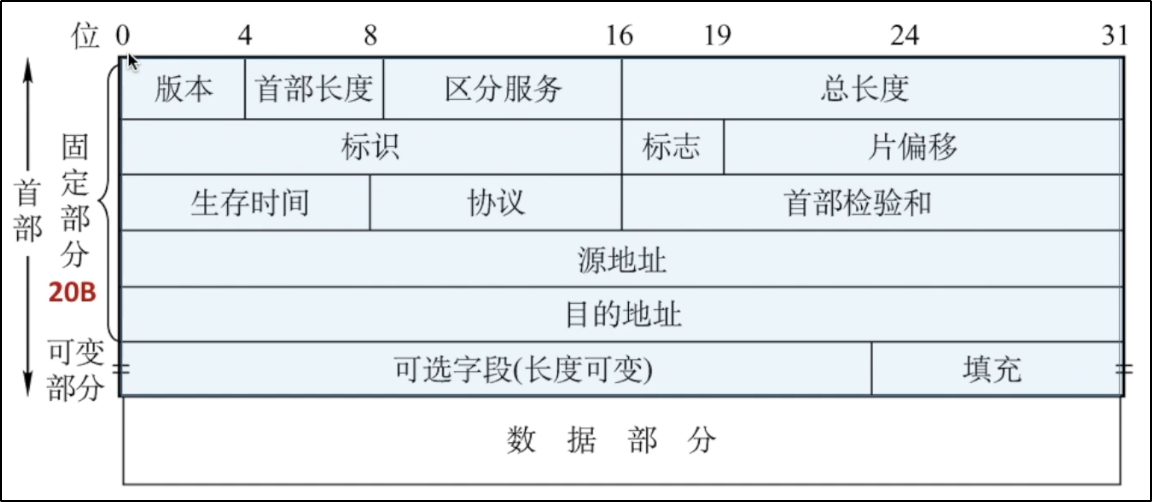
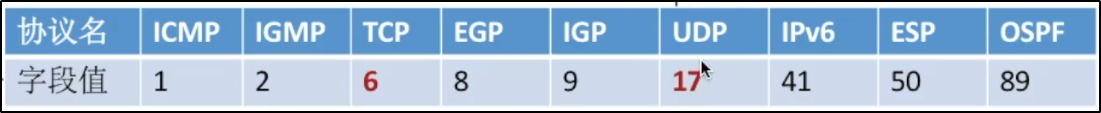
> edition The length is 4 bits, indicating IPv4 or IPv6 > header length The minimum value is 5 and the unit size is 4 B,I.e. 4 B*5=20B (Minimum length of fixed part?) > Total length Indicates: head length+Data length The unit is 1 B Indicates that the range is 0~2^16-1 // I.e. 0 ~ 65535 // It is usually not too large, otherwise it does not meet the MTU. The maximum link transmission unit will be segmented to obtain packets > survival time TTL The number of hops through the router to prevent constant transmission in the network TTL Drop when reduced to 0 > Protocol field Protocol used in the data section // See below for details > Head inspection and For inspection of head only > source IP address and objective IP address The length is 32 bits > optional field Add datagram common energy > Fill field All 0, make up the head into 4 B Integer multiple of
*Protocol field
4.3.2 IP datagram fragmentation
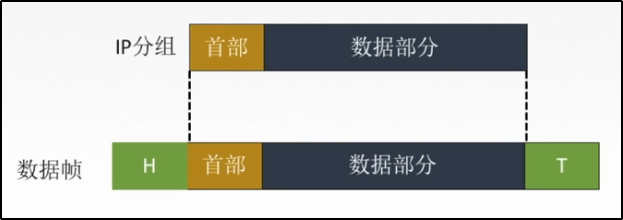
*IP packets are encapsulated into data frames
*Relevant knowledge
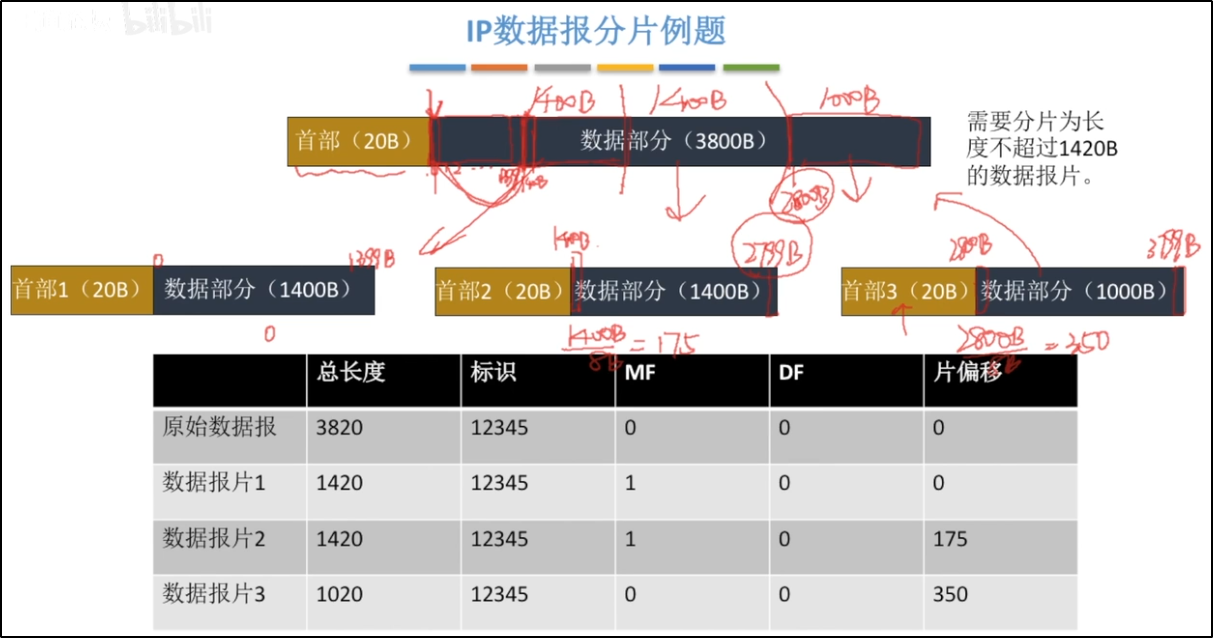
> identification Fragments of the same datagram use the same identifier >sign The length is 3 digits, but only 2 digits are meaningful X _ _ Second place DF(Don't Fragment): DF=1,No slicing DF=0,Allow fragmentation Third place MF(More Fragment): MF=1,There is "slice" behind the representative" MF-0,It means that this is the last piece and there is no piece >Slice offset 13 After slicing, the relative position of a slice in the original group With 8 B Unit // That is, except for the last partition, the length of each partition is an integral multiple of 8B when it is certain If the slice offset is 000....1 Then, its position in the original group is 1*8B
*IP datagram segmentation example
*Deepening of knowledge points
IP In datagram: The unit of total length is 1 B The unit of head length is 4 B The unit of slice offset is 8 B
4.3.3 IPv4
*IP address
IP The address is the only 32-bit address in the world/4 Byte identifier indicating the interface of the router host
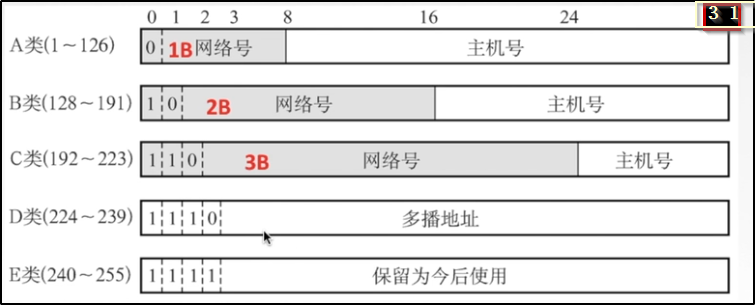
IP Composition of address
{<network number><Host number>}
IP Address writing (dotted decimal)
110111111 00000001 00000001 00000001 = 233.1.1.1
*Network division ABCDE
*Private IP address
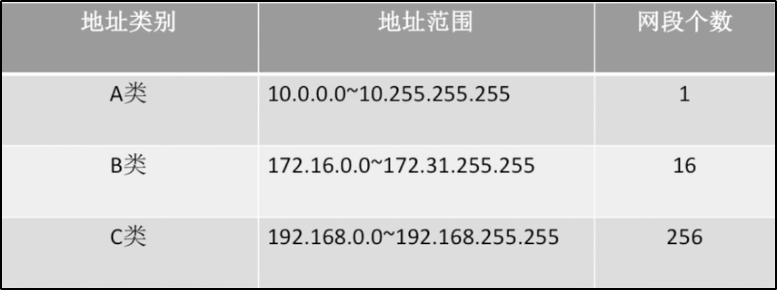
4.3.5 subnet division and subnet mask
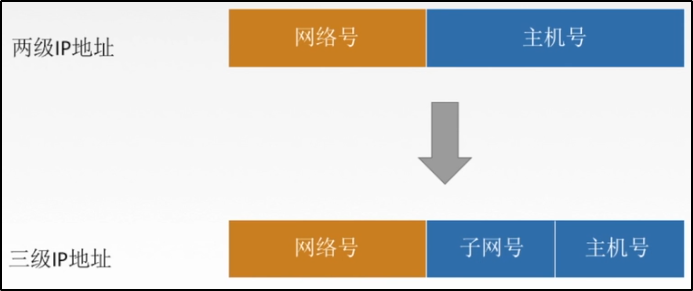
> After a unit divides a subnet, it still appears as a network (network number) externally > The internal subnet division cannot be seen from the outside > Whether the subnet number can be all 0 and all 1 depends on the situation > The host number cannot be all 0 or all 1 > The host number shall be reserved for at least two digits // When only 1 bit is reserved, either 0 or 1 // All 0 indicates this network, and all 1 indicates broadcasting
*Subnet division diagram
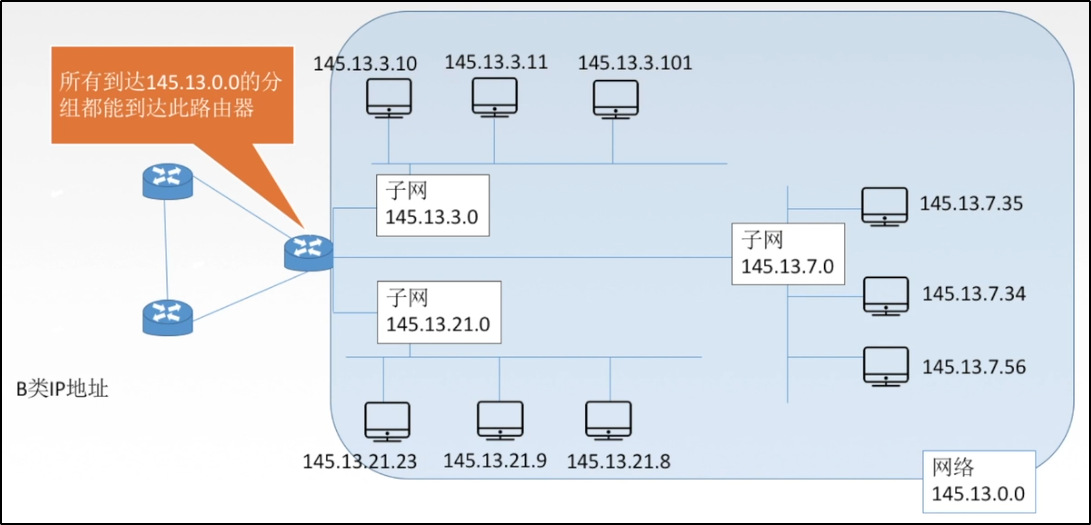
*Subnet mask
> IP The address is dotted decimal, and every 8 bits are represented as a decimal number, but some of these 8 bits belong to subnet number and some host number; > Subnet mask: 1 on the left and 0 on the right; > The number of 1 tells us which of the above 8 bits is the subnet number and which belongs to the host number
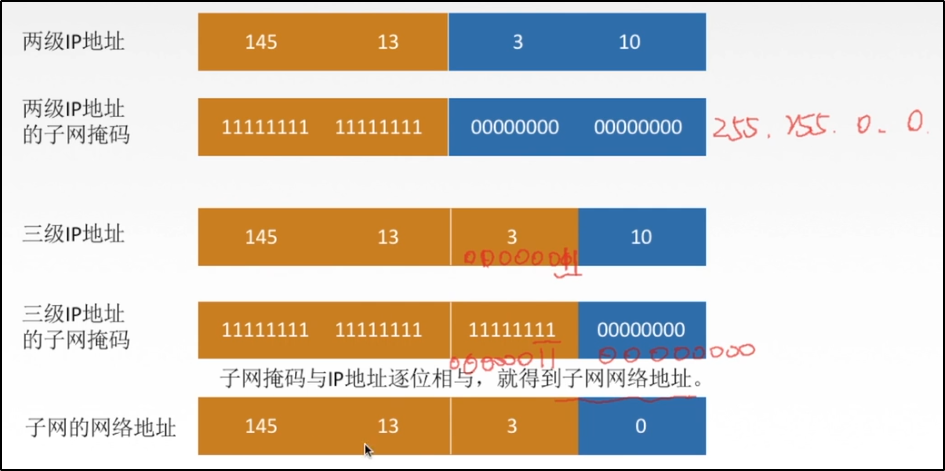
*Example of subnet mask
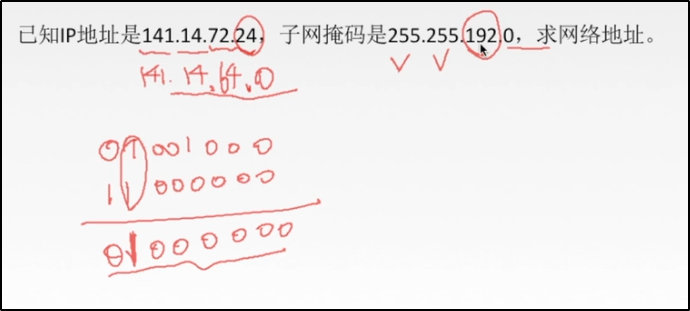
To find the network address is to find which network segment it is located in
The method is the IP address and subnet mask and performs the and operation
# explain 1 And 1, the result is 1 0 And 1, the result is 0 IP Address: 72=64+8 The corresponding binary is 01001000 The binary corresponding to 192 in the subnet mask is 11000000 And operation: 01001000 11000000 ------------ 01000000 = 64 So the network address is: 141.14.64.0
*Subnet mask and decimal representation
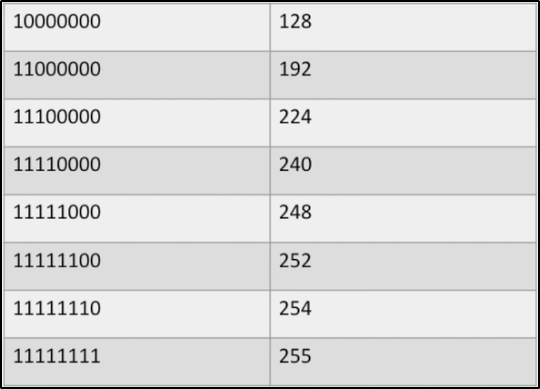
*Example of subnet mask
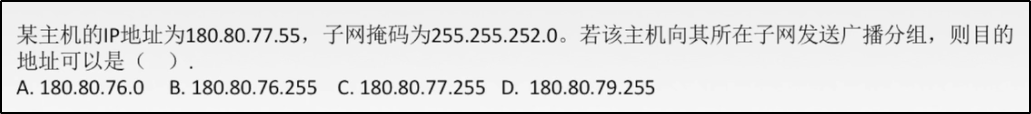
Answer D
Here is the destination address, not the network address in the previous question!!!
# explain 252 of the subnet mask corresponds to 111111(00) That is, if the subnet number is 6 digits, the host number is 2+8=10 position Because it is a broadcast packet, all 10 bits of the host number in the destination address are 1 Namely:(11)11111111 But, IP The address is displayed together with 8 bits, so the two 1s in the above brackets should be counted into the preceding subnet number 77 The corresponding binary is (010011)(00) Take the first 6 digits as the subnet number, plus the two extra ones of the host number Namely:(010011)(11)=79
4.3.6 non classified addressing CIDR
*CIDR diagram

*CIDR benefits
1.Eliminates traditional A Class, B Class, C Class and the concept of dividing subnet 2.Integrate subnet address and subnet mask to facilitate subnet division
*Examples
some CIDR Address in address block: 128.14.35.7/20 // /20 indicates the network prefix, and 20 also means that the first 20 bits of the subnet mask are 1 Convert to binary: (10000000 00001110 0010)0011 00000111 Minimum address: all host numbers are 0 (10000000 00001110 0010)0000 00000000 128.14.32.0 Maximum address: host number all 1 (10000000 00001110 0010)1111 11111111 128.14.47.255 // Can not be assigned, because all 0 and all 1 problems Address block: 128.14.32.0/20
*Form a Supernet
> What constitutes Supernet? Forming a subnetwork of Jiaotong University by multiple subnetworks is called forming a supernetwork; > method: Add network prefix - 1
... to be continued
*Longest prefix matching example
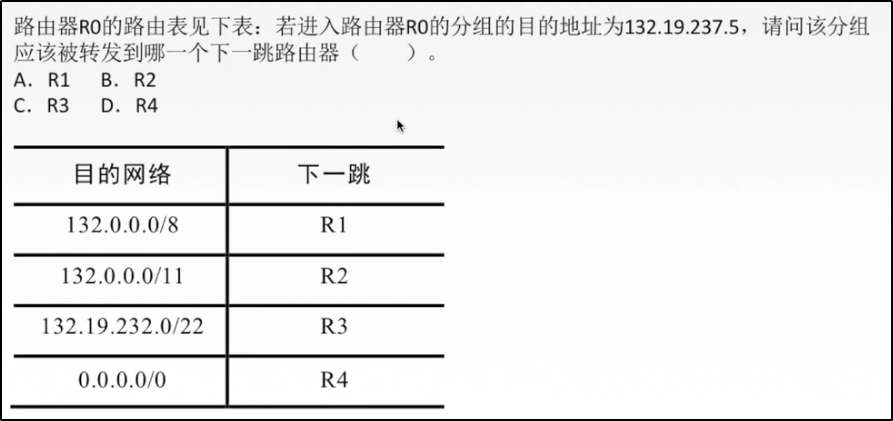
Decimal: 132.19.237.5 1)Divided by prefix 8 Only 8 bits of the first bit, so CIDR The result after addressing is 132.0.0.0/8 // Part of the network prefix remains unchanged, and the rest are set to 0 2)Divided by prefix 11 Among the 8 bits of the second bit, take the first 3 bits and set the others to 0 Existing: take 19 = (000)10011 Top 3 of, 000=0 So: 192.0.0.0/11 3)Divided by prefix 22 22=8+8+6 The 16 bits of the first two bits do not move Among the 8 bits in the third bit, take the first 6 bits,Other set to 0 237 = (111011)01 Set 0:11100000=236 So it should be: 132.19.236.0/22 C The answer is wrong, AB All match, so choose the longest prefix, i.e. 11, 11 B
*CIDR example

# This problem is to divide the subnet number on the basis of CIDR 24=8+8+8,So the first three bits don't move The 8 bits of the fourth bit are divided 248 = 255-7 = 11111000 There are five 1s, so the first five digits are the subnet number and the last three digits are the host number Number of subnet numbers: 2^5=32 // In CIDR, all subnet numbers are allowed to be 0 and all 1, so there is no need to subtract 2 Maximum number of assignable addresses in each subnet: 2^3-2=8-2=6
4.3.7 ARP Protocol
4.3.8 DHCP protocol
4.3.9 ICMP Protocol
4.4 IPv6
4.5.1 RIP protocol and distance vector algorithm
*Overview
> RIP Advantages: simplicity > RIP The protocol requires every router in the network to maintain ta Unique best distance record to each network > RIP Suitable for smaller networks // RIP allows a route to contain up to 15 routers, i.e. 15 hops // Distance ≈ "hops", that is, the number of routers passing from the source port to the destination port, and the number of hops passing through each router is increased by 1 // A distance of 16 indicates that the network is unreachable
*RIP protocol and routing table diagram
> explain // When a router is separated between router A and network a, the number of hops is 2 // Router A and network b are next to each other. There are no other routers in the middle. The number of hops is 1
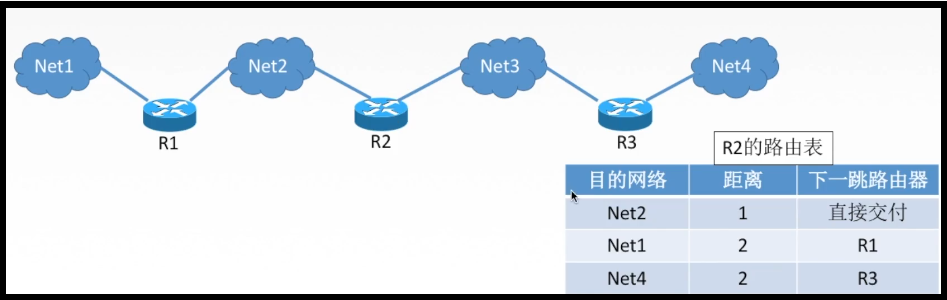
*Information exchange of RIP
> Exchange information with neighboring routers only > The information exchanged is its own routing table // Distance to a network, which router is the next hop
*Routing table updating and convergence
> Exchange information every 30 seconds and build a new routing table according to the new information > If it exceeds 180 seconds, it is determined that the neighbor is gone and its own routing table is updated > After several updates, each router will eventually know the darben autonomous system AS The shortest distance between any network and the next hop router // Convergence is reached
*Distance vector algorithm
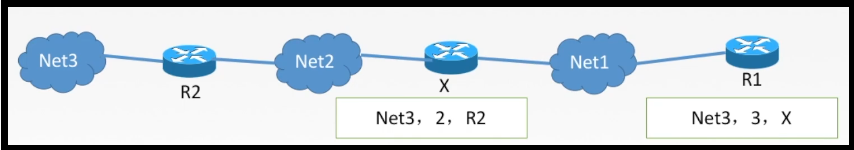
*To router R1 take as an example*
> Modify messages sent by adjacent routers RIP All table entries in the message
// For RIP messages sent from adjacent routers with address X: change the address of the next hop field to X and the distance field to + 1
> For the modified RIP For each item in the message, perform the following operations
> R1 The destination address does not exist in the routing table( Net3),Fill this item in R1 Routing table for
> R1 The destination address in the routing table( Net3),Then view the original next hop address:
> If the next jump is X,Replace the items in the original routing table with the received items
// Just the latest
> If the next jump is not X,If the number of hops is less, it will be replaced, and if the number of hops is more, it will not be processed
> If more than 180 s,Then put X Mark as unreachable router
// That is, the modified distance is 16
4.5.2 OSPF protocol and link state algorithm
*OSPF features
> With whom? Use the Hongfan method to send information to all routers in the autonomous system // Each router sends its own information to adjacent routers // Eventually, all routers get copies of the information > For what? Link status between this router and adjacent routers (which routers are adjacent to this router and the cost of this link) // Exchange all routing information different from RIP // The routing information includes the distance d to the destination network A and the next hop router Rx > How often? When the link state changes > Finally, all routers establish a link state database, that is, the whole network topology > Each router knows its cost to a router and the shortest path to a router
... to be continued